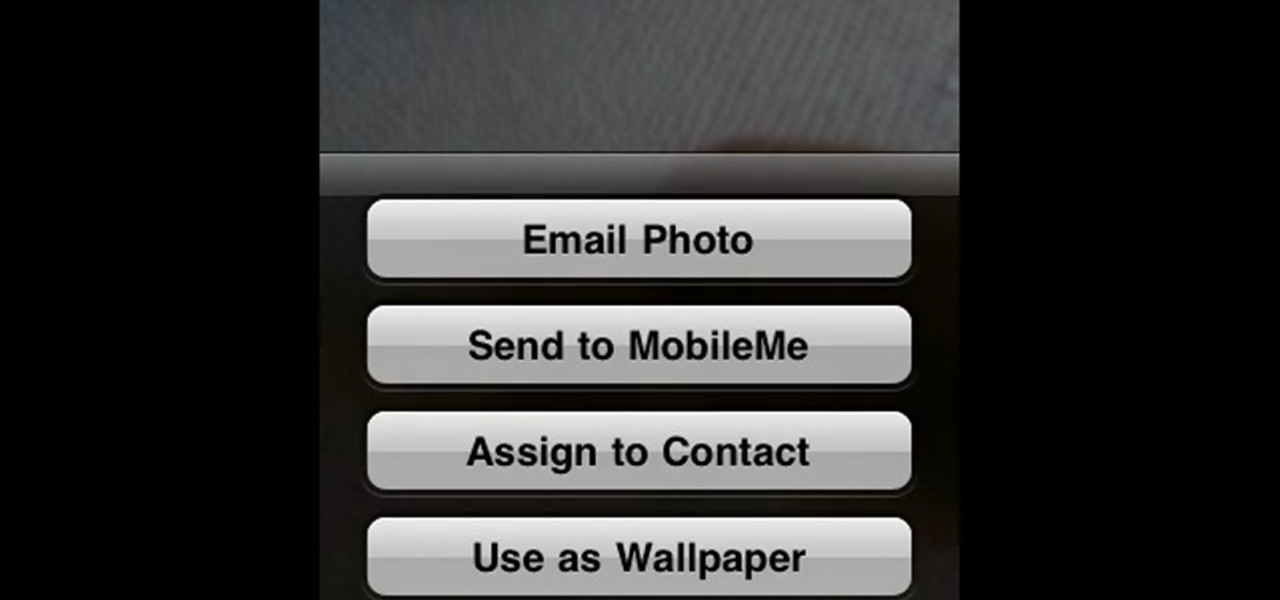
In this Electronics video tutorial you will learn how to Email photos from your iPhone. This is really very easy and simple to do and takes practically no time. On your iPhone go to the camera icon and tap on it. Then find a picture that you want to email. Then tap on the little icon on the lower left of the screen as shown in the video and then select email photo. Then you put in you want to send the photo to, type in a subject and add some text if you want. And the final step is to tap ‘s...

Your IP address is what identifies your personal computer while you are online. You may want to change your IP address for privacy, to bypass website settings, to download, or for various other reasons. This tutorial will take you through the steps you need to start surfing more anonymously.
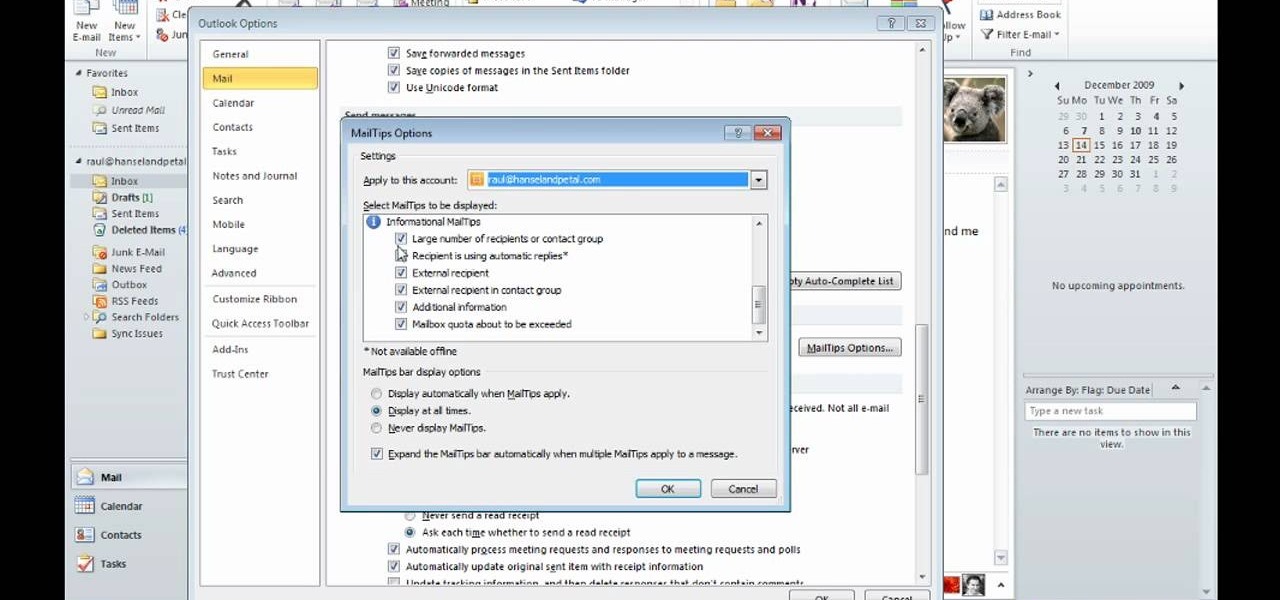
David Rivers is back to give us some more tricks on using MS Outlook 2010. In this video he tells us how you can avoid sending email to the wrong person by setting up some email preferences in MailTips. MailTips actually has the ability to alert you when you are about to send an email under certain conditions. Don't worry about sending an email to your boss that was meant for your co-worker. Your MailTips folder contains many options that you can use to restrict some of your outgoing mail and...
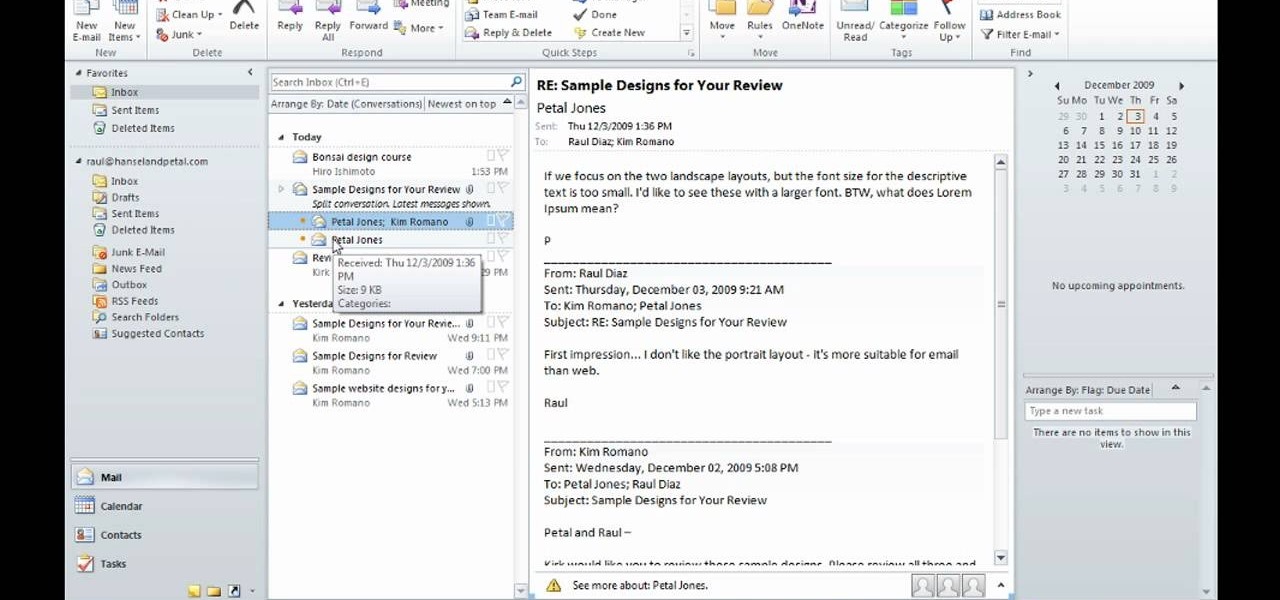
In this video David Rivers shows that the conversation look of Excel 2010 has greatly improved. Tracking and managing related emails, saves your inbox space to enable you to manage large number of emails effectively. By default, the conversations are arranged by date. Email interactions will have an arrow displayed. You can easily expand and collapse the conversation. The major improvement is the function of ignoring or clearing up conversation with just a few clicks. The future conversations...
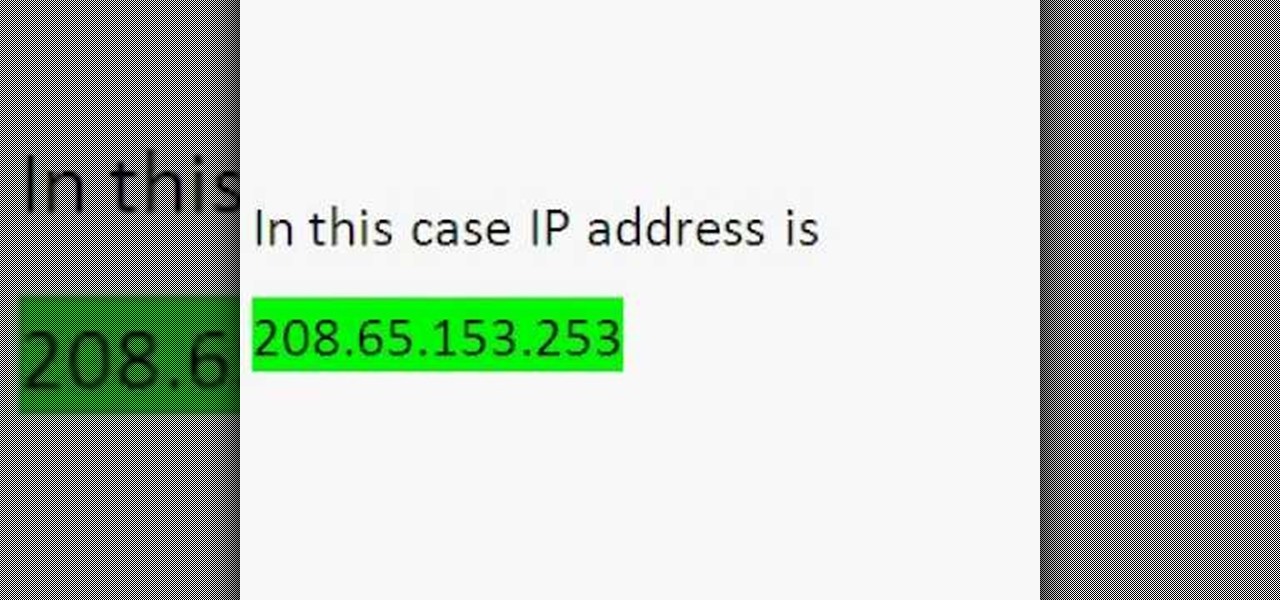
Wondering how to find the Internet Protocol address of a website?
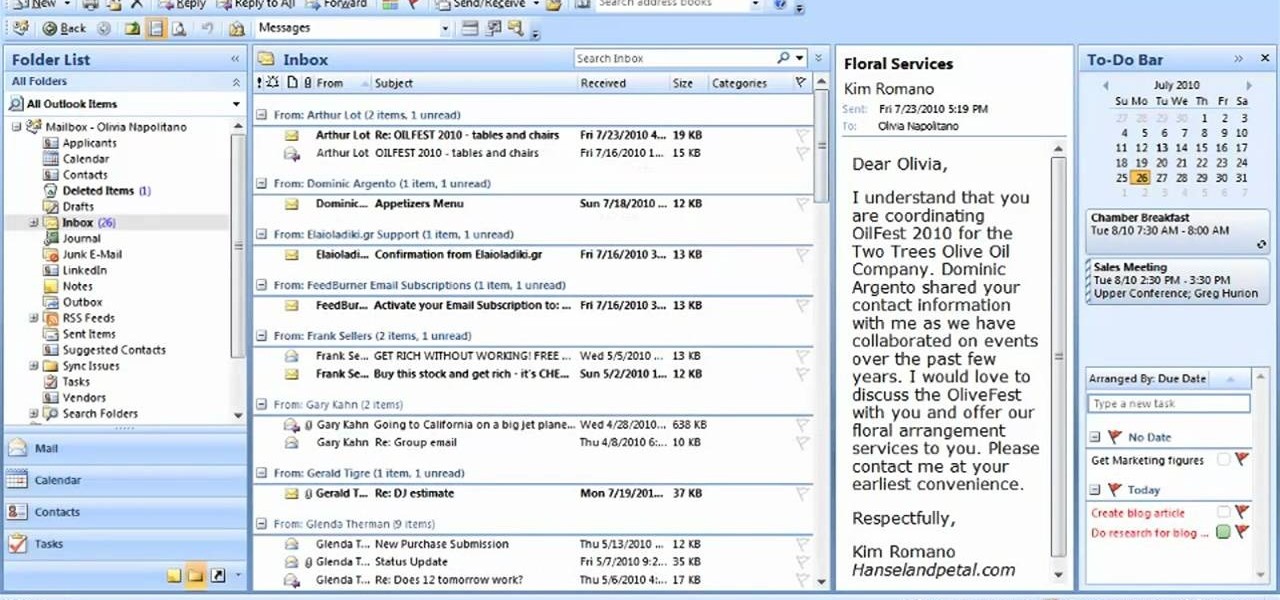
Sort your emails by either date or sender within MS Outlook 2007. This clip will teach you how. Whether you're new to Microsoft's popular email and scheduling application or a seasoned MS Office professional just looking to better acquaint yourself with the Outlook 2007 workflow, you're sure to be well served by this video tutorial. For more information, and to get started organizing your own inbox, watch this free video guide.

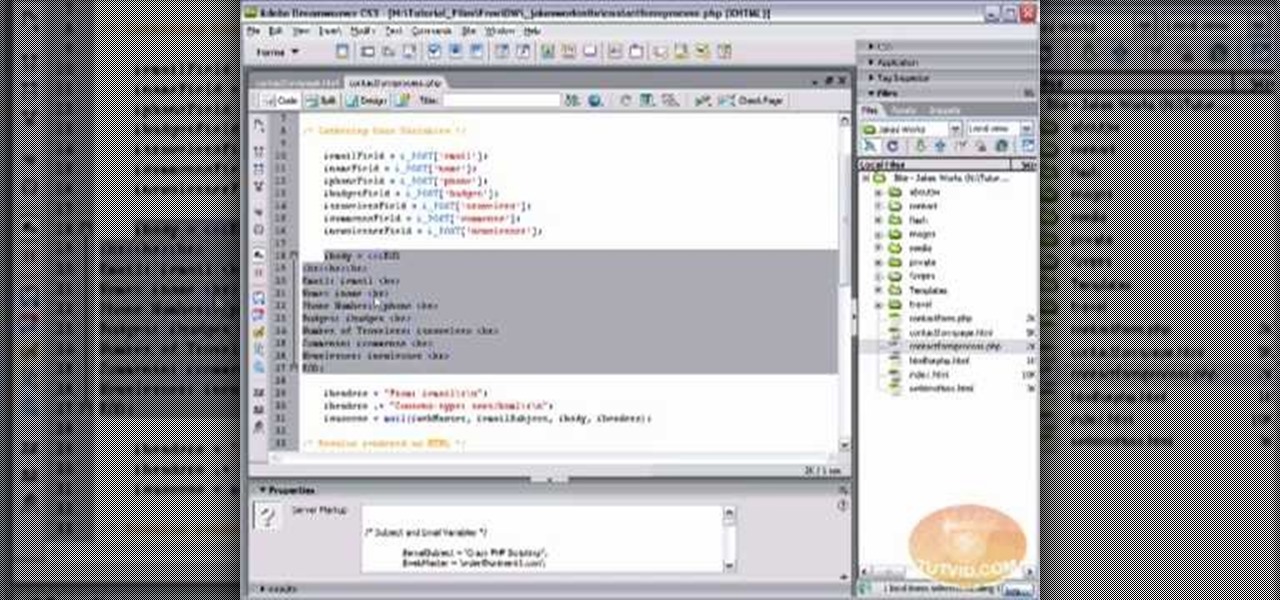
Learn how to build a an Email Handling PHP script in Dreamweaver that sends info from your web form to your email.

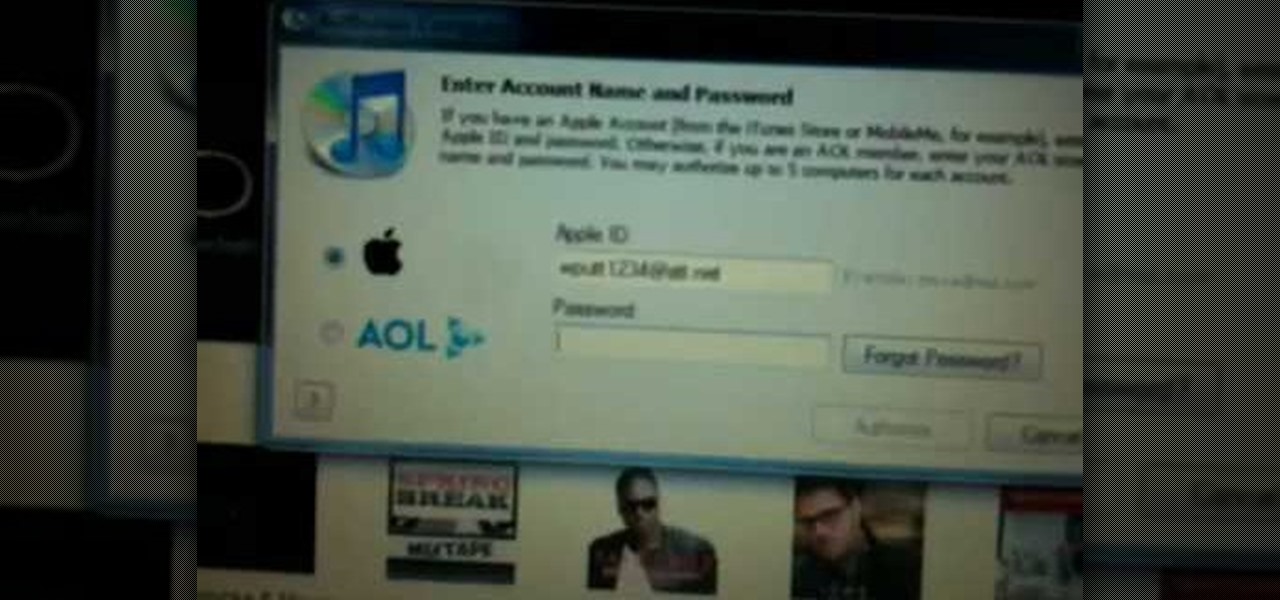
In this video from wadeputtii we learn how to authorize or de-authorize a computer on iTunes. Go to iTunes, sign into your account. Now click on Share and you will see Authorize Computer or Deauthorize Computer. If you want to authorize, click on that and enter your apple user email address and password. Then click authorize. If you have a new computer or you want to prevent someone else from using your account on your computer and you want to deauthorize your old computer, go to Share and De...

Take a look at this video if you've ever been curious on how people send video messages via the iPhone.

One of the many features of the webOS tablet, the HP TouchPad, is a full featured mail app. Before you can use the app however, you will need to setup your email account on the tablet. Take a look at this guide to learn how to setup an account using the automatic method, or the more customizable manual mode.

If you're an iPhone owner tired of have the same email notification sound as every other iPhone owner on the planet, check out this video to see how to change it to what YOU want! You will need to have a jailbroken iPhone, you'll need a little program called Green Poison, and you'll need to have the iPhone jailbroken app Cydia to get it all done. So go for it and tweak it today!

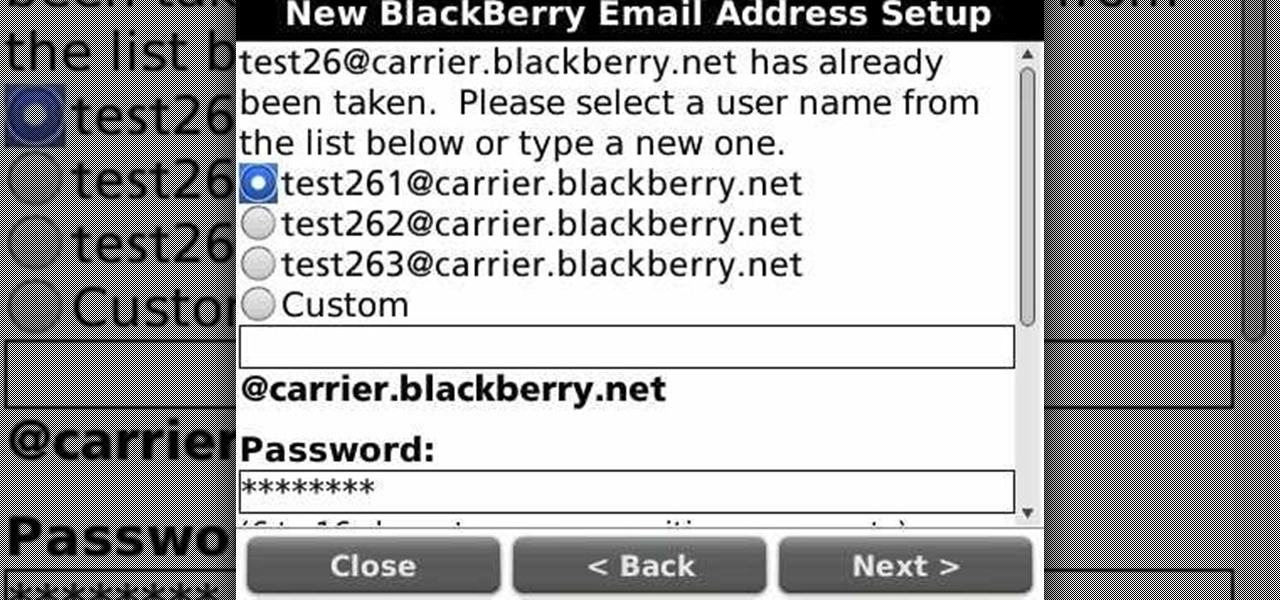
Learn how to create a new BlackBerry Internet service email account on a BlackBerry device running version 5 of the BlackBerry OS. This clip will show you how it's done. Whether you're the proud owner of a BlackBerry smartphone or are merely considering picking one up, you're sure to be well served by this video guide. For detailed information, including step-by-step instructions, take a look.

Learn how to create new email accounts on a BlackBerry phone running version 5 of the BlackBerry OS. This clip will show you how it's done. Whether you're the proud owner of a BlackBerry smartphone or are merely considering picking one up, you're sure to be well served by this video guide. For detailed information, including step-by-step instructions, take a look.

Learn how to create or add existing email accounts to your BlackBerry Bold 9650 phone. This clip will show you how it's done. Whether you're the proud owner of a BlackBerry smartphone or are merely considering picking one up, you're sure to be well served by this video guide. For detailed information, including step-by-step instructions, take a look.

In this video tutorial, viewers learn how to read Google email offline. Begin by logging onto your Google account. Then click on Settings and select the Labs tab. In the Offline headline, click on Enable. To not grab all your emails, go to the Offline tab and select which messages will be synchronized with your computer, based on labels and time frame. This video will benefit those viewers who use Google mail, and would like to learn how to read their emails offline in case their internet con...

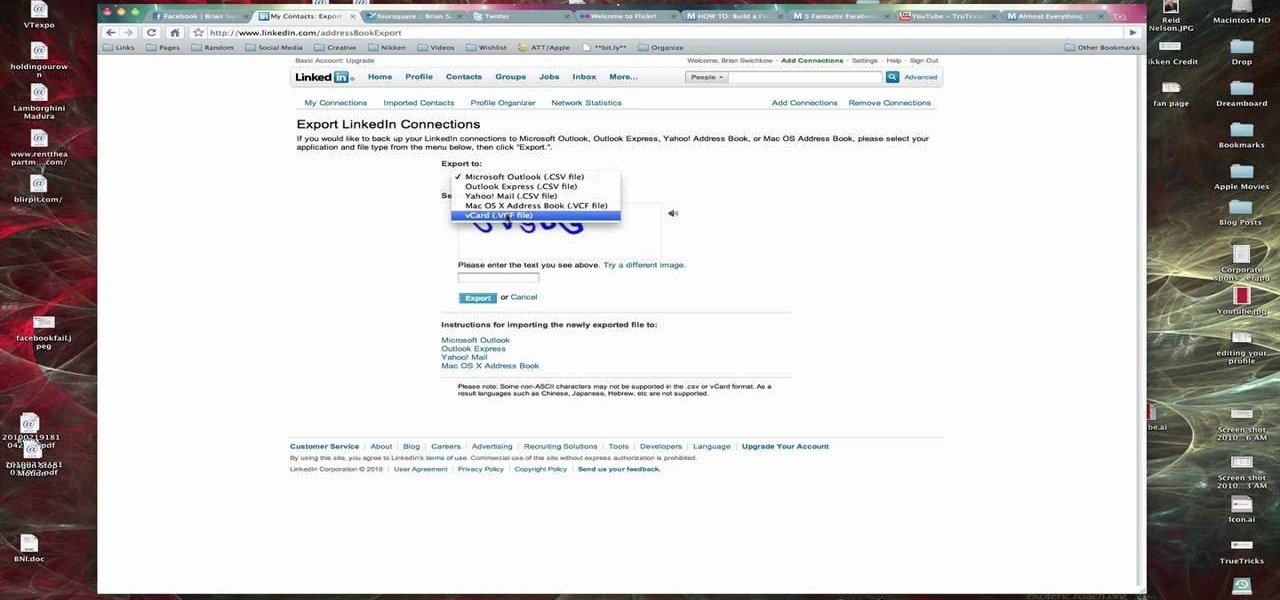
In this Computers & Programming video tutorial you are going to learn how to export LinkedIn contacts to an address book. LinkedIn is great for keeping your contacts in your professional network. To export your contacts go to home page and click on ‘contacts’. Now your full network of contacts will be displayed. On the right hand bottom, click on ‘export contacts’. On the next page select where you want to export the contacts, type in the security code and hit ‘export’ and all the contacts wi...

As with any other Internet-enabled mobile device, the Apple iPad can be used to send, receive and manage email. This official video guide from Apple presents an overview of the Mail app and will teach you everything you'll need to know to use read and compose email messages on your own iPad.

In this video I show you how to get a Flash plugin to allow you to play videos in safari. Your iPhone/iPod Touch does not have to be jailbroken to do this. If you are having problems not getting the email make sure you look in your bulk or spam folder of your email. Just click the activation link in the email refresh the safari page and everything should work.

We've all seen the login pages that allow you to log in to third-party accounts using your credentials from Facebook, Google, or Twitter. It saves you the trouble of creating another account and remembering more passwords — but it can also become a privacy and security issue, which is why Apple created the "Sign in with Apple" feature for iOS 13.

Now that we have our payload hosted on our VPS, as well as Metasploit installed, we can begin developing the webpage which will trick our "John Smith" target into opening our malicious file. Once he has, we can take over his computer.

I misplaced my iPhone 6 just a few weeks ago, so I know firsthand that losing an iPhone sucks. Luckily, my tale didn't have a bad ending.

In the weeks before Apple officially released iOS 8, consumers were abuzz over rumors that a new feature would password-protect your photos and text messages from prying eyes. Unfortunately, this ended up being untrue, though we did cover some alternatives to protecting your important information using some built-in features and a third-party app. Now, there's a new iOS app that can do it all.

It's been rumored for months, but now we've got some official news about Google's newest music offering, YouTube Music Key. The subscription service will allow for an ad-free experience with background listening (i.e., having your screen off) and offline playback.

Welcome back, my greenhorn hackers! Before we attempt to exploit any target, it is wise to do proper reconnaissance. Without doing reconnaissance, you will likely be wasting your time and energy as well as risking your freedom. In previous guides, I have demonstrated multiple ways to perform reconnaissance including passive recon with Netcraft, active recon with Nmap or hping3, recon by exploiting DNS or SNMP, and many others.

Now that you've got a BlackBerry smartphone you'll want to get online and start emailing the world about it. You can use an exisiting email account and this simple how to by AT&T shows you the necessary steps to do it with OS 5.0.

In this video tutorial, we learn how to use Teleflip's flipOut email-to-SMS service to send free text messages over email. For more information, including a complete demonstration and detailed, step-by-step instructions, watch this how-to from the folks at CNET TV.

In order to find out if an email is a scam, you should avoid clicking on any links in that are in any emails. The links that are attached to emails, in this manner, usually have cloned the website of the institution where you do your banking. The link will look similar to your banking institutions site. Do not enter any of your personal information in emails in this fashion. Your bank will not contact you in this way.

Windows Live Mail makes it easy to manage multiple email accounts. The accounts are laid out on the main screen and are easy to access, making Windows Live Mail a convenient email client. For more information, including detailed, step-by-step instructions, and to get started using multiple email accounts with Windows Live Mail yourself, watch this helpful video guide from the folks at Butterscotch.

In order to block websites on your computer, you will need the address for the website that you want to block. Gather that information first. Then, click on Start. Then, go to Run. Next, type in the following: c://windows/system32/drivers/etc. Click OK.

In order to unlink your Google account and your YouTube account, you will need to go to Google. Click on My Product. Then, click on Edit. Next, click on "Close the account and delete and all services linked to the account". Check the box that says YouTube. Scroll down to the password box. Enter your YouTube password. Next check both boxes. Then, click Delete Google Account.

Protect your email account from would-be hackers and crackers with this free video tutorial from the folks at MacMost. If you have a Gmail, HotMail, Yahoo! Mail or other web-based email account, this video is much recommended. For more information, and to secure your own online free email account, watch this helpful guide.

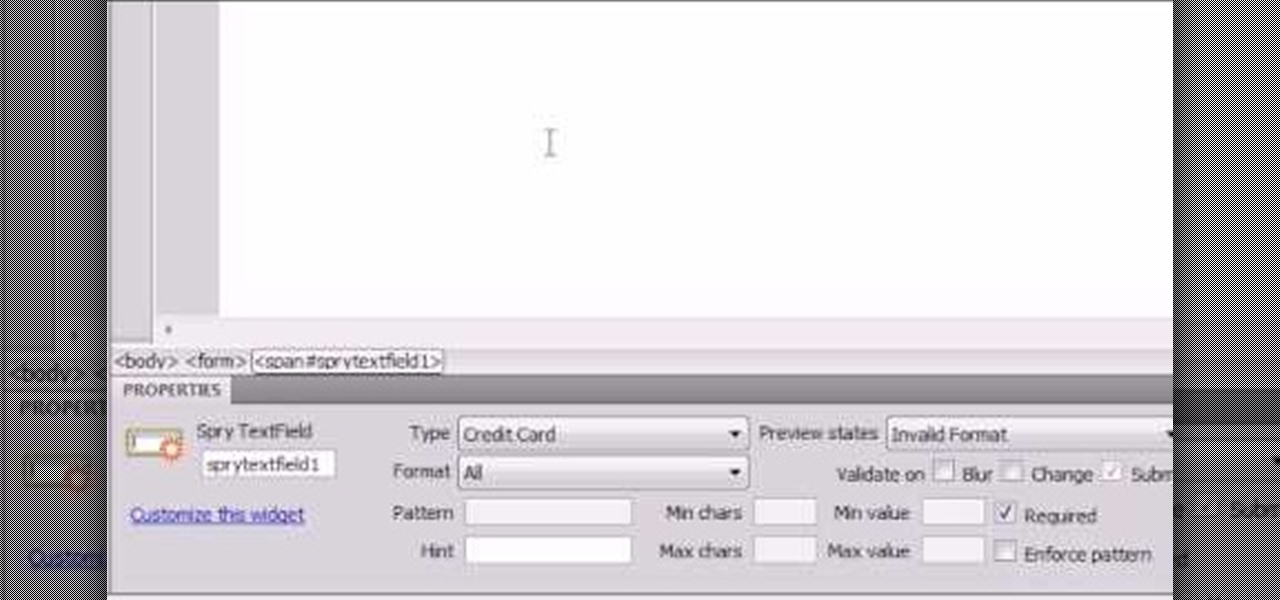
Here the New Boston shows you some tips about using the Spry Validation Text Field. To begin you will go to the Spry Validation Text Field, on Dreamweaver CS4. Looking at the bottom of the page notice the various options that are available for Properties. You find drop-down boxes for Type, Pattern, Minimum or Maximum values, Required, Enforce pattern, Format, Validate on, Blur or Change and Preview States. You can see the types of text available for validating by left mouse clicking the Type ...

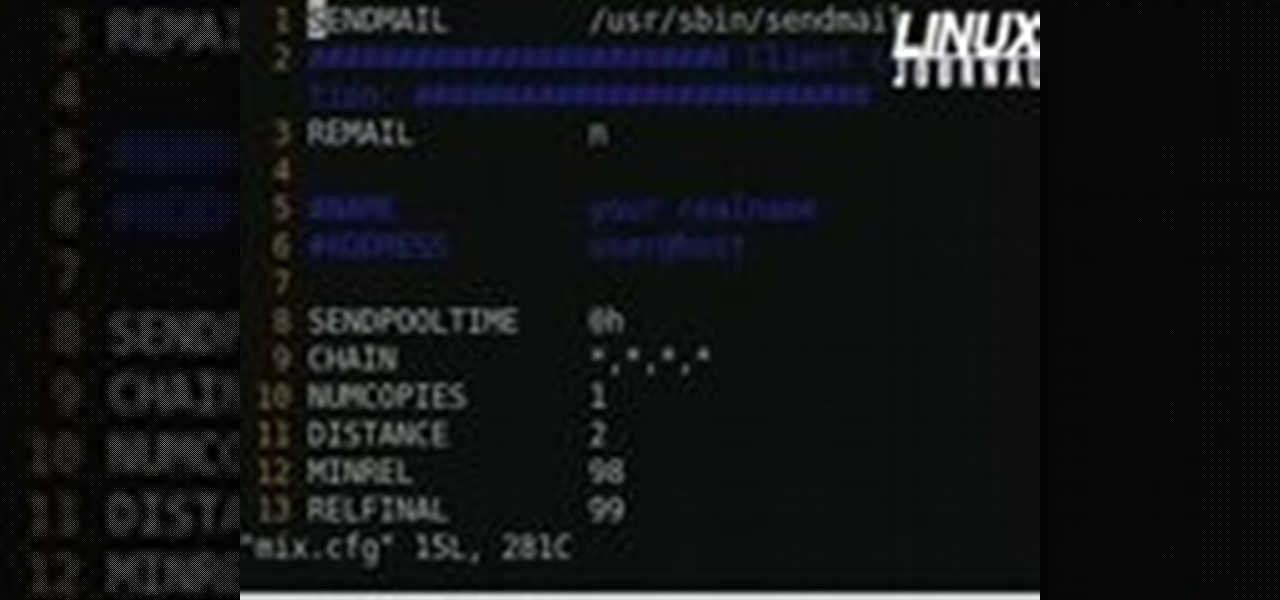
Email is one of the least private and least secure forms of communication, although few people realize this. MixMaster is one way to allow secure, anonymous communication even over the very public medium of email. This tutorial will get you started with MixMaster quickly and easily.

If you're like most people running Mac OS X, you've got quite a large number of entries in your Apple Address Book. In this how-to, you'll find instructions for organizing your addresses into groups for easy access in Address Book, other applications, and even sync devices such as other Macs, iPods and iPhones. For more on using groups in Apple Address Book for Mac OS X, watch this video tutorial.

Gmail is an amazing e-mail service being offered by Google for free, and over the years it has built a large list of great, reliable features. The problem is not many have heard of Gmail, or know how to use it. In this great three part video series you will learn how to sign up for a Gmail account and also how to use some of its fantastic features to get you started on the right track.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

How to enable email based subscription for your drupal blogs using feedburner feeds. Part 1 of 3 - How to Enable email subscription in Drupal.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

On average, an office worker receives 121 emails a day. Many of these emails are trivial and don't require immediate attention. While Gmail's automatic spam filters catch plenty of irrelevant emails, some still make their way into your inbox. Fortunately, Gmail's tools aren't limited to just spam filters.

Before many games make it to the US-based iOS App Store, they get "soft launched" in a smaller country to get real-world testing for bugs. It's a pilot program, so to speak, as countries like Vietnam or the Philippines have far fewer iPhone users than the US, thus offer a more controlled environment for developers to get feedback and zero-in on issues that may occur in a game's early development phases.