Most of the animated characters and animals we've seen in augmented reality are still fairly basic in terms of visual fidelity. And because many are still impressed by simply seeing 3D figures properly scaled and tracked alongside real-world objects, this approach has worked ... so far.
Apple CEO Tim Cook told us that augmented reality would change everything, and now we have a better idea of exactly what he meant.

All the Driverless news you need to know from the past 24 hours, bundled together in a tightly written package, about Uber, London delivery services, capital investments, and kangaroos.

Google's Allo is still a work in progress, but the innovations to the chat and messaging app just keep on coming. The latest update rolling out now includes chat backups and a group incognito feature that we're very excited about.

It always looks different when it's not about you. The Internet is our world's Alterego. Those many bits don't really make sense unless we want them to be valuable, to mean something.
Welcome back Hackers\Newbies!

We're living in uncertain times. The sudden outbreak of the novel coronavirus and subsequent self-isolation of roughly half the world's population has led to a massive reorganization of the economy, countless layoffs, compromised security networks, and a variety of other significant disruptions that will forever alter the landscape of our daily lives.

There have been enough music artists releasing Snapchat AR experiences over the past week to fill a small festival. Count them with me: Bruno Mars. Gucci Mane. Kodak Black. Missy Elliot. Imagine Dragons. Panic! At the Disco.

Years ago, in 2013, Occipital introduced its original Structure Sensor for iOS, a mobile 3D scanning device for measuring three-dimensional objects. Soon after, in an unrelated deal, Apple acquired PrimeSense, the company that made one of the components for Occipital's scanning device.

If online retail is war (and who says it isn't), then CGTrader is prepared to arm its allies with augmented reality ammunition.

While privacy and security are cornerstones of Apple's ecosystem, your iPhone isn't bulletproof. Creating a strong passcode will protect you from most threats, but there exist tools that can break through even the toughest passcodes via the Lightning port. Luckily, Apple has implemented a new security feature to disable your Lightning port and keep your data safe and secure.

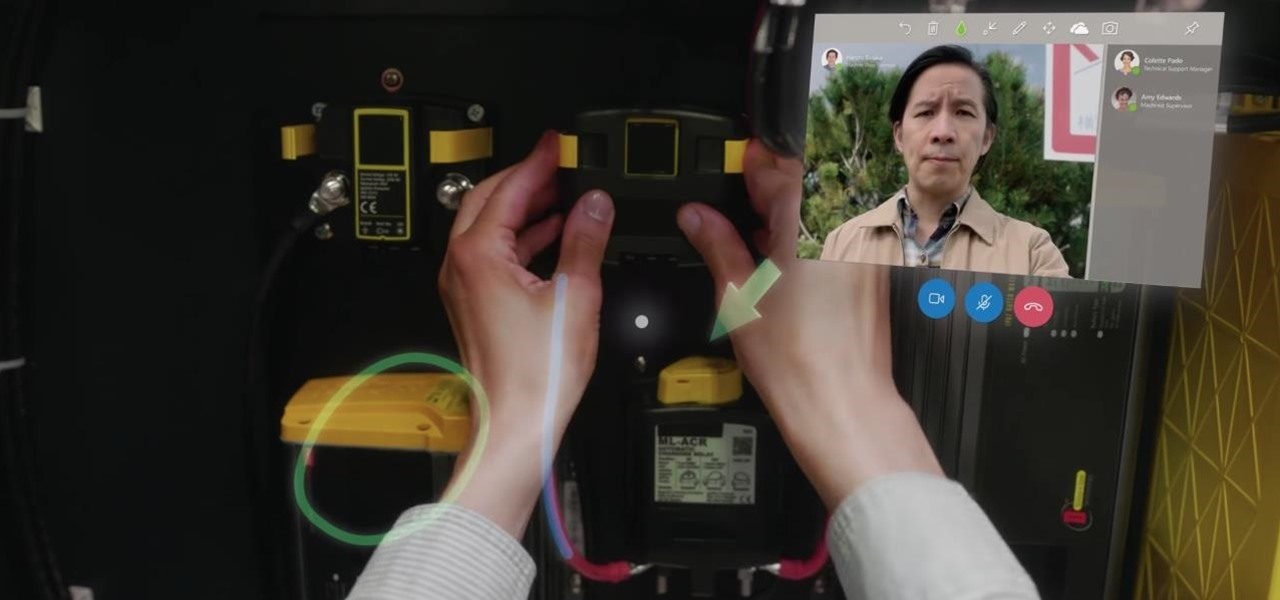
On Monday, at its annual Build developer conference, Microsoft revealed two new apps for the HoloLens apps.

Noted poet T.S. Elliot once wrote that "April is the cruelest month." But Magic Leap might argue that March is the most miserable, as the Ides of March brought more legal woes to augmented reality startup. Elsewhere, its closely-held branding secrets have been spilled by way of the US Patent and Trademark Office (USPTO).

For a company who hasn't released a product and has a reputation for being secretive, Magic Leap sure has a tendency to make waves. Over the past few weeks, they've refreshed their website design, released an abstract YouTube video, and announced a partnership with Madefire to offer mixed reality comics on its device whenever it launches. Next, they are gearing up for another round of funding.

Mobile apps themselves are not always the end product or service for generating revenue. More often, they are deployed as tactics within a larger marketing or public relations strategy.

While fully closing apps on your iPhone can keep it running at peak efficiency since it frees up memory and stops background refreshing, it's most critical when dealing with unresponsive apps. If you have an issue with a certain app, you can just force-close it instead of rebooting.

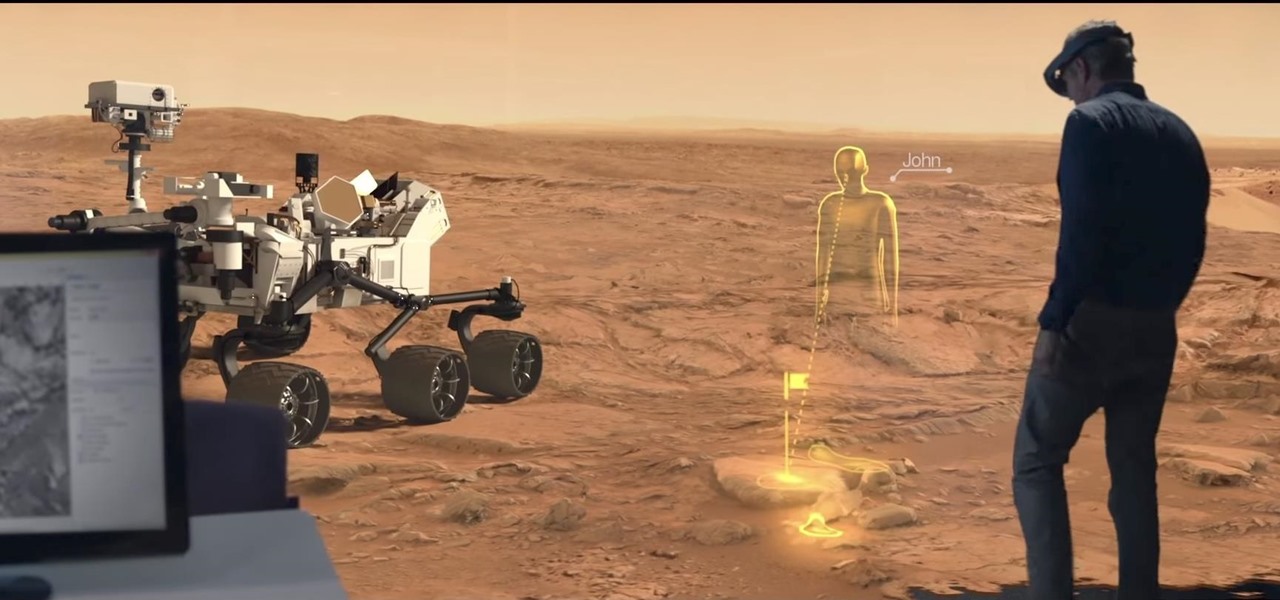
Apple likes to play their cards close to the vest, don't they? The iconic company doesn't usually reveal much about their projects until it's time for an official announcement. But sometimes ... They can't stop a leak of information from happening, or they just leak the news themselves like Steve Jobs used to. That brings us to today's news. It appears the tech giant has hired an augmented reality specialist from NASA to join their AR team.

A federal judge wants answers after an Uber engineer accused of data theft pleaded the Fifth in the ongoing Waymo versus Uber battle. This privilege would protect the accused, Anthony Levandowski, of self-incrimination and handing over specific documents demanded in a previous subpoena and forthcoming deposition.

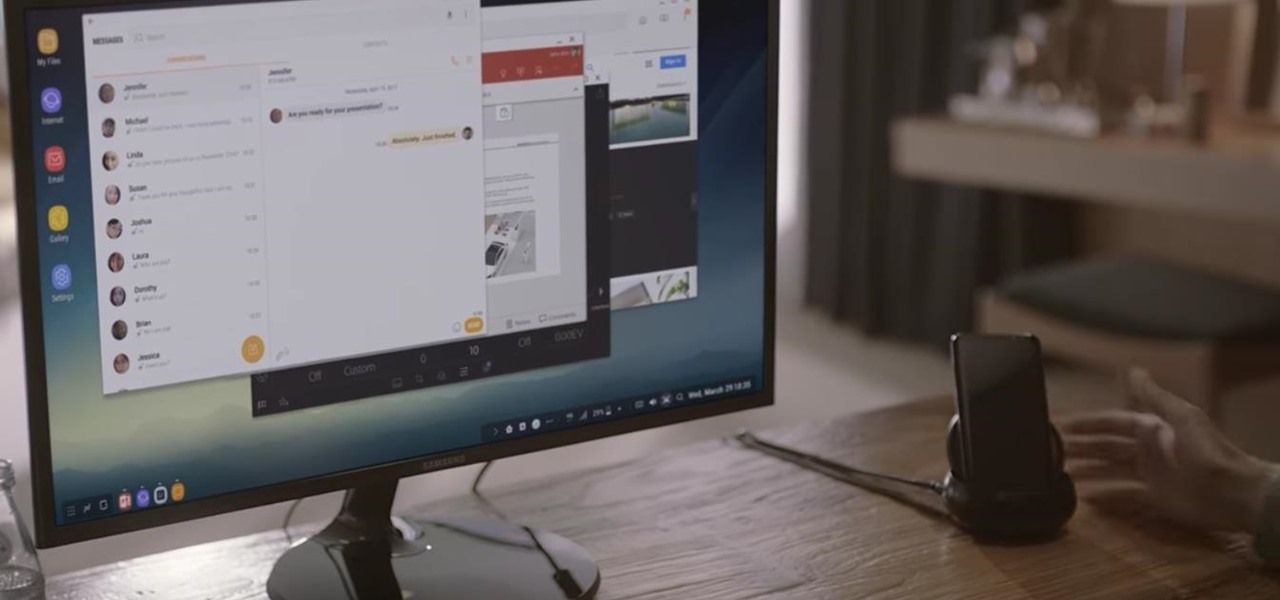
Samsung's new Galaxy S8 can turn into a PC with its DeX dock, but while that may sound like the future of mobile computing on the surface, there are definitely a few issues with the entire setup.

If you're in the market for a non-root ad-blocker, developer Julian Klode has an app that you'll definitely want to check out. It uses Android's VPN system in a similar manner to alternative apps like NetGuard and AdGuard, but it's got a new twist that should save lots of battery life in the process.

Welcome back, my nascent hackers!

Prying into people's lives without them putting up their guard can be difficult, unless you can convince them that you already know them very well. Most people don't have many friends they can be honest with, and this can be exploited. Once they're convinced you already know their secrets, they'll start to fill you in on the little details.

Welcome back, my newbie hackers! Hackers often are associated with clandestine and illegal activity, but that is not necessarily always the case. Hackers are increasingly being used and employed for law enforcement, national security, and other legitimate purposes. In this installment, we will look at how a single hacker could save the world from nuclear annihilation.

Since Motorola engineer Bill Smith invented Six Sigma in 1986, corporations around the world have employed it to eliminate costs and process cycle time while increasing profits and customer satisfaction. These techniques and tools for process improvement were invaluable to famed CEO Jack Welch, who used them to redefine General Electric's business strategy in 1995.

Before smartglasses makers can dream of taking smartglasses to mainstream consumers, they must first determine the right mix of form, function, and price that will drive customers to buy into what they're hoping to sell.

During the recent Augmented World Expo (AWE), we had a chance to try out the Lenovo ThinkReality A6 AR headset. Unfortunately, the experience was all downhill from there.

In its latest feature with an assist from augmented reality in storytelling, the New York Times shows readers the virtual crime scene it constructed to prove that the Syrian military conducted chemical warfare against its citizens.

The next frontier for AR hardware is the consumer headset, and tech companies of varying size and tenure are working hard to strike the right mix between comfort, cool factor, and cost. How these companies handle the hype and flow of information vary wildly.

Null Byte users have often requested video content, but the question has always been what format would best serve our community. This week, we partnered with Null Space Labs, a hackerspace in Los Angeles, to test the waters by hosting a series of talks on ethical hacking for students in Pasadena Computer Science Club. We invited students and Null Byte writers to deliver talks on Wi-Fi hacking, MITM attacks, and rogue devices like the USB Rubber Ducky.

Forget the rise of the machines. Tardigrades are set to outlive everything — even the bots. When the last echo of a whisper in a cell phone has long dissipated into space, the water bears will still be hanging out.

The community of bacteria that lives in our gut has a lot to tell us. It can give clues to what we eat, the environment we live in, and diseases and disorders we may have. Now, scientists have linked these bacterial species to how we feel. A new research study found an association between women's gut bacteria and their emotions.

The search is on to find antibiotics that will work against superbugs — bacteria that are rapidly becoming resistant to many drugs in our antibiotic arsenal.

On October 17, 1943, a story in the New York Herald Tribune read "Many laymen — husbands, wives, parents, brothers, sisters, friends — beg Dr. Keefer for penicillin," according to the American Chemical Society. Dr. Chester Keefer of Boston was responsible for rationing the new miracle drug, penicillin.

Ever since the FBI took down the Silk Road and Dread Pirate Roberts last month, many questions have been raised about whether Tor still provides anonymity or not, and if it's now broken. I'll try to address that question here today succinctly from multiple angles, keeping it as simple and plain-language as possible. The Closing of Silk Road

No longer strictly relegated to the realm of science fiction shows and novels, artificial intelligence can be found behind important technologies that are driving innovation throughout the world. From space exploration and self-driving cars to data science and marketing algorithms, AI is the driving force behind many technologies that are moving humanity forward.

Cross-site scripting can be one of the easiest vulnerabilities to discover, but to be successful with this type of attack, it is essential to learn how to get past filters. In the previous guide, we explored some ways to do this, such as abusing attributes and event handlers and tricking the application into accepting unusual characters. Now, let's take a look at more techniques used to defeat filters.

A new study published by American University demonstrates how Pokémon GO and other augmented reality games can help city governments bring communities closer together.

Database technology has vastly improved the way we handle vast amounts of data, and almost every modern application utilizes it in one way or another. But the widespread use of databases naturally invites a slew of vulnerabilities and attacks to occur. SQL injection has been around for awhile, and as such, there are many defense methods in place to safeguard against these types of attacks.

Every industry has its own jargon, acronyms, initializations, and terminology that serve as shorthand to make communication more efficient among veteran members of that particular space. But while handy for insiders, those same terms can often create a learning curve for novices entering a particular field. The same holds true for the augmented reality (also known as "AR") business.

Welcome back, my budding hackers! People often ask me, "Why are you training hackers? Isn't that illegal?" Although I usually give them a short version of this post, there are MANY reasons why YOU should be studying hacking.