Back when I worked in the music industry, I never imagined there would be a day that I'd be able to sit in a room surrounded by virtual album covers while listening to beats, but that day is really here.

While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show you how a hacker would do so and explain why they should be careful to avoid hacking into a honeypot.

In the previous article in this short series, we learned how to find our neighbor's name using publicly accessible information and how to monitor device activity on their home network. With this information at our disposal, it's time to get into installing and configuring the necessary tools to begin our attack on John Smith's computer.

Despite concerns with SafetyNet, Google actually cares about root. Every phone they sell has an unlockable bootloader, so you can toggle a setting and send a Fastboot command, then start flashing custom firmware right away. The Pixel 2 and Pixel 2 XL continue this tradition, and now they have an official root method.

In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodology behind an actual attack and demonstrate the proper way to practice on a VM.

UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found at my blog, here - https://techkernel.org/2015/12/19/embed-metasploit-payload-in-apk-manually/

It's been a while when the major web browsers first introduced HTTP Strict Transport Security, which made it more difficult to carry Man In The Middle (MITM) attacks (except IE, as always, which will support HSTS since Windows 10, surprised?).

With the Wigle WiFi app running on an Android phone, a hacker can discover and map any nearby network, including those created by printers and other insecure devices. The default tools to analyze the resulting data can fall short of what a hacker needs, but by importing wardriving data into Jupyter Notebook, we can map all Wi-Fi devices we encounter and slice through the data with ease.

Why do you need augmented reality? Because enterprise, they say. And while that's certainly true for several disciplines, there's still that mainstream use case hanging out there waiting for users to discover beyond the realm of enterprise and gaming.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

While there are many ways to see the exact battery life left on your iPhone, you can take all the work out of it by making your iPhone verbally tell you the current percentage every time you start or stop charging it. Best of all, this trick works whether you use wired or wireless chargers.

Ah, subscriptions. Whether you love or hate them, they are now a fundamental part of our increasingly digital lives. If you have some essential subs on your iPad, iPhone, or Mac, like Apple Arcade, Apple Music, Apple News+, Bumble, Pandora, Tinder, or YouTube Premium, there are three key issues you need to know about that could unexpectedly stop your membership from renewing.

While Google Play Music fans mourn its demise, its replacement, YouTube Music, is gaining some neat features that its predecessor never had.

I've covered augmented reality apps for about three years now and the most useful mobile app I've encountered over that time is Google Lens.

There are more than a few subscription-based movie streaming apps available for Android and iPhone, each with different benefits and varying pricing plans. Needless to say, it can get expensive fast if you sign up for multiple services because you can't decide on what's best. Hopefully, we can help you out with choosing the right video-on-demand app to spend your hard-earned dollars on.

You can mod every aspect of your phone's software with root, but if you want to make changes at the hardware level, you'll need a custom kernel. If you've looked into custom kernels before, one name undoubtedly kept coming up: ElementalX. It's easily the best custom kernel out there, and the reason for that is its awesome developer, flar2, aka Aaron Segaert.

Around this time in 2016, the predictions for the next year had reached something of a consensus: 2017 would be the year of augmented reality. But a funny thing happened on the way to the future — nothing much, really. At least not for the first half of the year.

My first encounter with a phablet was late last year with the AT&T version of the Samsung Galaxy Note 2, having never touched or even seen its highly-acclaimed and pioneering predecessor. Initially, I was a bit overwhelmed by the enormous screen and taken aback by the dated stylus, which brought up ugly memories of my dad using his ten pound PalmPilot.

Whether you're wielding an iPhone, iPad, Mac, Android phone or tablet, or even a Windows PC, this little-known secret holds the key to effortless assistance and unwavering obedience. Intrigued? I thought so.

One of the most promising avenues of attack in a web application is the file upload. With results ranging from XSS to full-blown code execution, file uploads are an attractive target for hackers. There are usually restrictions in place that can make it challenging to execute an attack, but there are various techniques a hacker could use to beat file upload restrictions to get a shell.

Silence spreads over these mountains like nothing I've ever felt. If I didn't have Moby blasting in my earphones, there'd probably be no other sounds around. Well, except for someone, Phil probably, murmuring in a nearby tent just low enough to make his words indiscernible.

No more carrying around heavy laptops and thousands of Linux Live CDs and USBs to always be ready for pentesting on the fly!

With Unc0ver, Pwn20wnd was the first to jailbreak an iPhone and iPad running iOS 12 versions. While it initially couldn't work on all devices, it's an entirely different story now. Unc0ver currently works up to iOS 13.5 for most A7 to A13-powered devices. Plus, Chimera, another jailbreak tool, supports a similar range of models on iOS 12 to 12.3 and iOS 12.4.

This year's big iPhone update, iOS 12, aims to solve many of the issues that arose during iOS 11's controversial, buggy tenure. With that in mind, it may be tempting to jump on board the new software immediately and leave iOS 11 in the dust for good. Here are some reasons why you might want to reconsider joining the iOS 12 beta.

Sometimes I forget that I'm also a fiction writer, so I thought it might be a nice change of pace to share one of my stories with you. I wrote this piece awhile ago for an anthology that never came together and I'm tired of just sitting on it.

It can be very frustrating: You open your Messages app, send an iMessage, and then see that dreaded red exclamation point or horrible green SMS bubble. At this point, you may be curious whether it's just your iPhone or whether iMessage is broken for everyone, but how do you find out?

The last iOS software update was a modest one, but iOS 17.4 has a lot more for your iPhone, including changes to emoji, Podcasts, security, Safari, widgets, Apple Cash, CarPlay, and more.

In previous versions of Acrobat you could run PDFs against the Preflight tool and it would either pass or fail. If it failed you would then have to manually resolve the problems in the PDF or by generating a new PDF. In Acrobat 8 Professional you can now apply "Fix-ups" to correct the most common problems encountered in working with PDFs for print.

Automotive lighting is one area of mechanics and car care that might seem intimidating to the average driver when it comes to do it yourself repair and replacement. However, vehicle headlamps work very similarly to all the lighting fixtures encountered around the home or office: bulbs illuminate the road, and occasionally need to be replaced to ensure safety on the road and proper standards for inspection. In this video clip series, you will learn the basics of headlight and taillight removal...

Synopsis: Tell one guy that a girl that one of the other guys knows just had some sketchy demonic encounter/satanic experience at some Wicca gathering she went to last night while she was trying to get answers from the past. Then say she’s incredibly creeped out right now and is home alone tonight so they are going to seize the opportunity(while she’s still scared) and have him dress up as Satan himself and go to her house late at night and “appear” to her in her bedroom. (Don’t be overly des...

I will illustrate a simple, yet effective way to stop tracking and third-party cookies without installing any additional software on your computer. Third-party cookies are often used to track your visits and activities on webpages and can slow down your browser and hinder your privacy. They are often the most common detected adware or spyware installed on most computers.

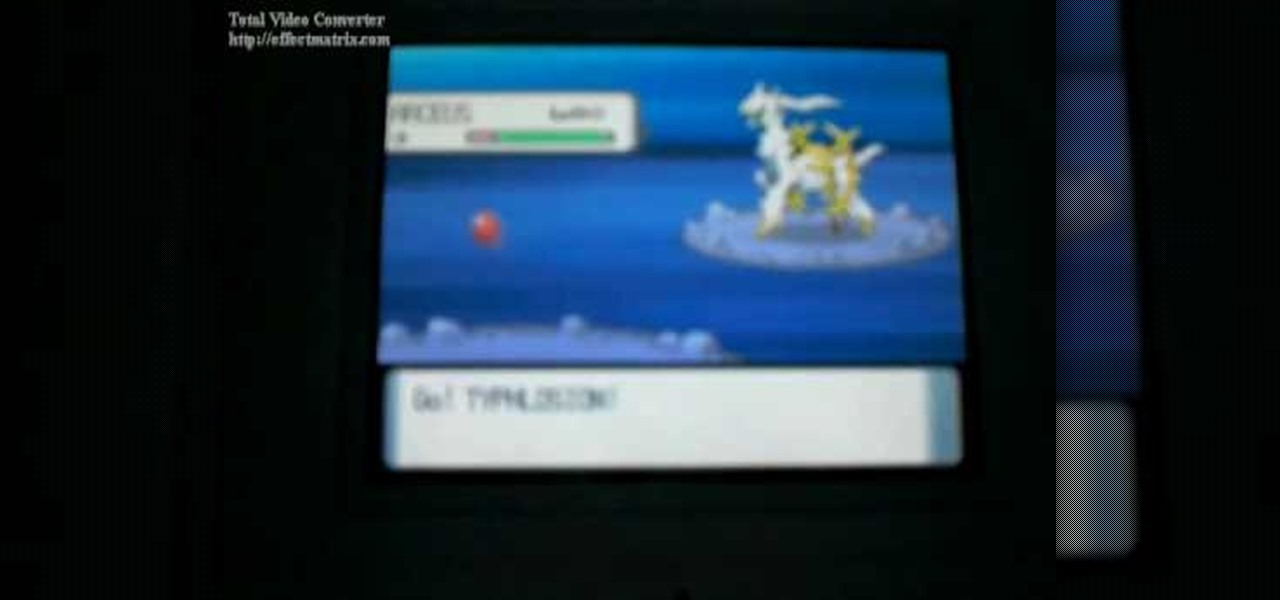
Arceus is the 493rd pokemon added to the National Dex. It can be encountered at level 80 which is the highest level wild pokemon in the game. This video will show you exactly how to find and catch the legendary god pokemon Arceus.

"Chef" Marilyn isn't the first thing that comes to mind when thinking of the infamous blond bombshell. Yet a recipe featured in Fragments, a compendium of handwritten Marilyn artifacts, has led Marilyn-o-philes to believe the icon was in fact more domesticated than one may think.

From Walt Disney Pictures and visionary director Tim Burton comes an epic 3D fantasy adventure ALICE IN WONDERLAND, a magical and imaginative twist on some of the most beloved stories of all time. JOHNNY DEPP stars as the Mad Hatter and MIA WASIKOWSKA as 19—year—old Alice, who returns to the whimsical world she first encountered as a young girl, reuniting with her childhood friends: the White Rabbit, Tweedledee and Tweedledum, the Dormouse, the Caterpillar, the Cheshire Cat, and of course, th...

STANDP'S WINDOWS 7 "ASTON-2" CUSTOMIZED DESKTOP IT ROCKS COMPLETELY!. DEC

Smartphones are impressive devices, to say the least. A smartphone user can consume TV, music & movies; communicate via streaming video; check the weather; record audio; take professional quality video footage; snap high quality photos… The list just continues to grow and grow. With all of these incredible capabilities, why not add surveillance?

For more than a decade, free-to-play games with microtransactions (also called In-App Purchase or IAP) by which players can pay real money for in-game content have been the industry standard for online success in Asia. Mainstream American gamers have long resisted these "freemium" games, with World of Warcraft and other subscription based online games reigning supreme, and being seen as more AAA than their free-ish counterparts. Casual games developers have encountered no such problems, and m...

This article describes the very basics of compiling a program on Linux. It is targeted at the absolute beginner. Sometimes beginners search for programs on the web for their Linux systems, and is faced with the reality that they have to compile the program themselves, either because there exists no binary for their architecture, or the author of the program just doesn't release any binaries at all, but only sources.

Hello readers again! Sorry about the long wait (scary computer problems). Today I am going to talk to you about security problems on Wizard101. I have recently encountered many security flaws on Wizard101, including hacking, frauding and other crazy things. Wizard101 is the target for many online predators, many of who are fully-grown adults aged 60 or 70. Here is the link to an article I found about it: Wizard101 Internet Predators

The Fog of Will Suki = a chink in the armor, a psychological weakness. Doubt.