Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. To prove it, we'll show how to take a normal command shell and elevate it to a Meterpreter session.
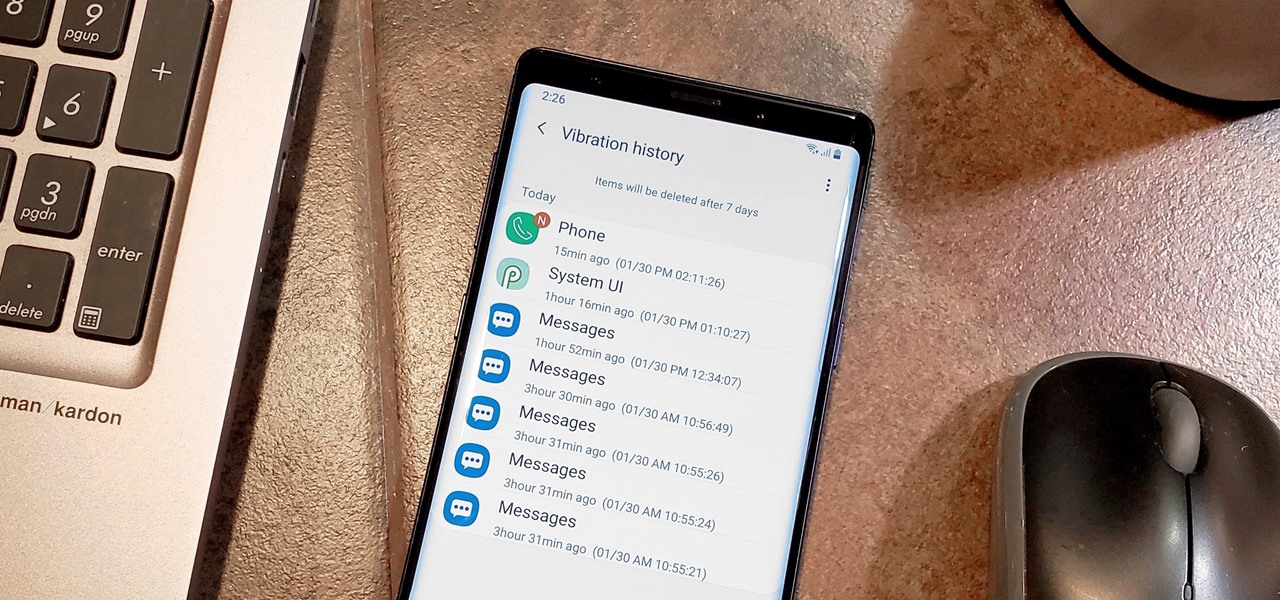
Random vibrations, ghost buzzing — whatever you call it, when your phone goes off for seemingly no reason, it's pretty frustrating. Finding the source of a phantom vibration can be almost impossible if there's no associated notification, especially given the myriad apps and system processes that run on your Galaxy device.

Intel's RealSense family of depth tracking cameras has a new addition with a different set of sensory capabilities.

The tradition of using cutting edge technology to prepare for missions in space, in this case, augmented reality, continues with a new team of international astronauts slated to board the International Space Station (ISS) later this year.

It looks like Facebook really likes Google's augmented reality leadership talent, as the social media giant has hired away another employee from the AR and VR team at Mountain View to lead its team for a product that brings Facebook's AR platform into homes.
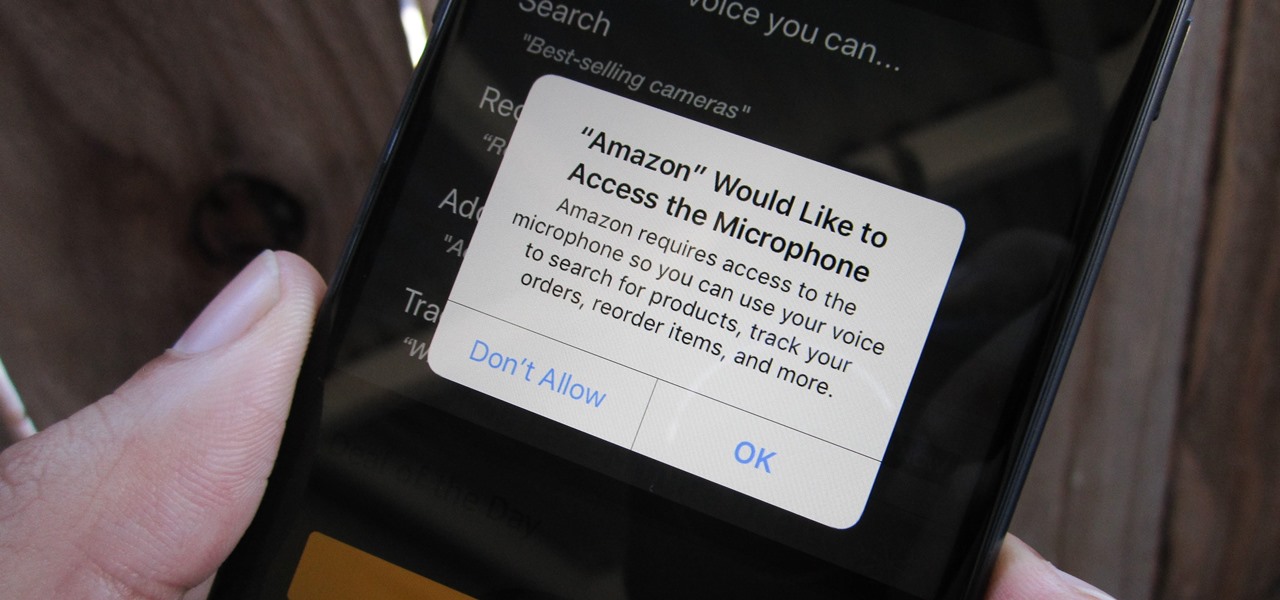
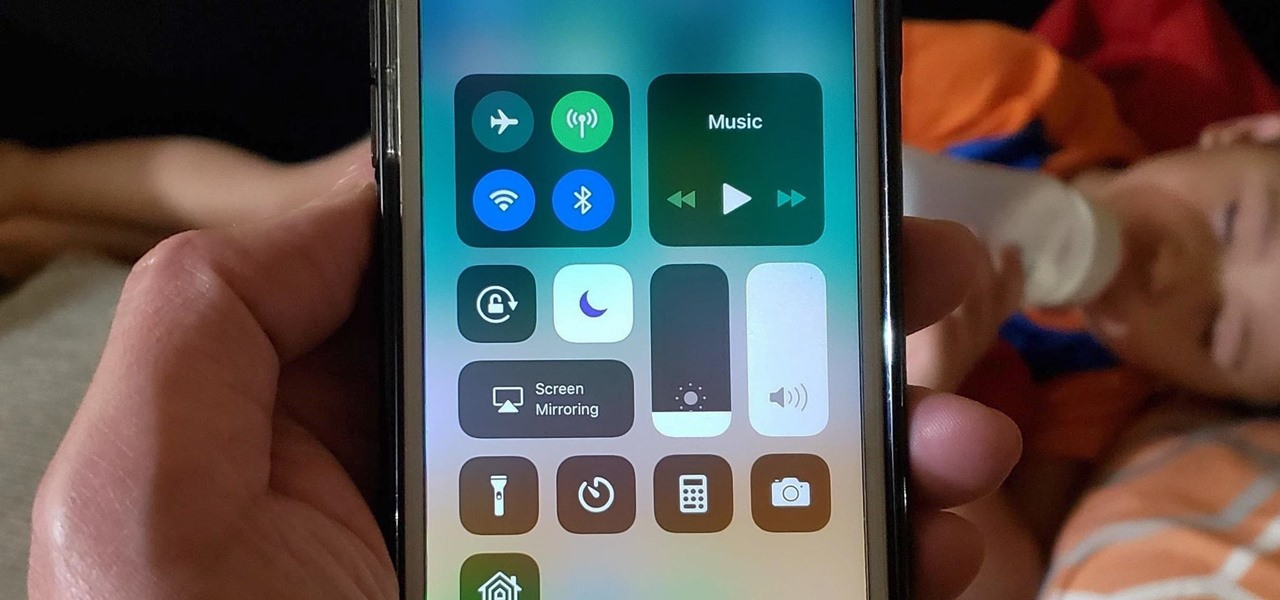
Any app on your iPhone could potentially listen in on your conversations and use that information to target you with tailored ads. Although most companies, including Facebook and Apple, have come out and vehemently denied these claims of spying on consumers, who's to say they're telling the truth? The only way to be sure you're safe is to take matters into your own hands.

Users are often the weakest link when probing for vulnerabilities, and it's no surprise they can be easily fooled. One way to do this is called clickjacking. This type of attack tricks the victim into clicking something they didn't mean to click, something under the attacker's control. Burp Suite contains a useful tool called Clickbandit to generate a clickjacking attack automatically.

Everyone from first responders to hotel cleaning staff use radios operating in the sub-megahertz range to communicate, often without even encoding the transmission. While encoding and encryption are increasingly used in radio communication, an RTL-SDR adapter and smartphone are all it takes to start listening in on radio conversations happening around you.

On Sunday, Apple CEO Tim Cook (the number one person on our NR30 list) made a rare television appearance to talk about and show off his current obsession: augmented reality.

As Samsung's very own take on Android 9.0 Pie, the newly-dubbed One UI (formerly Samsung Experience, and TouchWiz before that) comes with a slew of new features and redesigned elements for the Galaxy's interface. Many of the changes, like the redesigned native app icons, are readily apparent, but other features got subtle enhancements that greatly improve user friendliness.

In the world of technology, there's often a trade-off between convenience and security. The Java Remote Method Invocation is a system where that trade-off is all too real. The ability for a program written in Java to communicate with another program remotely can greatly extend the usability of an app, but it can also open up critical vulnerabilities that allow it to be compromised by an attacker.

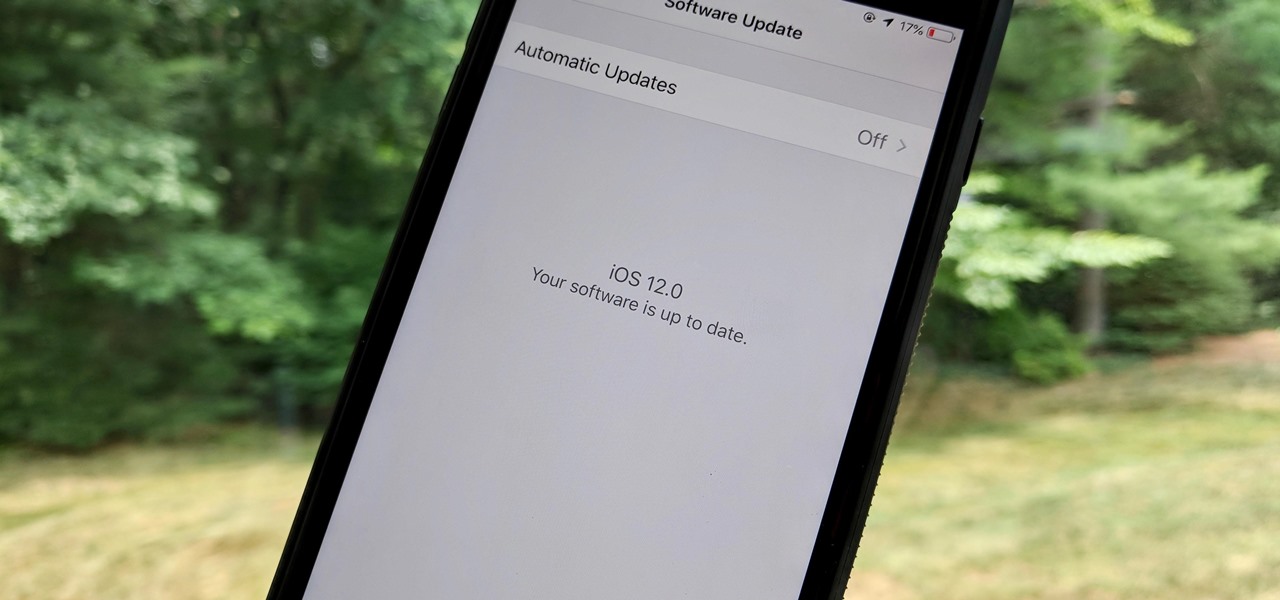
Apple released the first beta for iOS 12.1 on Tuesday, Sept. 18. The update comes just one day after the official release of iOS 12. For developers, it's the first beta release since the "gold master" version on Sept. 12.

Apple officially released iOS 12 to everyone on Sept. 17, and while the new iPhone XR, XS, and XS Max will come with the software by default, you have a choice on whether or not to update your current iPhone model from iOS 11. There are a lot of tempting features to want to update right away, but there are also some compelling reasons to wait it out and install at a later time.

If you didn't get the memo, passwords aren't enough protection for your online accounts. Even a long and complex password offers only one line of defense which can falter. Two-factor authentication adds an additional layer, bolsters your defense, and decreases the risk of your account becoming compromised.

Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such flaw, known as CSRF, allows an attacker to use a legitimate user's session to execute unauthorized requests to the server.

With the arrival of iOS 12, Do Not Disturb has received long-overdue enhancements to make the feature more user-friendly. Among these changes is a subtle but incredibly convenient feature that helps ensure you remain undisturbed for short periods of time to more focus on your task at hand — without having to worry about turning it off manually or messing with complicated settings.

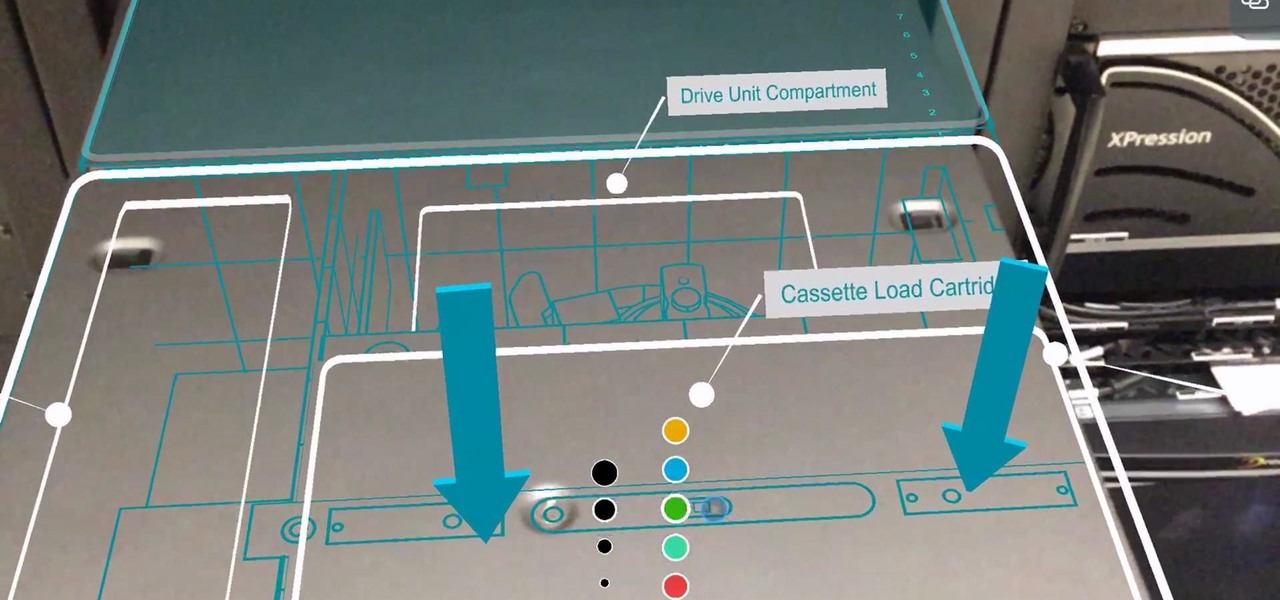
The long and slow road toward the actual release of the Magic Leap One appears to be accelerating, with a couple of new demonstrations of how the system works revealed in this week's creator's portal updates along with the company's developer documentation.

After first being announced at Mobile World Congress 2018, the ASUS ZenFone 5Z will finally be coming to the US. Deemed an iPhone X clone by some, there is more than meets the eye when it comes to this flasghip. While it is similar to the iPhone X, in some ways, it improves on the design.

The HoloLens team is finally beginning to realize that to truly engage the mainstream, augmented reality needs to make its way out of the lab or factory floor and onto the streets.

Transferring hundreds of screenshots, webcam recordings, keystroke logs, and audio recordings between your VPS and a local Kali machine can be tricky. Services like Dropbox don't always have the best privacy policies and suffer data breaches just like any other website. To mitigate these risks, we'll use a secure, open source, and decentralized alternative.

As the official release of iOS 12 nears closer each day, Apple continues to update its betas. The company released the fourth beta of the upcoming software to developers Tuesday, July 17, exactly two weeks after the release of the third developer beta which came out just a few days before the second public beta.

Note-taking apps are a dime a dozen on the Play Store. However, due to their inability to sync across devices, many can't compete with Google Keep. Mozilla decided to throw their hat in the ring with Notes by Firefox, and unlike others, their notes app syncs easily with one of the most popular browsers, plus it's encrypted.

For those of us who love to multitask, picture-in-picture mode is a godsend. The feature, introduced in Android 8.0 Oreo, lets you enjoy videos in a floating window overlaid on top of another app. However, while the OS does have native support, only a select number of apps support the feature.

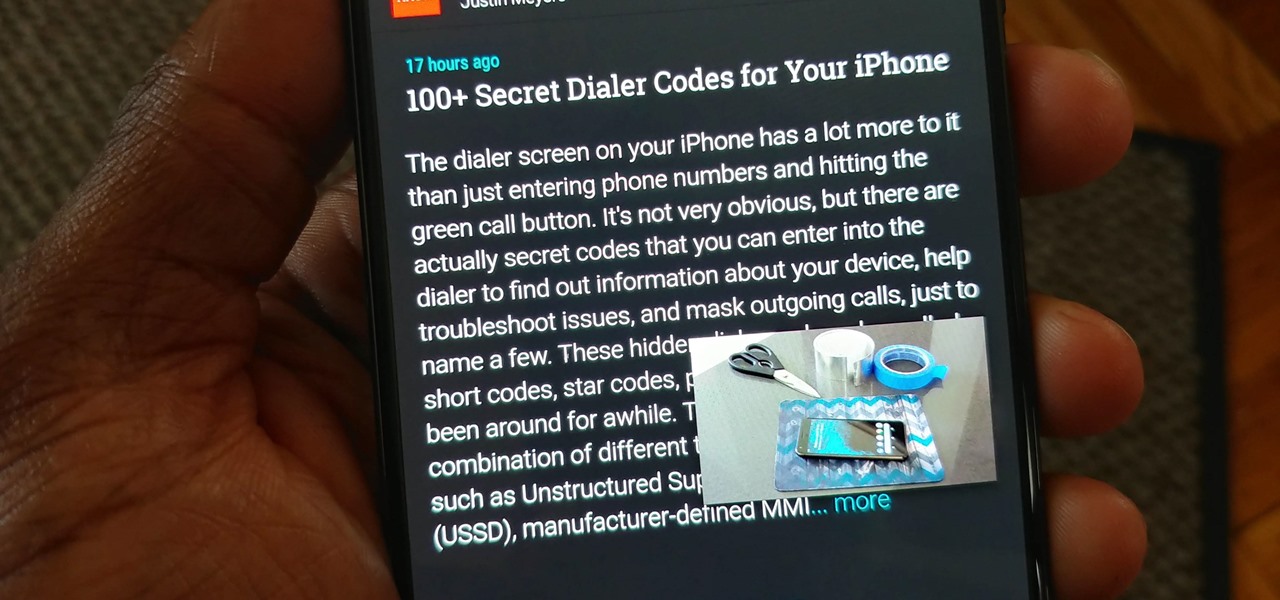
There's a lot more to your iPhone's dialer screen than just entering phone numbers and hitting the green call button. It's not very obvious, but there are secret codes that you can enter on the dialer to find out information about your device, help troubleshoot issues, and mask outgoing calls, to name just a few things.

With developers chomping at the bit to play with ARKit 2.0, Unity has updated its ARKit plugin to enable access to the new augmented reality superpowers of the toolkit.

Passwords and data stored in web browsers are extremely valuable to hackers. If not for financial gain, black hat hackers may still leak your passwords and personal information for amusement. Never undervalue what you're worth to a hacker.

We need to take our privacy and security much more seriously. Whether it's malware-infected apps or the mishandling of our data by companies like Facebook, there are threats all around us in this digital world. Fortunately, some smartphones are simply designed to protect us better.

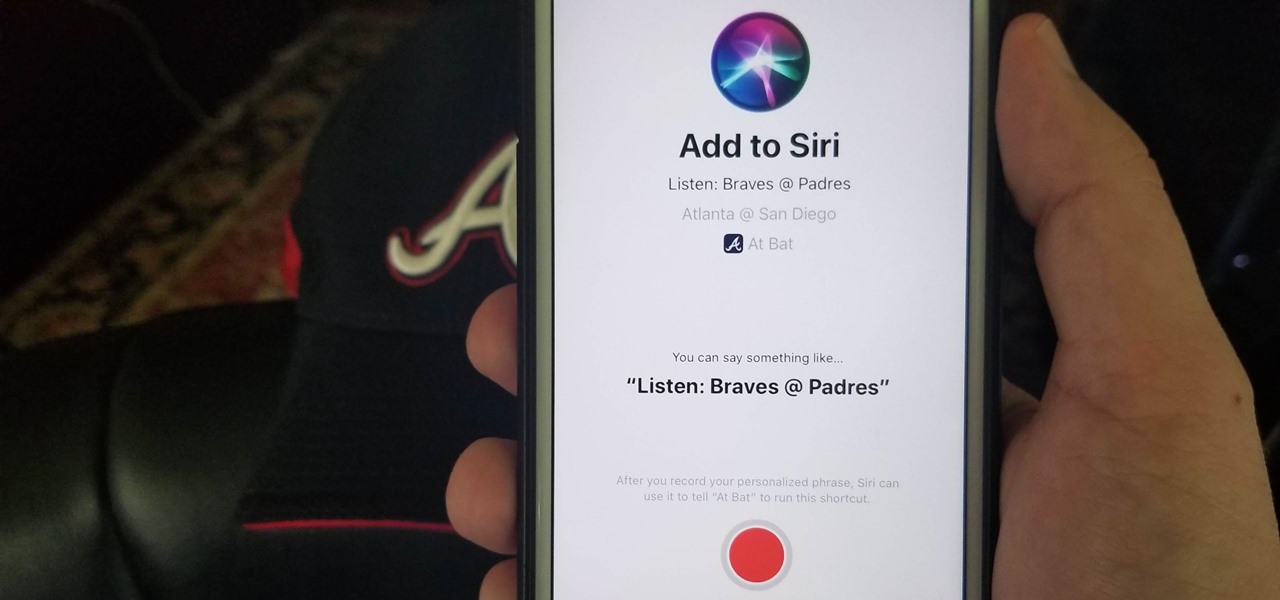
Apple is putting their Workflow acquisition to use with the new Shortcuts feature, integrated right into Siri. It allows you to connect commonly-used actions to a phrase that you activate with Siri. In addition to some of the other speed improvements in iOS 12, Shortcuts helps streamline your mobile experience.

This year's big iPhone update, iOS 12, aims to solve many of the issues that arose during iOS 11's controversial, buggy tenure. With that in mind, it may be tempting to jump on board the new software immediately and leave iOS 11 in the dust for good. Here are some reasons why you might want to reconsider joining the iOS 12 beta.

Enterprise augmented reality software maker Scope AR is bringing the powers of its two productivity apps together like the Wonder Twins into the form of a single app.

Augmented reality avatars that mimic facial expressions are no longer the exclusive province of Animojis on the iPhone X or AR Emojis from Samsung. Camera app Snow has added its own alternative to Apple and Samsung's features, which it also calls AR Emoji, for iOS and Android.

Thanks in large part to our phones, many of us don't get the recommended eight hours of sleep. In Android Pie, Google introduced a feature called "Wind Down" that aims to help combat this. However, thanks to a creative app developer, we don't need to wait for Android 9.0 to enjoy this feature.

Android lets you sync your contacts across devices. The OS will use not only contacts saved on your phone, but also your Gmail. This choice can lead to a contacts list populated with entries that don't have a phone number, which can quickly add up. To mitigate this problem, there are a few methods.

Spotify is a great music subscription service, but constantly streaming songs can really run up your monthly mobile data. Fortunately, you're able to download music from Spotify on Android and iOS in order to preserve your precious data cap.

While our time with the Protostar VM from Exploit Exercises was lovely, we must move on to bigger things and harder challenges. Exploit Exercises' Fusion VM offers some more challenging binary exploitation levels for us to tackle. The biggest change is that these levels are all network services, which means we'll write our first remote exploits.

Deleted bank statements and private photos are still within an attacker's grasp, so don't think that emptying your recycling bin is enough to keep your files from coming back to life. It's possible for a hacker to recover compromising files and images from a backdoored computer completely without the victim's knowledge.

Magic Leap's recent flurry of patent applications prompted us to look around for any trademark movements from the company, and it turns out that the Florida-based company has been quite busy.

The Galaxy S9 is an audio powerhouse. It has the first set of stereo speakers on a Samsung flagship, and it even comes standard with a set of AKG-tuned earbuds that would normally cost $99. But if you want to further enhance your audio experience, there's a feature that will customize audio output to your own specific hearing.

Next to things like natural disasters and disease, the specter of war is one of the only things that threatens to derail the 21st century's long stretch of technological innovation. Now a new app is using augmented reality to remind us of that by focusing on those most impacted by war — children.

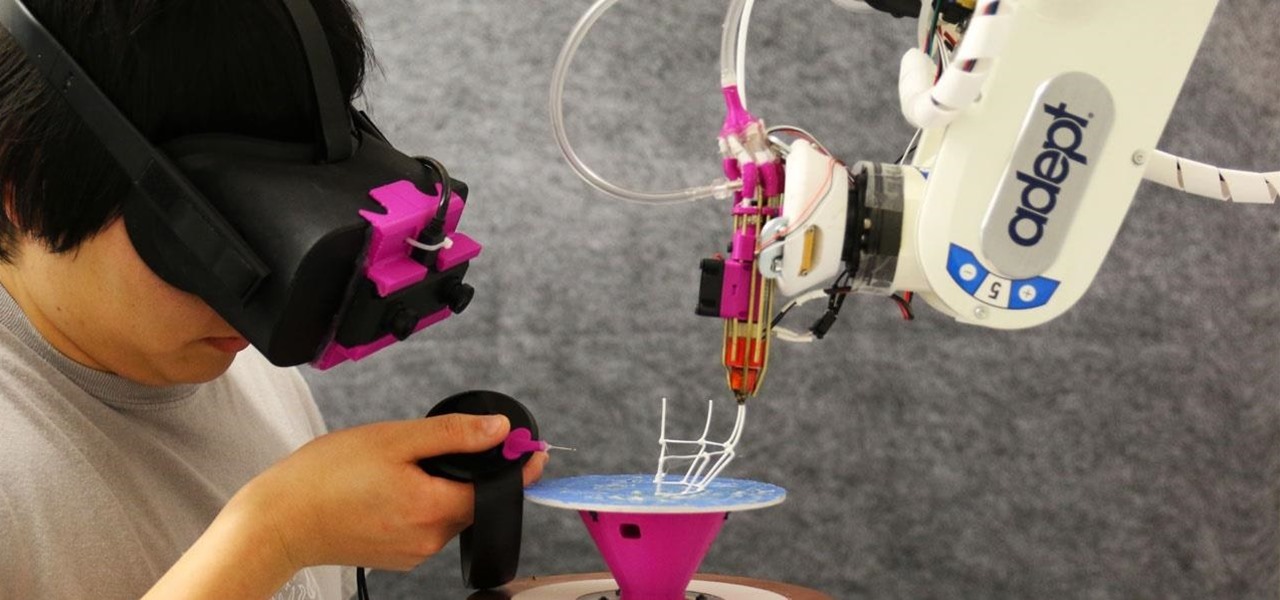
We've seen a number of unique mashups of augmented reality with other bleeding edge technologies, but somehow it took until 2018 for someone to come up with a now obvious complement to AR: 3D printing.