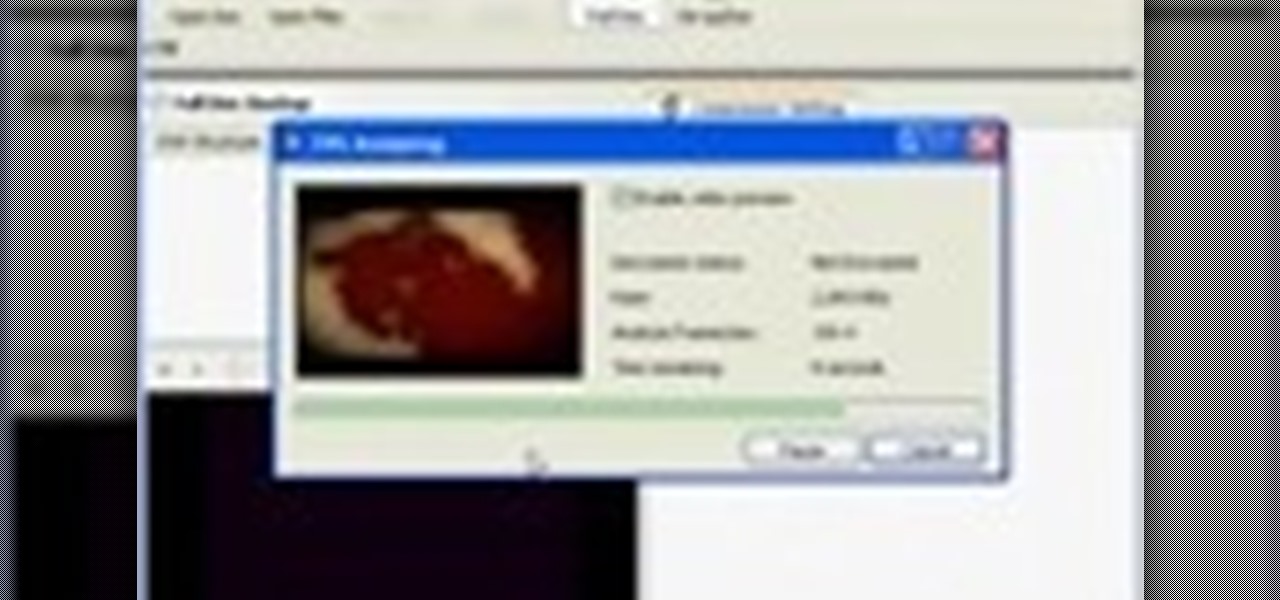
A tutorial on how to "break in" to your Windows machine after you have lost the password. This works in Windows NT, 2000, and XP machines without an encrypted file system. I then show you how to wipe a hard disk to assure no one can gain access to your data once the drive is sold or discarded.

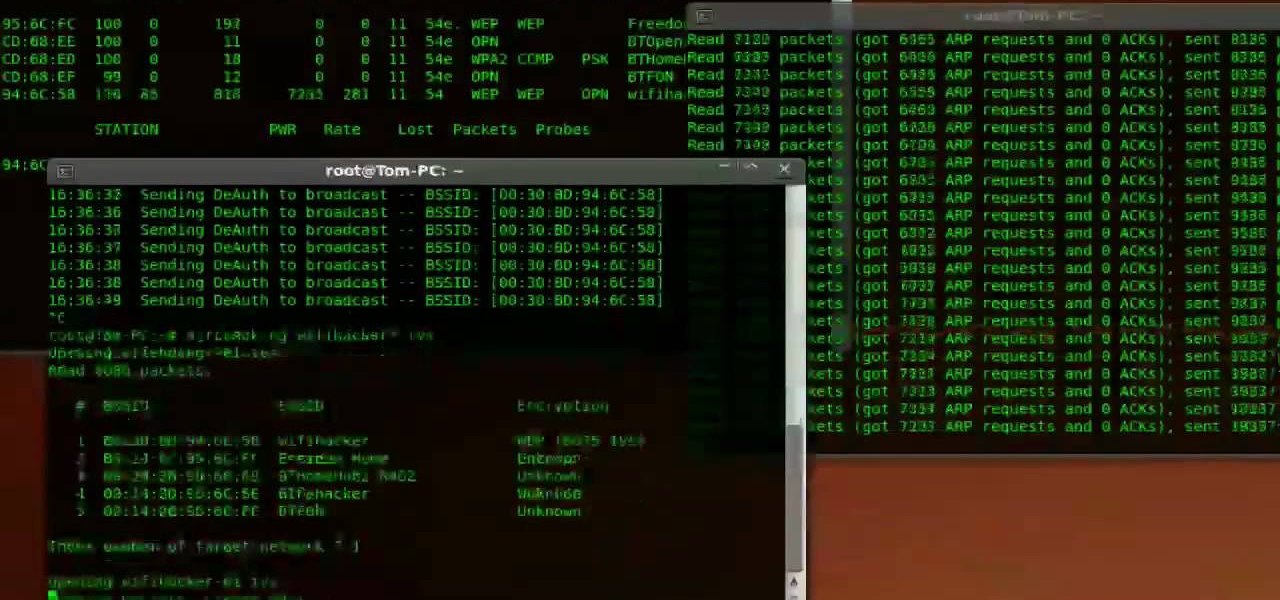
This is the second episode of Full Disclosure by InfinityExists.com. This episode includes how to crack WEP encryption, and why it can be cracked so easily.

As of 2016, there are approximately 1.85 billion Android smartphones worldwide. This growing popularity has led to an increasing number hacks and cyber attacks against the OS. Unfortunately, Android users need more protection than what is offered by Google. The good thing is that there are a number of options available.

Last month, it was revealed that Juniper Networks' routers/firewalls were hacked. It was reported that a backdoor was implanted in the operating system of their routers/firewalls and that attackers could listen in on all encrypted communication. There are now fears that all confidential communications by U.S. government agencies and officials could have been compromised over the last three years.

One thing that makes Signal Private Messenger better on Android over iOS is that you can better secure the app with a password or passphrase. Best of all, you don't need to install an app locker to get this working — you can do it right from inside Signal.

Welcome to a tutorial on XOR encryption. We'll be looking at what XOR is and how we can use it to encrypt or decrypt data.

Want the next level security? Well then take a read here because this is some next level stuff. Heard of It?

Almost 20% of the US population (about 60 million Americans) live in rural areas where mobile reception is weak or nonexistent. In times of crisis, these Americans can't rely on the internet to communicate with loved ones or receive new information. This is why being able to interact offline is so important.

While MacOS computers have been spared from some of the most famous malware attacks, there is no shortage of malicious programs written for them. To keep your computer safe from some of the most common types of malware, we'll check out two free tools. These tools can automatically detect ransomware encrypting your files and watch for unauthorized access to your microphone and camera.

This is the very first article in my series on setting up a Mac for hacking. In this series, I will be operating under the assumption that you have a clean install of macOS (previously OS X). If you aren't starting with a clean installation, there may be a few differences, but nothing we can't help you out with.

Hello World ! Well, welcome in my post. This will be in series, and this is first part. Throughout the series, I will share my research and findings with you. And that will be on topic, Encryption Is Not Enough. We will see, how Encryption is broken & what countermeasures should be implemented to secure it. Let's begin, Why do we encrypt ?

As you may have already heard, the worst bug in OpenSSL history went public yesterday, dubbed Heartbleed. While we can go deeper into the technical details of it later, the short version is that OpenSSL, the library used to encrypt much of the web running on Linux and Apache has been vulnerable for up to two years.

We all know about PRISM. The Surveillance Program allowing the U.S Government to access private user information. Such as, Google Searches, Tweets, Facebook Posts, Private Images, and other private user data. "Hiding" yourself can be very difficult, but it is possible. I'm here to show you How to Become Anonymous & Browse the Internet Safely.

Oh how we love open source software. If it wasn't for Open Office, we never would have been able to write that seven-page English paper while on our friend's Microsoft Office-lacking laptop during an impromptu road trip to Mexico. And Ubuntu, an open source secure operating system, offers you similar convenience. A much more intuitive computer operating software than your standard Windows or Mac OS, Ubuntu is great if you know what you're doing.

This tutorial series shows you how to put up an Adobe Air Flex 3 Encryption System. One of the weak points of Adobe AIR and Flex is there is no encryption system built in, making your data and applications vulnerable. But that's ok, because this tutorial will show you how to remedy the problem by adding an AES encryption system.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Whether or not you believe that the government is snooping around in our private emails, texts, and phone calls, it wouldn't hurt to protect ourselves a little better in the digital realm.

Want to be as secure as you can while you surf the web? The EFF and the TOR project have brought you HTTPS Everywhere, a Firefox addon that encrypts as many websites as possible. This clip will show you how to use it. It's simple! So simple, in fact, that this home-computing how-to can present a complete, step-by-step overview of the process in just over two minutes. For more information, including complete, step-by-step instructions, take a look.

Ever have the problem of people messing with your word documents? This guy shows you the solution by telling you how to create password protected encrypted word documents. The process starts with your open file. Clicking on save as... and in the popup window clicking the tools button in the bottom left corner and clicking general options. There it shows you text entry boxes, one for setting a password to open the file, another to set a password for rights to modify the file. Enter your passwo...

In order to secure a PDF with a password when opened in Adobe Acrobat 9 Pro, press the secure button and go into password security settings. Here you can change on what versions of this software the file will run on, the next option asks which portion of the document is to be encrypted when a password is placed. Further below here is where you actually choose the password, this ensures that only people who know the password will be able to see the contents of the document. Below this is the d...

This new episode of Full Disclosure shows you how to use a SSH Tunnel to secure your data when you are on an untrusted LAN (ex. Coffee Shop, School's network, or Defcon). Furthermore, you can use the SSH Tunnel to bypass the LAN's internet filters. The SSH tunnel protocol works by encapsulates your data into an encrypted payload and transmitting it to the SSH Server which is setup on a trusted LAN.

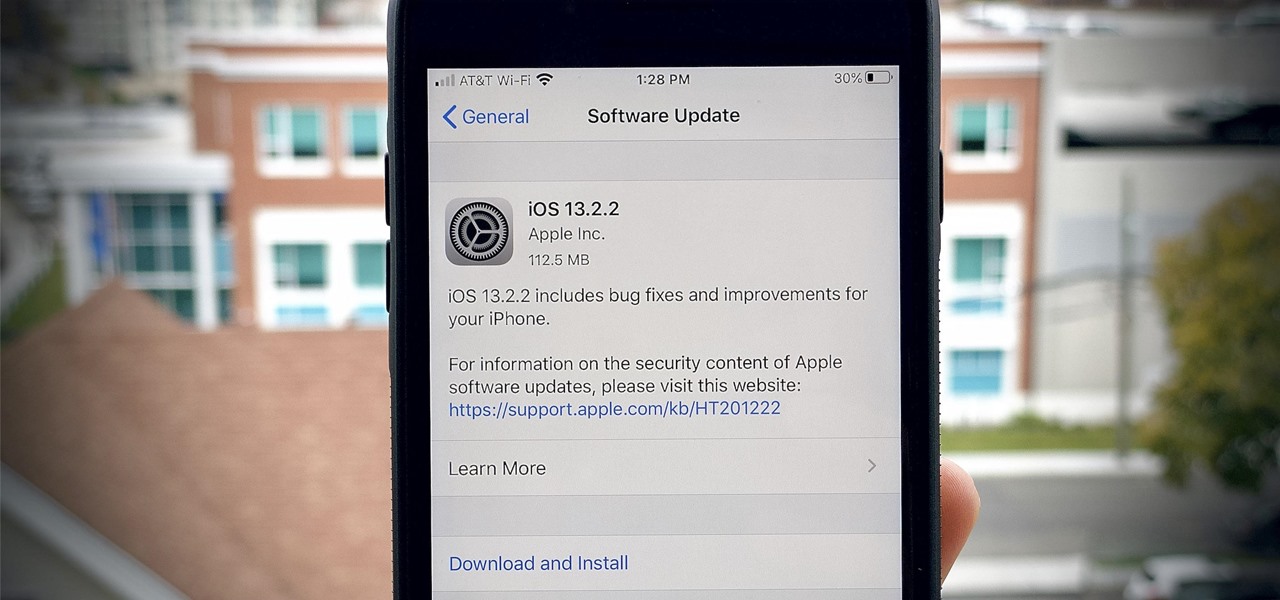
If you're a beta tester, you know Apple released iOS 13.3 this week, bringing with it stability for multitasking as well as minor changes throughout the OS. It seems Apple doesn't want the rest of us to go without this critical patch, as the company releases iOS 13.2.2 today, Thursday, Nov. 7.

If you have friends who aren't privacy-conscious, you've surely heard the old "What do I have to hide?" excuse. Despite the fact that billions of people are using the internet each day, many of them don't know the dangers that can find them. And many don't know the tools to combat them.

New updates to the journaling app Day One include more security for journal writers' data. For example, users can now enable end-to-end encryption. The encryption does not happen automatically; however, users must go to Settings — within Journals — then select each journal they want encrypted.

Hello again, readers! In our previous crypter tutorial, we looked at how we could obfuscate our malware (or any program) by using a simple one-byte XOR key. In this quick tutorial, we will be looking at how a simple little tweak can create a better means of obfuscation. Let's get right into it!
Hello Strangers, This is my first article for null-byte and its about staying anonymous on the Internet. But the question is why would you want to stay anonymous online?

Hello Everyone! I wanted to share a free and open source note taking tool that I've been using for quite some time now.

Security is a priority for many when they first set up their mobile devices. Nobody wants to have a stranger or nosey friend go through their phone and discover risqué photos or embarrassing text messages. These days, the closet is gone—everyone keeps their skeletons in their phones.

Adding to the recent recent slew of bugs and issues within iOS 7, it now seems that emails sent with attachments are not encrypted, despite Apple's claims that they are.

With more people joining the internet scene each day it's important that it's security is.. well it has to be good. Of course everything can be hacked and that's the way hackers work. They know there IS a vulnerability but they don't don't know the rest. in this article i'll try to explain the big difference between HTTP and HTTPS

Windows users have been getting a lot of bad news about their security lately. First, we found out that passwords in Windows 7 and 8 can easily be exploited if password hints are enabled, and now, Russian password-cracking software developer Elcomsoft has found another huge vulnerability.

Various ways to password protect a file or folder using Microsoft Vista are shown in this video. The first step is to choose a file you want to add a password to. After you decide on the file you wish to protect you must right click and select add to archive using Win Rar. After the file has been opened using Win Rar you can then select the add password option to begin encrypting the folder. After you type in the password of your choice you must select ok to finish attaching the password. Onc...

In this tutorial, we learn how to password protect a folder on Windows Vista. To do this, you will first need to have WinRAR downloaded on your computer, you can get it here: http://download.cnet.com/WinRAR-32-bit/3000-2250_4-10007677.html. Next, you will right click on your screen and click "new" and "folder". Then, you will rename your folder to anything you'd like. From here, you will right click and then click "add to archive". Then, go to advanced and set password from the toolbar. Enter...

Do you worry that if your PC is stolen someone can copy all of your data? Then you should encrypt your hard drive and removable USB drives too. In this video tutorial, you'll see how Windows 7 has beefed up Bitlocker, its built-in encryption program, and learn how to use it. It's simple! So simple, in fact, that this home-computing how-to can present a complete, step-by-step overview of the process in just under two minutes of your time. For more information, including complete, step-by-step ...

There are 10 major ways to protect your PC. Disable Autorun, in Windows. Make sure that your system is up to date, by setting automatic updates. Always use a log on for your computer that does not have administrative privileges. Use different passwords, and change your passwords on a regular basis. Don't use simple passwords. Be careful of using links sent to you via email. Never disclose your sensitive information in public forums: e.g. social networks. Encrypt sensitive data on your compute...

In this video tutorial, viewers learn how to copy DVD videos with DVD Shrink. This task is very fast, simple and easy to do. Begin by opening the DVD Shrink program and make sure that you have inserted the DVD into the disc drive. Now click on Open Disc and select the DVD drive from the drop-down menu. Click OK. The program will begin to analyze the DVD. When finished, click on Full Disc, select a folder destination and click OK. Now wait for the DVD to finish encrypting. This video will bene...

The Mac OS's Disc Utility allows for the encryption of files. To open Disc Utility click on the magnifying glass (spot light) up in the top right hand corner, and search for Disc Utility. Click on the first result in the list. Once Disc Utility is open, click on "create a new image" in the top tool bar. A new window will drop down, where you choose what you want to save the new image as. Give it a name, and choose the size you want it to be. Moving down, choose the encryption you want to use ...

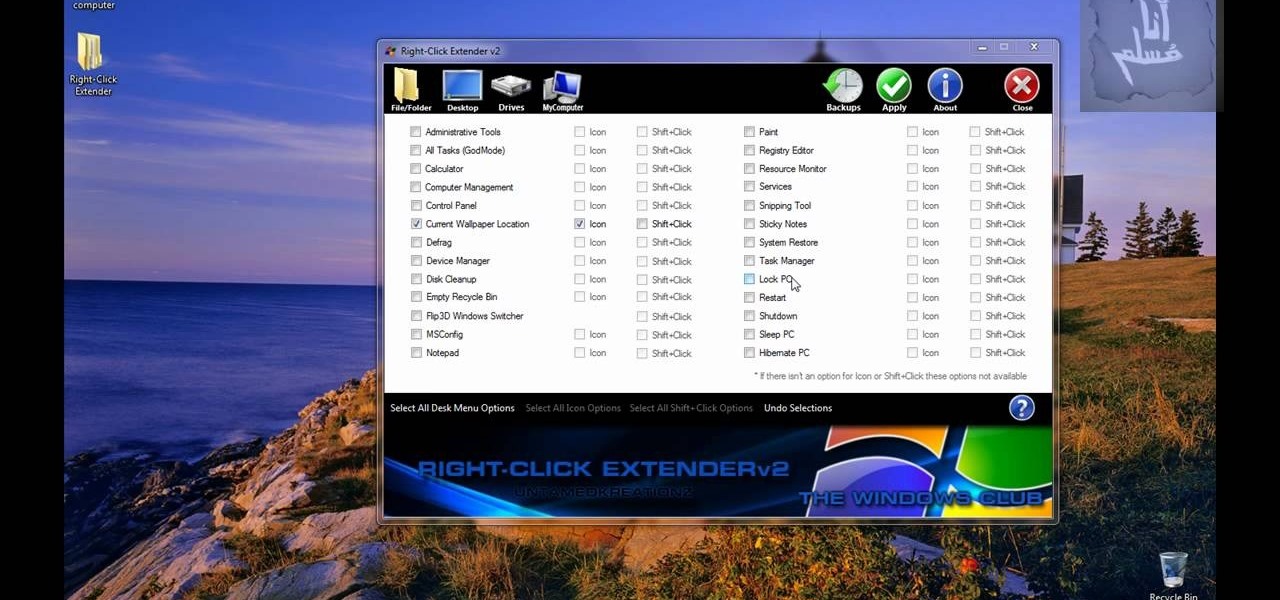
Tired of being limited with your right-click options in Microsoft Windows? There's a program that could help you out, and it's called Right-Click Extender. Insert many different additional items to the right-click context menu.

A burner number isn't just for criminals and cheating spouses. In this digital world, with many of our interactions being conducted online, a throwaway phone number acts as a buffer — it lets you enjoy the web without having to give out your personal information, such as real name or phone number.

Kryptowire, a company specializing in mobile security solutions, released a report on Tuesday, November 15 that exposed firmware in a number of Android devices that was collecting personally identifying information (PII) and uploading it to third-party servers without users' knowledge.