Learnasyouwatch shows viewers how to automatically play YouTube videos. First, you need to open your web browser and go to YouTube. Find the video you want to automatically play or upload your own video to YouTube. On the ride bar there is a section that says 'Embed'. Click on the pin wheel icon next to it that is 'customize' and you can set various parameters. Now, you need to copy the embed code and right click and copy this code. Paste this code into a word document. You will need to add '...
Do you want to be that cool person on the web? Heh. Actually, did you just want to try spicing up your embedded YouTube videos? Try it in HD, or have it in autoplay or different sizes! With this code, you will be able to play music, or display your latest vlog as soon as you get a viewer, as long as they allow embedding!

Want to make sure a message doesn't fall into the wrong hands? Try embedding it in a web image. With the Mozaic Encrypt web app, it's both quick and simple. For all of the relevant details, and to get started adding secret messages to image files yourself, watch this home-computing how-to from Tekzilla.

Learn how to import and attach mp3, mov, and wmv files to your website both by embedding and linking the files with Adobe Dreamweaver

You know YouTube is able to host high-defintion video content online now, right? Well, how do you watch it, or make it, or embed it? Well, this video tutorial will show you how to upload, embed and watch 720p HD video on YouTube. This YouTube hack will let you watch and embed videos in true 1280x720 high definition.

This is an intensive one-day overview video tutorial of the fundamental concepts of the Ruby on Rails Web programming framework, presented by the UC Berkeley RAD Lab. The overview consists of six sections of approximately one hour each. Click through the video chapters to go through the Ruby on Rails programming course.

Looking for an easy way to hide a file or folder? Try embedding it within an image file. It's easy and this clip presents a complete, step-by-step overview of the process. For more information, including detailed instructions, and to get started embedding files within JPEG files yourself, take a look.

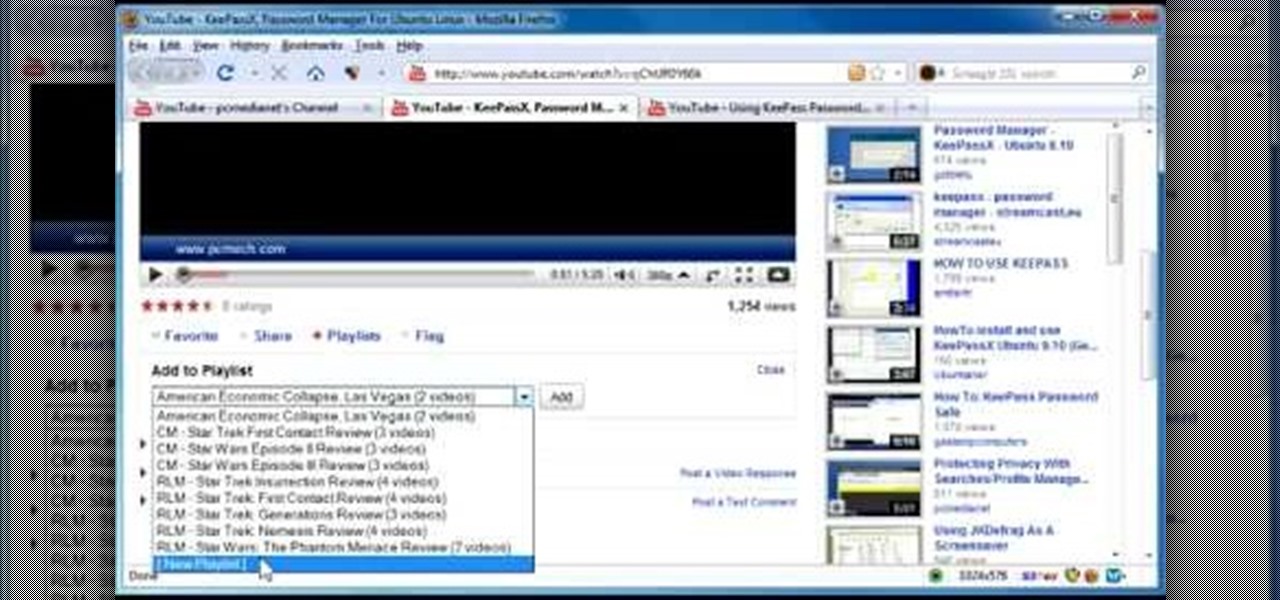
In this video, the author shows how one can make one's own playlists on YouTube, and also get the code which can be embedded on one's website or blog. All one has to do' according to the author, is to first load all the videos which one wants in a playlist and pause them. Then one has to click the 'Playlists' option under the video pane. In the drop-down list which opens, one can choose one of the existing playlists or create a new one, and then, simply click the 'add' button. This action has...

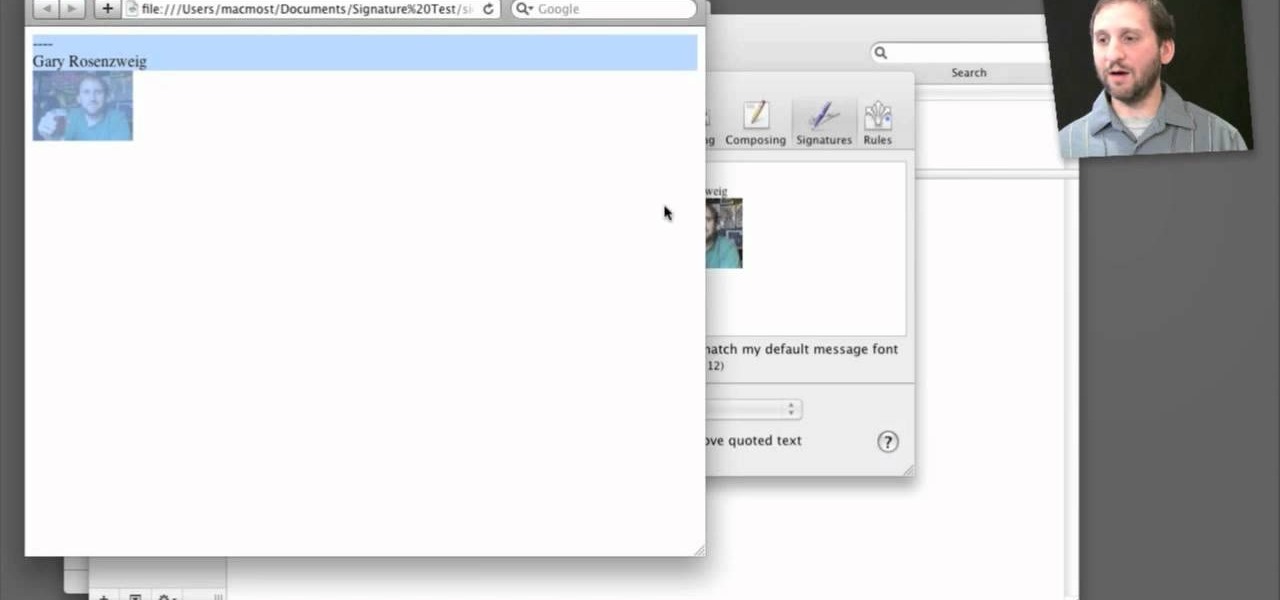
Looking to spice up your email signature a bit? Why not add an image? This simple how-to shows you an easy way to take advantage of some simple HTML embedding so you can add an image to your Apple mail signature.

Interested in importing and displaying an external feed on your Tumblr page? This brief video tutorial from the folks at Butterscotch will teach you everything you need to know. For more information, including detailed, step-by-step instructions, and to get started embedding feeds on your own Tumblr blog, take a look.

This video will show you how to embed subtitles into video files using the free softwares VirtualDub and dvXLand. Embedding subtitles with VirtualDub and dvxland allows you to add subtitles to your videos without having to keep two separate files.

Uploading photos to Photobucket and embedding an image onto your Myspace profile.

If you are looking to get your point across even better, why not add video to your Powerpoint presentation?

If you're looking for a cool way to add text to your videos, like for an opening sequence to a film where the credits are displayed, embedding the text directly into the scene is the way to go, especially if you like the hit television show "Fringe", who used these kind of embedded title effects in establishing shots. Car adverts use this technique a lot, as well. "Panic Room" also use this effect in the opening title sequence.

In this video, The Home Depot shows us how to tile the surrounding walls of a bath or shower. Since these walls stand up to a lot of wetness from daily showers, they need to be sound and waterproof. Ceramic tiles are a great way to go. In this demonstration, the tiles are attached to backer board. Protect your tub with a cardboard inlay before you begin. Then seal the edges of the tub with asphalt roofing cement. Then staple 15 pound felt to the studs, embedding the bottom layer to the asphal...

Welcome back, my tenderfoot hackers! One key area on the minds of all hackers is how to evade security devices such as an intrusion detection system (IDS) or antivirus (AV) software. This is not an issue if you create your own zero-day exploit, or capture someone else's zero-day. However, if you are using someone else's exploit or payload, such as one from Metasploit or Exploit-DB, the security devices are likely to detect it and spoil all your fun.

It has been a long while since I last came here to write an article. Graduate school keeps you busy. After I looked over what I had written previously, I decided that I should introduce another fun topic from cryptography. In this case, steganography.

In this web design tutorial learn how to embed a YouTube video for your website design. This Xara Tutorial takes you step by step through the process and understanding of embedding a video for your Xara Web Designer website.

YouTube is a great video service because it's free and has invaded the world… meaning, practically everybody has been on YouTube at one point or another. Another great aspect of YouTube is the ability to embed content on your website or blog… like your WordPress blog. You can also embed full YouTube playlists. This video will show you the steps to embedding YouTube playlists on your WordPress blog, and the principles can be applied for other sites as well.

YouTube is the third most popular website in the world, after Google and Facebook. Millions of subscriptions happen each day on YouTube, with over 800 million unique users visiting each month. In that timespan, roughly 4 billion hours of video are watched, with 72 hours of video uploaded every single minute.

It seems fitting that Time magazine's first augmented reality cover is an issue guest edited by Bill Gates, since the company he founded is currently leading the AR charge via the HoloLens.

Mozilla helped get the ball rolling with WebVR, but support for the technology has been notably absent in Google Chrome until recently. Now, the latest Chromium developer build offers limited support.

The cell phone has come a long way. The very first "mobile devices" were made and used by the military in the late 1930s, with the first commercial mobile telephone service introduced by Bell in 1946. These devices were hardly what we'd call mobile today—some took up the whole trunk of a car, and others had to be carried on your back in a heavy bag.

Curve stitching is a form of string art where smooth curves are created through the use of straight lines. It is taught in many Junior High and High School art classes. I discovered it when my math students started showing me the geometric art they had created.

The "Zoombombing" trend is still strong on the Zoom video meetings service, despite security measures Zoom put in place to stop it. That's why it's up to you, as either a host or co-host, to be proactive about preventing Zoombomber harassment, as well as stopping it whenever it slips through the cracks.

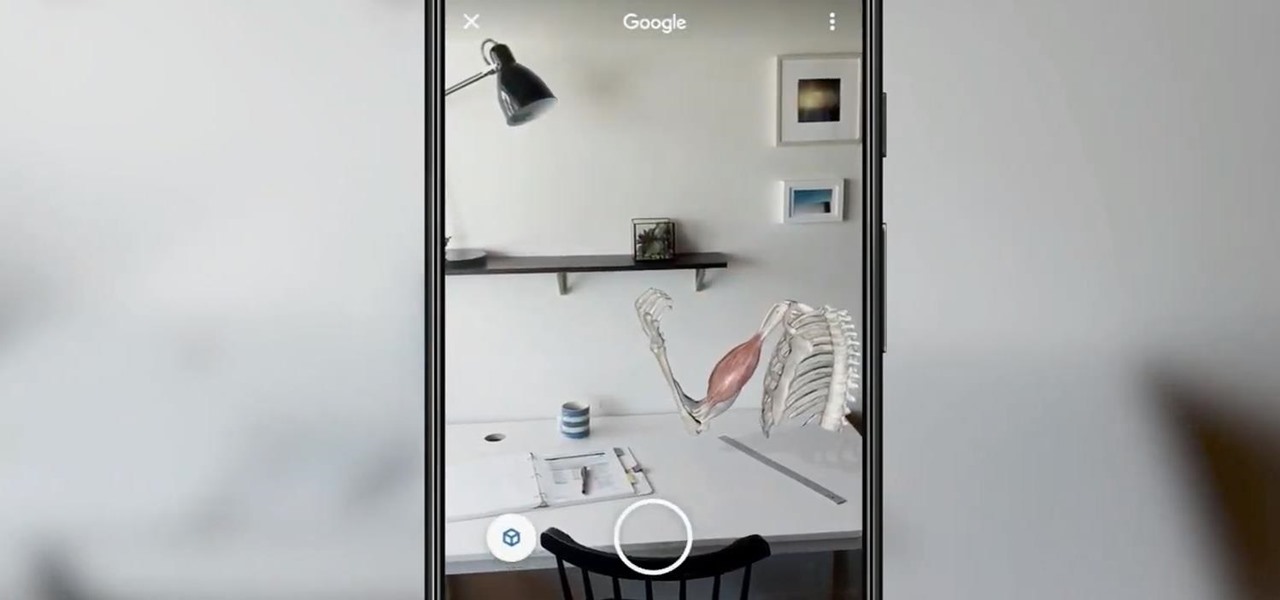
Lions and tigers and bears are just a few of the animals that Google users can now bring into their physical environments.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

The first mobile augmented reality app out of the gate with support for Magic Leap One Creator Edition is Thyng, who is planning to release the headset version of the app later this year.

If you have yet to receive your invitation to next weekend's royal wedding in the UK, then you can still experience part of the pomp and circumstance in augmented reality courtesy of ABC News.

The future of augmented reality isn't on your smartphone or face, it's in the everyday items all around us. At least that's the belief of Gordon Meyer, the vice president of marketing at New York-based startup Lampix.

Moviegoers who arrive at the theater early are no longer a captive audience for the ads, trivia, and miscellaneous content that precede the movie trailers than run before the feature presentation, as the ubiquity of the smartphone has become the preferred distraction for early birds at the theater.

When security firm Zimperium discovered Android's biggest security risk in years, it sent shock waves through the ecosystem. As a result, Google, LG, and even Samsung decided to change the way they issue updates to their devices, by pledging to release monthly security patches to plug up loopholes exactly like this one. Yeah, it's that big of a deal.

If Google hasn't already demonstrated that it is serious about augmented reality, then it made it abundantly clear at the Google I/O keynote on Tuesday.

Users of Epson's smartglasses can now tell their devices to "talk to the hand" when it comes to passwords and authentication.

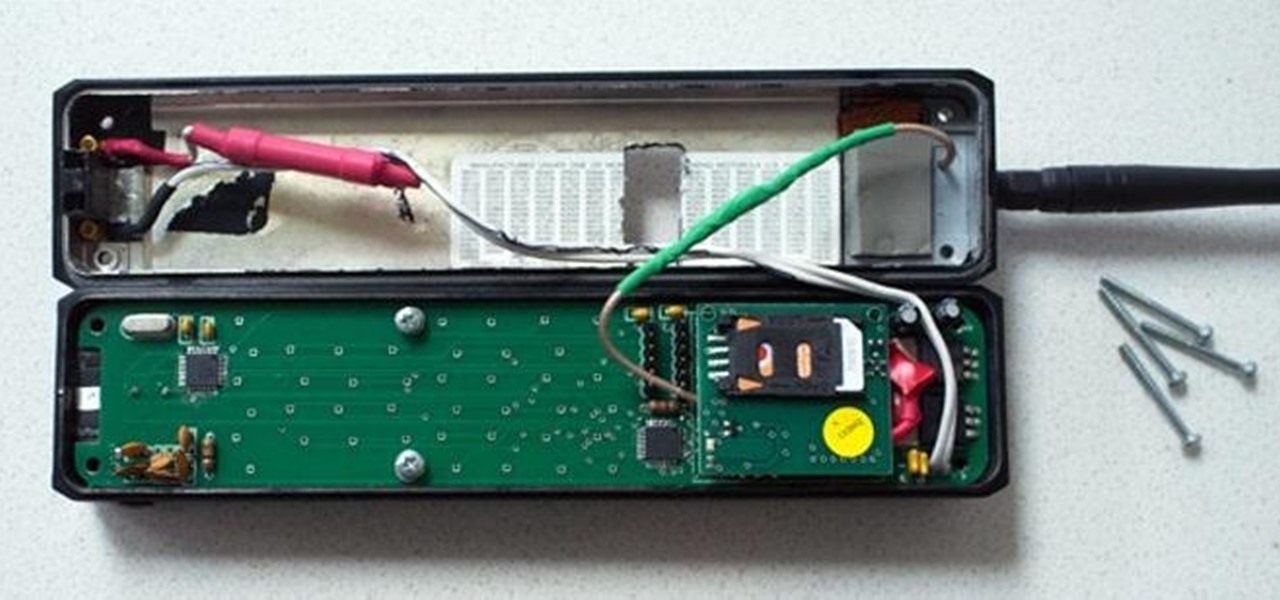
Welcome back, my hacker wannabees! Most of my recent posts have addressed using Metasploit’s Meterpreter and what we can do once we have embedded it on the victim’s system. This includes remotely installing a keylogger, enabling the webcam, enabling the microphone and recording, disabling the antivirus software, among many other things. The list is almost unlimited.

Welcome back, my tenderfoot hackers! In some of my past articles, I've shown numerous ways of embedding a listener/rootkit on a remote system, including buffer overflows of the operating system, getting the victim to click on a link to our malicious website, and sending a malicious Microsoft Office and Adobe Acrobat file.

Welcome back my fellow hackers! In my last few articles, I've concentrated on what is called a listener, which is basically the same thing as backdoor and rootkit, only "listener" sounds much less malevolent than the other two terms.

Now that Microsoft has squarely focused on the enterprise market with the HoloLens 2, it appears Lenovo is content to play follow-the-leader with its new augmented reality headset.

A week after the L.E.A.P. Conference, our cup of Magic Leap news continues to floweth over, with the company's content chief giving us some insight into the company's strategy, and Twilio sharing what its virtual chat app looks like.

It doesn't matter how cool or groundbreaking a particular technology is, if it doesn't offer the promise of big returns on investments, you'll have trouble drawing interest from both Silicon Valley and Wall Street. That's why we're increasingly seeing existing augmented reality players doing everything they can to focus in on revenue generation, which was the message coming from Snap Inc. this week.