When the Samsung Galaxy S7 and S7 Edge came to market in 2016, they were universally praised as being the pinnacle of Android smartphone design, even topping Consumer Reports' smartphone ratings.

Considering how much smartphones cost in the first place, we're understandably reluctant to throw them out when we've bought a newer model. And this is probably the best practice, too, as there are many great uses for an old Android device.

Apple's MacBook line of laptops is quite famous for their extensive battery life, thanks to various technologies that Apple has utilized. However, all things must pass, and over time your MacBook's battery will degrade. Certain use scenarios can accelerate the degradation of the battery—from excessive usage to high temperatures to overloading the system—and this can all lead to the untimely obliteration of your battery.

It's been a while since I wrote up an article for this series but I did say that I'd be covering some WinAPI. So if you're interested in programming for the Windows platform, hop aboard and follow along.

Hello again, readers! In our previous crypter tutorial, we looked at how we could obfuscate our malware (or any program) by using a simple one-byte XOR key. In this quick tutorial, we will be looking at how a simple little tweak can create a better means of obfuscation. Let's get right into it!

Macs are generally highly power efficient due to, in part, the optimized sleeping schedule with OS X. Yet in certain scenarios, you might not want your Mac to go to sleep: downloading a huge file, reading a book, reviewing a spreadsheet, analyzing some content on the screen... the list goes on. To resolve this, you can go to System Preferences and mess with the settings, but this can be an annoying process if you need to do it often.

If you've been around computers long enough, you've probably heard the phrase "have you tried turning it off and on again?" This trick usually works because it forces your computer to empty out the contents of its RAM and disk caches when you restart.

Managing hard drives in Linux is crucial to understanding your system and its operation as well as understanding the system you are exploiting or conducting a forensic analysis on. Linux has numerous commands that can provide us with information, control, and management of hard drives, and in this tutorial, we will examine a number of the most important ones.

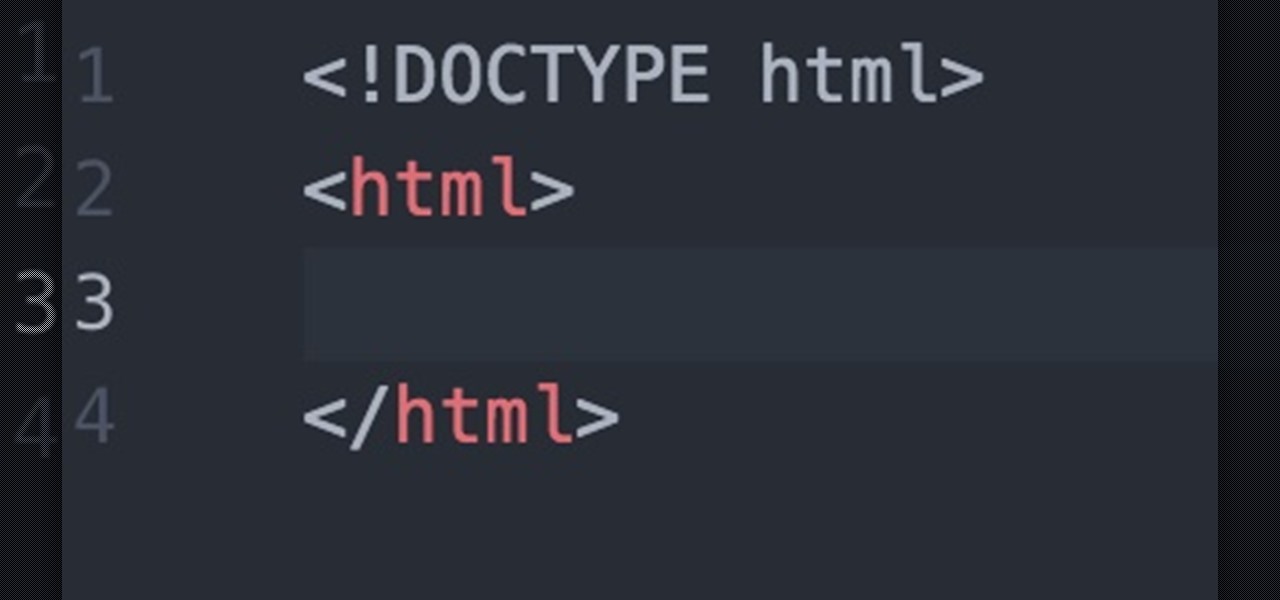
Hello fellow Null-Byters! In this "tutorial" we will be going basics of HTML. In the next tutorial, we will be going over CSS and then apply JavaScript.

Continuing this series, I am now moving on to the section, 'Anonymous'. Hope you are looking forward to read this.

Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of modules: exploits and payloads. Remember, Metasploit has six types of modules:

Welcome back, my fledgling hackers! Over the years, we have examined multiple ways to own, exploit, or compromise a system. On the other hand, we have not spent a lot of time on denial-of-service (DoS) attacks.

Although pasta is a remarkably simple dish, I find it to be one of the most aesthetically appealing foods. The noodles—especially thicker iterations, like linguine and fettuccine—are graceful and luxurious. Add in some sauce coating the noodles, and a sprinkle of Parmesan or a drizzle of olive oil, and pasta single-handedly reminds us of a basic tenet of cooking: sometimes keeping it simple is the perfect way to go.

Welcome back, my tenderfoot hackers! One of the issues we often encounter with Metasploit is how to add new modules. Although Rapid7 (Metasploit's owner and developer) periodically updates Metasploit with new exploits, payloads, and other modules, at times, new modules appear that are not added to the Metasploit repository.

The fridge is the heart of the kitchen; take it away, and the whole operation falls apart. Yet, despite this, the fridge is also one of the most overlooked appliances in any kitchen. Most people organize their drawers and shelves for maximum efficiency, while many others buy islands simply to make their culinary playground more space efficient. Heck, I know some people who have passed up on otherwise great apartments because the counter space simply wasn't large enough.

Welcome back, my fledgling hackers! With this first article, I am initiating a new series intended to convey to my readers the skills necessary to develop your own exploits.
This how-to is for everybody who faced the problem of intercepting personal data sending through the Internet and is looking for fast and secure method to protect his activity in the global network.

Welcome back, my tenderfoot hackers! As you know, DNS, or Domain Name System, is critical to the operation of the Internet. It provides us with the ability to type in domain names such as www.wonderhowto.com rather than the IP address. This simple service saves us from having to memorize thousands of our favorite website IP addresses. Instead, we simply type in a domain name to retrieve the website.

Security is a priority for many when they first set up their mobile devices. Nobody wants to have a stranger or nosey friend go through their phone and discover risqué photos or embarrassing text messages. These days, the closet is gone—everyone keeps their skeletons in their phones.

Welcome back, my hacker novitiates! In previous guides, we have used one of the most powerful hacking platforms on the planet, Metasploit, to perform numerous hacks. They ranged from exploiting Windows XP and Windows 7/8 vulnerabilities, to installing a keylogger and turning on a webcam remotely. We have even been able to save the world from nuclear annihilation, see if our girlfriend is cheating, spy on suspicious neighbors, evade antivirus detection, and more.

Welcome back, my novice hackers! We've done a number of tutorials using one of my favorite hacking tools, Metasploit. In each of them, we've used the msfconsole, which can be reached through either the menu system or through simply typing "msfconsole" from the terminal.

A rooted Android device means we're on our way to some truly amazing customization options. But there may be a few steps left to completing that journey, and a major one is installing a custom recovery.

Russians are well known for their knack at documenting exciting and horribly beautiful events on the go, from insane car accidents to attempted insurance fraud and even a superbolide meteor streaking across the sky.

How to easily build a raised garden bed out of wooden pallets for free! …Well almost free. Building a raised vegetable garden with pallets or reclaimed wood is a really rewarding experience. The garden bed idea out of pallets came about from the fact that l wanted to build a rustic looking raised garden bed. A vegetable garden bed that not only provides delicious food, but looks good at the same time. The recycled wood has come from hardwood timber pallets that have been sourced totally FREE ...

2 + 2 = 4. That's about as much math as I can handle without a calculator on a daily basis. I literally hate doing math more than anything in life, mostly because I'm not good at it—and I hate doing things I'm not good at.

If you're an avid PC gamer, then you're probably well familiar with the term overclocking, which is basically just tweaking your computer hardware to run faster than it was originally intended.

Yes, you read that right—you can now get Google Maps back on your iPhone again. It may not be officially replacing Apple's notorious Maps app, but it sure is a sight for sore eyes.

You're probably sharing a ton of information on your iPhone with other people, apps, and services without really realizing it. Now there's a new tool to show you just how much, and it can be an eye-opener as well as a fast way to manage sharing permissions and review your account security.

Thanks to numerous smartwatch deals this holiday season, many people are receiving their first one. But what exactly can they do? In regards to fitness, quite a lot. With a growing list of sensors and software updates, these small devices can be the very thing you need to ultimately reach your fitness goals.

One of Android's biggest strengths is its flexibility. There's usually more than one way to perform the same task, which makes it easy to find an alternate method that works better for you. Android also has some hidden features that newer users might not be aware of, so we made this list to highlight lesser-known tips and tricks.

In our first part on software-defined radio and signals intelligence, we learned how to set up a radio listening station to find and decode hidden radio signals — just like the hackers who triggered the emergency siren system in Dallas, Texas, probably did. Now that we can hear in the radio spectrum, it's time to explore the possibilities of broadcasting in a radio-connected world.

Beginners luck is a phrase I have always hated. But really, beginners luck comes down to not letting your experience in something get in the way of the idea.

A dislocated shoulder involves movement of the ball of the humerus away from the ball and socket joint. Ninety-five percent of the time, it will come out anteriorly when an individual's arm is forcefully pushed backwards and rotated in such a way that the ligaments in the front of their shoulder tear and the ball will pop out the front of the shoulder. This is a very common injury seen in contact sports. Learn how to diagnose and treat a dislocated shoulder in this medical how-to video.

Building a lean-to shelter can be the difference between survival and not coming home. Learn to build an emergency shelter with this free wilderness survival video series.

Find out how everything in a chemistry lab works, from pipettes to burners to recrystallization to storage. You'll get precise instructions on how to work and perform certain scientific duties in the chem lab, whether it's chemical or just ordinary high school science.

In this music recording software video tutorial, learn how to use one of the latest programs for bands and musicians: Apple Logic Pro. This software allows the user to record a song from beginning to end, bounce tracks, master, and do a final mix down to CD, mp3, and other desired formats. Our expert will walk you through the operations you need to understand to create audio tracks, lay down drums, keyboard, and a bass part, edit and master them, and mix to a final song

In these music studio recording and production videos, learn how to use a 4-track reel to reel tape recorder to capture your vocals, guitar parts, drums, record songs, or even make a demo CD. Our expert will walk you through the operation of a fairly simple reel to reel machine in several steps, including the basic and advanced functions, rear components, using mics and connecting to other mixing boards, recording on four different tracks, mixdown, bouncing tracks, and final tips for masterin...

In this music recording software video tutorial, learn how to use one of the latest programs for bands and musicians: Apple Logic Pro. This software allows the user to record a song from beginning to end, bounce tracks, master, and do a final mix down to CD, mp3, and other desired formats. Our expert will walk you through the operations you need to understand to create audio tracks, lay down drums, keyboard, and a bass part, edit and master them, and mix to a final song. This series is a grea...

In this music recording software video tutorial, learn how to use one of the latest programs for bands and musicians: Apple Logic Pro. This software allows the user to record a song from beginning to end, bounce tracks, master, and do a final mix down to CD, mp3, and other desired formats. Our expert, Bill Macpherson, will walk you through the operations you need to understand to create audio tracks, lay down drums, keyboard, and a bass part, edit and master them, and mix to a final song. Thi...

In this video clip series, our expert will demonstrate the ways in which you prepare a welding machine, manage voltage and energy levels as well as techniques for the different modes of operation and equipment. Learn how to use the weld supplies, tig, wig and arc welds and more. Techniques such as the “Push and Pull” are explained and demonstrated, as well as basic information such as setting up the welding machine and an introduction to the gases used for welding are included.