Driverless partnerships continue to appear as Continental AG, leading German automotive manufacturing company, has signed a strategic cooperation agreement with global electric startup, NIO. The goal of this partnership is to research, share, and develop autonomous technology, among other developments.

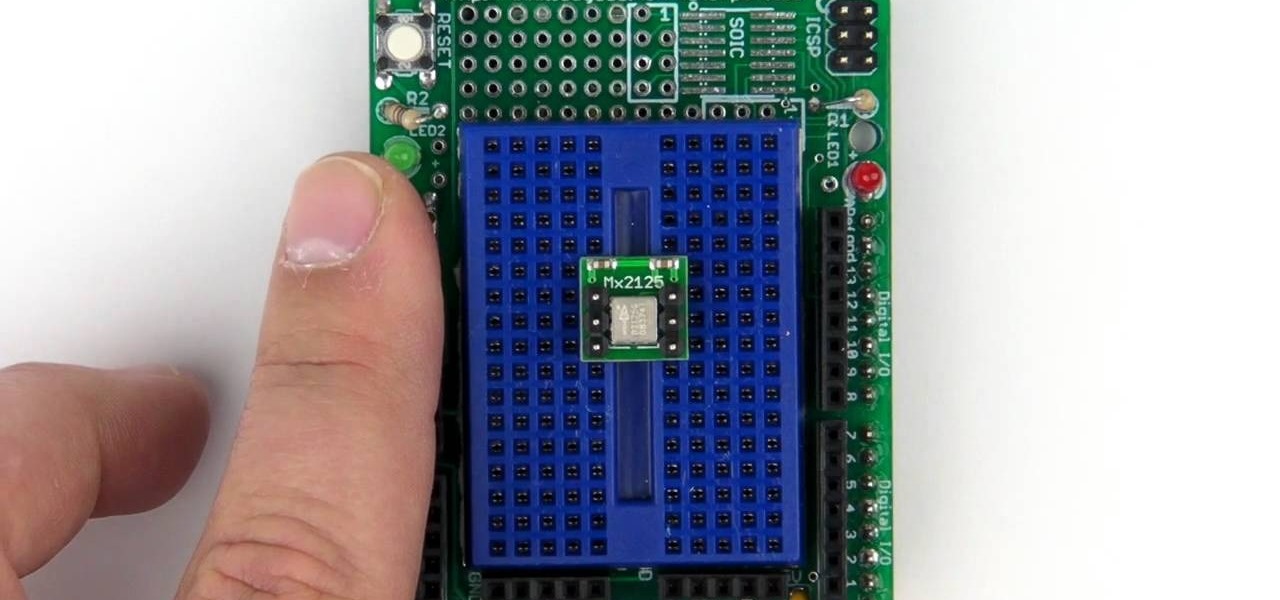
Dave and Pat break down the basics of RFID technology and show you how to put it to use by building an RFID beer safe!

For anyone wanting to keep information private, plain text is a format of the past. Instead, cheap, powerful encryption is widely available, but often not easy enough to use to attract widespread adoption. An exception to this rule is EncryptPad, an easy to use application that lets you encrypt text, photos, or archives with strong encryption using a password, keyfile, or both.
This week in Market Reality, we see two companies capitalizing on technologies that contribute to augmented reality platforms. In addition, industry mainstays Vuzix and DAQRI have business news of their own to report.

Beware: After a new caucus — the Congressional Caucus on Virtual, Augmented, and Mixed Reality Technologies for the 115th Congress — formed in the US House of Representatives, the government has decided to go after all mixed reality head-mounted displays. The HoloLens, Magic Leap — nothing is safe anymore.

Uber has been in the hot seat for awhile now, for many reasons, especially for being sued by Waymo over stolen LiDAR designs. But now, perhaps the attention will be taken off both Uber and Waymo as a new contender enters the LiDAR arena; A small, independent company called Luminar has finally let the world in on what it has been cooking up.

The first augmented reality hardware and software functional requirements guidelines have been released today by UI LABS and the Augmented Reality for Enterprise Alliance (AREA).

Apple is in the process of developing its own graphics processors for future iPhones, according to recent reports.

Now that smartphones have ensured that we're connected to the internet 24/7, online privacy has become more important than ever. With data-mining apps hoping to sell your information for targeted ads, and government agencies only one subpoena away from knowing every detail of your private life, encryption has become our last line of defense.

One of the more talked-about features of Google's new flagship device is the fact that all of the data on the Nexus 6 is encrypted by default. At face value, this certainly seems like an added bonus for the 6-inch phablet, especially in this day and age with growing security concerns abound. It's definitely something that the FBI is none too pleased about.

Welcome back, my hacker trainees! A score of my readers have been begging for tutorials on how to hack Wi-Fi, so with this article, I'm initiating a new series dedicated to Wi-Fi hacks. This will probably be around 6-9 articles, starting with the basics of the technologies. I can hear you all groan, but you need to know the basics before you get into more advanced hacking. Then hopefully, developing your own hacks.

You want the best quality photos you can get, and the Canon EOS 7D digital SLR camera makes perfecting your pictures easy. There is a range of technologies to enhance image quality. This video shows you the many options you can use.

MAKE and Kipkay brings the do-it-yourself mindset to all the technology in your life. Make Magazine celebrates your right to tweak, hack, and bend any technology to your own will.

MAKE and Kipkay brings the do-it-yourself mindset to all the technology in your life. Make Magazine celebrates your right to tweak, hack, and bend any technology to your own will.

MAKE and Kipkay brings the do-it-yourself mindset to all the technology in your life. Make Magazine celebrates your right to tweak, hack, and bend any technology to your own will.

MAKE and Kipkay brings the do-it-yourself mindset to all the technology in your life. Make Magazine celebrates your right to tweak, hack, and bend any technology to your own will.

MAKE and Kipkay brings the do-it-yourself mindset to all the technology in your life. Make Magazine celebrates your right to tweak, hack, and bend any technology to your own will.

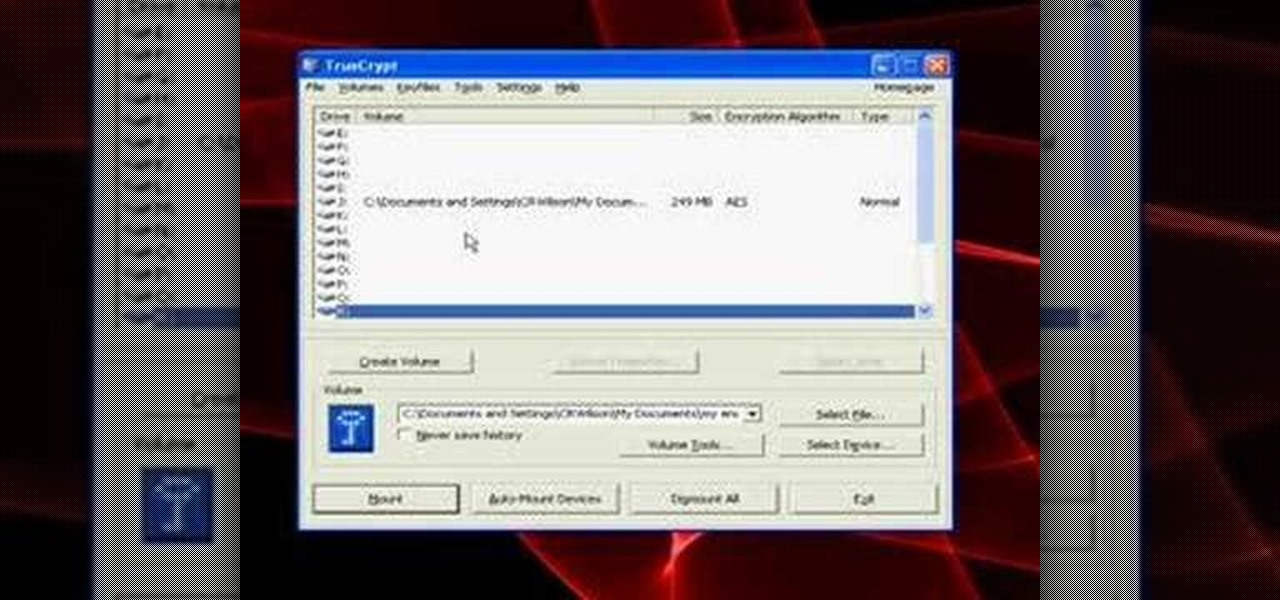
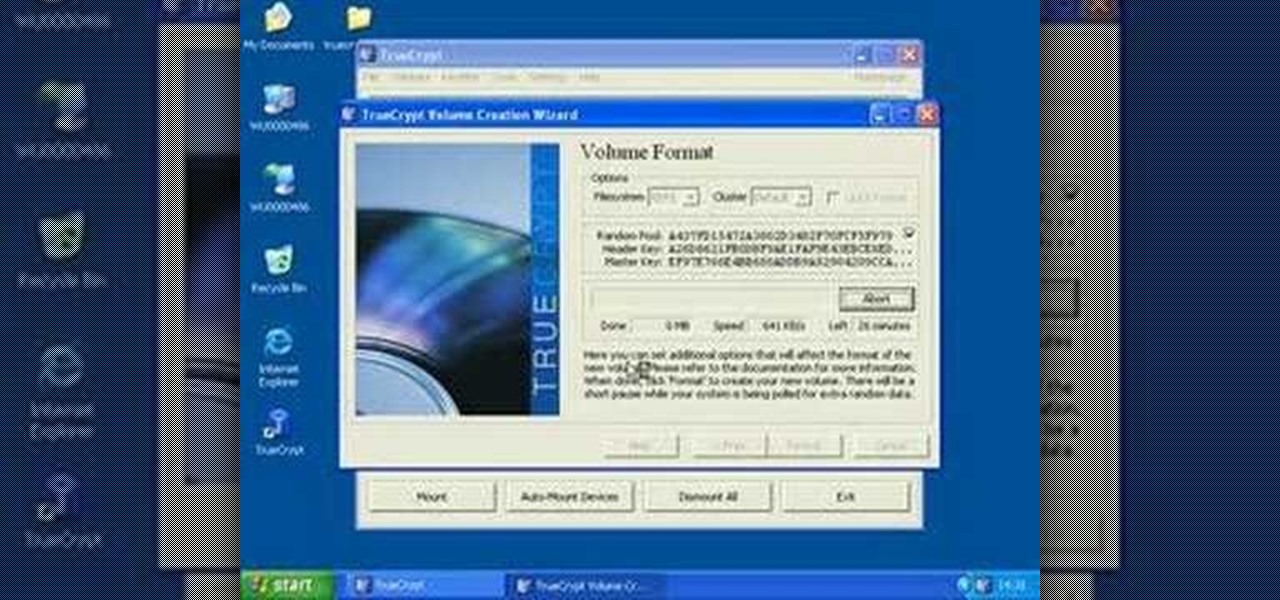
A tutorial on how to open, mount volumes, create volumes, and dismount volumes with Truecrypt, the free, open-source encryption software. GRAB LOW RES VERSION AS A DUP LINK!!

The augmented reality industry has an insatiable lust for 3D content, which makes an investment of $48 million into Matterport a no-brainer for investors.

When we reviewed the best file managers on Android, MiXplorer easily topped our list with its abundance of features, including tabbed browsing, support for up to 19 different cloud services, file and folder encryption, and much more. The only major complaint we had was the fact it couldn't be installed from the Play Store, but now, that is no longer the case.

The interactive displays of the future as visualized in Steven Spielberg's science fiction classic Minority Report, as well as the augmented reality interfaces used by millionaire playboy Tony Stark in the Marvel Cinematic Universe, are now closer to becoming reality in the military realm.

Facebook may have shamelessly copied Snapchat and its camera effects for faces (as well as its World Lenses), but it might beat its social media competitor to virtual body augmentation.

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

Due to the overnight success of smartphones, millions of people are connecting with others. Currently, over 15 million text messages are sent every minute worldwide. Most of this communication is happening in the open where any hacker can intercept and share in the discussion unbeknownst to the participants. However, we don't need to communicate insecurely.

Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed over the Tor network, Ricochet and XMPP.

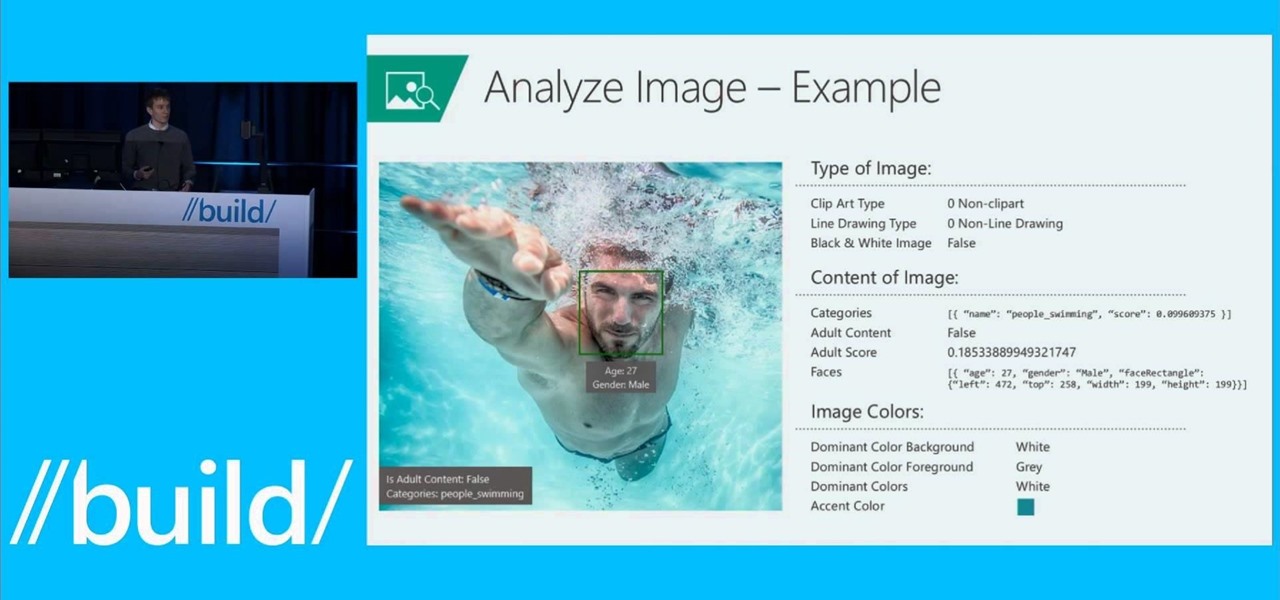
Microsoft is developing a new API project called poject "Oxford," and it includes face, speech, and more "smart" API technology. Despite being Microsoft, I actually found this to be very useful. ;)

In this clip, you'll learn how to implement video encryption and decryption in a VB app. Whether you're new to Microsoft's popular event-driven program language & IDE or a seasoned developer merely looking to improve your chops, you're sure to find benefit in this free Visual Basic programming lesson. For more information, including a complete demonstration and detailed, step-by-step instructions, take a look.

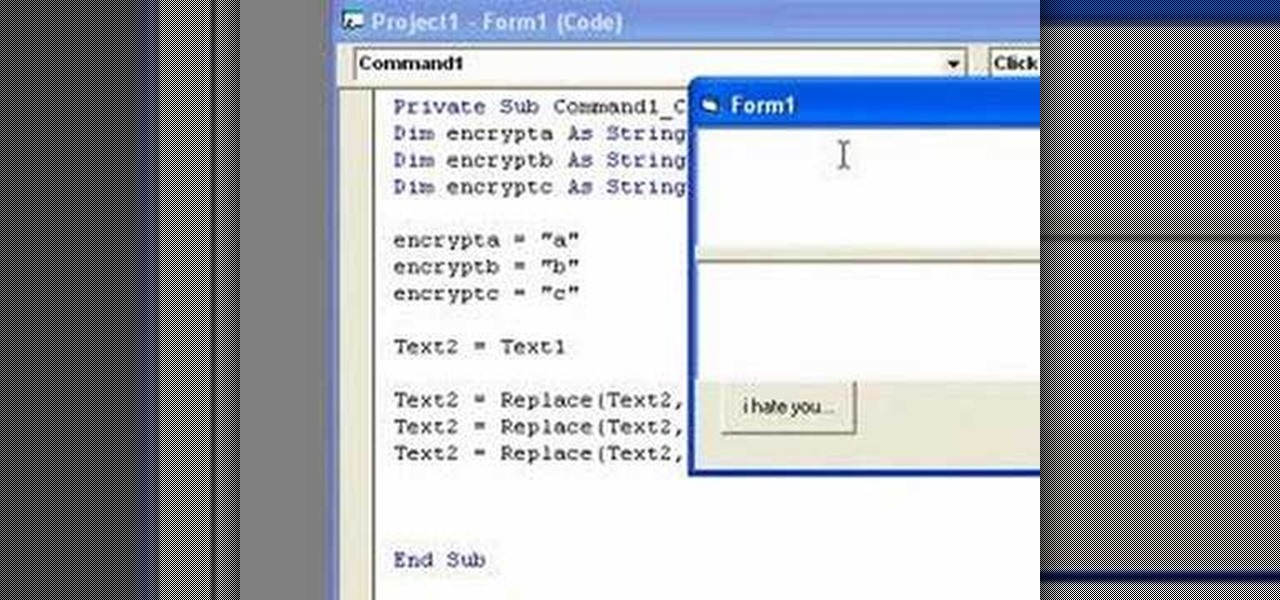
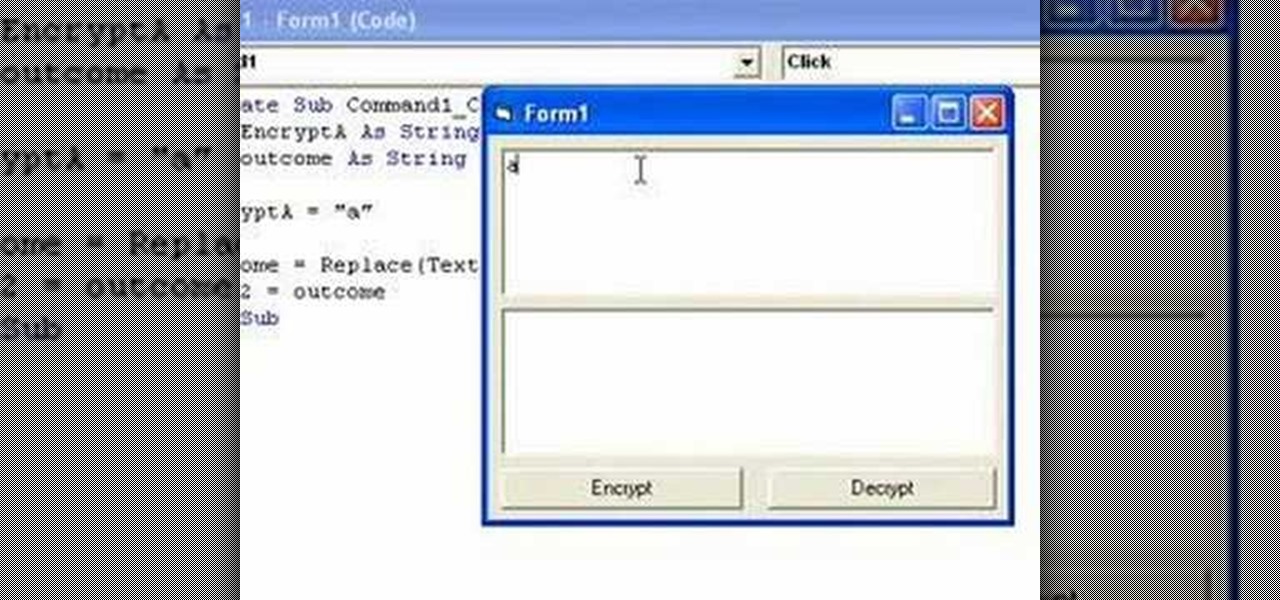
In this clip, you'll learn how to implement simple text encryption and decryption in MS VB 6. Whether you're new to Microsoft's popular event-driven program language & IDE or a seasoned developer merely looking to improve your chops, you're sure to find benefit in this free Visual Basic programming lesson. For more information, including a complete demonstration and detailed, step-by-step instructions, take a look.

These days, faucets are incredibly easy to install (removing old faucets is the hard part). And if you have a Delta brand single handle kitchen faucet with DIAMOND seal technology, this video will show you the steps to installing it. This is also very similar to other brands of single-handle faucets. This video from Lowe's and Delta will help you with your installation. You'll need a screwdriver, adjustable wrench and allen wrench.

MAKE brings the do-it-yourself mindset to all the technology in your life. Make Magazine celebrates your right to tweak, hack, and bend any technology to your own will. In this tutorial, Robert Bruce Thompson shows you how to make crystal iodine. As Thompson says in the video, crystal iodine is currently a schedule one compound, and in order to buy you have to fill out a lot of paperwork and you'll end up on a DEA list. This tutorial gets you around that, but proceed carefully.

MAKE and Collin Cunningham brings the do-it-yourself mindset to all the technology in your life. Make Magazine celebrates your right to tweak, hack, and bend any technology to your own will.

MAKE brings the do-it-yourself mindset to all the technology in your life. Make Magazine celebrates your right to tweak, hack, and bend any technology to your own will.

Keep private info from prying eyes and earn some peace of mind when you safeguard your PC or Mac against nosy intruders. You will need several great passwords, virtual desktop software, snoopware blockers, a screen filter, a mirror, a healthy sense of paranoia, WPA encryption, and an understanding IT specialist.

This video tutorial will explain you how to secure a USB thumbdrive (or flashdrive) using the free, open-source encryption software TrueCrypt.

Watch as Kipkay hacks a bulky VHS camcorder and turns it into a night vision headset. This video tutorial will show you that old technology can still be useful in today's world. Just think, you might not have ever been able to see in the dark corners of the night without this hacked VHS camcorder. Night vision isn't just for the military, it's for you, and me, and your dog...

The Newstweek might be the coolest new device of 2011 that no one is talking about. It's a pocket-sized device that allows you to access the data streaming through a wireless internet access point and change the news being read by fellow users at the hotspot, from any site, however you want. It allows you to do some amazingly inspiring and sinister things, like any really progressive technology, and this video will show you how to use it.

Nitrile exam gloves are the latest in disposable medical glove technology. They withstand stress well and won't trigger latex allergies, making them a great choice for first aid work. Watch this video to learn how to remove them properly, ensuring that your skin is not contaminated by whatever you were trying to keep off them with the gloves.

A cool technique on the guitar is Galloping Harmonics, combining the galloping rhythmic figure with harmonics and making it a little funky with some slap guitar, originally made famous by Regi Wooten! In this video, Jude Gold, head of GIT (Guitar Institute of Technology) at Musician's Institute completely breaks down the entire process of learning how to get the sound, the feel, and the technique down.

Have you ever wondered how all of the blood and dust that flies from wounds and bullet holes in Hollywood films gets shot through the air so convincingly? The answer is a pneumatic dust system. This video will show you how to make one yourself for almost no money, allowing you to achieve all sorts of cool special effects without any expensive digital technology.

Google is one of the most powerful forces on the Internet, and their technology can be the key to helping you find success in whatever your online endeavor might be, from web design to filmmaking. This video is a part of their Google Webmaster Series, offering help to webmasters the world over on how to best utilize Google in their work. This video will show you how to ensure that your Wordpress blog is safe from the hacker attacks that are so common for Wordpress users.