In the digital age, maintaining your privacy is a never-ending battle. All sorts of companies and agencies have access to your data, and quite a few can eavesdrop on almost every method of modern communication.

Some data can be very confidential. In such case you need to encrypt the data so that it does not go into the wrong hands. There are lots of encryption software available to encrypt the data. But to use them first you need to install then and this can take lot of time. You can also use Windows built in compression client to encrypt information. To use this feature you need not install any software and it is a fairly simple process. So select a file that you want to encrypt, right click on it ...

In this tutorial I will be explaining the purpose of unique encryption/decryption scripts ( I will be referring to these at "UEDS" for this tutorial). Then, I will show you how to make one. Finally I will talk about the downsides to the method I use. I will also provide links explaining the concepts and algorithms used in encryption to anyone who wants to see what is going on under the hood.
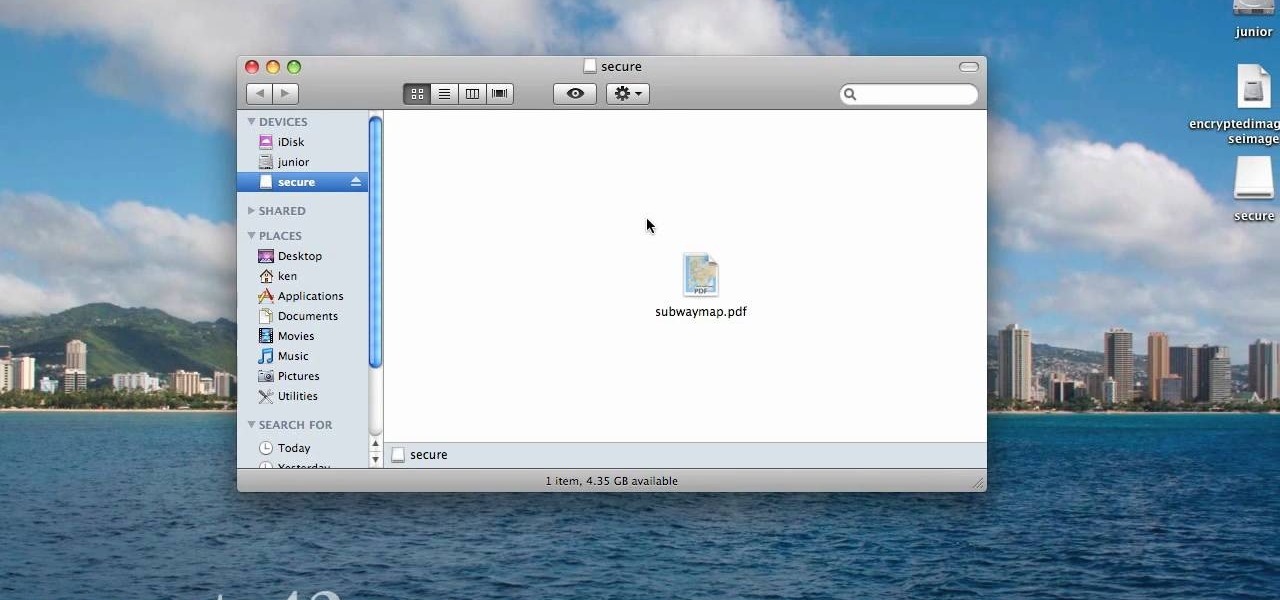
When you are sending any files over a network it is advised to encrypt it so that no can read it even if they get hold of it. You can encrypt files in Mac OS for this purpose. So first take any file or program that you want to encrypt. Open your hard disk and go to the applications. In the applications, under utilities open the Disk Utility program. Using this disk utility program you can create an encrypted disk image. Now this image will act as a disk image or other flash drive, but we can ...

For years, Skype has been synonymous with video calling and messaging. However, as the industry moved toward encryption and privacy, Skype usage was discouraged by experts due to its murky encryption. To combat this, Skype has introduced true end-to-end encryption.
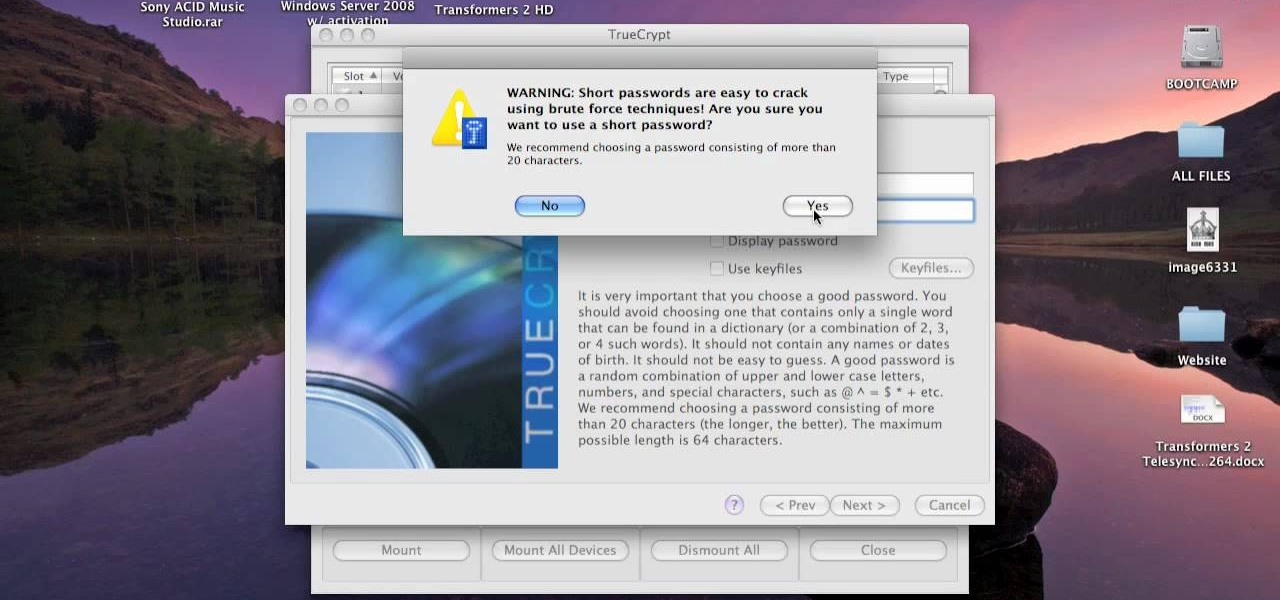
This video tutorial is in the Computers & Programming category where you will learn how to encrypt files & folders on a Mac with TrueCrypt. Open up TrueCrypt and click on create volume > create an encrypted file container > next > standard truecrypt volume > next. Here you name your file, choose the directory where you want to put the file and click 'save'. Choose the encryption type and click 'save'. Choose the volume size and click 'next'. Now type in a password and click 'next'. Then in th...

Encryption is the process of converting you data in to other obscure form so that no one can read it. Encryption can also be done using batch files. Batch files are scripting programs in windows which can be used to program small automatic operations. To do this open a notepad to write the batch program. First turn of the echo by inserting the command '@echo off'. Now write the rest of the program as shown in the video. Now save the image as a bat file. Now you can encrypt this batch file. To...

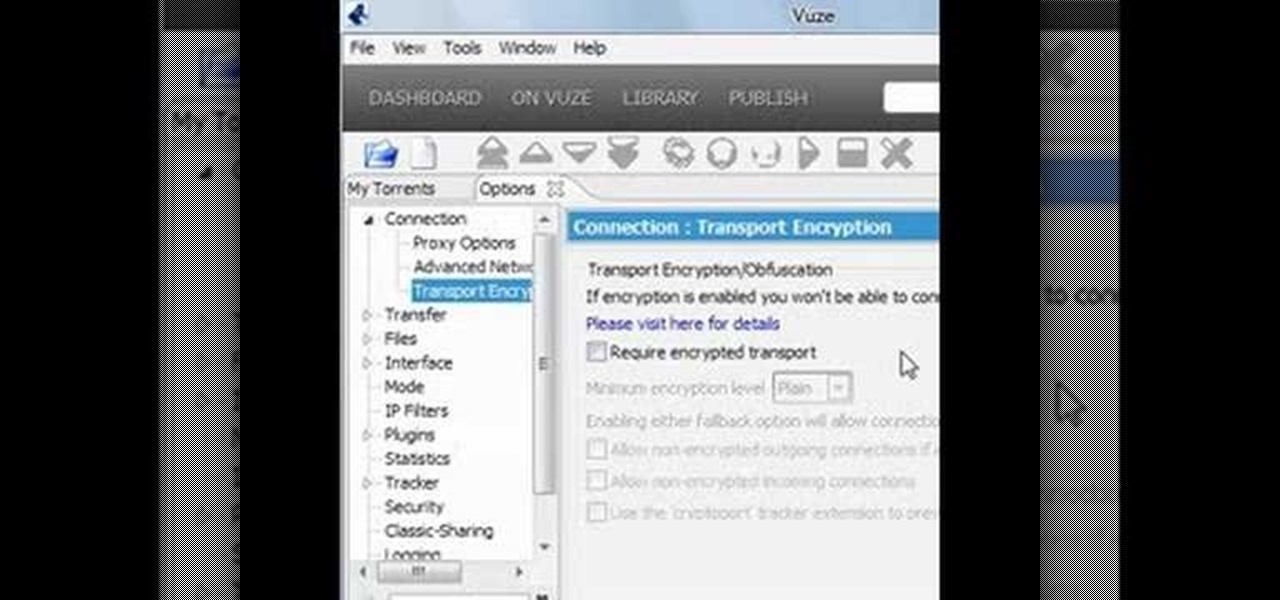
Torrents are a wonderful technology to share your files over the internet. If the data that you are sharing is confidential you may need to encrypt these files before sharing. To encrypt torrents in Azereus, go to tools and select options. From the left hand side menu select the connection option. Select the 'Transport Encryption' option from the connection sub menu. This section is intended for intermediate mode or higher and it is not available in beginner mode. So go to mode and select the...

In the wake of the NSA controversy and its subsequent fallout, many dashed towards finding means of secure communication—using private internet browsing and encrypted text messaging applications—out of fear of being spied on.

Have a file or a number of files too sensitive to be stored on your desktop hard drive? Thwart would-be snoopers with an encrypted USB flash drive. This free video tutorial from the folks at CNET TV will show you everything you'll need to know to create your own password-protected thumb drive directories.

In this day and age, maintaining your privacy is a perpetual battle, and doing so with an internet-connected device like your smartphone is even more of a struggle. Every website you visit, every app you install, every message you send, and every call you make is a potential vulnerability that could expose you to prying eyes.

Want to encrypt your thumb or flash drive? This Windows 7 tutorial will show you how it's done! It's easy! So easy, in fact, that this home-computing how-to can present a complete overview of the process in just under a minute's time. For more information, including detailed, step-by-step instructions, watch this Win 7 user's guide.

Archive files are great for portability and saving space, but a lot of people don't know they can also be encrypted. There are a lot of archiver programs out there, but most of them can open a file that's been encrypted using other software, as long as you're using a recent version.

Welcome back, my fledgling hackers! There's an evil dictator hellbent on destroying the world, and in one of our last hacks, we successfully compromised his computer and saved the world from nuclear annihilation. Then, we covered our tracks so no one would know what we did, and developed a hack to capture screenshots of his computer periodically so we could track of what he was up to next.

Have a super secret spy communication you'd like to send out, but don't have the funds to hire your own trusted operatives to deliver the message? Then stick to what you're used to—email it. SafeGmail is a browser extension that allows you to send encrypted emails right through your regular Gmail account. While this may seem a bit unnecessary for most messages, encrypting your email can definitely be useful.

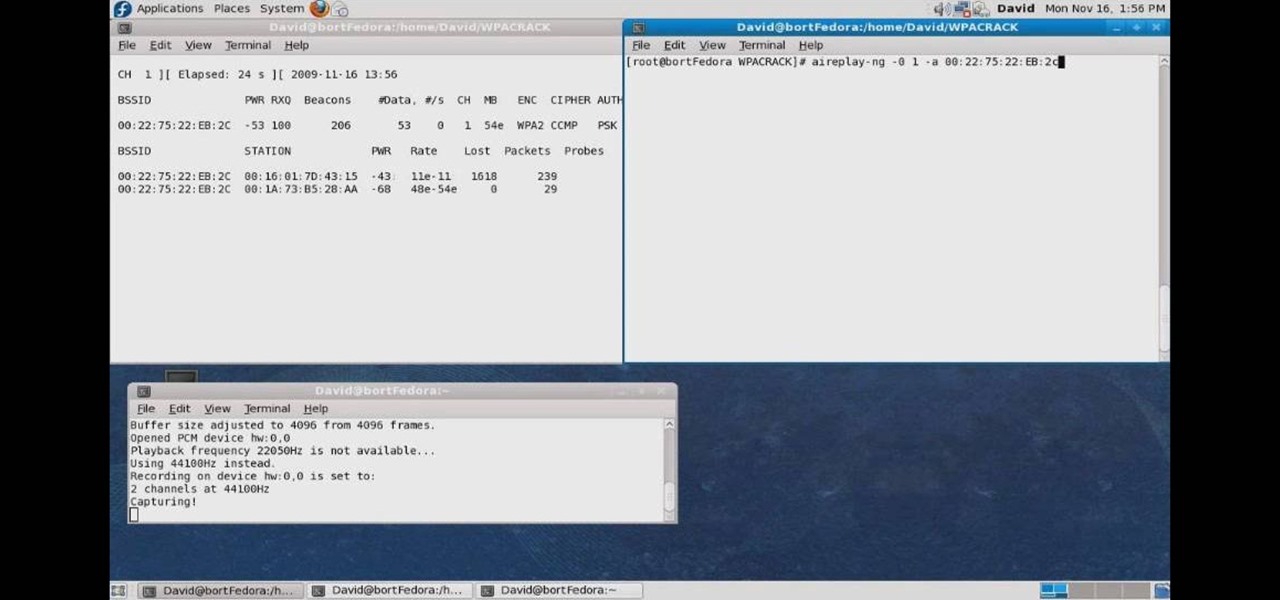
In this how to video, you will learn how to crack a WPA encrypted wireless network. To do this, you will need the Air Crack package for Linux. First, disable the wireless adapter and enable monitor mode. Next, identify the channel in the wireless network and Mac address. Once you have this, you can listen to the traffic coming to and from this point. Wait for the handshake or disconnect something in order to force it to reconnect. From here, you are ready to perform the attack. With any encry...

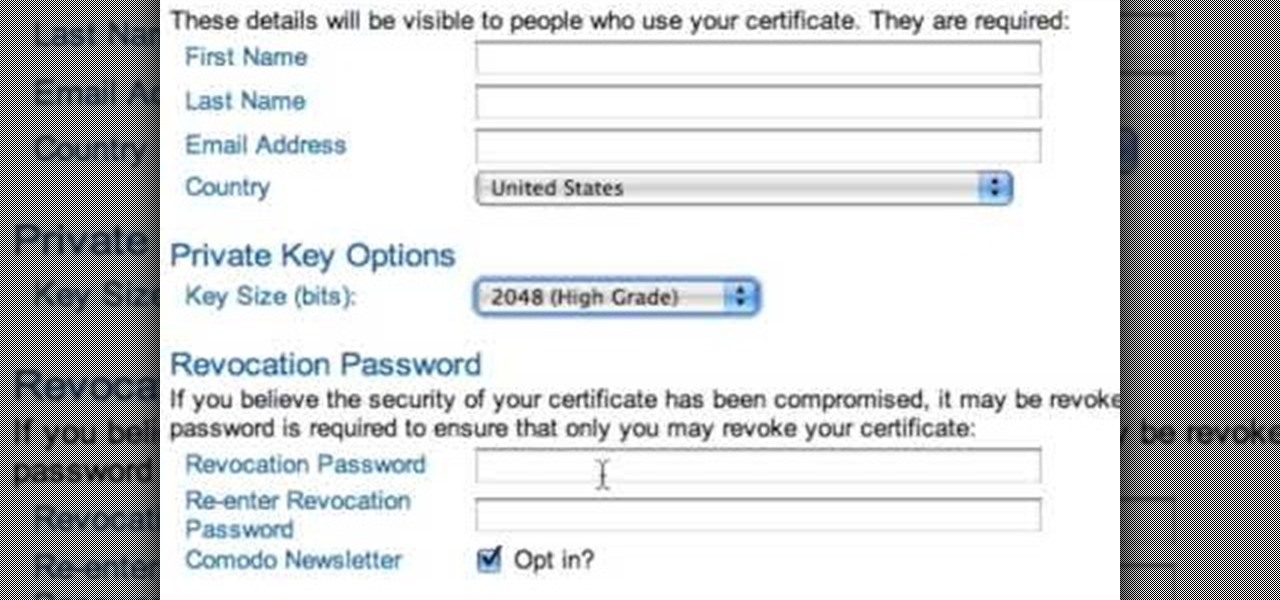
The only people who should read your emails are you and your intended recipients. Protect your privacy with this simple crytography guide, which shows how to obtain a free certificate for signing and encrypting email messages, how to download and install the certificate on Mac OS X 10.5, and how to use the newly installed certificate in Apple Mail.

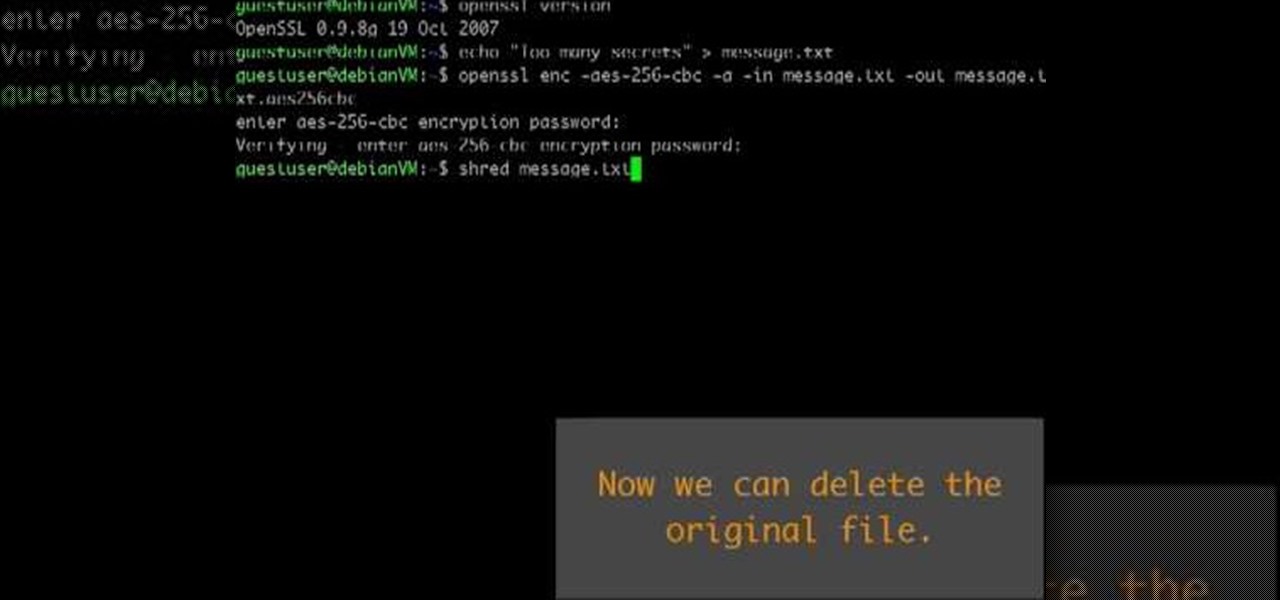
This video shows how to encrypt files with OpenSSL in Debian Linux. First we check if open SSL is installed on the system. If not, install it using packet manager. Next create the file going to be encrypted. Now encrypt the file. In this case AES algorithm in ypher block chaining mode is used. AES is US-government standard and can be considered secure. Now we are prompted for a password. In order for the encryption to be secure, we need to choose a strong password. Now we can delete the origi...

Check out this tutorial and learn how to encrypt Microsoft Office files to help prevent unauthorized people from opening a workbook, document, or presentation. Watch the video to see how easy it is to set a password to help you control who can open or modify the Office files you create.

For anyone wanting to keep information private, plain text is a format of the past. Instead, cheap, powerful encryption is widely available, but often not easy enough to use to attract widespread adoption. An exception to this rule is EncryptPad, an easy to use application that lets you encrypt text, photos, or archives with strong encryption using a password, keyfile, or both.

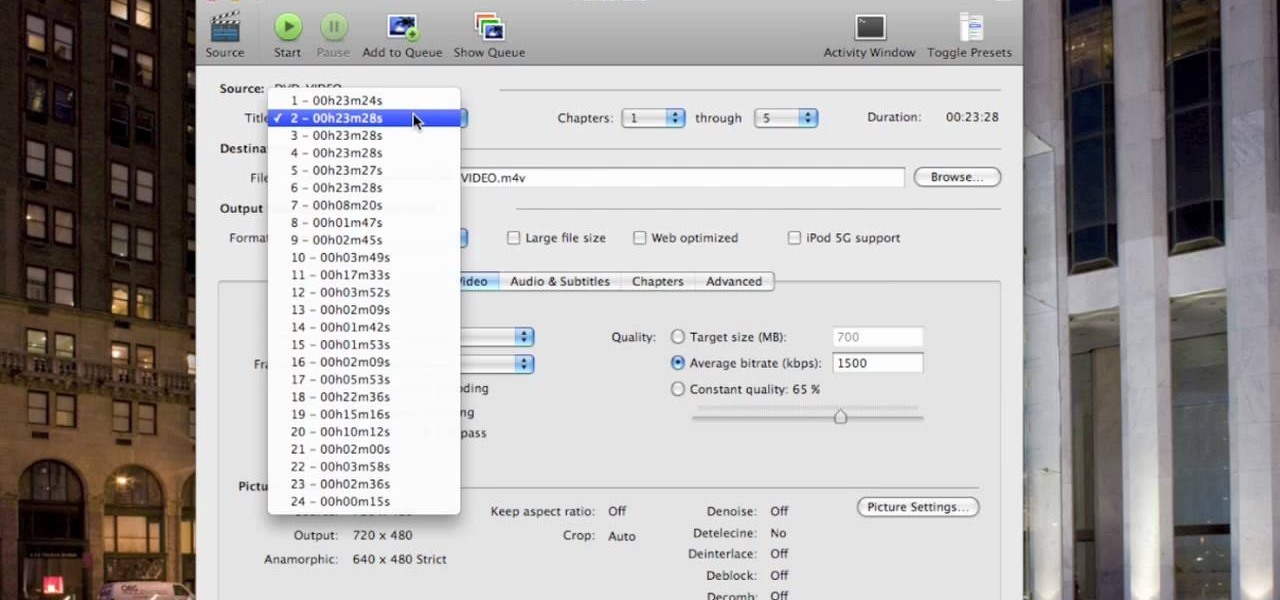
This video shows you how to copy a DVD to a Mac using a free application called Handbrake. Open the Handbrake window, select the DVD you want to copy from where it's listed on the side, and click open to start scanning. After the scanning is done, a window will come up where you can choose which file on the DVD you want to copy. If you're copying a movie, it's usually the largest file. Choose what type of file you want to convert it to, and it will start copying. If the DVD is encrypted, you ...

When it comes to security, Apple is usually at the top of the pack when it comes to your personal data, minus a few embarrassing flaws here and there. However, a new iOS security concern has been discovered that protects your data less than it did before — and Apple designed it like that.

In spite of the degree of difficulty it is to install, CyanogenMod has steadily climbed the ladder to become one of the most popular third-party firmwares for Android devices.

The convenience of storing things on the cloud can definitely make life easier, but if you're storing sensitive files, it could be a total disaster if anyone hacked your account. Some encryption services can be expensive, but if you just need it for personal use, there are some really great ones that don't cost anything. Here are three programs that let you encrypt your cloud storage for free. BoxCryptor

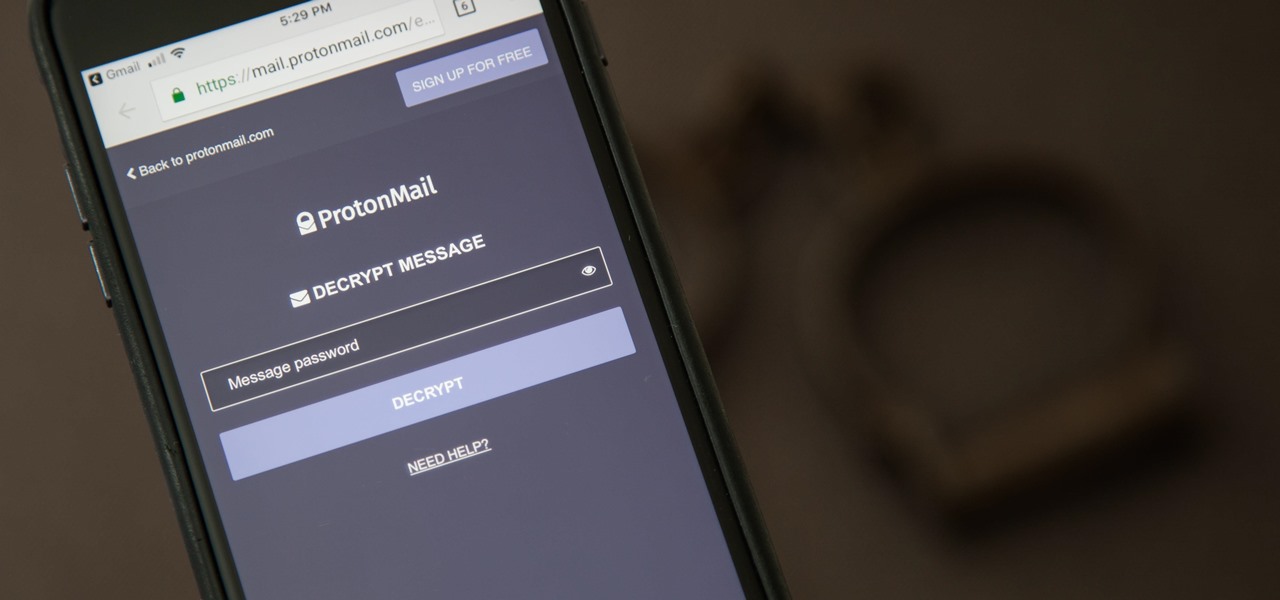
It can be hard to get all of your friends, family, coworkers, and acquaintances to jump on board with the more-secure email system ProtonMail, but that doesn't mean you can't still send them encrypted emails. Best of all, they won't even have to install any other apps or extensions to read or reply to the messages.

In this clip, you'll learn how to use the VSN plug-in to encrypt email in Microsoft Outlook. It's easy! So easy, in fact, that this helpful how-to can present a complete overview of the app in just over five minutes. For more information, including detailed, step-by-step instructions, take a look.

If everyone in the world properly secured their email account there would be no spam. But yeah… never going to happen. That's more of a reason to encrypt and digitally sign our emails, but isn't using p2p security really expensive and really hard? Nope. It's actually free and easy with GnuPG. It's demonstrated on Mac OS X, but it's just as easy with Windows.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

Due to the overnight success of smartphones, millions of people are connecting with others. Currently, over 15 million text messages are sent every minute worldwide. Most of this communication is happening in the open where any hacker can intercept and share in the discussion unbeknownst to the participants. However, we don't need to communicate insecurely.

Signal, the encrypted messaging app, has seen 1.4 million downloads in just the first quarter of 2017—roughly twice the downloads it received in the same period last year. Rani Molla at Recode attributes this to Donald Trump's inauguration, as the private messaging service saw a 40% increase in US downloads between Election Day and the end of the first quarter of 2017.

Welcome back, my nascent hackers! In the conclusion of the Mr. Robot television series, Elliot and fsociety successfully completed their mission of encrypting all of Evil Corp's data with AES-128 encryption and destroying the key.

If you have some photos, videos, and documents that you want to keep completely hidden and encrypted on your Android device, Andrognito is the app you need. We showcased this app in the past, but since then, CODEX has rebuilt it from the ground up with new and improved features.

Make sure your private documents are completely secure. This episode by Tinkernut deals with not only encrypting your files, but also hiding them in a hidden volume.

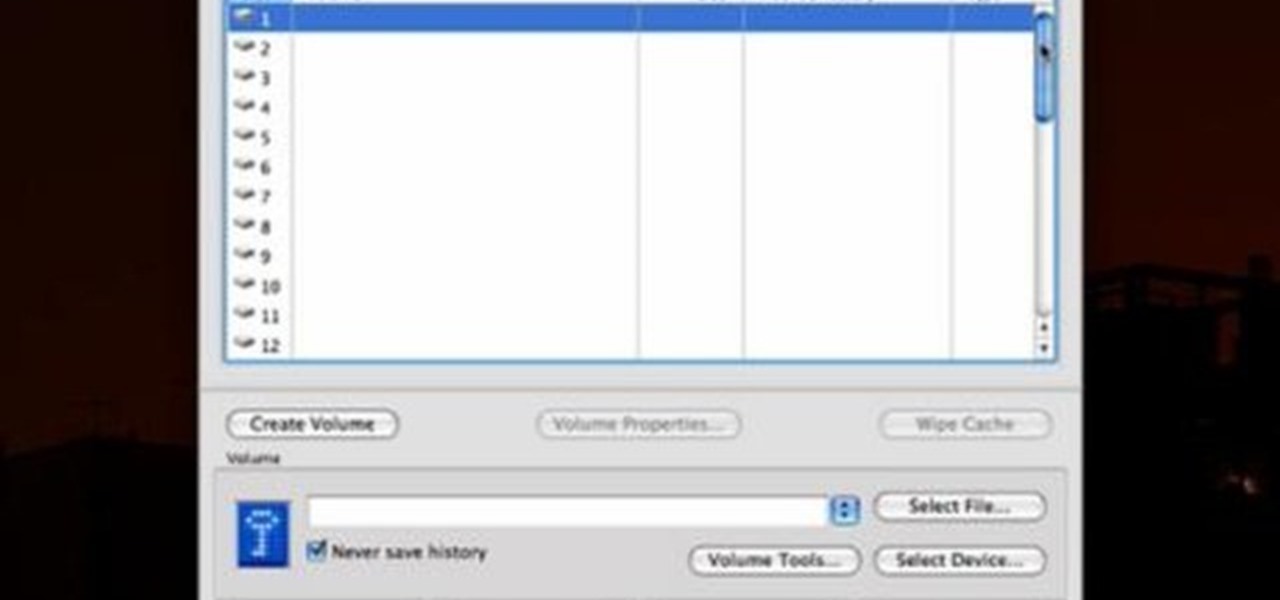
TrueCrypt is a free application that lets you encrypt designated programs on your Ubuntu system to prevent unwanted access. Provided you select a strong password, intruders will not be able to open your personal files and documents. This instructional video walks you through the process of installing TrueCrypt on your Ubuntu operated machine and demonstrates an example on how to create an encrypted volume within a select partition.

Check out this video tutorial on how to hack into WEP encrypted wireless networks. The aim of this video is to show people how easy it is to crack a wireless network with WEP encryption. Seriously, if you know how to do it, even a little kid could if you showed them how. Now that you know this, you should upgrade to WPA! It is much harder and takes much longer to crack.

Want to make sure a message doesn't fall into the wrong hands? Try embedding it in a web image. With the Mozaic Encrypt web app, it's both quick and simple. For all of the relevant details, and to get started adding secret messages to image files yourself, watch this home-computing how-to from Tekzilla.

Hello people again, I wrote my last post about crypto about 10 months ago, now I will introduce something not fresh for the science, but fresh for the people who wants to learn. In my http://null-byte.wonderhowto.com/forum/cryptography-0161538/ post of crypto concepts, there is just basics, today we will see something that targets wide concepts like Symmetric crypto, Public Key Cryptography, Hashing, Keys etc...

BitLocker. What is it? And what can it do for you? Well, it's a handy new feature built-in to Windows 7, and it can help protect all of your data from loss, theft, or hackers. It's the easiest way to make sure your documents and files are safe from the devil's hands.

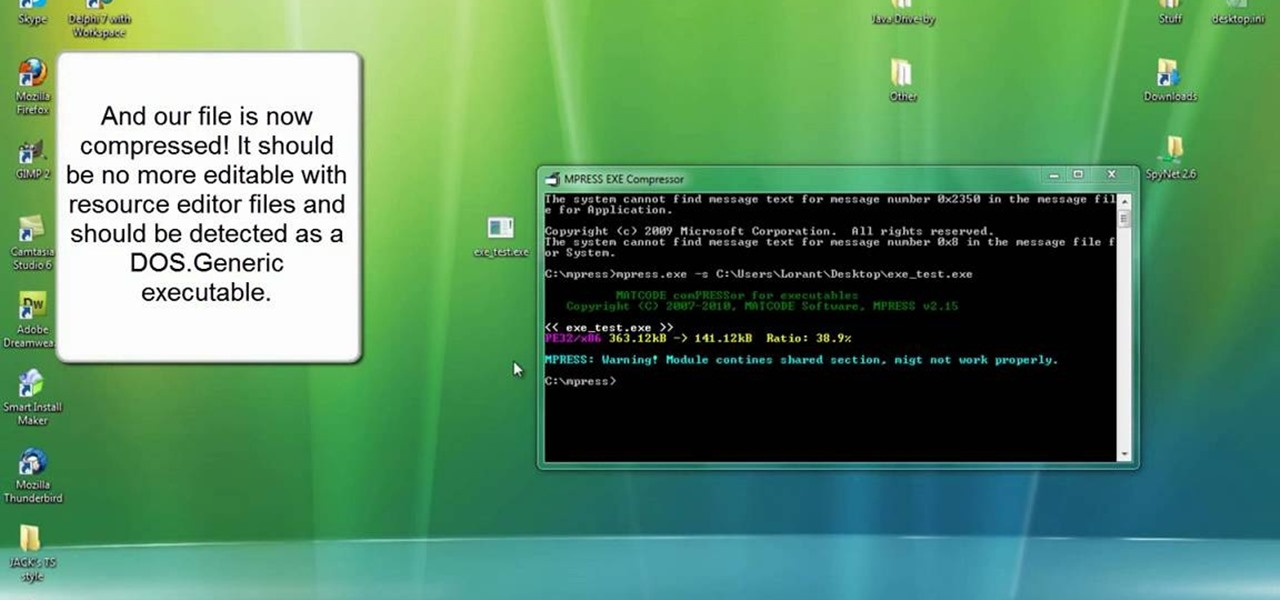
For the newer generation, using a computer is now a common thing that a lot of people must know how to do. Regular things like opening programs, writing papers, and using the internet are all easy to get, but there are other things that can be a bit harder for those less experienced. So if you're starting off or just looking to learn something new, this video can help. In this tutorial, you'll find out how to compress and encrypt an .EXE file for free using MPRESS. Good luck, pay attention, a...

Check out this video tutorial to see how to keep your private files private, even if you have to email them to yourself at your office? TrueCrypt, an open source piece of software, lets you encrypt your files so they remain accessible only to you. This works on any platform; Windows, Linux, or Mac. So, watch this video to see the TrueCrypt download process, how to install it, and how to create an encrypted volume on your hard drive.