
How To: Beat Act 3 of Call of Duty 4
Learn how to beat Act 3 of Call of Duty 4 for the XBox, 360, Playstation 3 (PS3), and PC on veteran difficulty with this video from NextGenWalkthroughs.com


Learn how to beat Act 3 of Call of Duty 4 for the XBox, 360, Playstation 3 (PS3), and PC on veteran difficulty with this video from NextGenWalkthroughs.com

Gmail uses TLS, or Transport Layer Security, by default for all email communications, so all of your emails will use the standard encryption as long as the recipients also support TLS. But there's a way to add even more security to your Gmail emails, and you can use your iPhone's Mail app to do it.

Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed over the Tor network, Ricochet and XMPP.

People like Ralphige and The Jerky Boys have elevated prank phone calls to an art. Here’s how you can get in on the fun.

There's actually more to the dialer screen on your OnePlus than meets the eye. Besides its obvious purpose of calling people, there's a vast array of secret codes that you can input to troubleshoot your device, in addition to revealing important information, making anonymous phone calls, and so much more.

The dark web is an intimidating place for a newbie hacker, but it's a powerful tool once you've learned to navigate it safely. To help you out with that, this guide will cover some need-to-know information for traversing the dark corners of the internet while keeping your identity and data safe. (Hint: Using Tor is not enough.)
Throwaway phones aren't just for seedy criminals and spies—they can be useful for many everyday situations.

Welcome back, my budding hackers! One of the most basic skills the forensic investigator must master is the acquisition of data in a forensically sound manner. If data is not captured in a forensically sound manner, it may not be admissible in court. In my Kali Forensics series, I showed you how to acquire a forensically sound, bit-by-bit image of a storage device such as a hard drive or flash drive, but now let's dive into live memory.

It always looks different when it's not about you. The Internet is our world's Alterego. Those many bits don't really make sense unless we want them to be valuable, to mean something.

One of Android's biggest strengths, when compared to other mobile operating systems is its open file structure. Google introduced a built-in file manager with Marshmallow that provides basic file management, but like with most apps on Android, there are alternatives. Third-party file managers are readily available, providing deeper access and control of all your files.
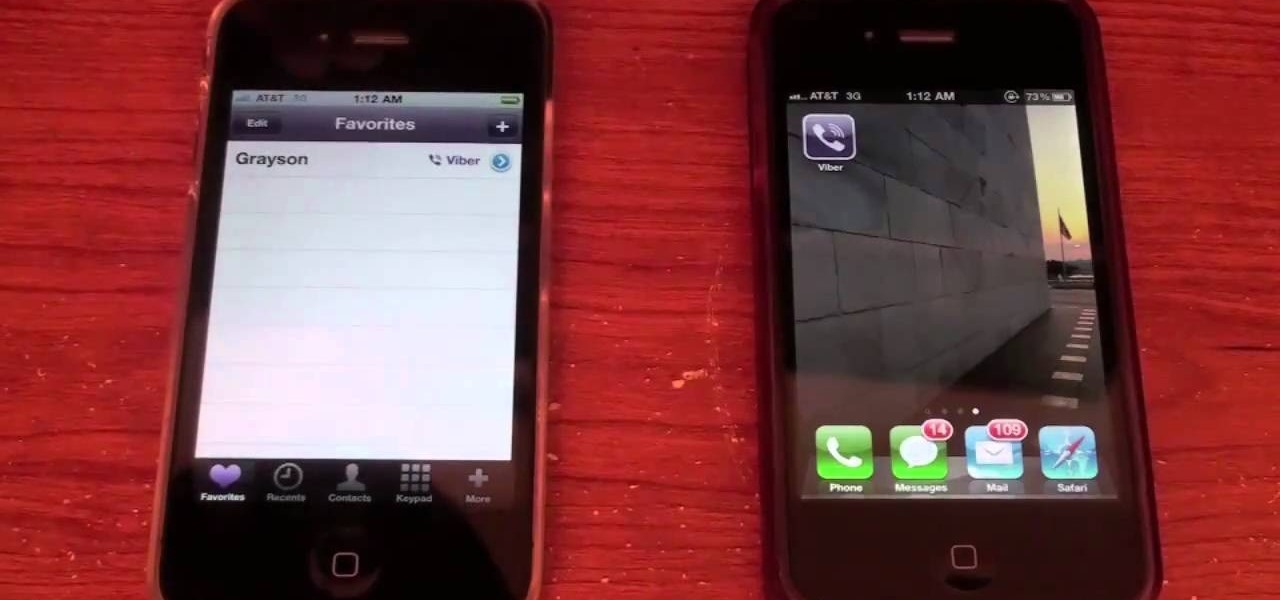
Sure, the iPhone is a phone, but why use your phone service to call people when VOIP is cheaper? This video will teach you how to use a new App called Viber to make free VOIP calls on the iPhone.
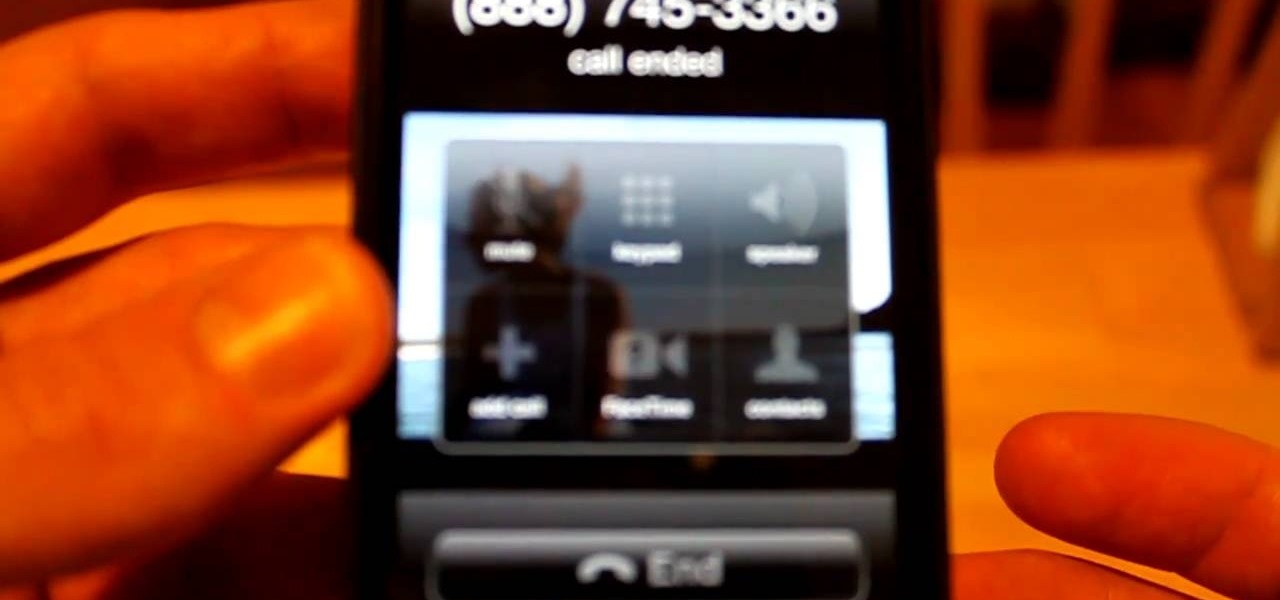
Want to make a phone call on an iPhone 4 running Apple's iOS 4.1, but don't know its passcode? Not a problem. In this clip, we learn a simple trick that will allow you to bypass the lock screen entirely and permit you to view the phone's contact list and place phone calls to any number you like. This glitch has been fixed with iOS 4.2, so treasure this hack while it still lasts! This will let you unlock someones password on an ipod or iphone touch.
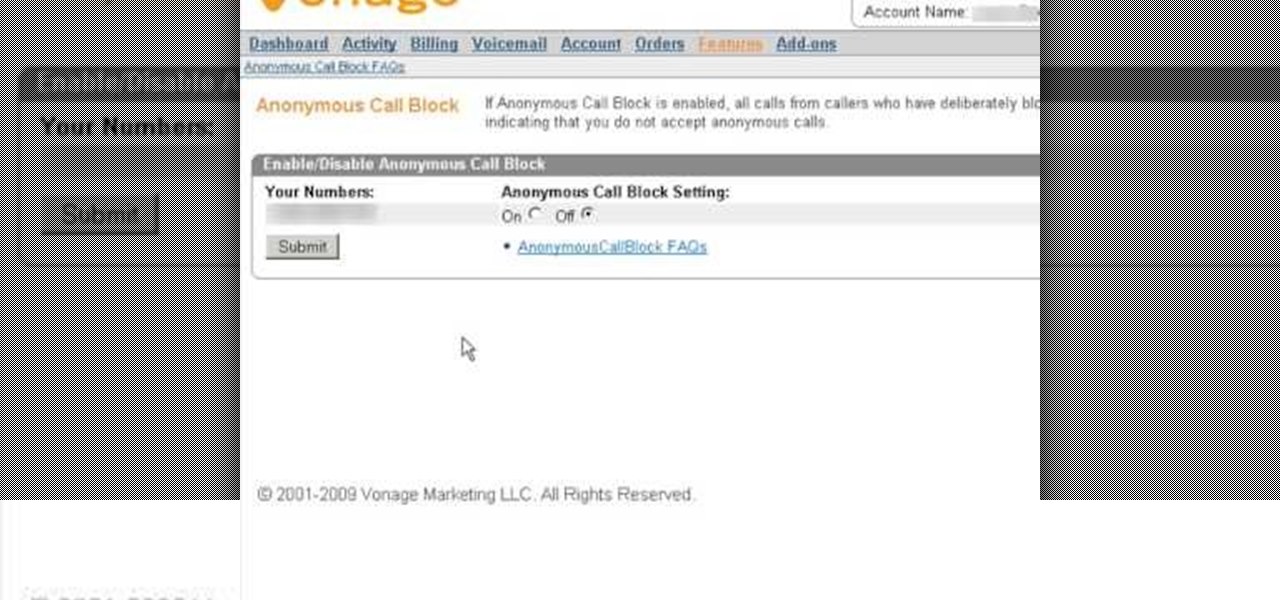
If you are looking for a way to prevent telemarketers and nothing else is working, consider signing up for Vonage's call blocking feature. In this tutorial, brought to you straight from the professionals at Vonage, learn how to set your phone to block any incoming call without a number attached to it.

Right out of the box, iPhone is incredibly easy to use. If you want to get the most out of every feature, you’ve come to the right place. This video tutorial straight from Apple will teach you how to make calls and use voicemail on the Apple iPhone 3G. The iPhone redefines what a mobile phone can do.
Watch this how-to video and learn how to use a soundboard to prank call people with perfect quality. Hope this helps you make hilarious prank calls.
The iPhone supports conference calling capabilities with up to six people. You can even transition from a single-person call to a conference call, or transition from call to call. This tutorial shows you how to make the most of your multi-line call functions in your iPhone.

Learn how to beat all of the achievement challenges on Call of Duty 4 for the XBox, 360, Playstation 3 (PS3), and PC on veteran difficulty with this video from NextGenWalkthroughs.com

This weekend, hackers broke into the servers of the popular shoe shopping site Zappos, giving them access to the personal information of 24 million Zappos customers. The user data taken included names, email addresses, billing and shipping addresses, phone numbers, the last four digits of credit card numbers, and encrypted passwords. However, full credit card data was not lifted, and passwords were cryptographically scrambled.

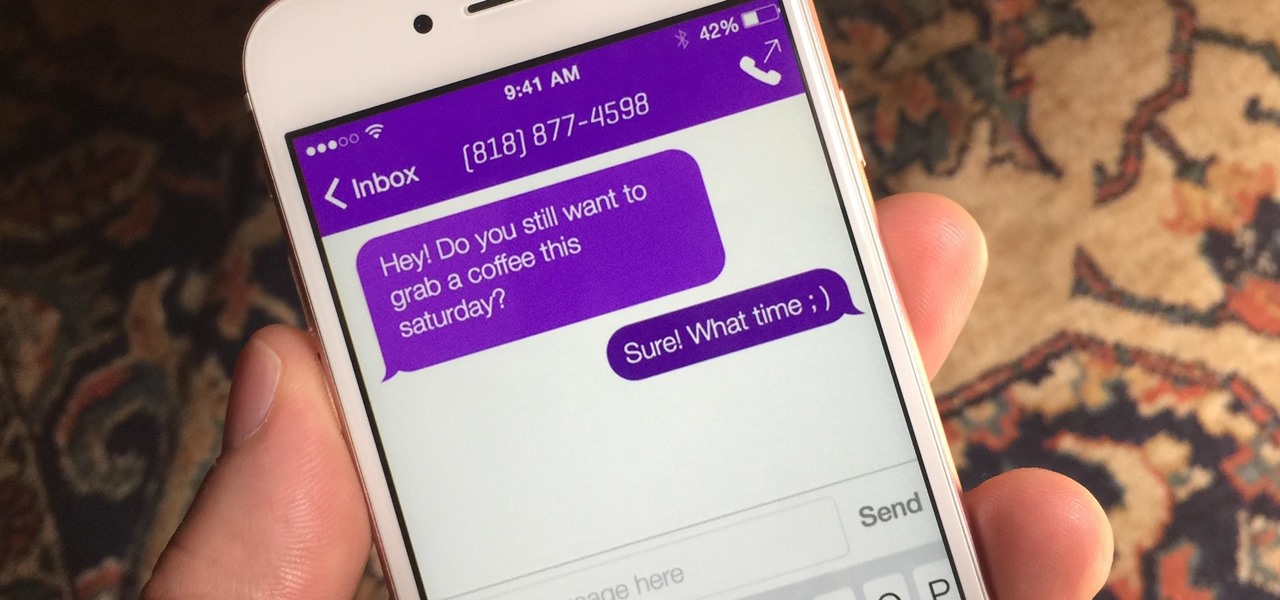
No matter your reasons, you might need a second phone number that's a little more disposable than your primary number — a "burner" number, so to speak. If you create this burner number using Google Voice, you'll get new functionality like call forwarding and voicemail transcripts, and best of all, it's completely free.

Making a NANDroid backup can save you from all sorts of flashing-related mishaps and accidents. Bootloops, SystemUI crashes, accidental wipes, bad ZIPs, or a dozen other possibilities—there's almost no condition in which a NANDroid is unable to correct problems with your device. However, recent changes to Android have created an almost paradoxical situation where restoring a NANDroid can actually lock you out of your phone.

A scary piece of malware just got a lot more terrifying this week. Security firm Comodo reports that "Tordow," a banking Trojan first uncovered in September 2016, received a massive update this December.

When it comes to hacking guides, most are written from the perspective of a Linux user. There are a few outliers, but it's mainly Linux, which leads to the idea that Linux is the only OS that's viable for hacking. This couldn't be further from the truth. A properly set up Apple machine can do quite a bit of heavy lifting.

Considering that nearly half a million brand new apps were published to the Google Play Store in 2015, you can definitely call it a banner year for Android development. In fact, it's getting to the point where we're a bit spoiled as end users, since we've grown to expect something new and exciting practically every week.

Welcome back, my hacker apprentices! A you know, Mr. Robot is my favorite TV show this year, and not just for the realistic hacking. Rami Malek, the actor who plays Elliot, is incomparable in his depiction of a young man with social anxiety who is alienated from a superficial, materialistic society and wants to make a better world. I believe we will see a lot more of this actor in coming years.
This how-to is for everybody who faced the problem of intercepting personal data sending through the Internet and is looking for fast and secure method to protect his activity in the global network.

Since The Guardian published leaked documents exposing the depth of the NSA's spying powers, many people who've never put much effort into protecting their privacy are finally starting to pay attention. Evidence of public opinion concerning PRISM can be seen from the rise in traffic for pro-privacy sites like DuckDuckGo to the petitions demanding that the program be scaled back or done away with altogether. Some would argue that you waive your right to privacy by signing the terms of agreemen...

We share links on an almost daily basis, usually not even thinking twice about it. Whether you're sending a funny cat video to your sister, or letting your coworker know where to go to download relevant files, there are plenty of reasons you might be giving someone a URL.

Android has released a new application called ezNetScan, which is a free app that scans the wireless network you're connected to and gives you a full log of all of the devices connected to that network. This isn't new for smartphone users, let alone Android users. Fing has been around for a while and does practically the same thing that exNetScan does. It gathers information such as the IP and MAC addresses, device vendors, and ISP location. But while Fing is a great program, it does lack a f...
If you've already watched our videos on basics of Unity3D, the awesome free 3D game design engine, and want something more meaty to dig into, watch this video series for a guide to making C4KE, a charming little 4-player action / strategy romp designed by the creator of this video for a game design contest.

Call of Duty: Black Ops has established Treyarch as the kings of Call of Duty once again. If you're having some trouble with learning the game's many awesome maps, watch this video for a full walkthrough of the Hanoi map.
The days of Skype 2.8 for Mac are over! Mac users can now rejoice and make calls with ease using the new beta version: Skype 5.0 for Mac OS X (available here). It was well worth the wait, with a revamped look and feel that simplifies navigation and provides a more Mac-like experience.

Prank calls are almost as old as the phone itself, but have entered a beautiful renaissance in the digital era. No need for the phonebook or a pay phone service anymore! This video will show you how to make really good, funny prank calls in the 21st century, including a rundown of necessary equipment and help with technique.

What to know how to pull off a perfect prank call? Well now you can! With the help of the dudes in this video, become a master of the art!

This video will show you how to unlock the secret arcade game in Call of Duty: Black Ops called Dead Ops Arcade. This secret game mode lets you kill zombies in the old arcade-style action. Plus, unlocking and playing Dead Ops Arcade will earn you 2 achievements:

In this how-to video, you will learn how to do the adult Blatt call. This call is made by an adult deer about 18 months old. There are many types of Blatt calls. The Estrus Blatt is the most effective in getting a Buck to respond. The key is to keep the call short. This call will be made by a Doe when in peak heat and looking for attention from a Buck. Turn the calling device quickly. This will be done several times in a row. Do not make a loud alarm Blatt. Keep it short. This video gives you...

YourTango presents relationship expert Rachel Greenwald, who breaks down why he didn't call you back. She takes us through the process of learning why men do not call women back after first dates. Find out if you are the type of woman who is at risk of not getting a call back, and it begins with "the blahs", a woman who gives the one word answer to standard questions. Next, see if you suffer from iPod repeatability, the Oprah eyes, or how men call it the Park Avenue princess. If you follow th...
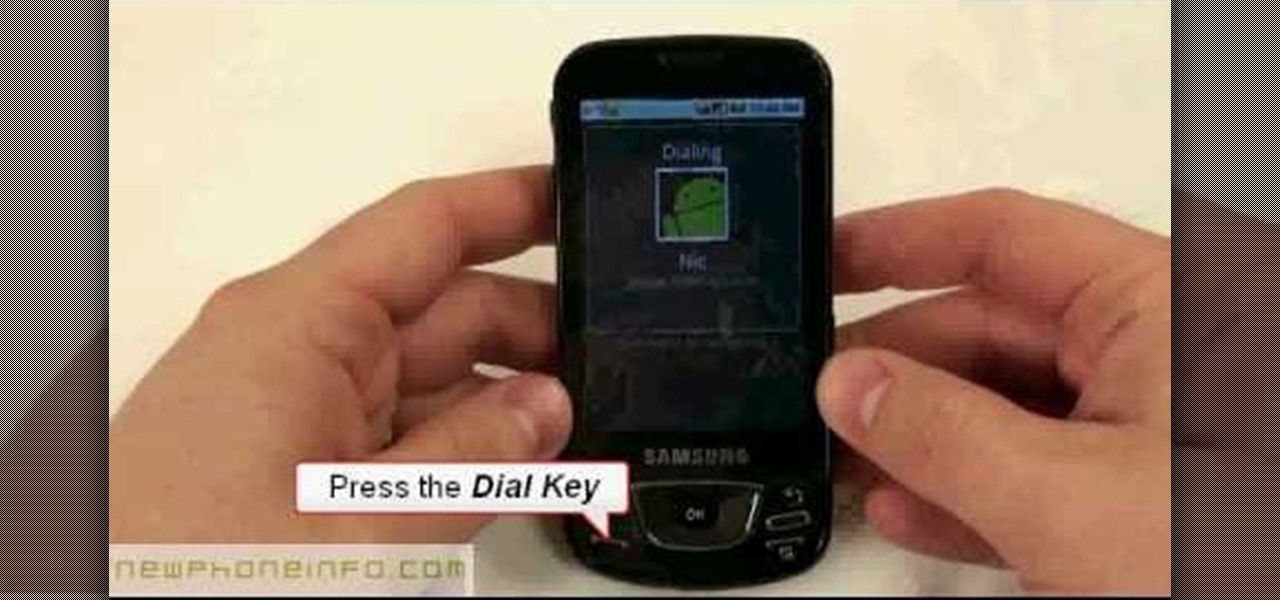
In this video, we earn how to make a call on the Samsung Galaxy I7500. From the home screen, tap on the dialer screen, then tap on the dialer tab. From here, enter in the phone number you want to call. Then, press the dial key after the number has been entered. To end the call, press the menu key and then press the end call button. If you wish to call a contact, tap the dialer key and then tap on contacts on the top menu. Tap on your contact that you want to call, then tap on call mobile to c...
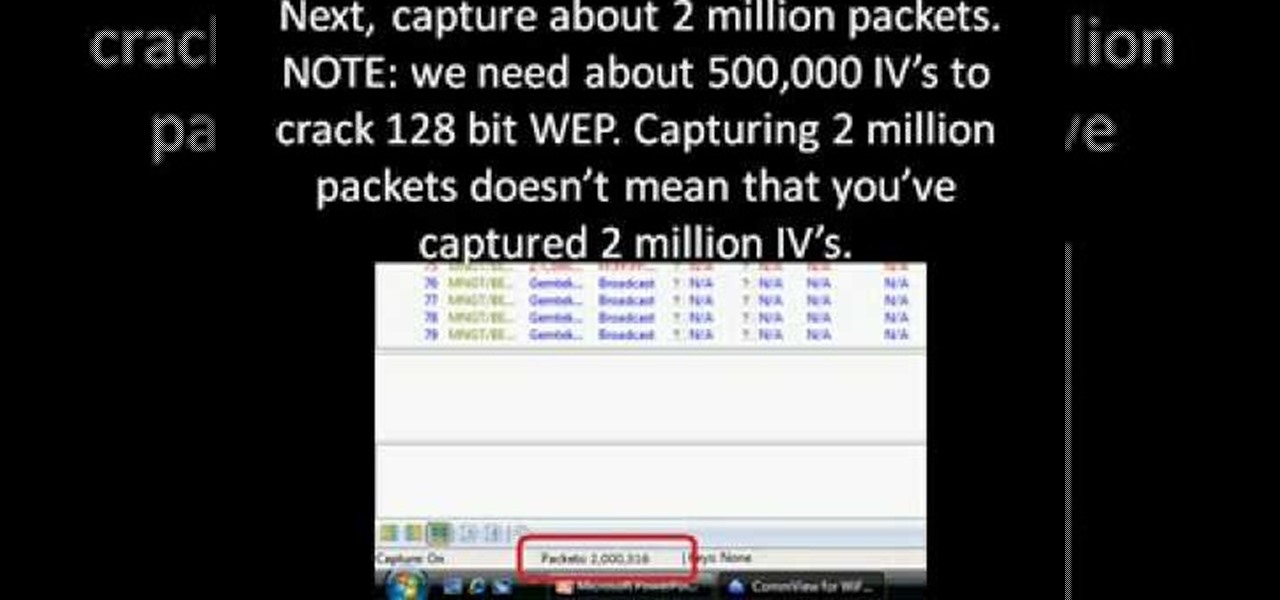
First you need to download Aircrack-ng and Second thing you need to download is CommView for Wi-Fi. Now you have to install CommView for Wi-Fi and then install the right driver.

Learn about military cadence calls in this free military video series, as well as keeping rhythm, marching steps, and cadence songs.

A tutorial series on how to woodturn a duck call. Part 1 of 4 - How to Woodturn a duck call.