OpenVAS is a powerful vulnerability assessment tool. Forked from Nessus after Nessus became a proprietary product, OpenVAS stepped in to fill the niche. OpenVAS really shines for information gathering in large networks where manual scanning to establish a foothold can be time-consuming. OpenVAS is also helpful for administrators who need to identify potential security issues on a network.

Welcome back, my fledgling hackers! In an earlier tutorial, I introduced you to probably the most popular scripting language for hackers, Python. To become a professional hacker, you need to have some scripting skills and Python is a good choice if you want to master just one. In this latest guide, I will expand your background in Python and offer you a tidbit of Python code to whet your appetite for all of the hacking to come.

Welcome back, my hacker apprentices! To enter the upper echelons of hackerdom, you MUST develop scripting skills. It's all great and well to use other hacker's tools, but to get and maintain the upper hand, you must develop your own unique tools, and you can only do that by developing your scripting skills.

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

Over the years, Magic Leap's long-cultivated shroud of mystery led some onlookers to buy into the company's dream before even trying the device, while for others, the secrecy seems to have stoked the kind of resentment and overcorrecting critique usually reserved for the mighty Apple.

Web application vulnerabilities are one of the most crucial points of consideration in any penetration test or security evaluation. While some security areas require a home network or computer for testing, creating a test website to learn web app security requires a slightly different approach. For a safe environment to learn about web app hacking, the OWASP Juice Shop can help.

Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exit nodes with a VPN, we can configure Kali to become thoroughly private and anonymous.

After previously learning how to make the material of an object change with the focus of an object, we will build on that knowledge by adding new objects through code. We will accomplish this by creating our bounding box, which in the end is not actually a box, as you will see.

The pictures we upload online are something we tend to think of as self-expression, but these very images can carry code to steal our passwords and data. Profile pictures, avatars, and image galleries are used all over the internet. While all images carry digital picture data — and many also carry metadata regarding camera or photo edits — it's far less expected that an image might actually be hiding malicious code.

An attacker can repurpose public MyBB forums to act as command-and-control servers. It only takes a few lines of code to configure a MacBook to fetch commands and send responses to any website the attacker desires.

An attacker with shell access to a Linux server can manipulate, or perhaps even ruin, anything they have access to. While many more subtle attacks could provide significant value to a hacker, most attacks also leave traces. These traces, of course, can also be manipulated and avoided through methods such as shell scripting.

Of all the new features and changes on iOS 16.5, the Apple News app has the most, and there are a few big ones that will change the way you read stories. Some updates even affect Apple News on iPadOS 16.5; the most significant ones apply to both free users and Apple News+ subscribers.

On the surface, AppleCare+ seems like an expensive and gimmicky option to tack onto your already pricey iPhone 11, 11 Pro, or 11 Pro Max. Upon further inspection, however, you'll see that its seemingly expensive price tag is chump change compared to the fees you'll have to pay if you end up having to repair your premium device outside its one-year warranty.

Developers creating login systems know better than to store passwords in plain text, usually storing hashes of a password to prevent storing the credentials in a way a hacker could steal. Due to the way hashes work, not all are created equal. Some are more vulnerable than others, and a little Python could be used to brute-force any weak hashes to get the passwords they were created from.

With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer.

Around this time in 2016, the predictions for the next year had reached something of a consensus: 2017 would be the year of augmented reality. But a funny thing happened on the way to the future — nothing much, really. At least not for the first half of the year.

First of all, I would like you all to meet my good friend Iggy. There he is, in all his scaly reptilian glory. As you can see, he spends a lot more time on top of his cage than inside of it. You see, Iggy here doesn't deal well AT ALL with confinement. I don't know if it's possible for a lizard to be claustrophobic, but if it is possible, then Iggy definitely is. When his previous owner gave him to me, I tried to keep him in the cage, but I quickly realized that it was a bad idea. When confin...

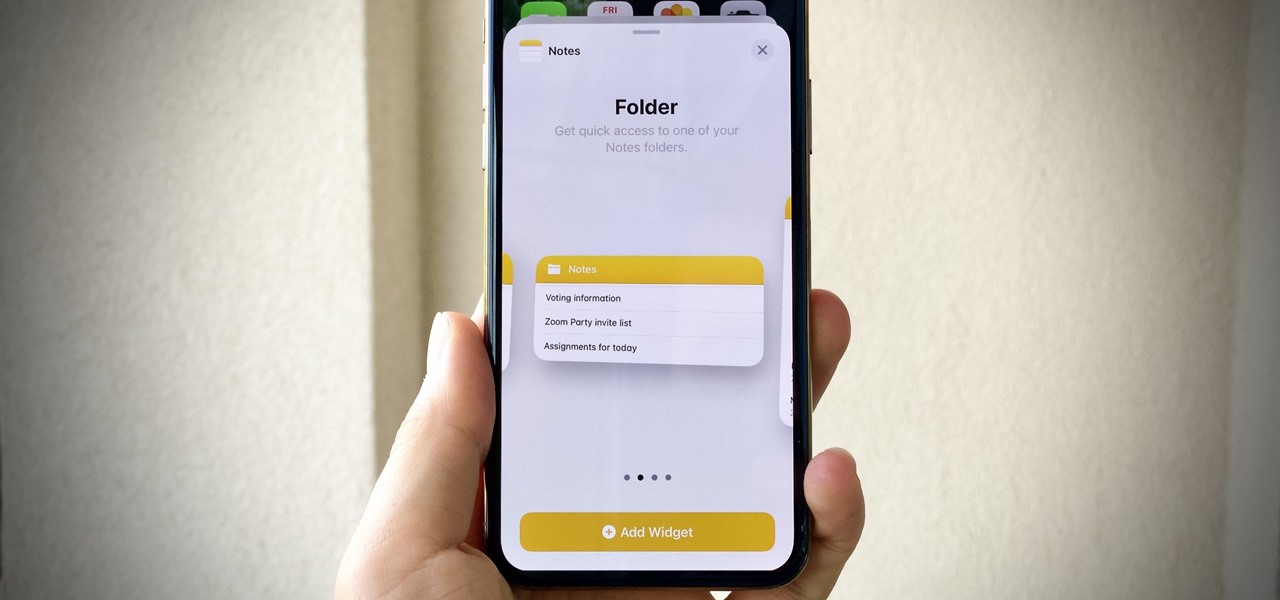
For a built-in app, Notes works pretty well and can stack up against some of the best third-party note-taking tools. Apple continues to update it with each iteration of iOS, adding new features and improving existing ones to make jotting down your daily thoughts a smooth and effective experience. With iOS 14, there are twelve such changes that we think you're going to want to know about.

Apple has a few exciting surprises for you in its latest iOS 16 and iPadOS 16 software updates. Released on Thursday, May 18, version 16.5 includes new features, bug fixes, and security patches, and there are even hints of some big things coming in future software updates for iPhone and iPad.

Paneling is so common among many American basements that we often forget that it can be installed in any part of a home. However, it is frequently used to finish the concrete walls of a basement because of its affordability, durability, and ability to make the downstairs livable.

Cow lurking behind a brick wall in Iraq. There, it's common for cattle, chickens and sheep to be enclosed by brick walls in the cities. It's also pretty common to have them on top roofs, kinda like a rooftop garden, only it's a rooftop farm. Pretty much nowhere for them to go!

In this article, I'll be exploring the basics of Python, i.e. variables, input and output. You'll need Python (2.7+), a computer, and some free time.

You may think of sugar as purely a sweet ingredient meant for baking, but it can actually be a deadly explosive, according to PopSci's Gray Matter:

UTILIDOR n pl. -S an insulated system of pipes for use in arctic regions 59 points (9 points without the bingo)

PLASTRUM n pl. -S plastron 62 points (12 points without the bingo)

I'm not going to lie. I was Catholic. But one of my reasons for my faithful departure was having to tell my innermost secrets— my sins— to a silhouetted figure behind a latticed screen. With the creepy enclosed booth structure and separation of sinner and confessor, its anonymity was clear, yet deceiving. You always knew the priest and he always knew you. If I wanted total privacy, was there really a need for this intermediary to God?

LIFE magazine has posted a gallery of bizarrely wonderful old school scientific models. Don't miss the giant fetus or massive colon (double ew). Behold, science education before computers ruled our world.

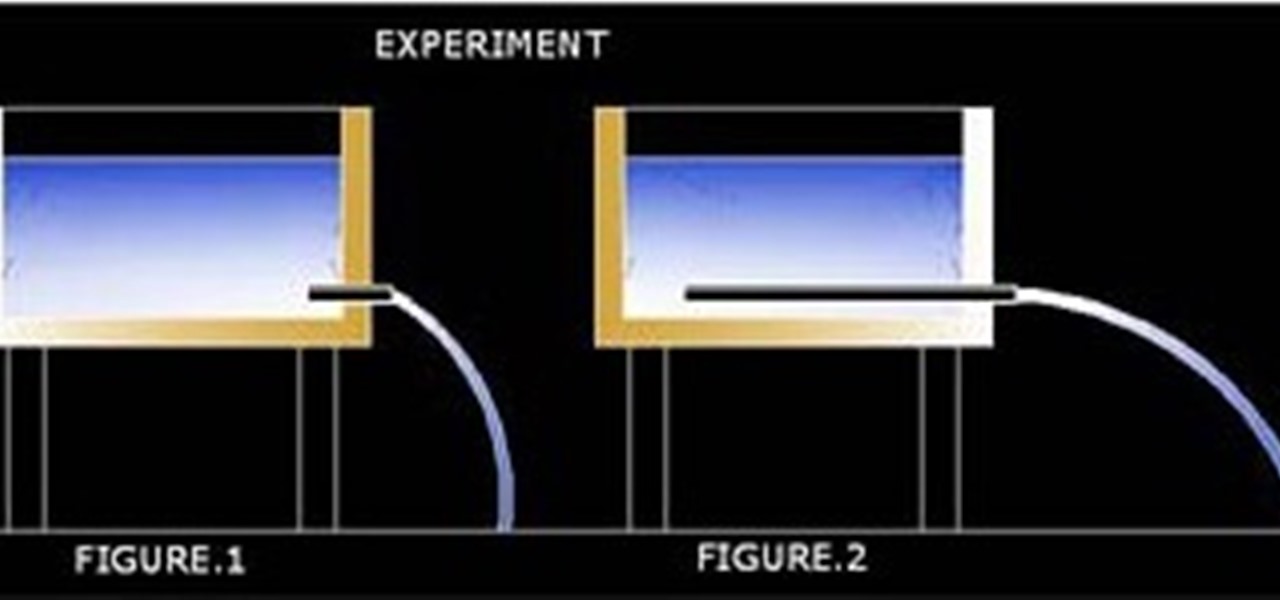
An experiment was carried out at our laborataries to investigate the flow through two pipes of same diameter fitted at the same height from water level inside of a water tank as shown. It is found the longer pipe line inside the water tank generates a higher speed resulting more powerfull flow. Flow in this pressure pipe develops due to gravitational accelaration on a horizontally flowing water column also, when it is an enclosed stream of flow. If this length is short it is not possible to d...

Michael Faraday was an English chemist and physicist - a bona fide electromagnetism and electrochemistry genius. Without him, men couldn't walk on live electrical wires. Wait, what?

Halloween will be here in just over a week, which means next week these Scrabble Bingo of the Days will become more horrific. This week, there's just a few relevant Halloween seven-letter words for your Scrabble vocabulary, referencing witchcraft and one of the eeriest horror movies of all time, The Thing (not this year's version).

Welcome to Minecraft World! Check out our advanced tutorials and come play with us on our free server.

Welcome to Minecraft World! Check out our advanced tutorials and come play with us on our free server.

In this prank, all of the cast members will be involved because let's be honest, it's funnier when all of the "talent" is getting hurt.The premise is that each one of the cast members will have to complete a stunt in order for the next one to start. There will be eight individual stunts -- one for Preston, Wee-Man, "Danger" Ehren, England, Dunn, Bam, Pontius, and Steve-O. Each cast members will start in an enclosed box. Once their box opens they will be released into a 60x60' area that will b...

Have a guy go into an enclosed area with a bunch of people such as an elevator or a public bus/taxi. Once in, secretly take out a bottle of 'Liquid Ass' and either spray a bunch or if it's a liquid spill some drops on the floor. Once the smell gets really bad and people are gagging or about to throw up...basically look around saying it wasn't you and blaming other people (such as the women).

X amounts of bear mace , 5 mini mini motorcyles , 1 bam , 1 danger , 1 knoxville , 1 ryan dunn , and the one and only steve-o ... now in an enclosed area or a busy Los Angles street (rodeo dr.) whatevers easier , each member must be sprayed with ther bear mace while trying to slalom through a verity of objects (i.e people , cars , traffic , wee man equipped with a can of mace in each hand , crocidiles etc.) for each time one of he player miss they must start again ... the winner chooses the 4...