On your iPhone, your phone number and Apple ID email address are the default ways in which somebody can contact you on FaceTime. While you can't remove your phone number as an option, you can withdraw your Apple ID email account. More importantly, you can add any other email addresses you'd like to the list, so you never have to worry about a friend, family member, or coworker not being able to audio or video chat with you.

Seeing that wonderful blue verified badge on Twitter really adds something to your public persona, doesn't it? That's why, when I found out that the average person could get verified on Twitter with the right tools, I jumped on the chance to add that little blue check to my own personal account.
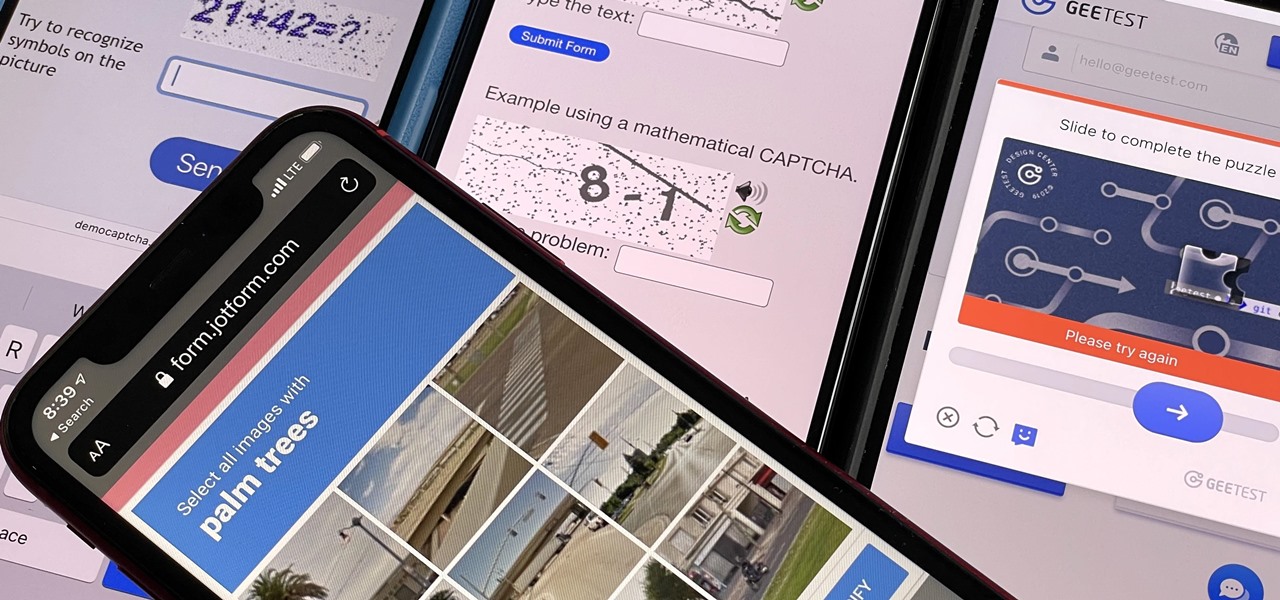
If you hate matching images, typing letters and numbers, solving math problems, and sliding puzzle pieces for CAPTCHA human verification, you'll love Apple's newest privacy feature for apps and websites.
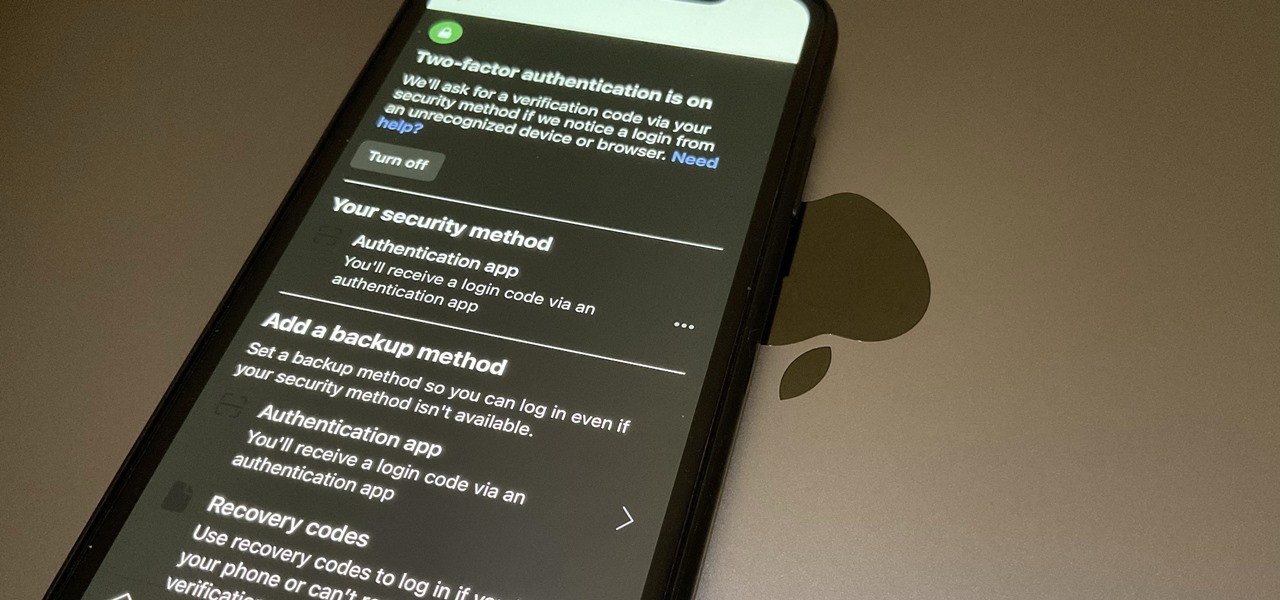
Most websites and apps support two-factor authentication (2FA), which adds an extra layer of security to your accounts by requesting another form of identification beyond username and password. The second factor can be a recovery code, physical security key, or one-time password (OTP) that only you can access, even if someone else has your password. This process is easier than ever thanks to iOS 15.

We've all seen the login pages that allow you to log in to third-party accounts using your credentials from Facebook, Google, or Twitter. It saves you the trouble of creating another account and remembering more passwords — but it can also become a privacy and security issue, which is why Apple created the "Sign in with Apple" feature for iOS 13.
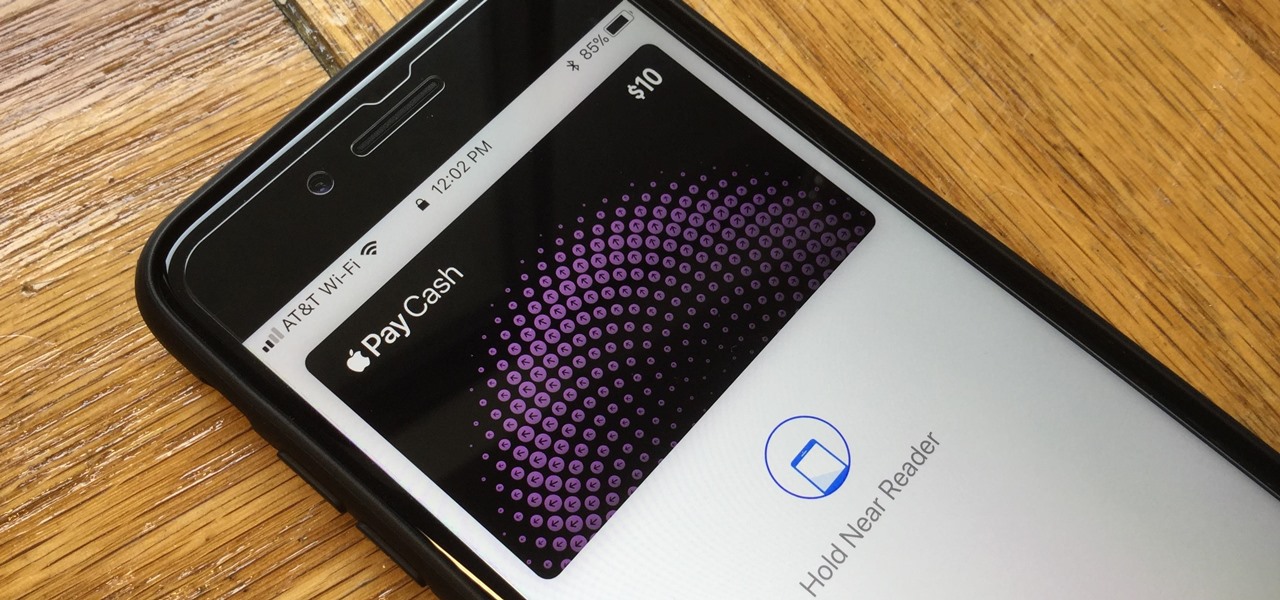
With Apple Pay Cash in iOS 11.2, your iPhone potentially becomes the only form of payment you need. Whether you're sending money to a friend via iMessage or paying for your groceries, you can use Apple Pay Cash to complete those transactions. It makes sense, then, that Apple would allow you to add your Apple Pay Cash card to the lock screen, for quick access wherever you are.

Windows 10 universal apps are actually pretty awesome—regardless of if you're using a desktop, laptop, tablet, or convertible, the same app automatically scales up or down to suit your device. Definitely cool, but the Windows Store is pretty bare-bones as it stands, so the downside is that you can't always find a good universal app for every purpose.

Last year, Apple debuted a feature that allows families to share iTunes and App Store purchases across their various accounts. Us Android users, on the other hand, have to buy separate copies of apps for each of our accounts—well, at least from an official standpoint.

Like its predecessor—and probably every device in the future—the Samsung Galaxy S6 comes with a fingerprint scanner that allows for a more secure lock screen, web sign-ins, and account verification. But unlike its brethren, the sensor on the S6 has been vastly improved. No longer does it require a clumsy swipe—all you have to do is place your finger on it for less than a second, much like Touch ID on iPhones.

Hello Elite Hackers! Welcome to my 3rd Post, which explains how to hack any account like G-mail, Facebook, etc.

Yes, "Safer Internet Day" is a real thing, and it's actually been around for 12 years. This year, Google again will be commemorating the event by giving away a 2-gigabyte storage bump for their Google Drive cloud service if you simply run through a security checkup.

In February of this year, the Higher Court of Berlin ruled that Facebook must follow strict German data protection laws, which Facebook's terms of services and privacy policies circumvent.

Update January 27, 2014: Samsung has released a statement to address the flip cover issue, claiming it as a bug with a "fix" coming soon:

In the wake of the NSA controversy and its subsequent fallout, many dashed towards finding means of secure communication—using private internet browsing and encrypted text messaging applications—out of fear of being spied on.

Are you constantly traveling? Well, as a Hilton HHonors member, you can enjoy special treatment at all of their hotels and resorts. It's free to register, but the difficulty lies in climbing up their membership level. To reach Gold elite status, Hilton HHonors requires that you have a minimum of 20 stays, 40 nights, or 75,000 base points—all in one year. While this may very will be easily attainable for those with jobs that revolve around traveling, it's almost damn near impossible for the re...

What's your Twitter handle worth? If it's considered "desirable" (aka short and simple), it'll get you around 100 bucks, or, if you prefer, the affections of a teenage girl.

In this tutorial, we learn how to bypass Captcha codes on Facebook. First, go to Facebook and log into your account. Next, go into your settings, then your accounts settings. In this section, click where it says "mobile". Next, it will take you to a section where you can activate a phone. You can use your cell phone for this, because Facebook is going to send you a verification text message next. So, enter your cell phone number and when you get the text message click "activate". Now, Faceboo...

You should feel relatively safe to watch and post videos on TikTok, but like with any online service, you're always at the mercy of hackers.

Another contestant has emerged in the race to deliver a mainstream augmented reality car navigation system, with Silicon Valley-based Phiar picking up $3 million in seed funding to launch its own artificial intelligence-based mobile app by mid-2019.

While Meta Company has agreed to a settlement in its lawsuit against a former employee and his company, they find the tables have now turned on them in the form of patent infringement allegations from another entity.

Meta Company filed suit today against a former employee and his startup DreamWorld USA, Inc. for the misappropriation of trade secrets and confidential information.

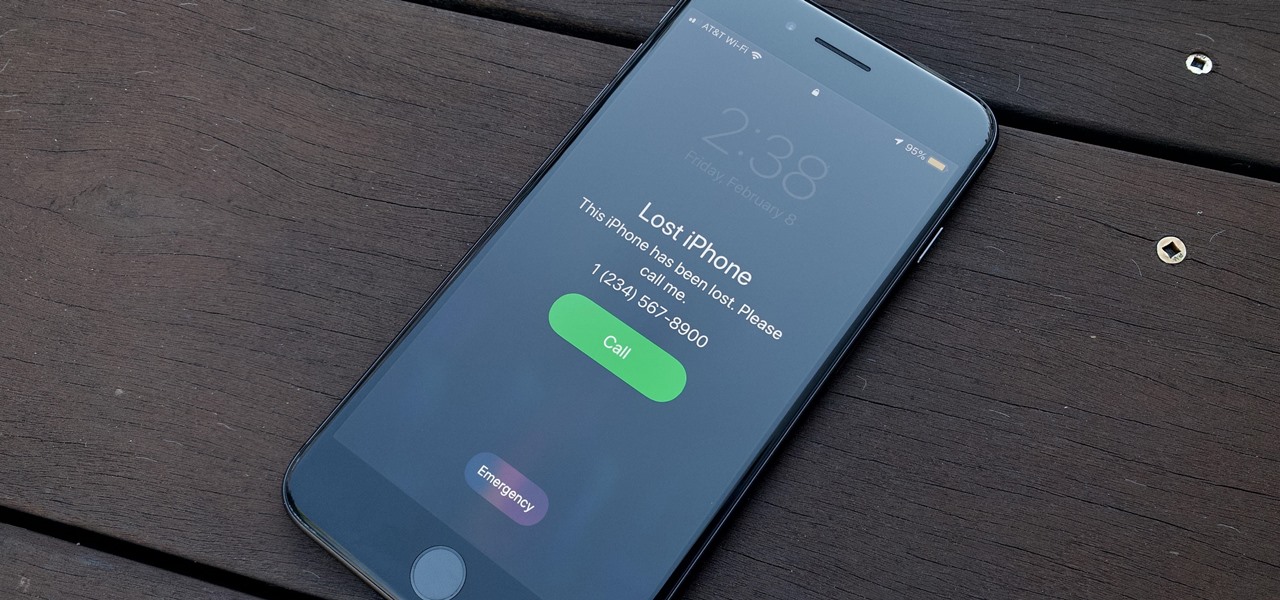
So, you're on the way back from a restaurant and realize you left your iPhone there, but you're late for a meeting and can't go back yet. You may as well kiss that iPhone goodbye, right? Not yet, as long as the right person gets their hands on it first. But that potential do-gooder won't know to contact you, and that's where Find My iPhone's "Lost Mode" comes in handy.

These days, that pocket-sized computer we call a smartphone is home to your entire digital life. But with the onset of mobile payments and online banking, the line between your virtual world and the physical realm is becoming increasingly blurred.

Apple just released its iOS 16.6 update for iPhone on July 24. When you install the new software, it may look like there's not much to it since Apple doesn't include any features in the release notes beyond "important bug fixes and security updates," but a few new features are hiding within.

With so many competing outlets to reach people, accessing inboxes remains one of the most effective forms of communication. Yet newsletter creators run into a constant problem: bounced emails.

As long as you're on the internet, you can be hacked. With an estimated 2.65 billion social media users, these apps are prime targets for hackers.

Suddenly, Magic Leap's lawsuit against Nreal, as well as its barrier to entry in the Chinese market, appears to be as insurmountable as The Great Wall itself.

WhatsApp, the popular messaging app owned by Facebook, has several important privacy and security-related features, including end-to-end encryption, screen lock, read receipts, and two-step verification. If you're an avid WhatsApp user, you'll be happy to know there are more privacy features you might not know, such as hiding your profile photo from other users.

Although all signs points to Microsoft releasing a new HoloLens in the coming days, the company is nevertheless looking to distribute its augmented reality apps to other operating systems.

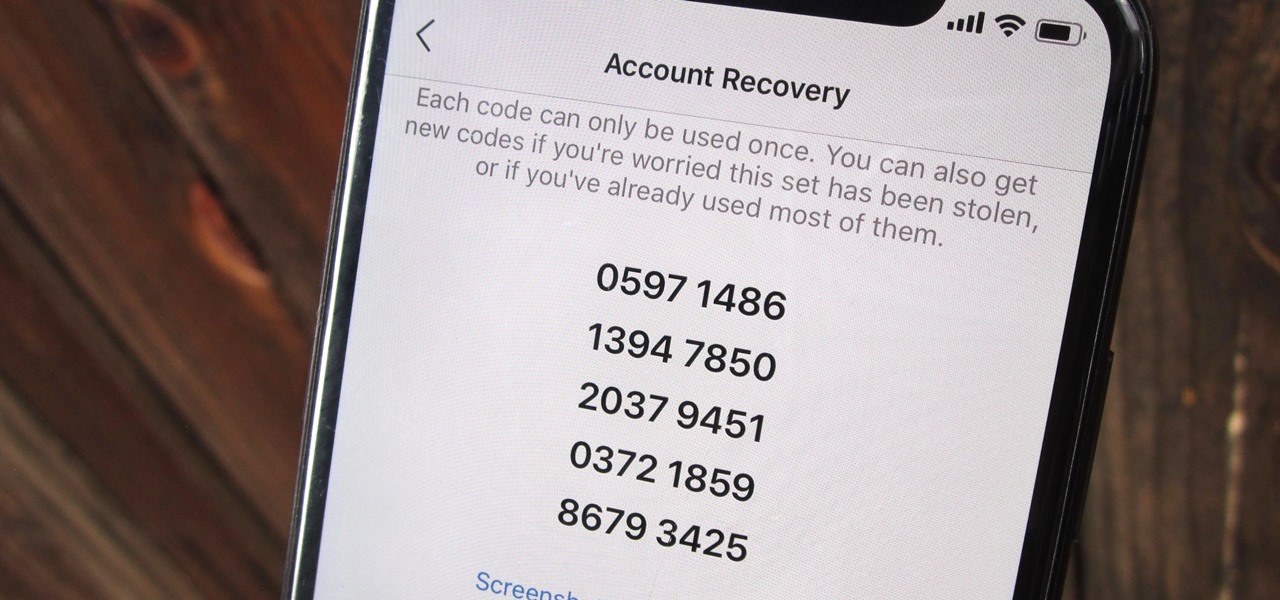
Two-factor authentication (also known as 2FA) adds a necessary additional layer of security to your username and password in many important apps. On Instagram, 2FA requires you to confirm it's you attempting to log in, with a special code sent to you via text message. Enter the code and you're in ... but what happens when you need to log in and don't have access to your phone?

Using either iMessages or FaceTime on the iPhone is a great alternative for coworkers to stay in touch in the event that messaging services like Slack go down. They're also a handy means of communicating between buyers and sellers, as it provides a more intimate way of either checking out or showcasing a product. But you're not always going to want to give out your real number to everyone.

While Apple's tech used for Face ID on the iPhone is impressive, it's debatable whether it's more convenient than Touch ID. There are also concerns that your face could be used to track shopping patterns or be seen during mass surveillance by intelligence agencies. More importantly, it could be easier for law enforcement, and even thieves, to force you to unlock your iPhone.

It seems that mobile app developers are constantly coming up with new ideas to apply augmented reality, with Apple's ARKit promising to increase adoption in apps exponentially.

The latest Google Play Services update has somehow broken major functionality in both Titanium Backup and Substratum. Titanium Backup has suddenly become stuck at zero percent while restoring, and Substratum simply fails to apply themes anymore. Both of these apps do require root, but they've slowly become essential to rooted users, especially since apps like these come into play when you're deciding what your next phone should be.

One of the main reasons for installing a custom ROM on an Android device is all of the added features. For instance, OmniROM offers a souped-up multitasking mod called OmniSwitch, so instead of the regular app switcher, you get an interface that lets you pin your favorite apps, access settings, view memory usage, and more.

Samsung will be launching the next edition of its Galaxy Note series in less than a month, and we're starting to get some solid information about the upcoming phablet. As previously rumored, Samsung is skipping a number on this year's model, so the new model will be called the Galaxy Note7.

Out of nowhere, Google released a preview build of the upcoming Android N release back in March—a full two months early. As if that weren't enough excitement for one day, they topped themselves by following up that announcement with the debut of a new "Android Beta" program that allows users with eligible devices receive preview builds as a regular OTA update, meaning no losing data or manual installation.

Welcome back, my tenderfoot hackers! One key area on the minds of all hackers is how to evade security devices such as an intrusion detection system (IDS) or antivirus (AV) software. This is not an issue if you create your own zero-day exploit, or capture someone else's zero-day. However, if you are using someone else's exploit or payload, such as one from Metasploit or Exploit-DB, the security devices are likely to detect it and spoil all your fun.

If you want to keep your online world secure, your best bet is to have a different password for every site and service that you use, and to make sure each of the passwords are comprised of random characters instead of familiar words or numbers. But this obviously creates a problem—how exactly are we supposed to remember all of these complicated passwords?

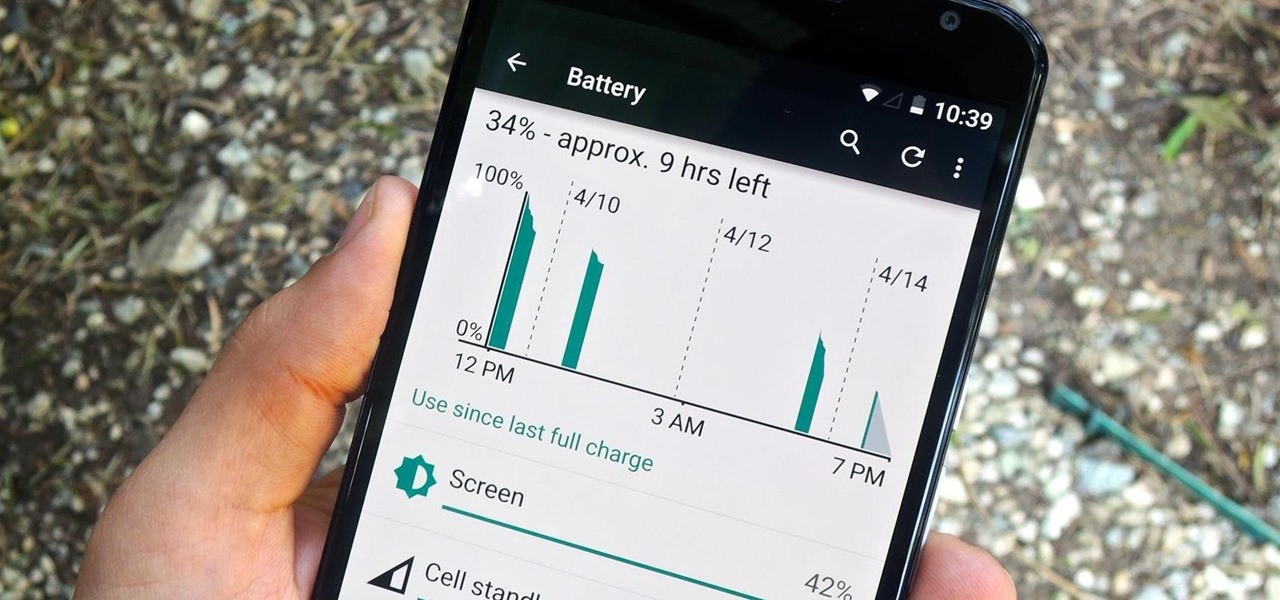
When purchasing a new phone, one of the most vital features to consider is battery life. Everyone wants to know how long they can use their device without needing to hug a wall. Increasingly, more and more manufacturers ship their devices with some variation of a "battery saving" mode, which can help combat dead-phone issues in times of dire need for battery life.