My friends can be pretty shitty sometimes, but they're my friends nonetheless. On various occasions, they've secretly taken my device and made me look foolish by posting crude and embarrassing posts to Facebook, Instagram, or Twitter. With friends like these, who needs enemies, right? And it's because of these types of friends that we need to substantially upgrade the app security on our devices.

If you're spending hours on your phone playing games like Angry Birds and Candy Crush Saga, or posting online to Google+ and Pinterest, you're probably being spied on. The latest releases from NSA whistle blower Edward Snowden reveal that the National Security Agency, and its UK counterpart, GCHQ, are mining the ad networks utilized in these apps to collect a trove of information on you.

Texting something as simple as "What up, bruh?" can be transformed into something way more baller by adding emojis, emoticons, GIFs, and textspeak. Some people would even argue that texting is a form of art, similar to Shakespearean sonnets, but it still has a ways to go if you ask me.
As of this week, Gmail is going to start letting Google+ users email each other using a new option called "Email via Google+." There's nothing wrong with making it easier to get in touch with people you want to hear from, but the default setting allows anyone with a Google+ account to send a message to your Gmail inbox. After the feature is in use, Gmail will start to suggest Google+ connections along with your other contacts as recipients. Email addresses will not be displayed for Google+ co...

For a photo- and video-sharing app based around privacy, Snapchat sure has a lot of security holes floating around. At one time, you were able to take screenshots of Snapchats in iOS 7 without the sender knowing, which is something that you can still do on rooted Android devices.

For those of you who have (or had) and iPhone, one of the cooler photo apps for iOS was VSCO Cam, an extremely popular camera with pro-quality filters and effects. Now this app is available for Android on Google Play for your Nexus 7 tablet and any other devices running Android 4.0 and up.

Snapchat was created for the sole purpose of removing evidence from your mobile that a photo or video ever existed. That way, snoopers can't find any of these questionable selfies in your photo gallery. Of course, there are plenty of ways around this safeguard, but it's still more private than the standard social networking app.

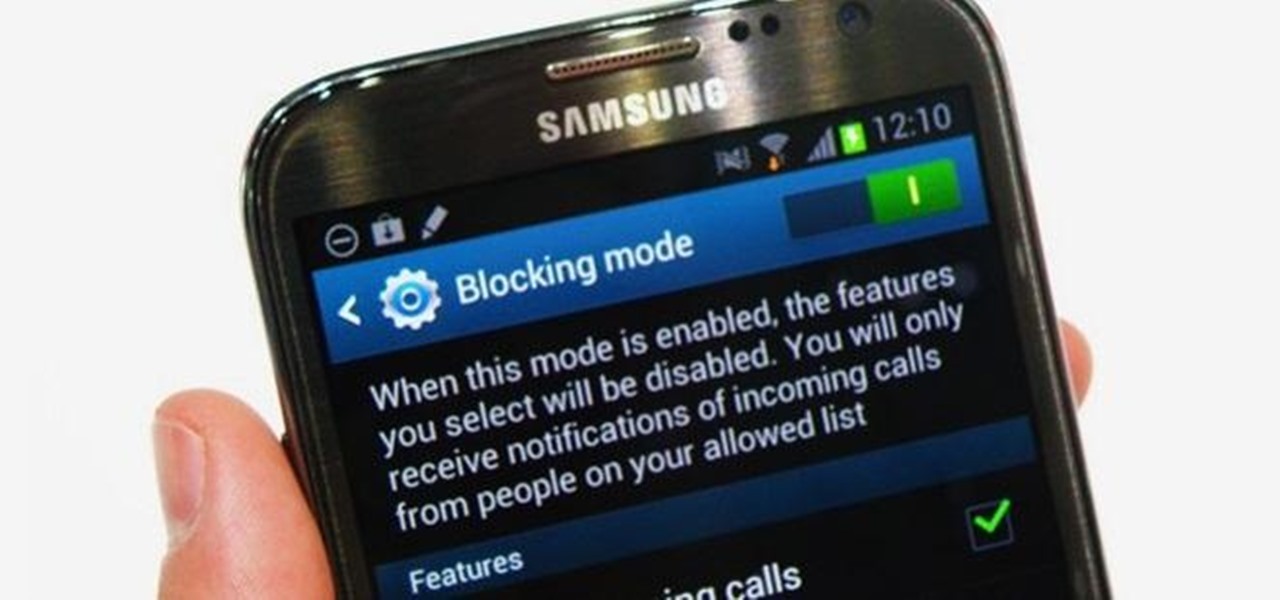
There are a gazillion lock screen apps available on Google Play, but the majority of them are subpar and not worth your time. However, in my opinion, there is definitely one out there worth your time—one that constantly learns and adapts to what apps you use when and where to determine which shortcuts to give you.

If you're a Twitter user, it's a safe bet to assume that you've used a hashtag. On all social networking sites that have the capability, such as Instagram, Facebook, and Google+, the pound (#) symbol is used to mark and designate specific keywords or topics in order to make it effortless for users to connect with one another.

I'm still amazed by all the things some people just don't know. Script-kiddies often refer to Metasploit if someone asks them how to hack a computer because they think there's simply no other way. Well here I am today trying to increase your set of tools and -of course- skills.

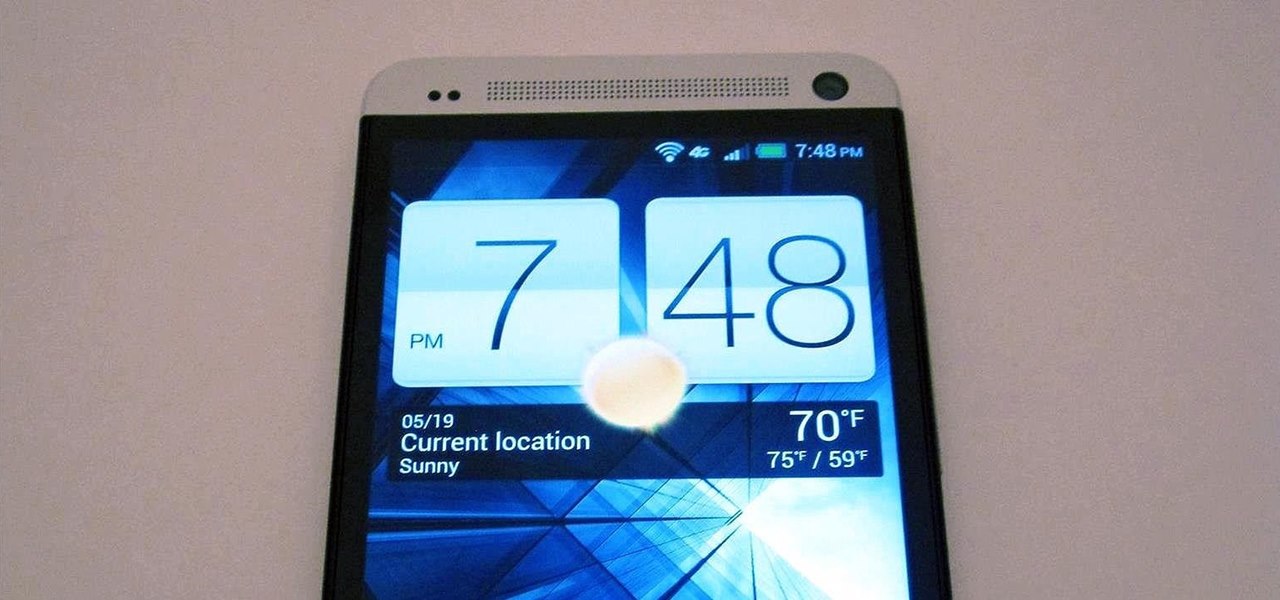
When the HTC One was announced, the fact that its IR transmitter was a side note more than a main feature made me dismiss it. When Samsung included one in the GS4, it became even less impressive. However, now that I actually have a One, I find that the "TV" app is way more than just one of Samsung's "S"-gimmicks. Step 1: Set Up Your Service Provider

The newer HTC One is arguably the best smartphone yet in terms of hardware, but its software moves considerably farther away from the stock Android experience. Even more so from HTC's own Sense.

As we all know, our attention spans are much shorter now that we're accustomed to getting information and news in tiny snippets via text messages, tweets, instagrams, and other constant updates.
Your company is deciding on starting new projects but there is a lot you need to do to make sure these projects are right for your company and will be financially rewarding to the bottom line. Before you begin you and your project management team will need to go through a Project Evaluation Process.

Self-restraint is one of the hardest thing to do. I'm a world-class procrastinator, and one of the biggest causes for my procrastination is my iPhone. Temple Run 2 was probably the best and worst thing that could have happened to me.

Welcome back, my greenhorn hackers! Several of you have you have emailed me asking whether it's possible to install a keylogger on a victim’s computer using Metasploit. The answer is a resounding "YES"!

We share links on an almost daily basis, usually not even thinking twice about it. Whether you're sending a funny cat video to your sister, or letting your coworker know where to go to download relevant files, there are plenty of reasons you might be giving someone a URL.

Being politically correct on social media sites is super boring. I've had my fair share of rage tweets and angry Facebook posts with some colorful wording, but sometimes using and F-bomb just gets the point across better. Now that Facebook is pushing out their new Graph Search, it might be time to clean up your profile. FaceWash is a web app that searches your Facebook profile for common bad words. You will need to give the app permission to access all of your wall posts (or course). Once acc...

Social media is where we post our thoughts for the world to see, but sometimes a little more exclusivity is needed. And that's where Scrambls comes in.

Humans clearly demonstrate altruistic tendencies towards other members of groups with which they identify.

Dianne Tice and Roy Baumeister gave a bunch of college students a questionnaire in which the students answered questions about their work habits. In a class which she taught, Tice also assigned a paper with a deadline which she said could be extended and observed which students availed themselves of the option to extend.

If you have a lot of friends on Facebook, chances are that every day is at least one of their birthdays. If you took the time to individually post a message every time, you'd spend ALL of your time on Facebook, but you don't want to be a bad friend either. Let's face it, some people take this stuff personally.

If you're like me, getting as much sleep as possible is priority number one. With more and more time spent on or around our cell phones, it's becoming harder and harder to block out all the noise.

With presidential voting going down on Tuesday, November 6th, voters are beginning to anchor down on their choice for president. But with the way the media works, this may be difficult for some people because the news sites they listen to give conflicting and sporadic information on the candidates.

Numerous studies have shown that people are over-confident in their own abilities. Most people, for example, think that they are better drivers than average.

What's your Twitter handle worth? If it's considered "desirable" (aka short and simple), it'll get you around 100 bucks, or, if you prefer, the affections of a teenage girl.

As if you needed another reason to lock down your Facebook profile, the company's sketchy new partnership with data mining firm Datalogix is geared towards giving advertisers more information on what you're doing—even when you're not online. It's just not enough that they can target ads based on your preferences, now they want to know how those ads are influencing your buying habits in the real world.

Robert Templeman from the Naval Surface Warfare Center in Crane, Indiana and several of his friends from Indiana University recently developed an Android application that is capable of gathering pictures and videos from mobile devices in order to reconstruct a user's environment in 3D. The malware would come coded inside of a camera application that the user would download. The malware, called PlaceRaider, would then randomly take pictures throughout the day and carefully piece them together ...

If you've ever logged on to the popular music application Pandora, your password is saved onto that computer in the local storage...for good.

There have been plenty of headlines recently about fake followers in both politics and entertainment. Everyone gets hit by a spam account here and there, but when a large percentage of someone's followers are fake, it can look pretty bad, especially with influential people being accused of buying their followers to look more popular.

Meez is the social entertainment leader combining avatars, web games and virtual worlds. Get help with all of your Meez avatar needs with these Meez tips and tricks! Watch this video tutorial to learn how to cross-dress on Meez.

Facebook is the most powerful social network web site that helps you to connect and share with the people in you life. You need to register an account with the face book website, which is free of cost, to use their service. In face book home page you can show others your live status updates. To do this first log in to your face book application. From the left hand side column select the status updates link. This opens the 'Status Updates' web page, where you can see the status updates of all ...

"Facebook is a social utility that connects people with friends and others who work, study and live around them. People use Facebook to keep up with friends, to share links, to share photos and videos of themselves and their friends, and to learn more about the people they meet." -- Facebook

"Facebook is a social utility that connects people with friends and others who work, study and live around them. People use Facebook to keep up with friends, to share links, to share photos and videos of themselves and their friends, and to learn more about the people they meet." -- Facebook

Downloading pictures from Orkut, Google's social networking site, is simple and can be accomplished in five steps. First, log into Orkut. Second, open the image you want to save. Third, drag the image to your web browsers address bar. Fourth, right click and select Save Picture As. Voilà. There's nothing to it. Save pictures from Orkut with this video tutorial.

Since Shazam became available on iPhone, it's been easier than ever to identify a song playing somewhere in the background. You could hear something you like while watching a movie or sitting in a coffee shop, and all you have to do is open the Shazam app and have it listen for you. But what about music playing on your iPhone via Instagram, TikTok, and other social media apps?

When it comes to the ever-shifting sands of the augmented reality space, you never know which week will end up being truly historic. Well, this one was one for the history books.

The Chinese short-form social media giant known as TikTok is getting into an increasingly crowded and competitive space: augmented reality effects tools.

With millions of people working from home as a result of the coronavirus outbreak, hacking is on the rise. Nefarious black hats are taking advantage of the fact that workers have been forced to abandon their secure office networks in favor of home wireless connections. And white hats are spending even more time at home trying to be the next great ethical hacker.

Does TikTok scare you? Trust me, I get it. It's a strange, unfamiliar place to those of us not accustomed to its ways, populated by teenagers and college students with their own subcultures, memes, and humor. But here's the thing: TikTok has something for everyone, you included.