Welcome back, my novice hackers! One of the most common questions that Null Byte readers ask is: "How can I evade detection by antivirus software on the target?" I have already talked about how AV software works, but to obtain a deeper understanding, what better way is there than opening up and dissecting some AV software?

Welcome, in this tutorial we shall we looking at creating a safe(r) way to back up your important files. The contents we will be covering are as follows;

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.

Welcome back, my rookie hackers!

Welcome back, my greenhorn hackers! Digital forensics and hacking are complementary disciplines. The better you are at digital forensics, the better hacker you are, and the better hacker you are, the better you are digital forensics. Unfortunately, few people in either profession cross these discipline lines.

Welcome back, my aspiring hackers! Although this article may have been better placed first in this series, I doubt that anyone would have read it when just starting out studying Linux. Now, that you are well into your Linux studies and have some familiarity with how it operates, I'd like to take this moment to explain the philosophy around the Linux operating system.

Welcome back, my budding hackers! People often ask me, "Why are you training hackers? Isn't that illegal?" Although I usually give them a short version of this post, there are MANY reasons why YOU should be studying hacking.

MacBooks are built for creation and creativity. They're built to withstand our careers, our hobbies, and our everyday use. I use mine every day, and there's nothing I'd recommend more for computing needs.

The new LG G3 is the latest Android flagship-level device to be released this year, and it's ready to give the Galaxy S5, HTC One M8, and the OnePlus One a run for their money. Sporting a gorgeous 5.5-inch QHD display, 3GB of RAM, and a huge 300mAH battery, the device looks great and has tons of power to boot.

Welcome back, my tenderfoot hackers! I have written many tutorials on hacking using Metasploit, including leaving no evidence behind and exploring the inner architecture. Also, there are my Metasploit cheat sheets for commands and hacking scripts.

The long rumored and recently leaked Amazon phone has finally been unveiled, and in the interest of branding, continues down the Fire line—the Amazon Fire Phone. You can check out the full reveal here (warning: it's long), but I'll take you through all the features that sets this device apart from the rest. Before we get into that though, let's check out the specs:

When you're using vacuum power, moving water, or compressing air, it's more than likely being done with some sort of pump. I'll be needing a pump for some of my future projects, so in this tutorial, I'll be showing you how to make your own customizable PVC hand pump that will let you do all three.

Rooting, bootloaders, custom ROMs, CyanogenMod, ClockworkMod... it's all pretty confusing, isn't it? You're not the only one having trouble with this. Many users in the Nexus 7 SoftModder forum have been scratching their heads at these many terms.

Video: . Optimize your Marketing with a Mobile Website

Here's how to make dry-ice at home, or wherever you feel like it! All you need is a pillow case, and a CO2 fire extinguisher.

Living in Los Angeles has taught me one thing—parking is a luxury. If you are lucky enough to find street parking anywhere near your desired location, do not pass it up thinking you will get an even closer one. It does not exist. Looking for free parking? Get real. You can't even park at a busted meter in Los Angeles, despite state law saying otherwise. Now, finding a good parking spot is not just relevant for Los Angeles, but for other large cities and any other crowded areas, be it a shoppi...

Your days as an ordinary Muggle are over — as long as you have an iPhone. With just a word or two, you can use your iPhone and newfound Muggle-born powers to cast spells or utilize charms just like Harry Potter and team. Only your "wand" is from Apple, not Ollivanders in Diagon Alley.

The beginning of autumn has delivered a number of new augmented reality developments, and we're on top of it.

On Friday, the Tokyo Olympics finally kicked off after massive delays and complications due to the pandemic.

With Samsung's One UI 3.0 update, the main on-screen volume slider has a little menu button on the top of it. Tapping this will expand the slider into a full-blown volume panel, complete with controls for all of the various types of sounds your Galaxy might make. Standard stuff, really, but there's more to it.

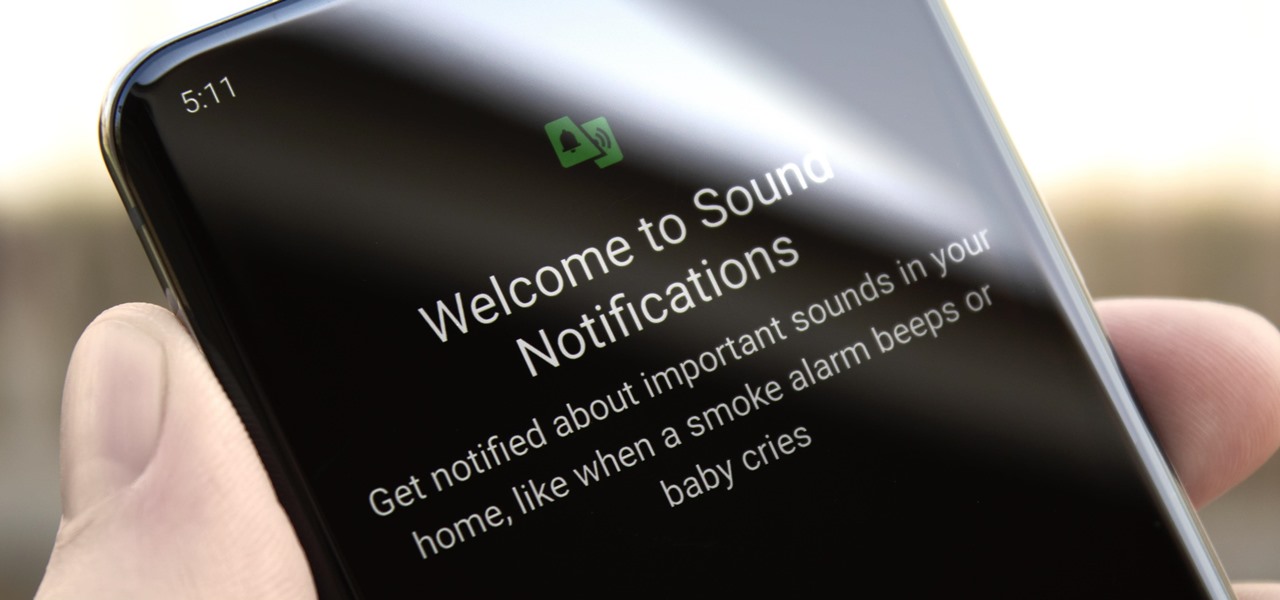
You don't have to be hearing impaired to appreciate one of Android's best audio accessibility features. This one can notify you when a baby is crying, a smoke alarm is going off, or when various nefarious sounds such as breaking glass are heard.

In a departure from Apple's newer iPhone models with Face ID technology, the 2020 iPhone SE goes back to the old days where the Home button ruled, and Touch ID was the biometrics method. But if you've never owned an older iPhone with a Home button, something as simple as shutting down and restarting the iPhone SE could elude you.

It seems like each day our phones become more integrated into our lives. School, work, shopping — so many tasks either require a phone or heavily benefit from one. But our phones are a double-edged sword that can easily distract us and harm our mental health as well.

If you're ever faced with a situation of handing over your iPhone to law enforcement (or getting it taken forcibly), whether by the police, feds, or court system, there are things you can do to prevent them from getting access to all that potentially self-incriminating data. And it takes less than a second.

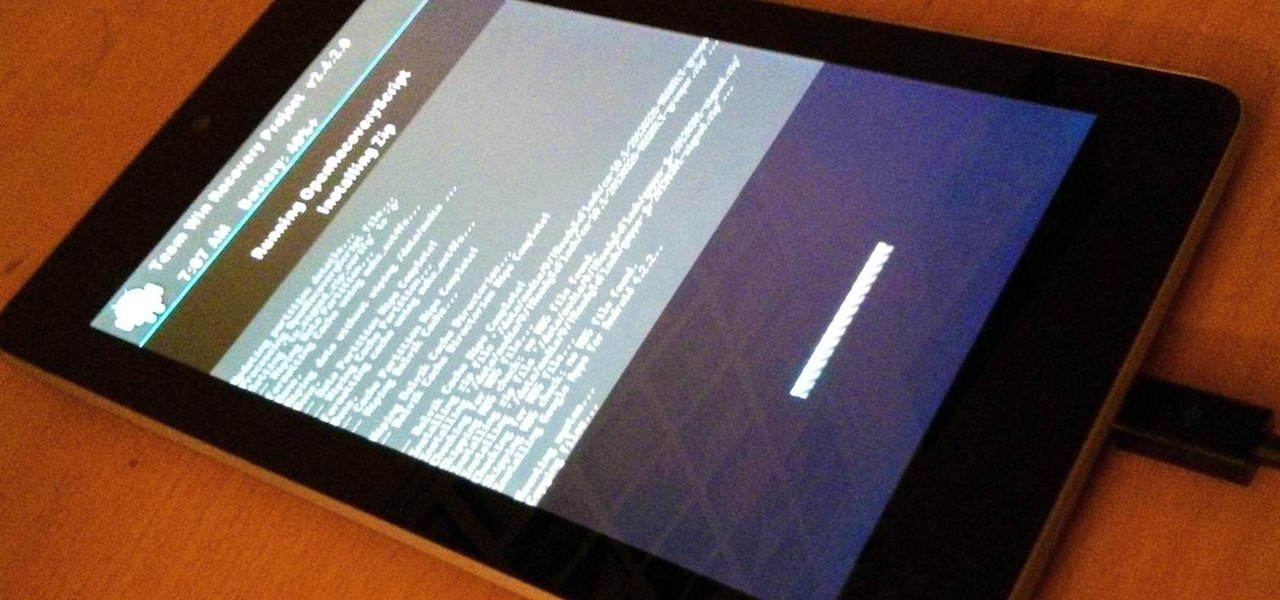
When flashing files through TWRP, ADB, or Fastboot, there's a slight chance for things to go wrong. Whether it's user error related or something else entirely, it's always good to have a backup plan. In most cases, you'll be dealing with a semi-brick or soft-brick, which can usually be solved by wiping the data of the device using TWRP. However, it can be more severe than that in some cases.

The iPhone XR has touched down alongside the XS and XS Max, and it utilizes tried and tested materials found on the iPhone 8, while being molded in the same vein as the iPhone X. The budget-friendlier flagship comes with its own set of design elements to set it apart from its more expensive brethren, but is powered by the same SoC, making it is a solid choice if you're thinking of upgrading.

A clean slate may be just what your Apple Watch needs. Whether you want to start fresh, wipe all your personal data, fix buggy issues, let someone borrow it, sell it, or get back in after you forgot your passcode, resetting the Watch back to factory settings is pretty simple, and you can do it with or without your iPhone.

When your iPhone is being sluggish, one thing you can do to get performance back up to snuff is clear the device's random access memory. It's not a publicized feature from Apple, but it's there nonetheless. And while it's easy enough to utilize on iPhones with Home buttons, the iPhone X is a little trickier.

When traversing the web, you'll regularly come across websites that require you to create an account. With the majority of these accounts, protection is limited to a simple password. Despite this, many people are still using weak passwords such "123456." For these reasons, you really need a password manager, and our research has shown that LastPass is still your best bet.

You may have seen news reports over the last two days detailing a major security flaw in virtually all smartphones. The devices that are at risk are not limited to either iPhone or Android — all of us are affected. If you want to make sure your smartphone and its data stay secure, there are a few steps you can take.

Just days before the release of the first image of the Magic Leap device, the company's CEO, Rony Abovitz, knew that the biggest moment of his life was about to unfold the following week. But instead of hunkering down in the Florida-based confines of the company's skunkworks, he instead decided to deliver a speech to the public about, what else, the future.

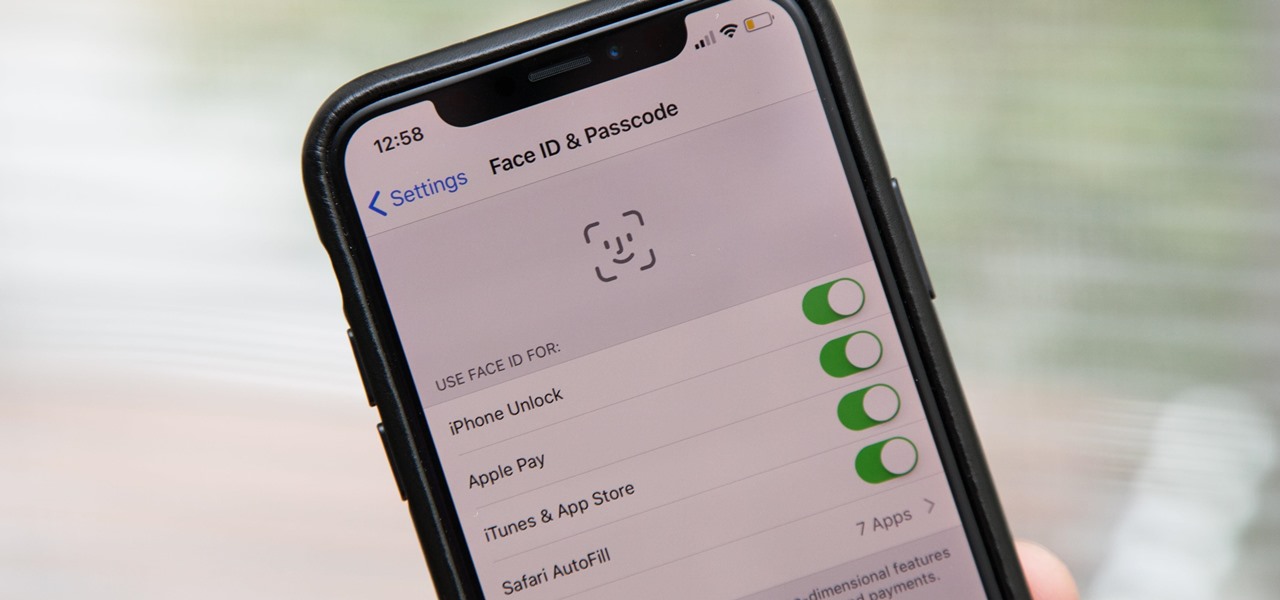
Aside from the second-generation iPhone SE, all new iPhone models since the iPhone X have had Face ID instead of Touch ID as the biometric authentication technology. While Touch ID can be touchy, Face ID is not without its own issues. If you can't get Face ID on your iPhone to recognize your face and unlock your iPhone, there are plenty of things you can try to get it working again.

Some of us woke up at the KRACK of dawn to begin reading about the latest serious vulnerability that impacts the vast majority of users on Wi-Fi. If you weren't one of those early readers, I'm talking about the Key Reinstallation Attack, which affects nearly all Wi-Fi devices.

Regarding foodborne pathogens, eating fish is not as hazardous as it was a few years ago — but if fins are on the menu, it's good to have a heads-up about what's good and what's bad these days.

To much of the United States, Zika seems like a tropical disease that causes horrible problems in other countries but is nothing to be worried about stateside. It may make you rethink your beach vacation abroad, but not much more than that. However, if you live in Florida or Texas, the possibility of getting a Zika infection where you live is real — and local outbreaks are more and more a possibility.

If you somehow forgot the pattern, PIN, or password that locks your Android device, you might think you're out of luck and are destined to be locked out forever. These security methods are hard to crack by design, but in many cases, it's not entirely impossible to break into a locked device.

Barbecue season: it's the perfect time to play with fire, produce your best burger ever (until next year, that is), and find even more ways to make beer a part of your daily life. However, even a grilling badass occasionally gets stumped by minor BBQ problems. No worries: We've got solutions!

We've all been there. You can't decide what you want to eat and, even more confusingly, you want two distinctly different things, whether it's sweet and salty, Chinese and, well, cheese. Chances are when you're in this state of indecision, you also want to make this mythically satisfying meal really, really fast.

My phablet has incredible battery life, but that doesn't mean I wouldn't like it to last even longer. Unlike the Samsung Galaxy S5, the Note 3 does not come equipped with Ultra Power Saving Mode, which can keep the phone running for another 24 hours with only 10% power remaining.

It may seem impossible to win an argument against an irrational person, but it turns out the tried-and-true techniques that hostage negotiators use against hostage-takers work surprisingly well in everyday situations. You may not ever deal with a real hostage situation personally, but life is full of negotiations with unreasonable people, and those conversations don't always have to end in rage or disappointment. The mental techniques that professional hostage negotiators use can help both pa...