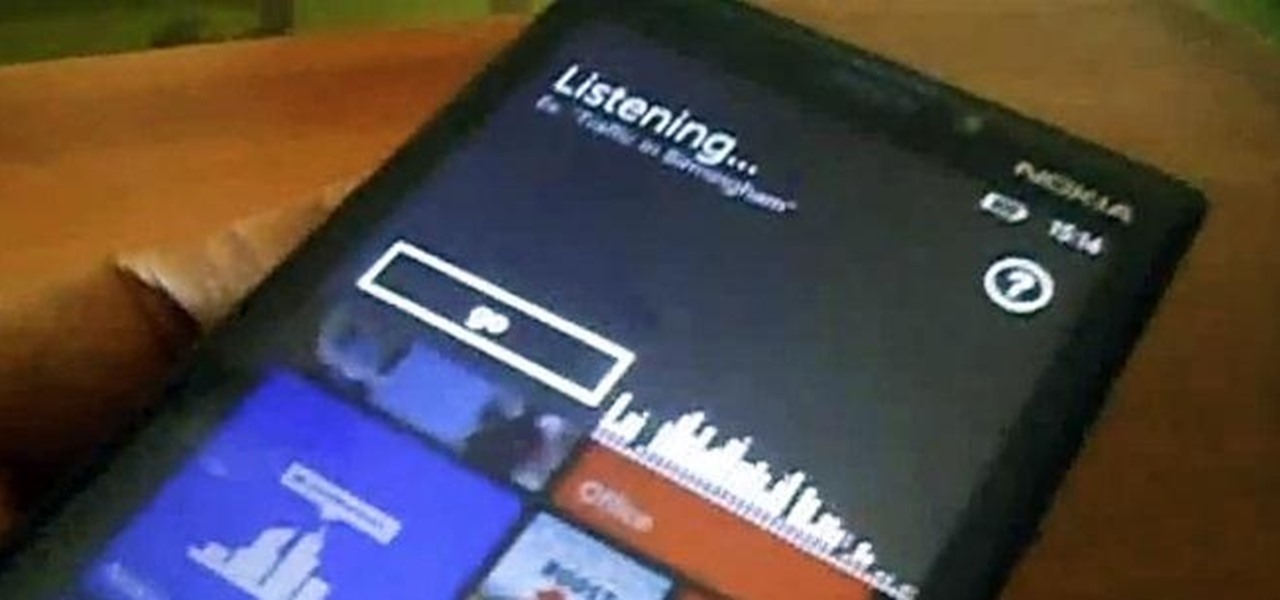
The beta firmware for OnePlus devices lets you record calls from the stock Oxygen OS dialer, but this feature is never included in official updates. This is likely due to legal issues with recording calls in some jurisdictions, but thankfully, there's a way to get this feature without having to run beta software.

While clicking random links on the internet probably isn't the best idea to begin with, now you can rest easy knowing that your iPhone won't repeatedly dial 911 after tapping a malicious link in Twitter, Facebook, or other apps that use iOS's WebView.

During the last few months, WhatsApp's Google Play Store ratings have been tanking—all the way down to an average of 3.4 stars from the instant messenger's usual average of 4.1. Within the last week, though, WhatsApp has received thousands of seemingly fake 5-star reviews that have bumped up the company's overall average to a 4.4.
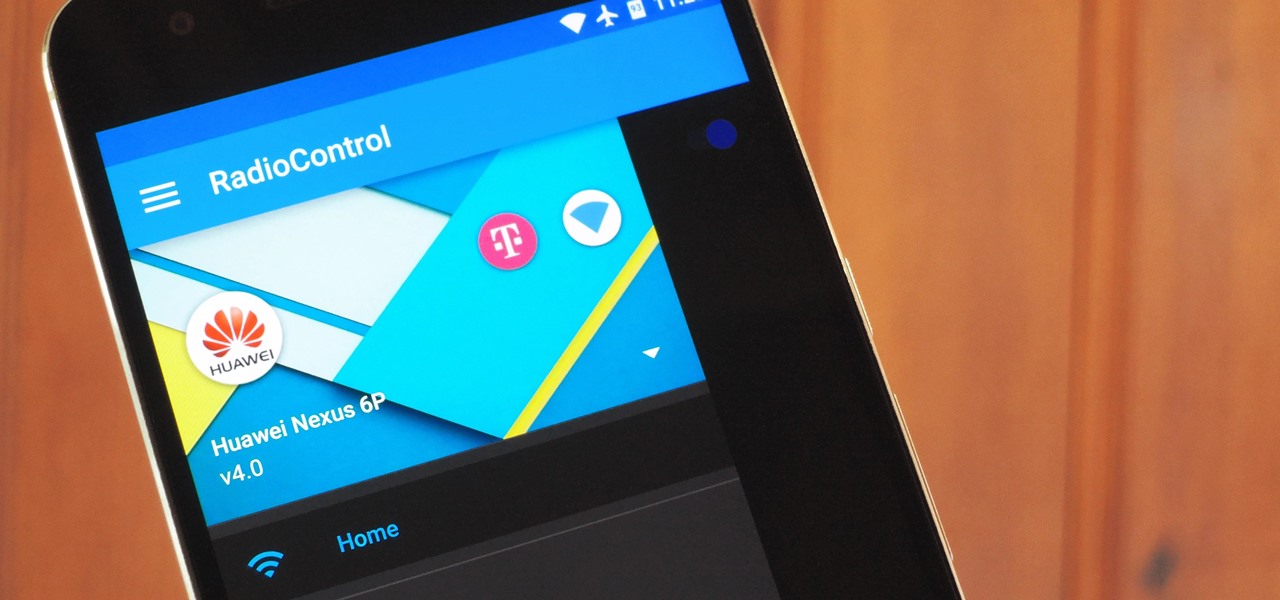
One of the biggest causes of smartphone battery drain is the mobile data connection—particularly if you live in an area with poor reception. But, chances are, you don't actually need this connection most of the time, because you're probably connected to Wi-Fi for a good chunk of the day, which uses far less battery life.
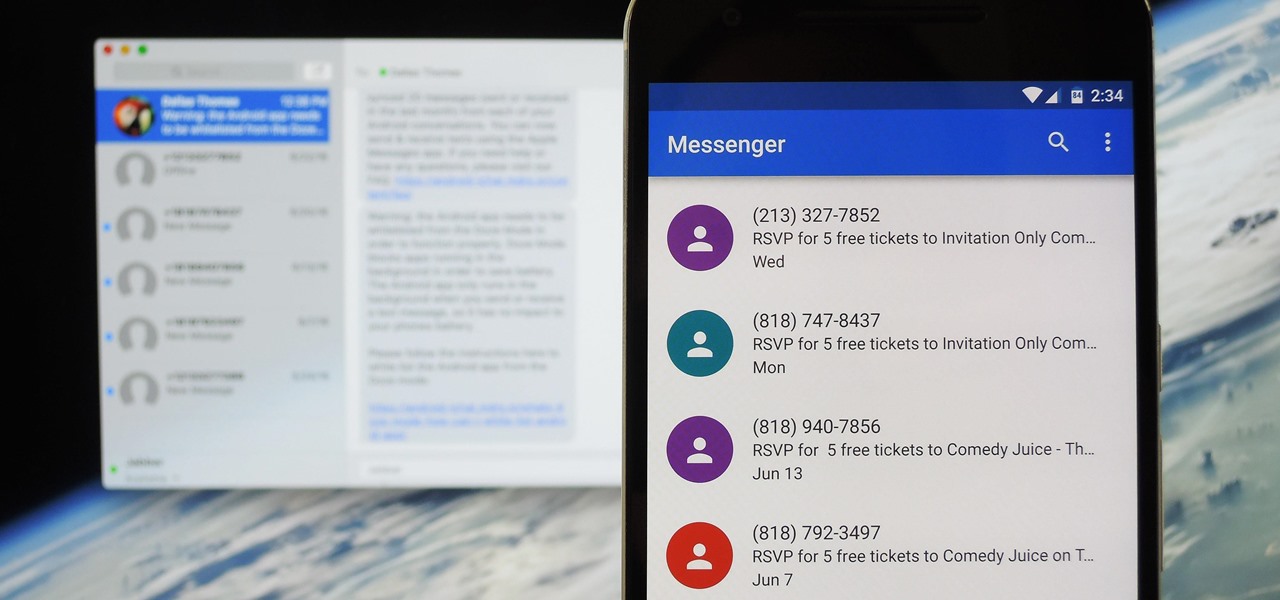
Prior to this year's WWDC, there were lots of rumors that Apple might finally be making a version of iMessage for Android. While that never came to fruition, a few big updates to a very useful app have now ensured that we can seamlessly send and receive Android texts in Apple Messages on our Macs.

The desktop browser market has some stiff competition going on, but Opera has always been able to maintain its market share by offering innovative features such as a data saver option. With over 350 million users, it's safe to say folks are appreciative of the efforts being made by the web browser's development team.
Most of you lot would be aware what WPA/WPA2 is so I won't bang on about the encryption or protocols a great deal. In short WPA and WPA2 both have a maximum of 256bit encrypted with a maximum of 64 characters in the password. The encryption is really only 64bit but x 4 because of the way the authentication functions as a 4 way handshake.
Hello guys I am ROMEO 64 (sounds weird I guess but who cares. :D).. Alright....Ever wondered what happens when you login to your Facebook account?

If you have personal information stored on a Kindle Fire tablet, be warned that Amazon has removed encryption support for Fire OS 5. So if you have stuff on these devices...maybe a risque book, or private notes, or pictures you'd rather not let out to the world, now would be the time to remove them. And unless Amazon changes its mind and re-enables encryption, don't use your device for anything personal, as anyone who gets a hold of it will be able to gain access to everything on it.

Welcome to a tutorial on crypting technology. In this article, we will be discussing types of crypters, how they work and why they work. After defining these, we will then make our own basic crypter using the function I gave to you as a task to complete by yourself in the previous tutorial.

Hello my fellow hackers, it's been a while since my last post, I can't get the time now-a-days for the posts but can manage to tend to comments.

T-Mobile's credit-checking system was recently hacked, and this one is about as bad as it gets. The names of 15 million customers, their date of birth and social security number, as well as driver's license numbers and additional information was illegally accessed, meaning the potential for identity theft here is huge.

If you have a ton of photos and videos on your iPhone, backing up to iCloud is probably a no-go since it only provides 5 GB of free storage. Yes, you can buy more storage, but who wants to do that? And what happens if you run out of storage, stop backing up, and your phone gets lost, stolen, or damaged.

When ringtones and vibration alerts miss the mark and fail to grab your attention, causing you to miss an important call or text, LED flash alerts are a great backup plan. While we already showed how to activate this on Samsung devices, the apps shown below make this feature easier to toggle on and off. Plus, they work on devices that don't have flash alerts included in the system settings.

Get some tinfoil hats and make a time machine because we are about to go back to the 90s and learn about some phreaking.

Every so often, we come across an app that makes us wonder "Why didn't someone think of this before?" This is definitely the case with developer Dor Sakal's latest offering, FloatNote.

This video will show you how to block or unblock someone from calling and sending your messages in your iPhone or iPad. So please watch the video and follow all the steps carefully. Employ the technique in your iPhone or iPad.

Only scumbags hide their call and message history, right? Wrong. While it may seem like a tactic for the unfaithful, it's still a good thing to do for certain contacts on your phone that you don't want to block outright.

Accessing your recent contacts just became a hell of a lot quicker with iOS 8. In addition to accessing recent apps, double-pressing your Home button now shows off recent contacts at the top of your screen.

I'm a textaholic, as I've said many times before, but even textaholics forget to respond sometimes. When I'm watching a YouTube clip or devouring delicious snacks in Candy Crush Saga, I'll often ignore incoming texts and forget to respond later.

Privacy features have become quite the hot commodity, emerging from the aftermath of the NSA scandals that rocked the United States this past year. While the NSA has the means to gather information on all of us (regardless of any security software we implement), it doesn't mean that they're the only ones looking.

We've all been there. Our phone rings, but we're at a concert or dinner and don't want to spend time sending a text explaining our whereabouts. While ignoring a call is easy, it isn't always the most polite thing to do.

Wouldn't it be cool to know exactly who is calling or messaging you without ever looking at your phone? It'd be a great way to keep you from reaching into your pocket or purse every time you get a message, and an efficient method to ignore people you'd rather not deal with.

Welcome back, my budding hackers! I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques is the antivirus (AV) software on the target system. For instance, if you try to email a malicious PDF or Word doc, it's likely that the victim system will alert the victim that it contains a virus or other malware.

Ringing and vibrating alerts on your smartphone can be a bit distracting when you're at work or school, but silent alerts can be a little too subtle if you want to know when you get a notification. Even the tiny LED alerts can be easily missed. So, is there's something in-between loud and almost-not-there alerts? In today's softModder tutorial, I'm going to show you how to get flash alerts on your Samsung Galaxy Note 2 and other Android devices. That way, whenever you receive a call or text m...

I used to have nightmares when I watched Terminator 2. I mean, I didn't step on a playground for a least two months after I saw that movie. There was something terrifying about computers having so much intelligence.

A lot of people text nonstop, but there are situations where it's either not allowed or considered rude to use your phone. Let's say you're in class or in a meeting at work, band you're expecting an important message or phone call. Rather than trying to check your phone discreetly, wouldn't it be better if you could just see your calls and messages on your computer?

Live Beyond Feng Shui consultation by Master Aur with guest Janine from Brisbane Australia. In this call Aur shows how that just by seeing a floor plan we are able to know many intimate details about a persons life.

Having all of your stuff in the cloud is super convenient if you want to access it on multiple devices, or if you want a backup in case it gets lost or wiped. The biggest downside with services like Dropbox, though, is security. With everything sitting there in one place, the last thing you want is for someone to break in.

In college, I enjoyed eating, sleeping and making my roommate's life a living hell. My most satisfying prank involved 500 red cups stapled together, filled with water, and strewn across his bedroom floor. He was not happy. To clean up, he had to unstaple each cup, carry it to the bathroom, and dump the water. He was furious, but I was okay with sacrificing our friendship in exchange for a fantastic story that I'll probably tell my grandkids one day. If you're not as cruel as me, there are oth...

Earlier this week, Spiderlabs' vulnerability researcher Jonathan Claudius discovered a key in Windows 7 and 8 registries that makes it easy for anyone with physical or remote access to a computer get a hold of the user's password hints. When the "UserPasswordHint" key is read, the hints are displayed as a code that looks encrypted, but Claudius noticed a pattern of zeroes that could be easily translated back to plain text with a decoder he made in Ruby. He added this functionality to the Meta...

There's nothing worse than losing your phone—except losing your phone when the ringer is silent. If you're alone, it can be excruciatingly hard to find your lost device even if the ringer is on, considering most of us don't have landlines anymore. So, the next time you find yourself hunting for your phone, don't tear your house apart until you've tried some of these quick tips.

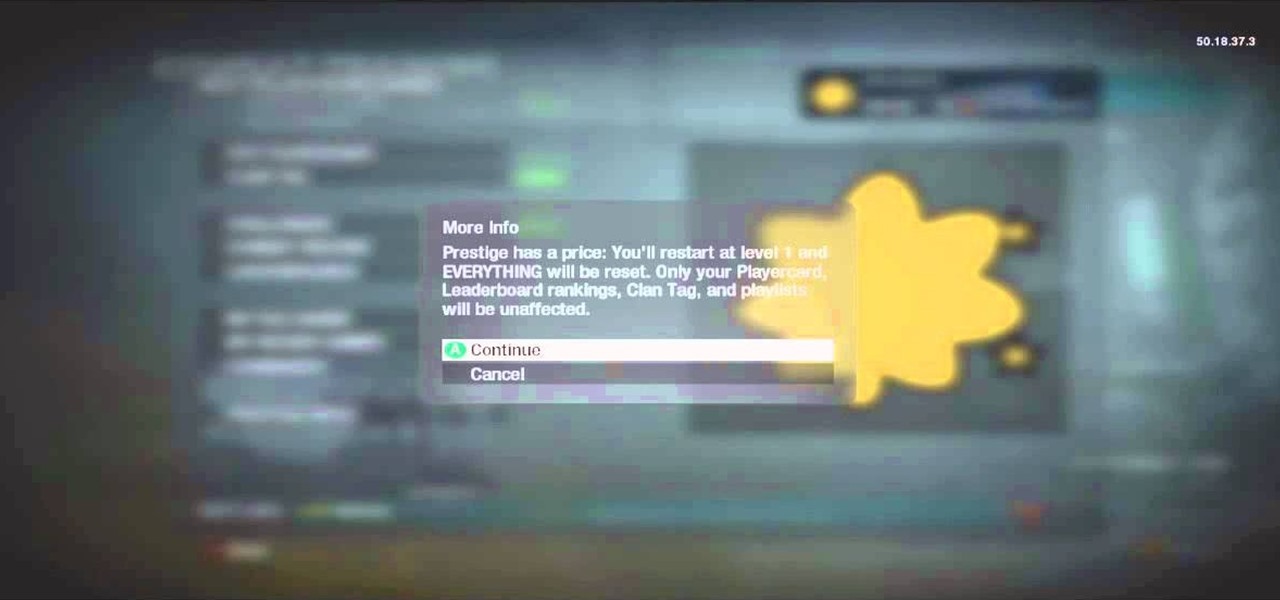
Okay, this is SO mean. But if you've got a friend (perhaps a frenemy) who annoys the hell out of you then you can pull this super awesome XBox 360 Call of Duty Black Ops prank. Your friend needs to be level 50 (doing combat training) in order for this to work.

Video game controllers are designed for just that: playing video games. When you try to use them for other things it seldom works well, and making custom Call of Duty Black Ops emblems is no exception. Fortunately, this video is here to teach you about a free web app you can use to make custom emblems on your PC with a mouse, which is much better suited to the task. It also allows you to use more types of images and textures from Photoshop and elsewhere.

The only way to get the "Sacrificial Lamb" achievement in Call of Duty: Black Ops is to be playing in multiplayer mode in Black Ops Zombies. It could be done on any map in Black Ops Zombies, and you could probably guess what needs to happen to get this achievement on the Xbox 360. Somebody's got to die. Who will it be? You? Or the other guy?

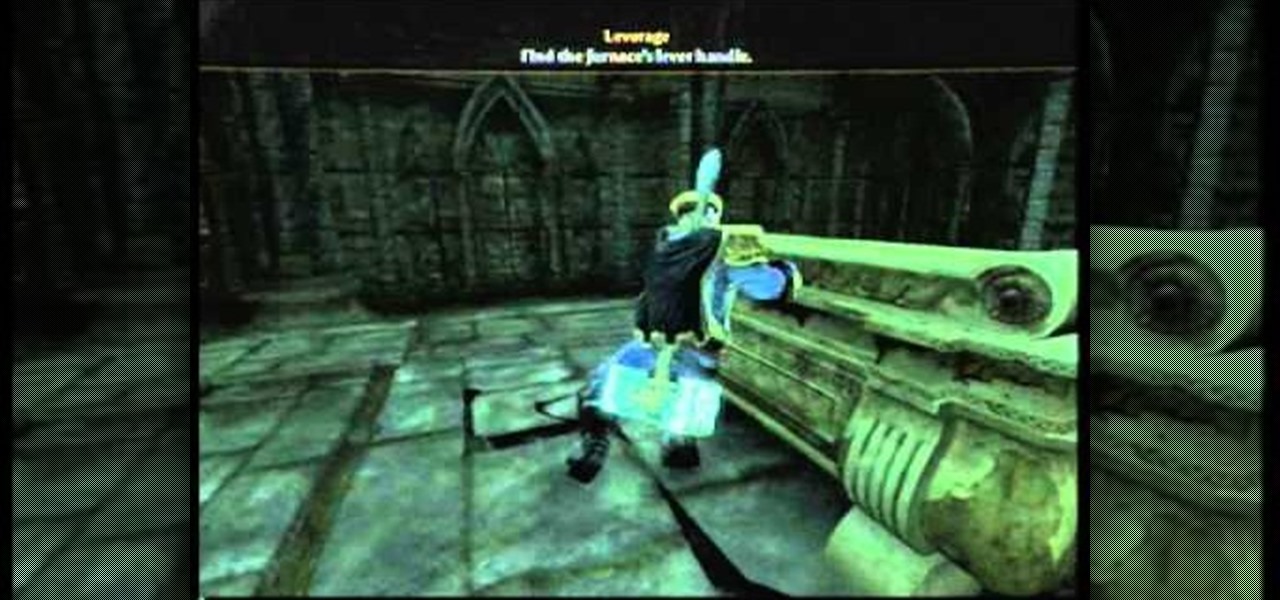
The Dark Sanctum Achievement in Fable 3 is a practical and fun one to unlock, and you need to do it to get The Tenderizer, one of the better legendary weapons. Watch this video for a walkthrough of how to get the Dark Sanctum, starting from the quest called "Leverage"

The Golden Egg is perhaps more of a state of mind than a posture in yoga. The Golden Egg involves sustaining and concentrating your core strength, creating what Sadie Nardini calls an "abdominal balloon."

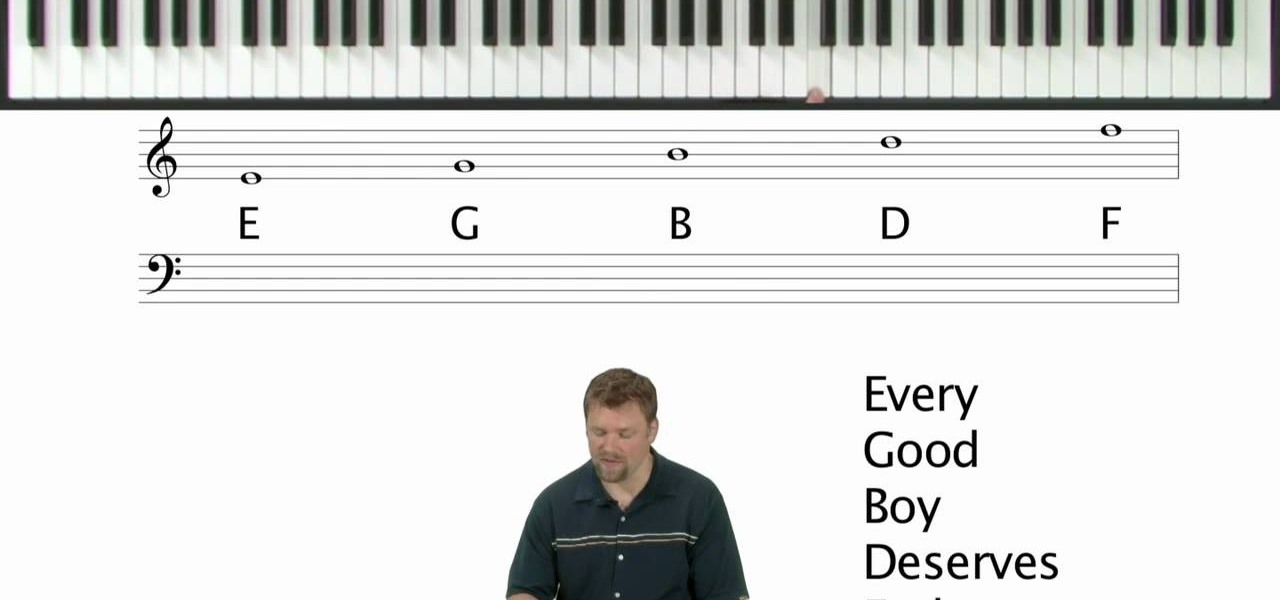
In this tutorial, we learn how to start reading sheet music for the piano. To be able to read the notes, you need to visualize what you are doing on the piano. A good starting point is the middle C on the keyboard. For a piano, you have horizontal lines in two sets on the sheet of paper. These lines are called "staffs" and the vertical lines are the "bar lines". The sections are called "measures". The top of those staffs is all the notes above the middle c. The bottom is all the notes below m...

In this video, Linnea Rose teaches us how to paint in a Norwegian folk style called "rosemaling". With this, you will double load your brush and do the strokes in the correct way. To double load your brush, first dip one corner into a color, then dip another color into the other color. After this, stroke again in between the two colors. Next, go to your canvas and simply stroke a looped shake on the paper. Firmly press down with your brush and as your curve around you lift it up to the chisel...

Call it what you will—puke, vomit, upchuck, barf, regurgitation—no matter what it's called, it always has the same sickening effect on people when they see it. Sometime it's like a yawn and can be contagious. That's what makes this the perfect prank, but there's no need to stick your finger down your throat! You can mold some fake vomit with this how-to video.