This week, we continued our NR30 series highlighting the leaders of augmented reality space by profiling the venture capitalists and strategic corporate investors that sustain the industry.

RIP Touch ID. Apple's fingerprint sensor on iPhone and iPad models with Home buttons is about to become phased out on Wednesday, Sept. 12. While Touch ID will remain an integral part of models from the iPhone 5S to the iPhone 8 Plus, as well as the iPad Air 2 through the sixth generation iPad, Face ID will completely take over as the default security method for unlocking future iOS devices.

Apparently, it's Google Week for the augmented reality business. Now that ARCore has a firm foothold in the app ecosystem, Google is making a case with educators and marketers that the apps should have a place in schools and campaigns, and the company is also encouraging developers to learn how to build apps using ARCore.

While numerous startups are competing to convert the AR Cloud from a pie-in-the-sky to a reality, Wikitude is thinking smaller with the latest edition of its augmented reality SDK.
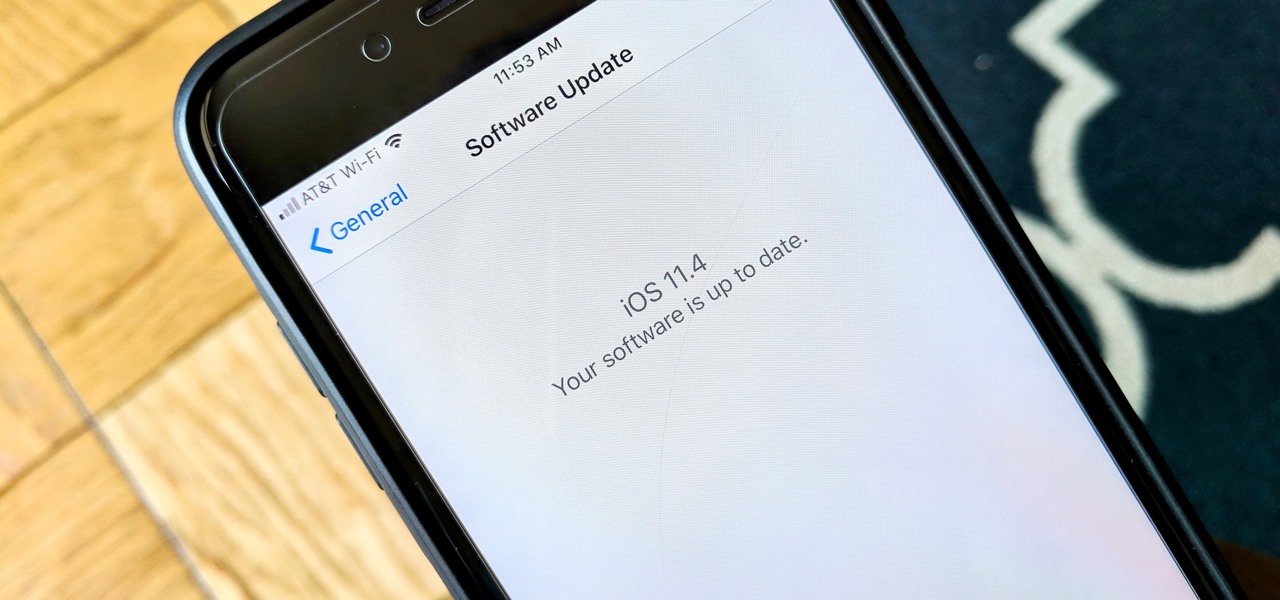
After six betas, iOS 11.4 was officially released to everyone with a compatible iPad, iPhone, and iPod touch. Some features are ones that Apple promised over eight months ago when iOS 11 was first pushed out. This update makes sense since iOS 12 will be announced at WWDC on June 4, and you can't announce a new version like that without first delivering on promises made for the one before it.

As manufacturers try to differentiate their smartphones from the sea of Android devices, a new genre of smartphone has emerged: gaming phones. Razer Phone was the first to gain traction, but the likes of Xiaomi, Asus, and ZTE have all announced gaming-first phones coming soon. Still, you don't really need to buy a "gaming phone" to play games like a pro on your smartphone.

In a LinkedIn post published on Tuesday, Microsoft's leading advocate for the HoloLens made a prediction that the mixing of immersive technologies will define augmented reality in 2018.

As the calendar year (and, for many companies, the fiscal year) comes to a close, it appears 2017 may stand as the new high-water mark for investment in augmented and virtual reality technology.

After recently being in the news for collecting PII (personally identifiable information) for analytics and after-sales support, OnePlus has another security problem. An individual going by the name Elliot Alderson discovered an app in OnePlus devices that can enable root access with one command.

While it's easy enough to ask websites not to track your browsing activity in Safari, they do not have to honor your request. Plus, some of the third-party content providers that websites use can actually invasively track you across other websites. Thankfully, iOS 11 includes a way to minimize companies from tracking you across the web on your iPhone.

If competition in the augmented reality space was a spectator sport, then ARKit, ARCore, and HoloLens dominate the prime-time broadcasts on ESPN.

While ARKit and ARCore are poised to bring AR experiences to millions of mobile devices, one company is poised to anchor those experiences anywhere in the world with just a set of geographic coordinates.

While IKEA is collaborating with Apple for its ARKit furniture app, Marxent is ready to help the rest of the interior decorating and home improvement crowd with their apps.

Not all bacteria in the eyes cause infection. A group of researchers from the National Eye Institue has shown that not only is there a population of bacteria on the eyes that reside there but they perform an important function. They help activate the immune system to get rid of bad, potentially infection-causing — pathogenic — bacteria there.

Augmented and virtual reality continues to be a hot commodity among tech investors, with more than $800 million invested in AR/VR companies in the second quarter alone and global tech leaders like Samsung focusing their investment strategies on the emerging field.

The leading platforms enabling augmented reality technology lead our headlines in Market Reality this week.

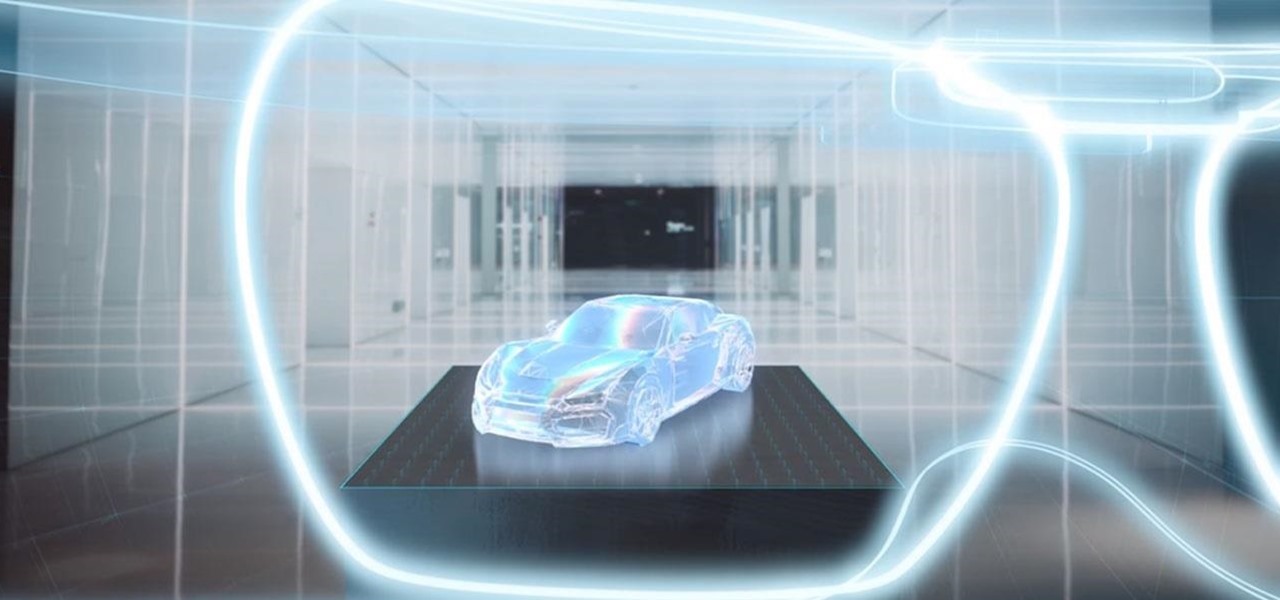
Mixed reality display manufacturer Realfiction has developed a 64-inch display capable of delivering 3D holograms without a headset.

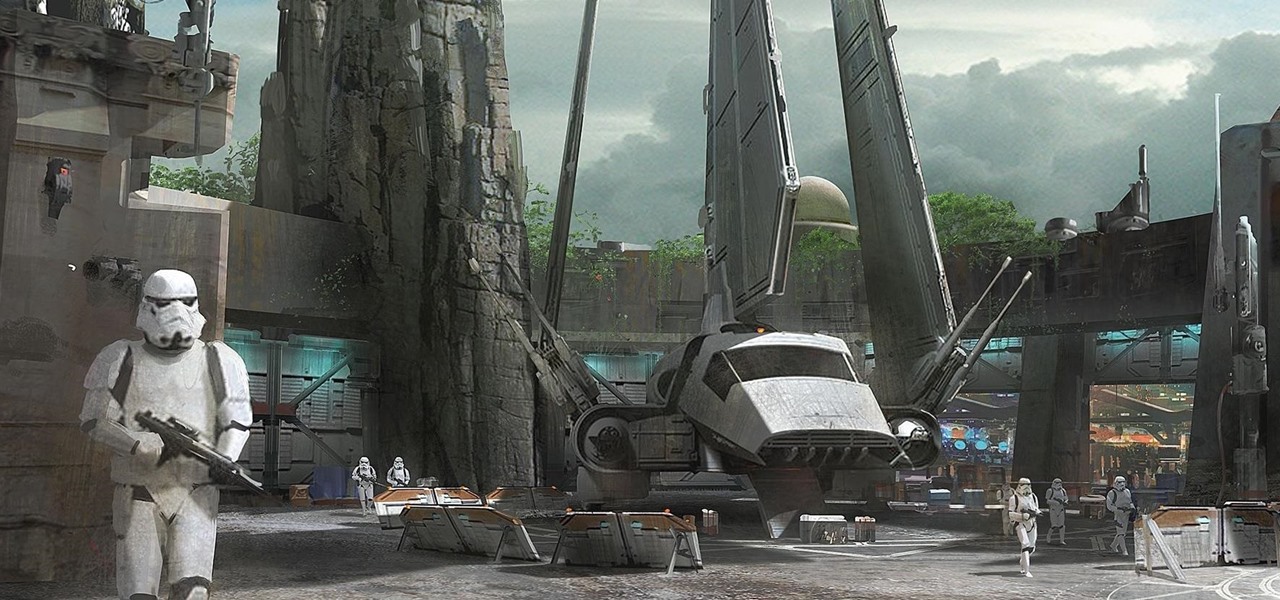
Disney Parks are hard at work bringing the technology from a long time ago in a land far away to life for the opening of Star Wars Land parks in Anaheim and Orlando in 2019.

One of the biggest features to come out with Android O was the addition of a new System UI Tuner submenu that lets you customize the navigation bar at the bottom of your phone's screen. But as it turns out, this same feature can be enabled on devices running Android Nougat, even without root access.

In a disturbing turn of events, Uber has been tracking oblivious iPhone users even after they removed the application from their phone. Two years ago, the situation escalated to such an extent that CEO Travis Kalanick earned a slap on the wrist from Apple mogul Tim Cook.

At the moment, it would be safe to say that demand for devices running Tango, Google's augmented reality smartphone platform, is relatively low among consumers. Kaon Interactive, a B2B software company who has built more than 5,000 interactive applications for use at trade shows, remote sales demonstrations, and other customer engagements, is betting that there is a market for the devices in sales and marketing.

LOOOK, a Seattle-based mixed reality and development studio, can now peer into the future with their new geotechnical engineering visualization application for Microsoft HoloLens.

BlackBerry has formally announced the arrival of its flagship, the KeyOne, during Mobile World Congress 2017 in Barcelona. The all-Android KeyOne looks distinctly BlackBerry, with its 4.5" screen and physical QWERTY keyboard. Here's the lowdown on this elegant handset that hearkens back to BlackBerry's heyday, which had previously been known by its code name, the BlackBerry Mercury. Aluminum Unibody with Physical Keyboard

We recently covered an app called Fingerprint Quick Action that let you use your fingerprint scanner to expand your notification tray like the Google Pixel, along with a few other actions. It's definitely a useful mod, but there's a similar app can make your fingerprint scanner do almost anything—literally.

Before the iPhone 7 was launched and all the unrealized reports about the phone's features were tucked back into their annual rumor mill, there was some speculation about wireless charging. Specifically, whether or not the iPhone 7 and 7 Plus would support it. We now know they don't, and here's why.

Google has a habit of starting on new projects for Android, then hiding them away if they didn't quite complete them in time for a major release. We saw this with multi-window mode last year (which is now an official Nougat feature), and this year, there was the hidden night mode setting that was easily activated.

Welcome back my, tenderfoot hackers! Many people come to Null Byte looking to hack Facebook without the requisite skills to do so. Facebook is far from unhackable, but to do so, you will need some skills, and skill development is what Null Byte is all about.

There are few things more annoying in life than getting interrupted—especially when you're in a groove, jamming out to your favorite song. If we can all agree on that sentiment, then why is it that our phones mute the music we're listening to for a few seconds whenever a notification comes in?

As many of you know, I have been running a couple of series here on Null Byte about digital forensics called Digital Forensics for the Aspiring Hacker and Digital Forensics Using Kali. Although many readers have seemed to enjoy these series, just as many seem to be pondering, "Why should I study digital forensics?"

Welcome back, my neophyte hackers! Metasploit is such a powerful tool that I can only scratch the surface of its capabilities here. As it has developed over the years, it is now possible to use Metasploit for nearly everything from recon to post exploitation to covering your tracks. Given its versatility, every aspiring hacker should have at least a tentative grasp of Metasploit.

Managing hard drives in Linux is crucial to understanding your system and its operation as well as understanding the system you are exploiting or conducting a forensic analysis on. Linux has numerous commands that can provide us with information, control, and management of hard drives, and in this tutorial, we will examine a number of the most important ones.

Welcome back, my neophyte hackers! Digital forensics is one of the fields often overlooked by aspiring hackers. In a rush to exploit every and any system they can, they often ignore learning digital forensics—the field that may lead to them being traced.

Man-in-the-Middle attacks can prove to be very useful, they allow us to do many things, such as monitoring, injection, and recon.

Welcome back, my tenderfoot hackers! A number of you have written me telling me how much you enjoy the Mr. Robot series on USA Network. I am also a huge fan! If you haven't seen it yet, you should. It may be the best show on TV right now.

Welcome back, my tenderfoot hackers! Have you ever wondered where the physical location of an IP address is? Maybe you want to know if that proxy server you are using is actually out of your local legal jurisdiction. Or, maybe you have the IP address of someone you are corresponding with and want to make certain they are where they say they are. Or, maybe you are a forensic investigator tracking down a suspect who wrote a threatening email or hacked someone's company.

Hi, dear co-apprentices and wise masters. I've been recently trying to learn the basics to hacking here, and I've read all guides on Wi-Fi hacking and noticed no word is dedicated to this awesome script that comes bundled with Kali!

Welcome back, my tenderfoot hackers! Now that we have begun this trip down web app hacking lane, we need to first address target reconnaissance. Like any hack, reconnaissance is critical. (Are you tired of me saying that yet?)

The wait is over. The Samsung Galaxy S6, arguably the best Android phone of this year, has just launched. There was already a lot of hype about this super phone—its looks, its specifications, and its other functions have been under the microscope for quite some time. It will not be a good idea that you take this phone in your hand and use it in the same fashion as you have been using your other phones in the past.

The first few times I posted on some of the Android forums out there, I asked things like "Does anybody how I can make my phone do this or that?" Without fail, the responses to these types of questions were always one word—Tasker.

Welcome back, my hacker novitiates! As you know by now, the Metasploit Framework is one of my favorite hacking tools. It is capable of embedding code into a remote system and controlling it, scanning systems for recon, and fuzzing systems to find buffer overflows. Plus, all of this can be integrated into Rapid7's excellent vulnerability scanner Nexpose.