This is a video tutorial in the Home & Garden category where you are going to learn how to use an electrical box extension. Bob Schmidt shows how to use an electrical box extension during remodeling; when adding drywall, tile or wood over existing surfaces. For this you will need a PVC box extension which is designed to fit over the box that is already embedded in the wall. It extends out of the wall which will be covered by the layer of tile or drywall. Disconnect the power source to the plu...

In this tutorial, we learn how to use quotes in an essay. When using a colon, you will set up the quote, then present it as proof of what you have just said. Note that the phrase before the quote could stand on its own as a sentence. For partial quotes, remember when summarizing to embed the author's words in your own sentence. If you take away the quotation marks the sentence should flow like you wrote it. When using commas with quotes, you can introduce the quote with an introductory phrase...
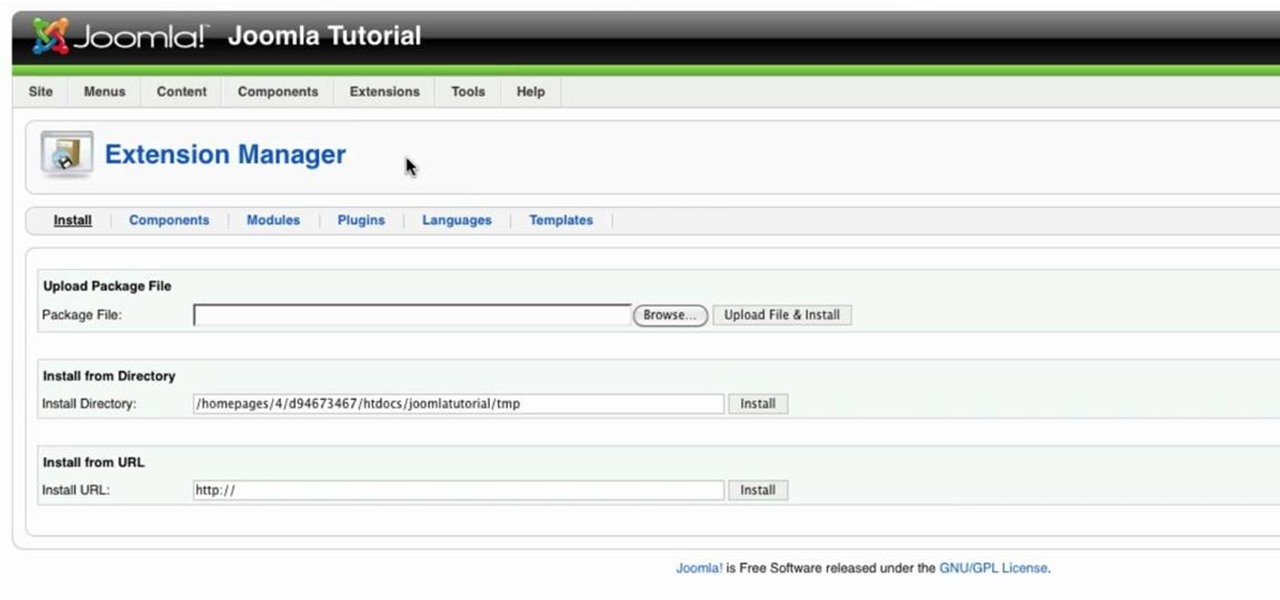
Go to your admin page of the Joomla and click on extensions and choose install/uninstall and there you can install your extensions. First you need to know what is extension, there are three type of extensions, one is called component, second is module and third is plug-in. components are like stand alone or application, like anything from video gallery, forms etc.

This video tutorial is in the Home & Garden category which will show you how to contain your sheep with hurdles. For this project you will need thin and long wooden staffs. This can also be done with bamboo. Split the wooden staffs in half. Take a heavy piece of timber and make holes in it at regular intervals. Place the timber at the boundary of the area where you want to contain your sheep. Then drive one unsplit wooden staff through each hole in the timber so that the end of the staff gets...

When learning any new dance, it's important to take your time and constantly practice any new steps you learn in order to embed it into your very mind. As dance intructors always say, practice makes perfect. So when watching this tutorial, remember those words as you are attempting to dance the triple-step for swing. It usually consists of a side step, then a together step, followed by a side step again. It seems pretty easy to do, but you never know. So good luck, pay attention, and enjoy!
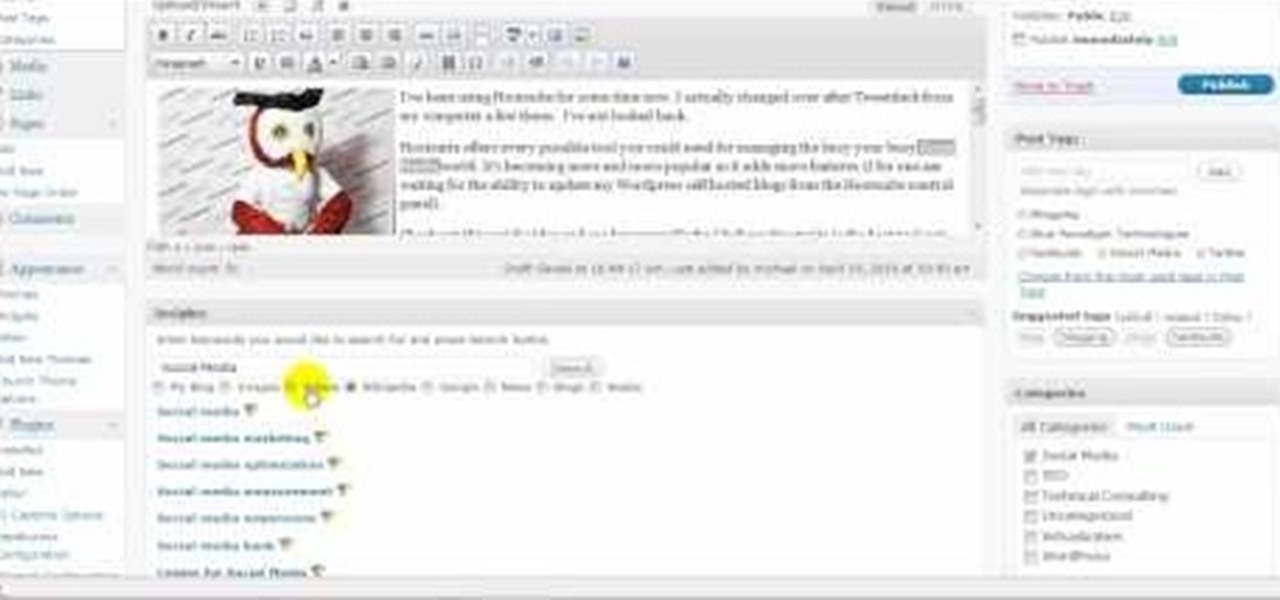
See how to insert a hyperlinked reference to a Wikipedia article in your blog post or page with this free video blogger's guide. Every version of WordPress brings with it new features, new functions and new ways of doing things. Fortunately, the very same technology that allows an open-source blog publishing application like WordPress to exist in the first place also makes it easy for its users to share information about the abovesaid things through videos like this one. Take a look.

This tutorial shows you how to create a picture rotating slideshow, that fades in and out using Adobe Flash. Using optimized embedded photos is not the only way, but it is a very basic and easy method to create a slideshow picture rotator. Whether you're new to Adobe's popular Flash-development platform or a seasoned web developer looking to better acquaint yourself with Flash CS3, you're sure to benefit from this free software tutorial. For more information, including detailed, step-by-step ...

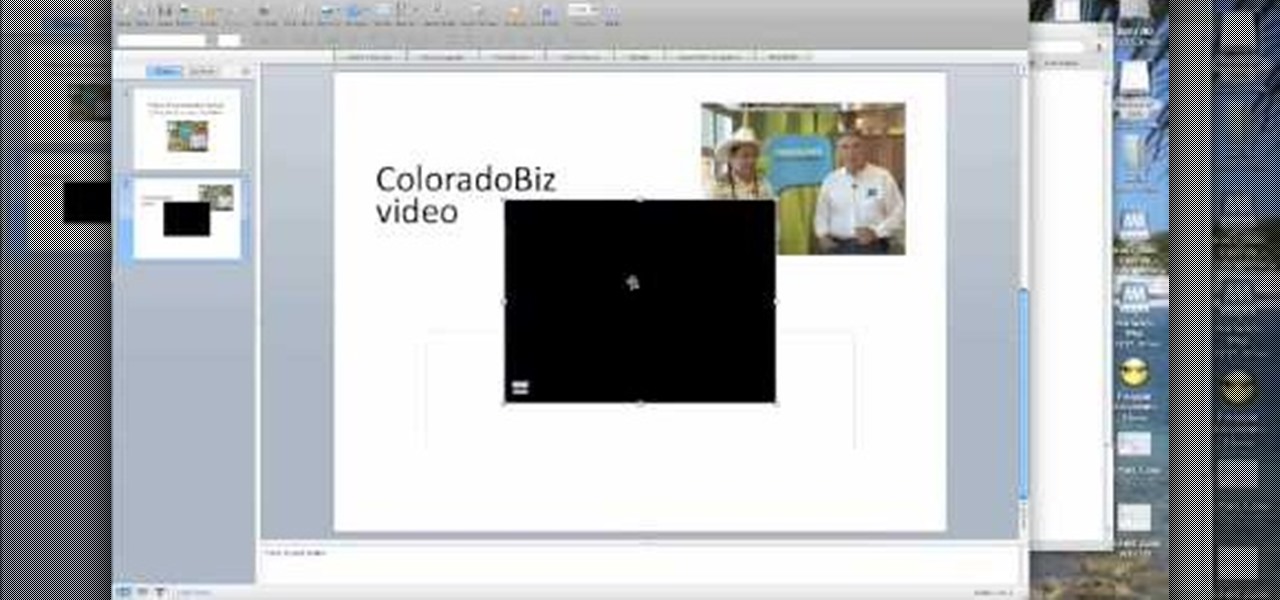
One of the best ways to get your point across during a PowerPoint presentation is to use video. This way, you can not only tell your classmates, students or coworkers about your subject with words and images, but you can actually show them with real footage.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to backup Wii games to SD to play in HD.

Wondering how to create an app bundle in Mac OS X? In this two-part video tutorial series, you'll learn how to create an application that is completely self-contained and is drag-and-droppable/relocatable. Frameworks, PlugIns, and Resources are embedded in the .app bundle, thus avoiding the need for installers and avoiding issues like dll-hell. There is also a quick demonstration on how to enable Universal Binary building at 15:46. Take a look!

Take a look at this instructional video and learn how to fit a projected image onto a target surface with Johnny Chung from Carnegie Mellon University. Typically, you'd need to use a screen to be directly in front of the projector and at a very specific orientation to get an undistorted image. What this tutorial is trying to accomplish is to place a screen at any location that is convenient and then calibrate the projector onto the target surface. This technique is used to automatically disco...

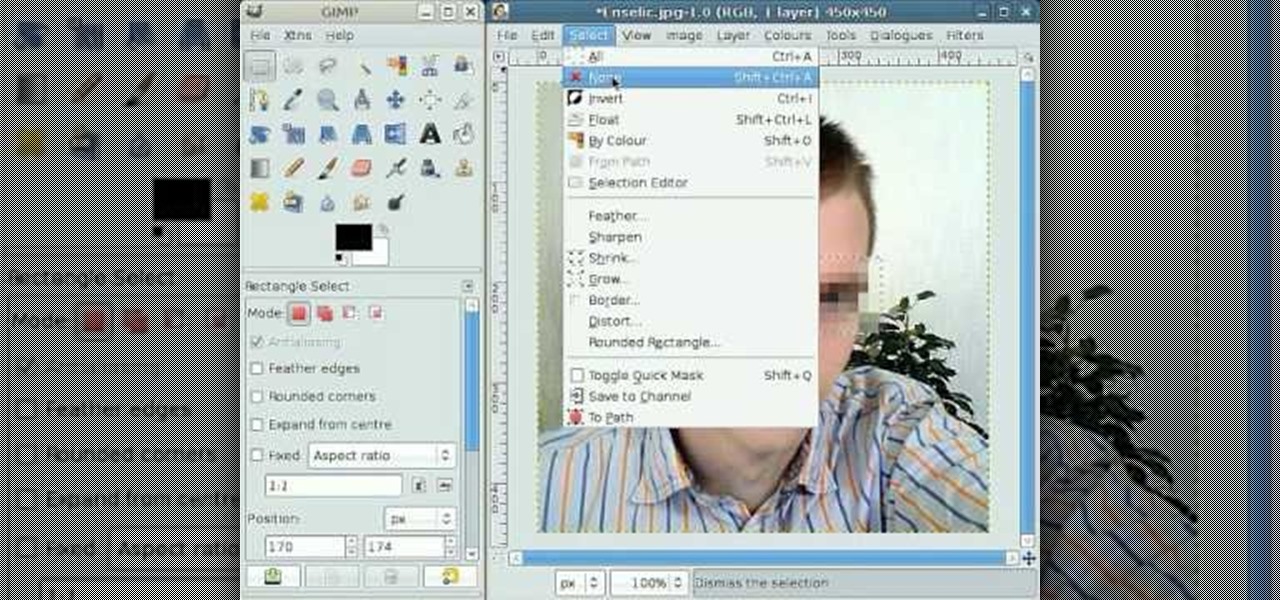
By following this tutorial you will learn the concept of selections in GIMP. Whenever he says "layer mask" he really meant "selection mask".

Scrabble Bingo of the Day: GEOPHAGY [n]

Welcome back, my tenderfoot hackers! One key area on the minds of all hackers is how to evade security devices such as an intrusion detection system (IDS) or antivirus (AV) software. This is not an issue if you create your own zero-day exploit, or capture someone else's zero-day. However, if you are using someone else's exploit or payload, such as one from Metasploit or Exploit-DB, the security devices are likely to detect it and spoil all your fun.

Ever wondered how to make no bake cookies? Today you can learn how to make this very easy treat! Video: .

While it's easy enough to make yourself invisible on Snap Map, nothing is quite as private as not having a Snapchat account at all. Whether you're concerned about your privacy or you simply never signed up for the social media platform, Snapchat's web-based map is an easy way to check in on what's happening in your area and beyond.

Just a week after news leaked out about Intel's 2018 plans for smartglasses, the company revealed what the device looks like and how it works in a new video (bottom of this page) released on Monday.

Stop me if you've heard this one before: scan an image with your iPhone's camera and augmented reality content shows up.

If Netflix's $9.99/month has deterred you from signing up for its streaming service, you're probably looking for cheaper alternatives to stream movies and TV shows, like Crackle (free with ads) or Hulu ($7.99/month with some ads). And now there's a new option for you when it comes to movies—Paramount Vault.

Notes on iOS has never been a particularly great app due to a lack of overall features compared to other note-taking apps like Evernote or Microsoft OneNote.

Welcome back, my hacker novitiates! Eluding and evading antivirus software and intrusion detection systems is one of the most critical tasks of the hacker. As soon as a new exploit is developed and discovered, the AV and IDS developers build a signature for the attack, which is then likely to be detected and prevented.

Windows XP will always have a special place in my heart—it's the operating system I grew up on. It guided me through the glory days of AIM, Napster, and MySpace, but now it's dead. The OS that had been supported by Microsoft for twelve years officially lost its support on April 8th, 2014. Just like that, Microsoft has killed the beast, but for those of you who stubbornly refuse to cooperate, you can resurrect the dead. If you have Windows XP, this little known hack will get you further suppor...

Welcome back, my hacker wannabees! Most of my recent posts have addressed using Metasploit’s Meterpreter and what we can do once we have embedded it on the victim’s system. This includes remotely installing a keylogger, enabling the webcam, enabling the microphone and recording, disabling the antivirus software, among many other things. The list is almost unlimited.

No one can deny that Bashar Al-Assad’s regime has been responsible for violence. But in failing to equally acknowledge the fact that NATO-backed rebels have also carried out innumerable atrocities is not only dishonest, it represents a deliberate effort by the press to manipulate the narrative of unfolding events in Syria as a one-sided war crime rather than the truth – which is the fact that Syria is in a state of civil war.

Mud cake might not sound very good but it sure tastes great. Try out this fun cake for a birthday, a party or just because. This mix of rich chocolate, nuts and a fluffy marshmallow top is sure to brighten any day.

While Snapchat had a head start in making augmented camera effects popular on smartphones, Facebook has spent the past few years in hot pursuit, with no less than three apps offering mobile AR experiences, plus its Portal hardware lineup of smart home devices.

There might not be a better brand partnership for the speedy Sonic the Hedgehog character than a fast-food restaurant. For that matter, augmented reality is also the ideal technology for promoting a movie that features an animated talking rodent living life in the real world.

When it comes to web-based augmented reality, 8th Wall has emerged as one of the leading platform providers, and the company just cranked up its capabilities another notch for AR marketers.

The future of augmented reality isn't on your smartphone or face, it's in the everyday items all around us. At least that's the belief of Gordon Meyer, the vice president of marketing at New York-based startup Lampix.

Moviegoers who arrive at the theater early are no longer a captive audience for the ads, trivia, and miscellaneous content that precede the movie trailers than run before the feature presentation, as the ubiquity of the smartphone has become the preferred distraction for early birds at the theater.

By default, images embedded using external links will not automatically load in any emails that you get with ProtonMail. This is a security mechanism that can prevent malicious code from being executed on your system, but it can also be fairly annoying to have to manually load images in email after email.

Update 10/12: Since the event has now ended, we figured we'd update this page with a link to a replay version of the Google event. So if you missed any of the goodies or just want to give yourself a refresher, jump down to the "Where to Watch" section below.

The rumor mill surrounding the iPhone 8 is churning this week, and not necessarily in a good way. Yesterday, we learned Apple may be leaving the 3D camera out of the next big iPhone to keep the phone on schedule. Today, rumors allege the 10th-anniversary edition of Apple's smartphone may not ship with Touch ID embedded under its display.

Welcome back, my tenderfoot hackers! So many of you responded positively to my post about using the keylogger, as well as my post regarding turning on the webcam, that I decided that you might enjoy another similar hack. In this article, we will enable the audio recording capability on the remote system of your roommate.

RFID cards are becoming a fairly common way to purchase goods, but they're already widely used to pay fares on buses, trains, subways, and trolleys across various cities. TAP cards are quick and reliable, but it can be a real pain to remember to bring them with you, especially if you weren't planning on using public transportation that day. Luckily, an intrepid tinkerer at Adafruit has managed to find a way to embed an RFID card into her phone, something you're far less likely to leave at home.

Chris Davis with the Educational Technology Center shows us a few easy steps to putting YouTube videos in our Microsoft PowerPoint 2007 presentations. To start you'll need to have an active internet connection and you should have the developer tab in PowerPoint active. To do this go to the Office menu, PowerPoint options, popular and click show developer tab. Locate the hammer looking more control option button and scroll down to Shockwave Flash Object and click it. This allows you to draw a ...

XSS Shell is a cross-site scripting backdoor into the victim's browser which enables an attacker to issue commands and receive responses. During a normal XSS attack an attacker only has one chance to control a victim's browser; however, the XSS Shell keeps the connection between the attacker and the victim open to allow the attacker to continuously manipulate the victim's browser. XSS Shell works by setting up an XSS Channel, an AJAX application embedded into the victim's browser, that can ob...

C-SPAN is one of the best ways to get your news on the web. Watching their videos from their website will get you up-to-date on all of the new headlines, and it will always give you a history lesson with all of the past headlines. See something interesting while watching a C-SPAN video and want others to see it, too? C-SPAN makes it easy to clip the exact portion you want, and share it with friends or embed it on a website or blog. Just follow these instructions.

If you want a calendar of events on your website, or just want everyone to know what you do all day, this video is for you. Learn how to embed your Google Calendar in a webpage using Contribute software.

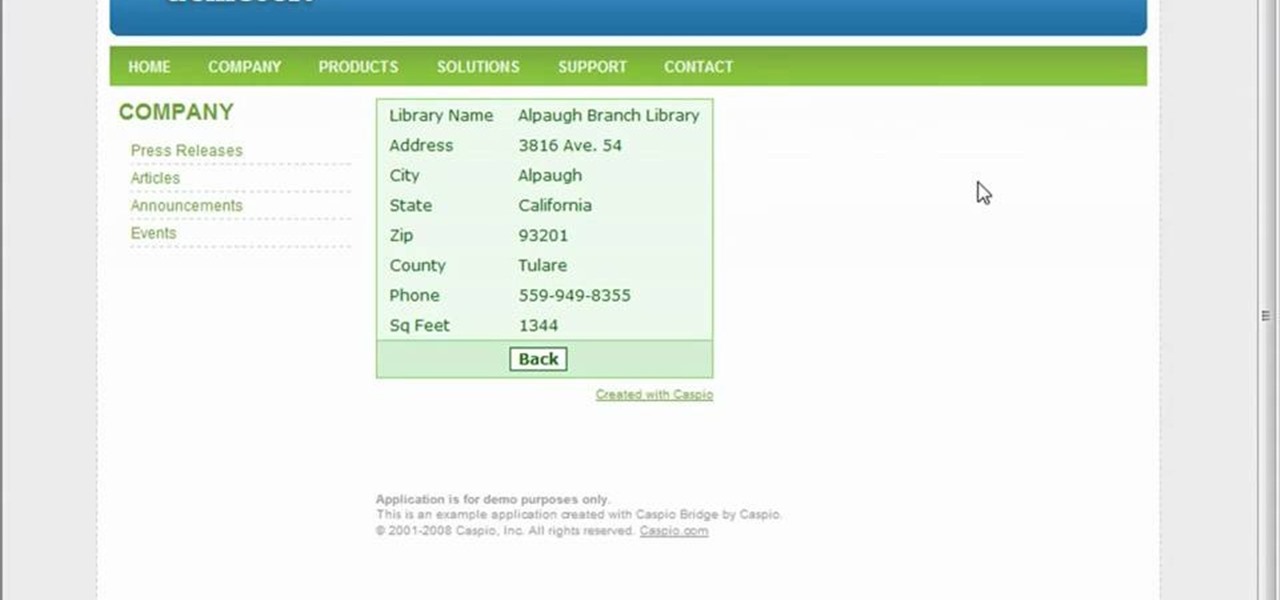
To start off the process of publishing your access database online we first look at a sample MS ACCESS database with typical formats and a online searchable application where users can search by library name or city and get details of the library. There are 3 steps to publish the database. The first step is importing data which can be done through clicking on the file menu and then click on import data through a Microsoft Access Database. Now select the file you want to import through the bro...