Starbucks' app is the most used mobile payment app in the U.S. because it's well-designed and convenient. But if you use the iOS version on your iPhone, your username, email address, password and location data could be compromised because the app stores them in plain text.

A hidden feature residing in Mac OS X Mountain Lion is the ability to view and also reply to your friend's tweets through the Contacts application, previously known as Address Book. The only way to do this, though, is to provide your Twitter account login data to the Contacts app. To integrate your Twitter, just go to System Preferences, then click on Mail, Contacts & Calendars and choose Twitter. Put in your Twitter login information and then click on Update Contacts. Twitter will use your e...

If you're looking for an efficient way to communicate with your online customers or fan base, one way to accomplish this is by setting up a PHP database of people who have signed up with your site, so you can send them email blasts or news updates.

This video shows us the method to use Blackberry email more effectively. Firstly, let us go to the place for typing your emails. Click on the leftmost icon at the bottom of the home screen. Now press the button on the left side of the track ball and choose 'Compose Email'. Now, if you want to enter your phone number in the body of the email, type in 'Mynumber' and then the press the space bar. You will now see your mobile number in the body of the email. Enter 'Mypin' for displaying your Blac...
The video is about how to change the IP address. MAC address is the unique identifier a site of the most network adapters. MAC address is used to determine what IP address the computer will have and one way to change the IP address is by changing the MAC address. The method is only applicable for the windows systems and for the MAC systems you need to look at the link provided. In Windows in the start menu, type cmd in the run/search box, which will launch the command window. Type ipconfig/al...

Adobe is best known for its photo and video editing software, but they also have a number of lesser-known apps that you may be interested in. Adobe Fill & Sign, available on iPhone and Android, is the best way to electronically fill out important documents on your smartphone with a third-party app.

Leaked databases get passed around the internet and no one seems to notice. We've become desensitized to the data breaches that occur on a daily basis because it happens so frequently. Join me as I illustrate why reusing passwords across multiple websites is a truly awful practice — and compromise hundreds of social media accounts in the process.

So much information exists online that it's easy to get lost in data while researching. Understanding the bigger picture can take a lot of time and energy, but narrowing the question to one that's easy to answer is the first step of any investigation. That's why analysts use open-source intelligence (OSINT) tools like Maltego — to help refine raw data into a complete understanding of a situation.

A VPN service is almost an essential these days. Good ones can block ads, prevent tracking cookies, encrypt your internet traffic for better security, and even spoof your device's location to bypass geo-restrictions — all things you should be concerned about in the age of NSA snooping and Facebook data mining.

Here I will show you how to properly dig information on the web that has already been published, you just dont know it.

Welcome back, my greenhorn hackers! As expected with Null Byte's dramatic growth over the last year, we have added many new aspiring hackers who are still lacking in the basics of networking. In addition, with the new "White Hat" certifications coming out shortly, the exam will require some basic networking skills and knowledge to pass.

Hi I am a new member of null byte(although I am reading this website from the beginning) and this is going to be my first post.

You must have read news about hackers dumping the data online, recent one was Ashely Madison. It's only the big companies' data, which gets noticed once it is out. There are many other small leaks which don't even get a mention. So this article is the first one of my series which will help you to find hacked accounts. Some of you must already know about this, but this post is intended for the new learners. This also serves as an example of my learning how a good service can be used in other w...

One of the many unique features that sets Android apart from other mobile operating systems is its live wallpaper system. Instead of the same old boring static image, this system lets developers create apps that provide dynamic home screen wallpapers.

Do you ever wonder how all these celebrities continue to have their private photos spread all over the internet? While celebrities' phones and computers are forever vulnerable to attacks, the common folk must also be wary. No matter how careful you think you were went you sent those "candid" photos to your ex, with a little effort and access to public information, your pictures can be snagged, too. Here's how.

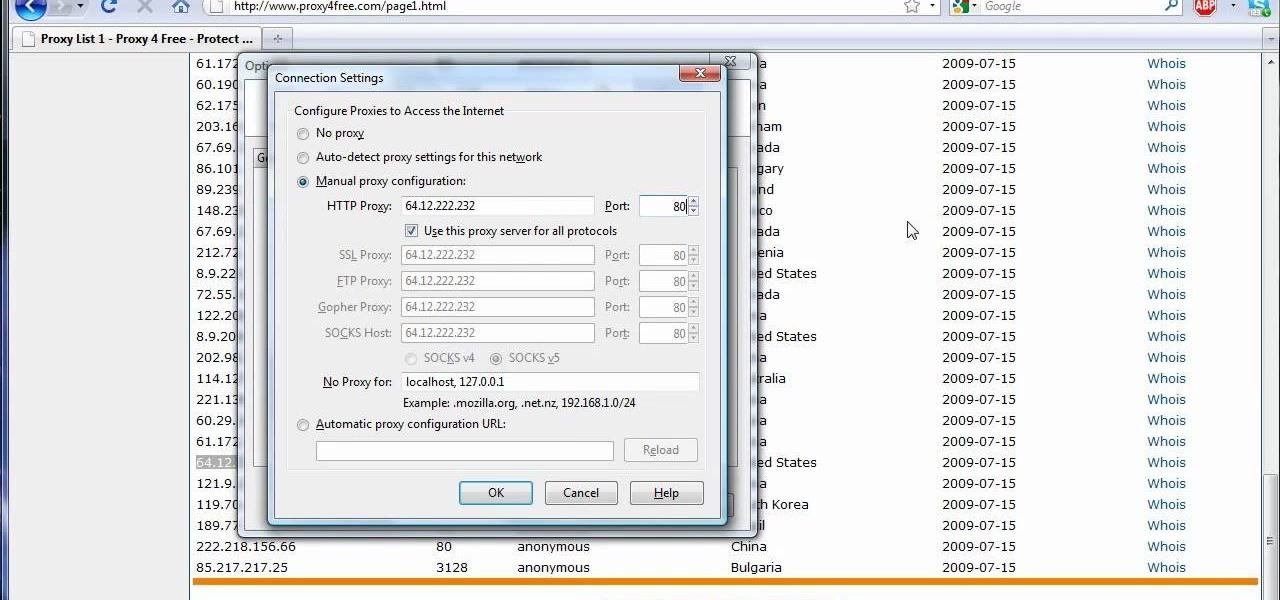
The video shows us how to use a proxy server with Firefox to hide your IP address. you can actually use this to avoid the hacking and various things that are blocking you from websites. Firefox is one of the easiest way to do this and for doing this you need to Google search the free proxylist and then you can select a proxy from the one which is related to the country you are residing in. Then copy that proxy server and then go to tools and click on options and under advanced tab click on ne...

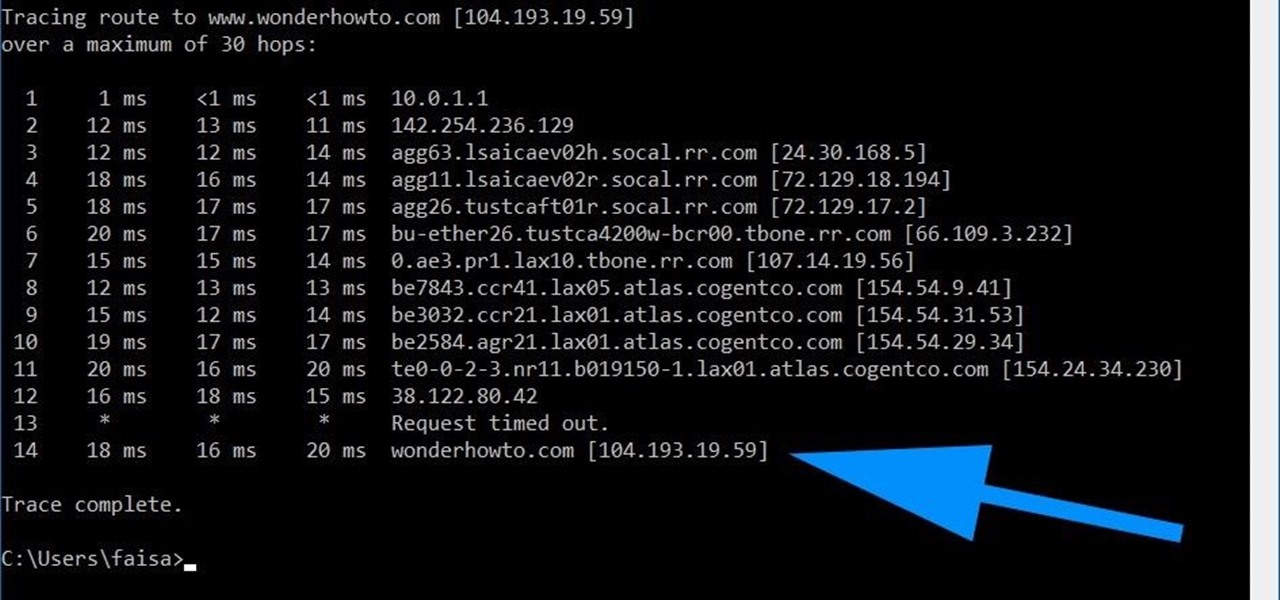
Using a simple trace trick, you can easily look up the IP address and its location for any website. This method uses a command line command to first find the IP address of a given website, and then uses a free online tool to get that IP's location.

In general, hacking and information security is not just one discipline, but a number of them, and today we will look into some of the networking concepts.

The Motorola Droid Bionic has support for both corporate email and personal email accounts. If you want to setup either, take a look at this guide from Motorola on how to sign into your email on the Android smartphone so that you can start reading and sending new messages using Verizon Wireless's 4G network connection.

This 5 part video tutorial series will show you how subnet an IP address on your personal computer. It's a thorough, detailed walkthrough of each step, with explanations on things as basic as "what's an IP address?" Watch the entire series to learn thoroughly about subnetting IP addresses on your personal computer.

Apple has seemingly always made it a priority to show how much it cares about user security and privacy — enough that it has a page dedicated to it, proclaiming that "privacy is a fundamental human right." It's true that there are few issues more important than user privacy when it comes to technology, and Apple only makes things better in iOS 13.

For a while, Gmail only had one swipe gesture, and it could only perform one of two actions: Archive or Delete. Not that it wasn't useful — you could eliminate most spam emails in a matter of seconds by swiping left or right on any email in your inbox. But now, Google has finally added more custom actions to its swipe gestures.

As cheesy as it sounds, #HODL became a thing for a reason. A lack of discipline when dealing with cryptocurrencies can lead to impulse buys and panic selling, and ultimately, depleted funds. Luckily, Coinbase has a way to safeguard your cryptocurrency savings to not only protect them against thieves, but to also help you resist the urge to sell off your investments.

Months before London-based Jonathan Moon would turn 30, he started musing over how to celebrate. While he had rung in past birthdays at home, he wanted to do something out of the ordinary as a farewell kiss to his twenties. A short ski vacation with friends felt like the perfect idea.

Your Nexus 7 may be a tablet, but it can also be used as a phone, thanks to the continued upswing of VoIP applications, which send voice and media messages over the Internet—not over a cellular network.

Send an email prematurely? Forgot to attach a file? Accidentally addressed it to the wrong person? It happens to the best of us. But what can you do to get it back? Hack into the other person's email account and delete the email before they get a chance to see it? Unless you're a hacker extraordinaire, that option is unlikely. So, what can you do? If the email has already been sent, you're probably out of luck. Even if they didn't read it yet, your chances of retrieving it are slim. But some ...

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.

This is a great solution if you need to get something off your computer, but you are not home. Want access to your files stored at home? How about hosting a home web server? Static IPs are expensive, if you can even get one. We set up Dynamic DNS instead!

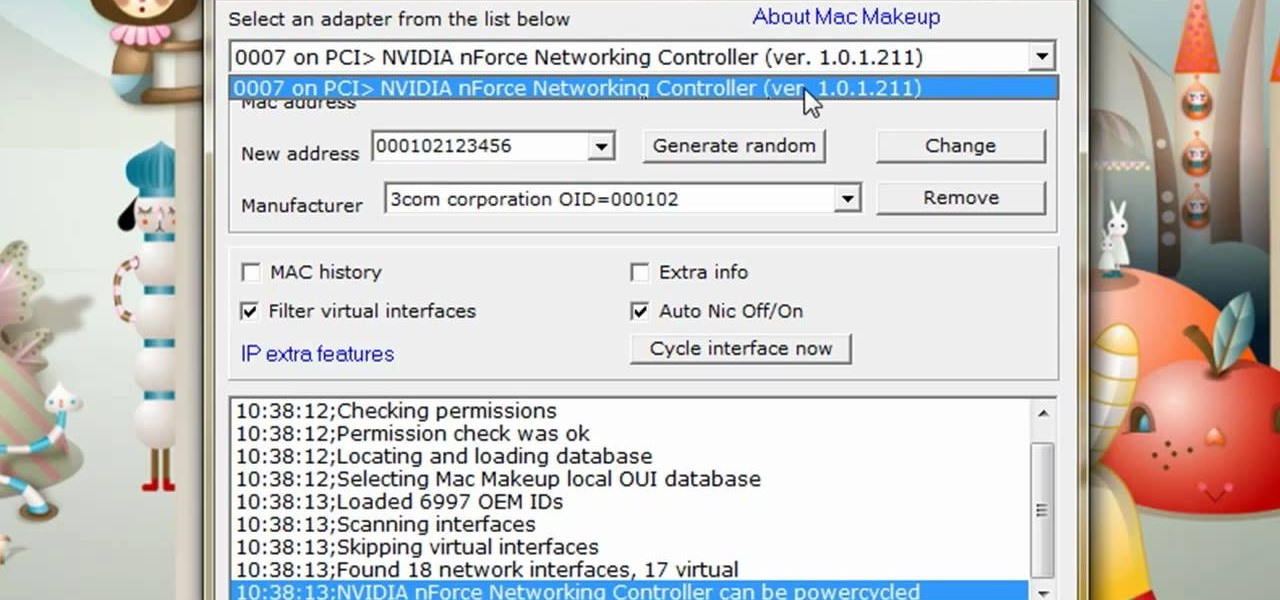
The Lab Rats, Andy Walker and Sean Carruthers, explain Media Access Control (MAC) addresses. Filtering MAC addresses allow you to very specifically control access to your wireless network.

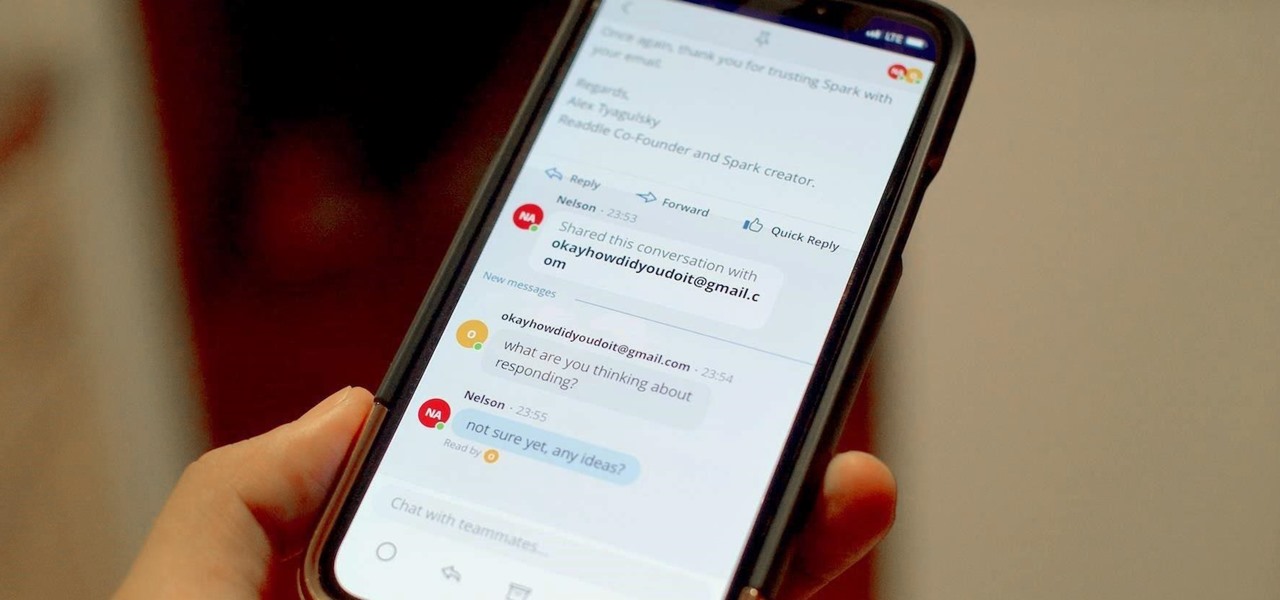
You usually reply to emails on your own ... unless it's related to your work. You may want input from coworkers or higher-ups, and while forwarding works, Spark offers an easier way to discuss important emails with others. Using Spark for Teams, you can easily share an email with your team and discuss it privately.

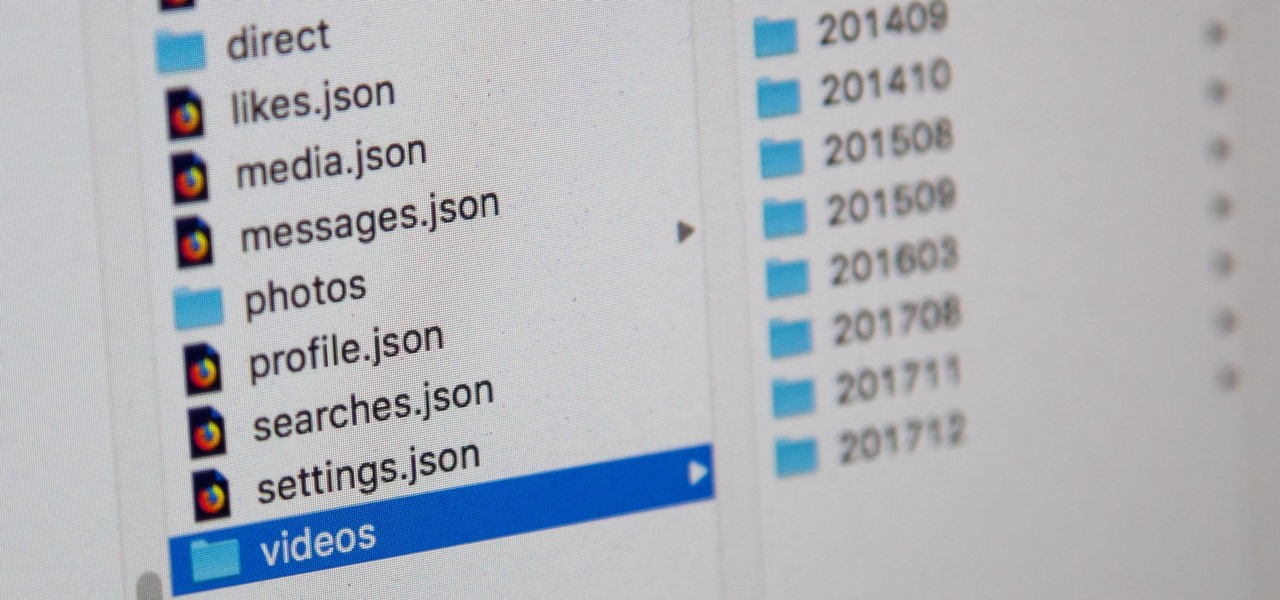
Facebook, parent company of Instagram, has allowed you to download photos and other account data for some time now, but the data request feature is also now available on Instagram to meet the GDPR data portability requirement in the EU — and it's available worldwide, not just in Europe.

One of Android's most glaring weaknesses is its lack of an iMessage equivalent. That is, of course, until now. There's one app that will allow Android users to experience iMessage on their non-Apple phone, complete with end-to-end encryption, message effects, and group messaging.

Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of modules: exploits and payloads. Remember, Metasploit has six types of modules:

With troves of sensitive information, like receipts and password reminders, hiding in your email, your inbox can become a sort of Holy Grail for hackers—or anyone with your password. Although my crazy ex-girlfriend had no hacking experience, using my email login, she was able to find a lot of account information with just a general search for "password" in my inbox.

Google Earth has long served as a great tool to explore the furthest regions of our beautiful planet from the comfort of our own homes, but for those with more than just a recreational interest, a bundle of pro features had always cost $399... a year.

The internet is forever. When you put something out there, it can easily be re-shared, floating from server to server indefinitely with no way of taking it back. It's a scary thought when you consider that a young adult's grandchildren will one day have access to their drunken party pics.

When you post something online, it pretty much stays there. So it's no surprise that Snapchat, the self-destructive photo-sharing app, became such a huge hit, boasting an estimated 50 million users. Its ephemeral nature has proven popular, especially with teenagers—who are now well aware of the burden that permanence on the internet has.

Let's get started emailing! This clip will teach you everything you need to know to install an email client on your mobile phone and to set up your email account. For all of the details, including complete, step-by-step instructions, watch this brief, official N97 Mini owner's guide from the folks at Nokia!

Want to add a cute tagline to the end of your emails? Or are you just tired of sending out ads for Apple everytime you send an email? Changing your email signature is easy, just watch this tutorial which shows you how!