In this video, you'll learn how to convert format files accurately and for free in two different ways. You can use a program called Format Factory, which you can download here, or you could use a website called Zamzar.

Because Call of Duty: Black Ops doesn't stack killstreaks in multiplayer mode, it can be more difficult to go flawless. Make sure you pick a gun that you are comfortable with, and also choose a map that will help you.
In this clip, you'll learn how to make VOIP (or voice over IP) phone calls over your Windows PC. For more information, including a complete demonstration and detailed, step-by-step instructions, and to get started making phone calls over your own Internet connection, watch this handy home-computing how-to from the folks at CNET TV.
Looking for a convenient way to make calls over the web? With Gmail's new VOIP feature, it's easy! So easy, in fact, that this home-computing how-to from the folks at TekZilla can present a complete overview of the process in just over two minutes. For more information, including step-by-step instructions, take a look.

It seems like everyone has Caller ID these days, but not everyone wants to give up their privacy. Whether you're calling from a cell phone or a landline, you can dial *67 to block your phone number from appearing on Caller ID, and many phone companies offer a permanent option as added service.

In this clip, you'll learn how to make "cold calls" when searching for a job, a technique that can be surprisingly effective. Finding a job can be a tough task even in the best of times. Whether you're out of work or are simply looking to land your dream job, you're sure to be well served by this clip, which discusses few tried and true techniques and best practices for job seeking.

In this video tutorial, viewers learn how to use the Nokia N97 phone. The power button is located on the top of the phone to turn on/off the device. The menu key will open a list of applications for use. The call key will allow the users to make a phone call. The end key will bring the user to a previous screen or end a call. There is a headphone jack at the top of the device. One the side there is a Micro connector, and lock key. This video will benefit those viewers who are just using the N...

If you have a new Land Rover and a Bluetooth enabled cell phone, you can pair them together for simpler in-car calling. This method of calling is safer and easier than holding a handheld or fumbling with a headset. Follow along with this video and connect your mobile device to the car for use anytime.

The catcher is the player on the baseball field on whom the most difficult mental and physical demands are placed. They have to squat for long periods of time, defend the plate from slides and, most importantly, call the game for the pitchers. This video teaches you, as a youth baseball coach, how to train your catcher's mind to make them better at calling games and improve the performance of your whole pitching staff.

Get started in the world of crochet? Get educated about the triple treble stitch with help from this video! This stitch is very very high if you crochet it in thick wool... It's best to be used with fine cotton.

In this video Mike Callahan walks you through using Skype on the iPhone. To start, download it from the Apple App Store. Next, launch the application on your iPhone. It will immediately prompt you to enter your name and password. If you don't have one you can use this screen to create one. Once you've logged into your account you'll see your list of contacts. Touch one of your contacts to place a call to them. There is a call option at the bottom of the screen that will launch your dial pad. ...

Childcareland demonstrates how to make a Thanksgiving book of thanks with kids in this video. A book of thanks can be done by a group or an individual. It begins a title page which can be labeled to reflect whether it is an individual book called "My Book of Thanks" or an group book called "Our Book of Thanks" or a general book called "Book of Thanks". The back page is a blank match of the cover page. In the middle are five pages labeled "I'm thankful for" with a line for older children to wr...

This is a video walkthrough of Mission 2: "Little Resistance" in Call of Duty 4 World at War. This includes cheats, glitches and quick play strategies. This game is a first person shooter (FPS).

This is a video walkthrough of Mission 8: "Blood and Iron" in Call of Duty 4 World at War. This includes cheats, glitches and quick play strategies. This game is a first person shooter (FPS).

Chad Schearer, world champion elk caller, magazine editor, television host, and outfitter and guide offers tips at the Internaitonal Sportsmen's Exposition (ISE) sports shows on how to put together bull and elk calls that'll work!

Is a constantly running toilet driving you mad? Don’t call the plumber until you try these simple adjustments. Don't waste your money just yet- watch this instructional video on how to fix a running toilet. You will need a faulty toilet and some food coloring.

Learn how to play The Calling's big hit, "Wherever You Will Go" on acoustic guitar. This song had some pretty easy chords, a bit of thumb over action and some tricky right hand picking. Follow the steps in this tutorial to play acoustic guitar like Aaron Kamin from the Calling.

This how to video teaches the hip hop line dance called the "Booty Call." This dance is often done to "Gyrate" by Da Muzicianz. Follow the steps in this tutorial and you'll be dancing this sexy line dance in no time.

Check out this instructional video for making closed reed predator calls.

A pre-release version of fring for the iPhone available from fring.com. This is a great App that lets you use your iPhone to instant message or Skype. Never pay for international calls again!! This is the new release for 1.1.4 Jailbroken phones.

Around here we call them "Jacks Ribs" but typically they are known as Country Style Pork Ribs. They are simple to grill and a great recipe to have on hand if you need a quick and easy meal from the BBQ grill. Although most Rib men describe this cut more as a "chop" than "rib", the pork industry prefers to call them Ribs. So Ribs they are!

If you want to block your cell phone number for all calls, this is the video for you. Learn to block not just one call, but all further calls with the push of a few buttons. Now no one will be able to see your cell phone number.

It's a myth that regular users only need the protection of a virtual private network when on a public Wi-Fi connection. First, almost all network connections can be accessed without the proper permissions. Second, ethical hackers also need to think about using a VPN as one step to encrypting and protecting their activity and identity during pentests, phishing, and other actions.

Since Apple launched iOS 13, we've seen four major updates for iPhone, each of which added some cool new features. Between iOS 13.1, 13.2, 13.3, 13.4, and all the minor updates in between, there's never been a better time to be on iOS. And now, we've got even more positive changes with the iOS 13.5 update.

If you want to carry a variety of network adapters without looking suspicious, a perfect solution is accessing them through Airserv-ng. Tucked away in the Aircrack-ng suite, this tool allows a hacker to plug any number of network adapters into a Raspberry Pi and access them over a Wi-Fi or Ethernet connection.

You've probably heard of RCS messaging. The new standard has been promoted by Google as their answer to iMessage and is the backbone behind the new "Chat" features in Android Messages. With RCS, Android phones will now enjoy enhanced messaging like iPhone users have had for years — but is it really the same?

Traveling abroad can be a hassle. Between the flight, hotels, food, and the languages barriers, it can be a lot to manage. There's one tool you have that can help with all of this — your smartphone. Fortunately, nowadays, you don't have to change your carrier to continue using your phone.

Depending on your region, you may not be offered the same call recording option other OnePlus users have. But, as with most things Android, where there's a developer with a will, there's a way regardless. And the method we are about to describe is one of the easiest, most stable, and undetectable ways to do it. Perhaps we should discuss why OnePlus has been holding out you when it comes to this feature, though.

If you've ever been on the receiving end of a threatening phone call, you'll immediately know the value in being able to record phone conversations on your iPhone. Beyond that extreme example, however, recording calls is still an extremely useful feature to have for important conversations like business meetings and verbal agreements, and it's totally doable with a third-party app.

From its introduction and all the way through iOS 11, FaceTime has been restricted to one-on-one calls. Apple will be changing that in a future iOS 12 update with Group FaceTime, which adds support for up to 32 people total in group audio and video calls. But that's not all we'll be getting in iOS 12 — there are more features that FaceTime has or will be getting soon that you should know about.

One of the main reasons Authy was able to top our list of the best two-factor authentications apps was its ability to transfer access to a new device. This feature ensures that whenever you get a new phone, you don't lose all your tokens. However, if the process is done incorrectly, you can leave your account vulnerable.

Incoming phone calls and FaceTimes, whether you want to answer them or not, will take over your entire iPhone's screen — no matter what you're in the middle of doing on the device at the moment. You could be browsing the web, playing a game, or chatting on social media. It doesn't matter, you'll get interrupted. But you don't have to put up with it anymore.

Front and center for iOS 12 this year is Group FaceTime, which allows users to chat with up to 31 additional people at once. While that ambitious feature is sadly delayed, don't cast away FaceTime just yet — you can always pick up your iPhone and start a call with any single contact directly from the Messages app.

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

I've called 911 accidentally more than a few times on my iPhone using the Emergency SOS triggers, but it's also just as easy to trigger an unintentional call to emergency services using an Apple Watch. These accidental 911 calls can put a strain on local public-safety answering points, or call centers, as well as local authorities and emergency medical technicians.

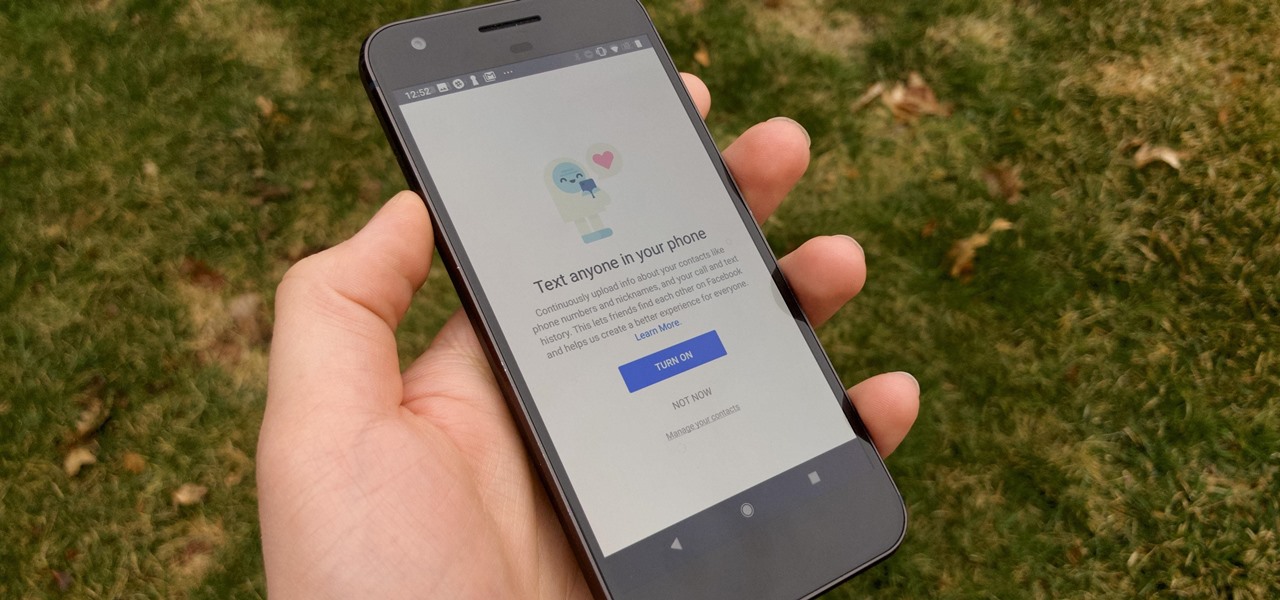
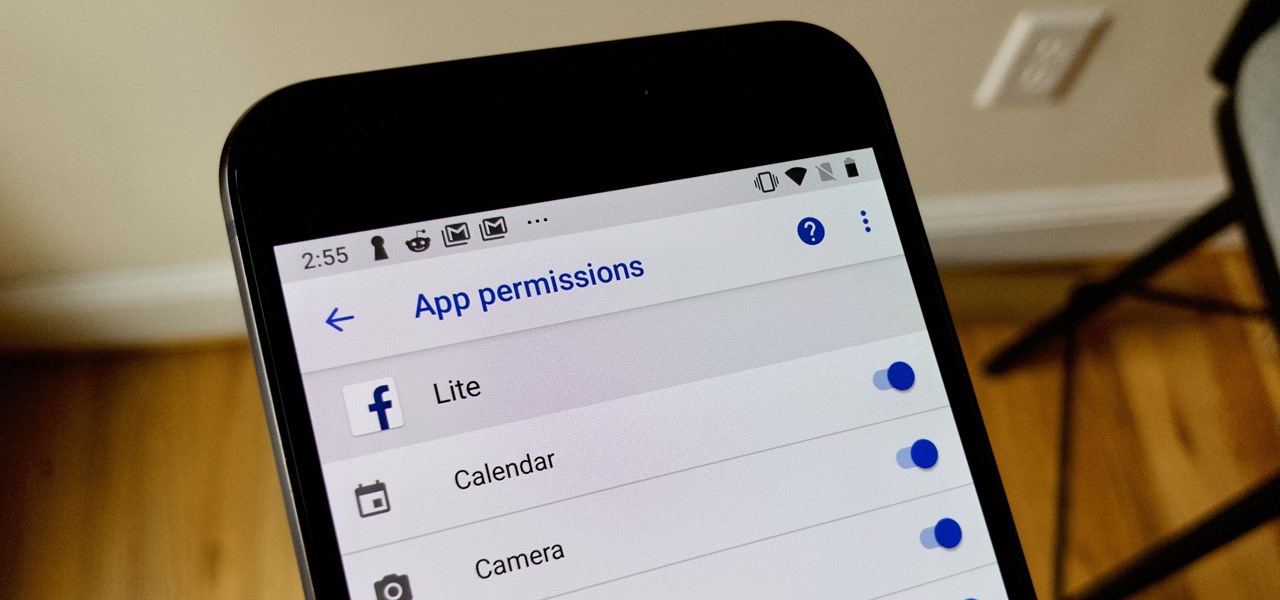
It hasn't been a great year for Facebook. Recently, Android users had to discover on their own that the company was logging their calls and texts in Messenger. However, according to Facebook, all users did approve of the data collection, and as such, all affected users can disable logging as well.

The Android world exploded when it was discovered that Facebook was logging the call and text histories of many of its users, although the company claims those users had explicitly given Facebook permission to log that data. The case remains that many users were unaware of this activity, which occurs on both Messenger and Facebook Lite. Luckily, it's very easy to disable.

Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless attack framework called Airgeddon is used to find vulnerable networks, and then Bully is used to crack them.

When you don't want somebody you're calling to know the real phone number associated with your iPhone, whether it's for privacy reasons, to avoid being called back, or to prevent being ignored, there are multiple things you can do to block it on their caller ID.

The app that started as simply a photo-sharing social media platform has expanded to encompass so much more than that. Between live videos, stories, chat, and animated stickers, Instagram is more than the sum of its pictures. Now, there's a new feature to add to that list for Android and iOS — video and audio calls.