Most people give their fruits and veggies a cursory rinse under the faucet before eating or cooking them, but is that few seconds under running water really enough to remove any remaining dirt, pesticides, or wax clinging to the surface?

Bottled water is a rip-off. Not only is it pretty much the same stuff that comes out of your tap for free, but plastic bottles are rarely recycled and thus account for a huge amount of the waste that's overflowing our landfills. Next Up: Water Bottles You Can Eat

Welcome back, my greenhorn hackers! Continuing with my Wi-Fi hacking series, this article will focus on creating an invisible rogue access point, which is an access point that's not authorized by the information technology staff and may be a significant security vulnerability for any particular firm.
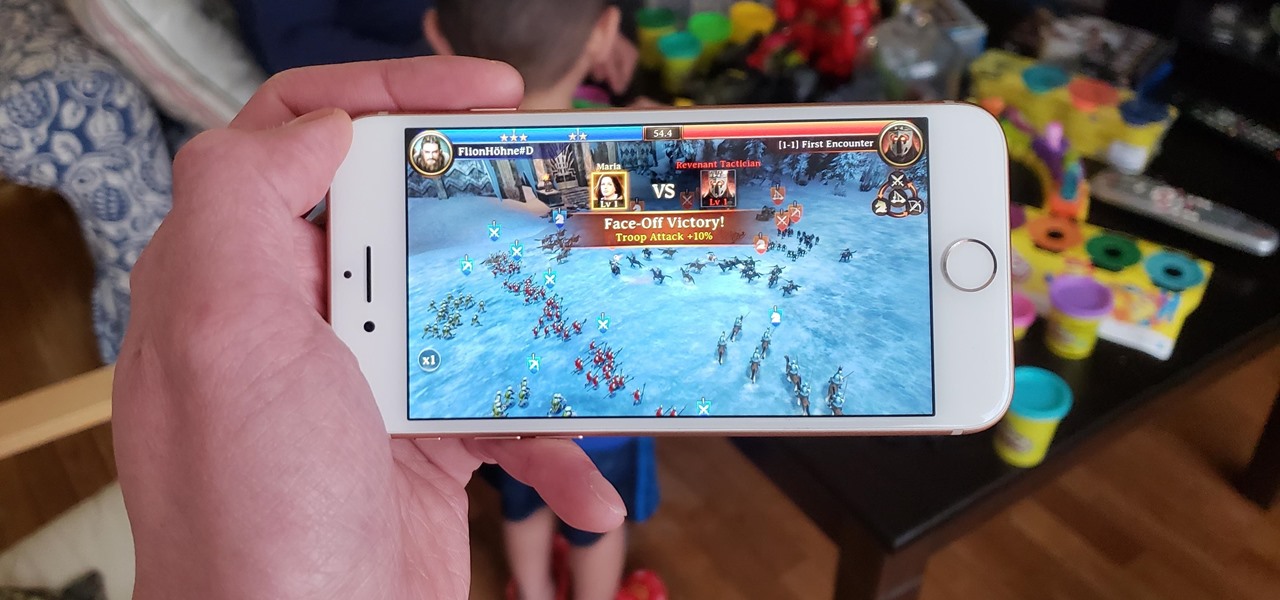
Netmarble has released a new MMORTS game called Firstborn: Kingdom Come to go up against competing games like Lords Mobile. Unfortunately, the game seems to be stuck in development as a soft launch in select countries, limiting its exposure to gamers worldwide. But don't let this hiccup deter you — we've found a simple workaround to play the game on your iPhone right now.

Mixed reality developer Arvizio has updated its MR Studio software suite to integrate processing of 3D light detection and ranging (LiDAR) point clouds.

The Galaxy S8's Bixby Vision feature isn't working up to its full potential for Verizon customers, according to a recent CNET report.

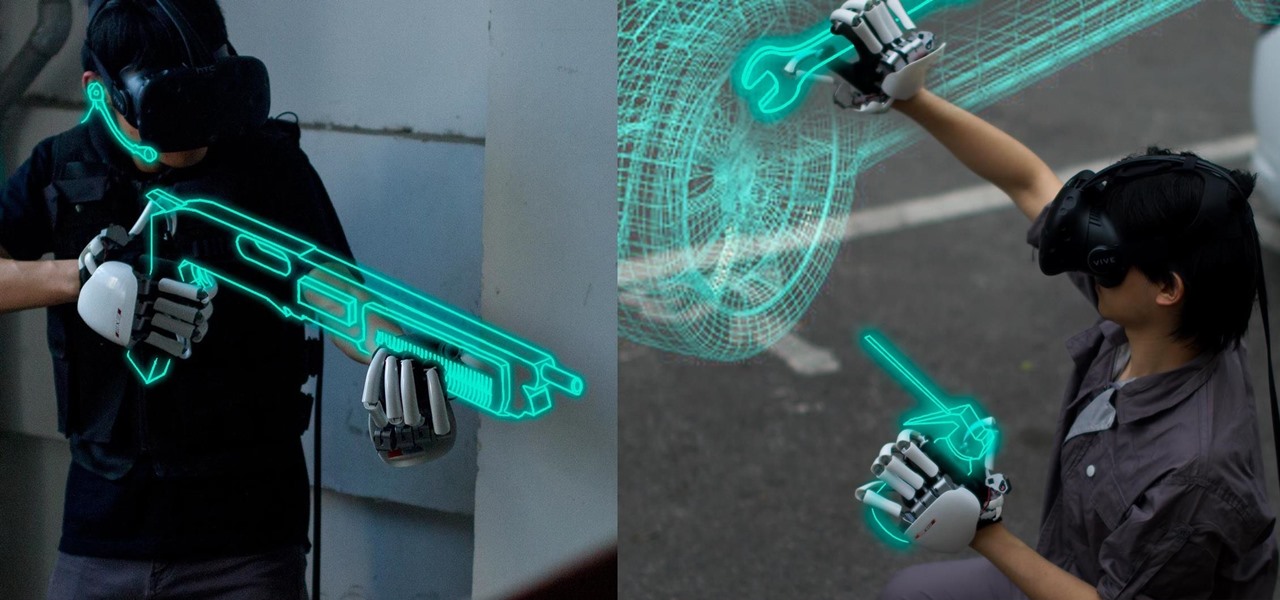
One of the disadvantages of the digital world is that you can't pick it up and touch it. While that can feel like less of a problem in virtual reality, where you're already holding controllers, mixed reality environments—like the one you'd experience in Microsoft's HoloLens—suffer from a lack of physical connection with the digital objects that appear in your real world. Dexmo aims to solve that problem with a relatively intimidating new controller that encompasses your hands.

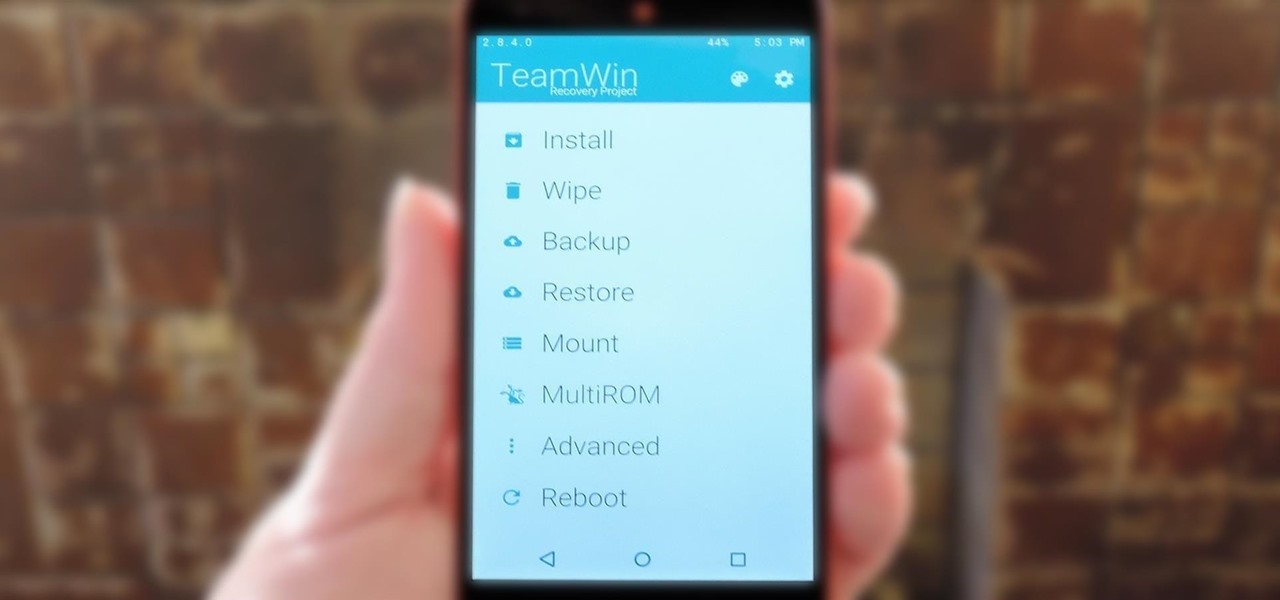
TWRP is hands-down the best custom recovery out there. Its interface, on the other hand, is... well, let's just call it utilitarian. The guys over at Team Win made sure that their product was robust, functional, and easy-to-use, but they didn't put a tremendous amount of effort into polishing the looks.

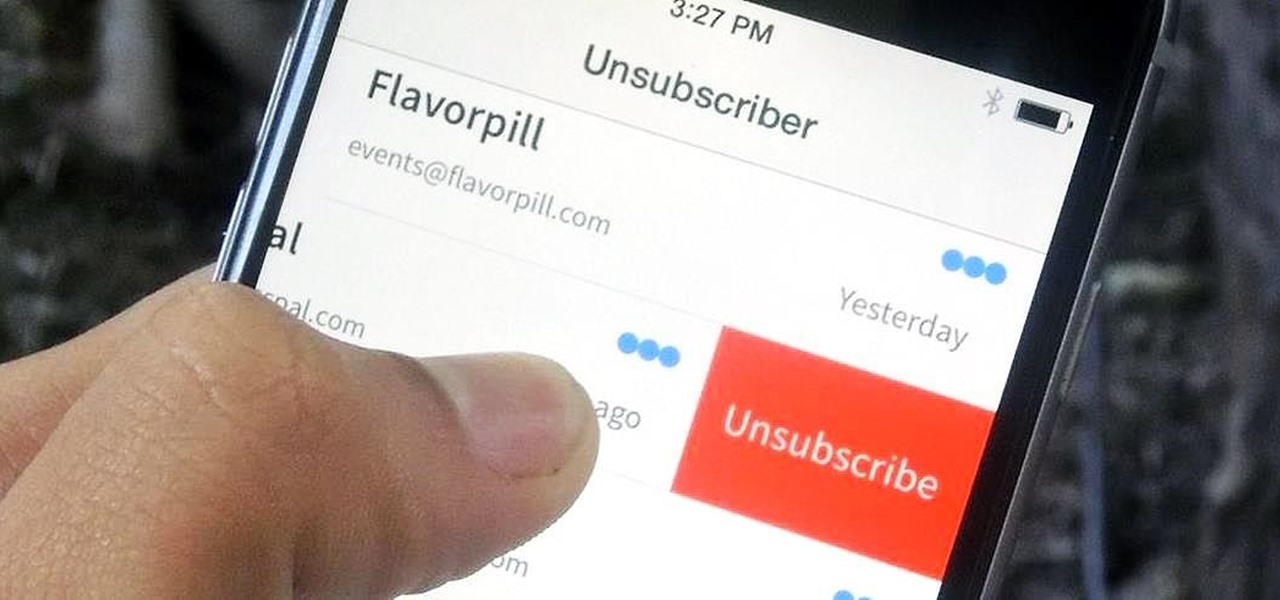
You've undoubtedly used your email address to sign up for a chance to win something online or to purchase something on sale. Often, these offers are too enticing to pass up, and you reason that you'll live with the consequences of handing out your information for the chance at making out big.

The new Camera app in iOS 8 has a few really great features, but some of the best photo-centric features were packed into the iPhone's photo editing tools. These new editing features can create even more dynamic images than before, no Instagram required.

If you purchased your Nexus 5 from Google Play in the United States, we've got great news for you. In an unprecedented move, Google has started offering customers the chance to exchange their broken or water-damaged Nexus 5 for a new or refurbished unit—free of charge.

Unless you're a high-schooler building a nuclear fusion reactor, the hardest part of a science investigatory project often is coming up with a good idea. You want it to be cool yet feasible, novel but still useful.

The original iPhone SE was, for some, the perfect iPhone. It brought back the popular one-handed form factor of the iPhone 5 but packed in the internals of the then-new iPhone 6S. Now, the second-generation iPhone SE is here for 2020, but can it live up to what made the first-generation iPhone SE so popular?

As I've mentioned in recent days, it was refreshing to discover that Microsoft's HoloLens 2 stage production was every bit as accurate as presented (check out my hands-on test of the device for more on that).

The app that started as simply a photo-sharing social media platform has expanded to encompass so much more than that. Between live videos, stories, chat, and animated stickers, Instagram is more than the sum of its pictures. Now, there's a new feature to add to that list for Android and iOS — video and audio calls.

Volvo Cars' "all-electric" announcement last week was seen as a direct threat to Tesla's electric vehicle (EV) and driverless lead, but German auto giant Volkswagen (VW) says it is in a better position to challenge Tesla.

Starting with Marshmallow, Android added a built-in theme engine called "Runtime Resource Overlay," or RRO. This theme engine was intended to be used only by smartphone manufacturers, not end-users, so unlike Cyanogen's CM Theme Engine, owners can't use it to change the look and feel of their phones.

Virtual reality, along with its siblings, has the opportunity to profoundly change the way we interact with all things digital. As a visual medium, we often don't think about the impact on audio, but it plays a significant role nevertheless. When it comes to music—and music videos—the possibilities are enormous.

Microsoft enjoyed a few months in the spotlight after releasing the developer version of the very first mixed reality (MR) headset, but now we're starting to see the competition jump in.

One of the few areas where Android lags behind iOS is a comprehensive backup solution for apps. Root tools, such as the popular Titanium Backup, are capable of backing up all of your apps and their data, but not everyone wants to root their device and potentially run into issues with voided warranties.

Welcome back, my greenhorn hackers! Lately, much of the discussion here on Null Byte has revolved around evading detection and not getting caught hacking. Several of you have written me asking for a series on evading detection and forensics, and while I began a series 5 months ago on just that, we have changed hacking platforms from BackTrack to Kali, which has a much more highly developed forensic toolset.

The lock screen music player in iOS 7 has all the controls you'd ever need from a lock screen, but it's not as visually appealing as I hoped it would be. Yes, it does show you the album cover art, but the way everything is presented makes it feel cluttered.

Are you staying up longer than you want to? Do you fidget with your tablet late at night before bed? Maybe you're using it to read or to watch something to help you knock out. If so, this may actually be keeping you up.

So, you've finally converted from an iPhone to a Samsung Galaxy S3 smartphone. Great. Only now you're overwhelmed with the unfamiliar look and feel of the Android operating system.

The enterprise applications powering the adoption of the HoloLens 2 are only just ramping up as developers continue to work with the still relatively new hardware.

Sure, Snapchat AR Lenses can be fun, but they can help communicate complex issues as well. While our Facebook news feeds were filled with references to 311 Day, March 11 is also World Kidney Day, the United Kingdom's National Health Service Blood and Transplant (NHSBT) used the occasion to educate its constituents about organ donation.

Rumors around Apple's not-so-secret development of an AR/VR headset have been prevalent throughout the young year, but the latest round of reports move speculation of the device into a clearer view.

Along with rebranding Magic Leap 1 for enterprise customers, Magic Leap has gifted its developer community with some new toys with a tease of more to come in 2020.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

Considering Rovio Entertainment quite literally owes its existence to Apple and the App Store, it may ruffle a few feathers that the company has opted to aim the augmented reality debut of its blockbuster Angry Birds franchise at Magic Leap instead.

With the software installation out of the way, it's time to build the framework within which to work when building an augmented reality app for Android devices.

The reveal of Magic Leap One: Creator Edition brought with it some insight into the path the device took from prototype to "final" design.

In the case of rotting food, microbes are not our friends. Now, scientists have developed a new food wrap coated with tiny clay tubes packed with an antibacterial essential oil that can extend the shelf life of perishable food, so we can waste less and eat more.

The bacteria in our gut — a community called the gut microbiome — have been in the spotlight a lot lately. What we're learning about how our intestinal bacteria adapt and grow with our bodies could help athletes perform better, according to researchers starting a company focused on creating probiotics that mimic athletes' microbiomes.

During the millions of years they've been on earth horseshoe crabs have developed a trick that can save our lives even now — and may be especially useful in the fight against healthcare-associated infections.

Just like your gastrointestinal tract, and the soil we walk on — a dust storm has a collection of bacteria, fungi, and viruses all its own called a "dust microbiome."

Bed bugs are parasites not yet known to spread disease — but they cause plenty of irritation. As scientists and landlords search for new ways to deal with the pests, a new study examines how we can deter bed bugs without so many chemicals.

Microbial cells can improve the functionality of clothes in creative and useful ways, including cooling us down during a workout or making clothing glow for better visibility.

Think of the coolest, most unique way to create art that you can. Got it? Now think about creating that art out of living things.