The response to the COVID-19 pandemic means that social distancing has become the new normal. It also means that more Americans are using video conferencing to connect with colleagues working from home or friends and family in quarantine because of the new coronavirus.

It's not hard to let the new SARS-CoV-2 strain of coronavirus put pressure on our minds. Fear of catching COVID-19 is never far from the topic of conversation. But it doesn't have to be that way. If you're struggling with anxiety, stress, depression, or any negative emotions due to the virus's effect on our lives right now, you might find some solace in meditation.

For enterprise augmented reality platform makers, remote assistance apps represent one of the greatest opportunities to show off the power of immersive computing. These apps enable experts to guide front-line workers or customers with AR prompts and other content in the field of view of their smartphones or smartglasses.

Whether you've made a resolution to try and read more books this year or are just looking to set time aside to listen to an audiobook a little bit each day, building good reading habits can be tough with a busy life. However, with iOS 13, Apple Books includes reading goals, which might give you that little extra bit of encouragement and accountability to help you reach your goals.

It seems like each day our phones become more integrated into our lives. School, work, shopping — so many tasks either require a phone or heavily benefit from one. But our phones are a double-edged sword that can easily distract us and harm our mental health as well.

Indian startup Dimension NXG is launching augmented reality headsets into India's consumer market with a bold idea: focusing on immersive computing in education on the high-end. The plan is to give a new kind of AR headset to schoolchildren in remote Indian villages, starting from class 5 (age 10) until graduation.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.

If you find yourself with a roommate hogging limited data bandwidth with video games or discover a neighbor has invited themselves into your Wi-Fi network, you can easily take back control of your internet access. Evil Limiter does this by letting you control the bit rate of any device on the same network as you, allowing you to slow or even stop data transfer speeds for them completely.

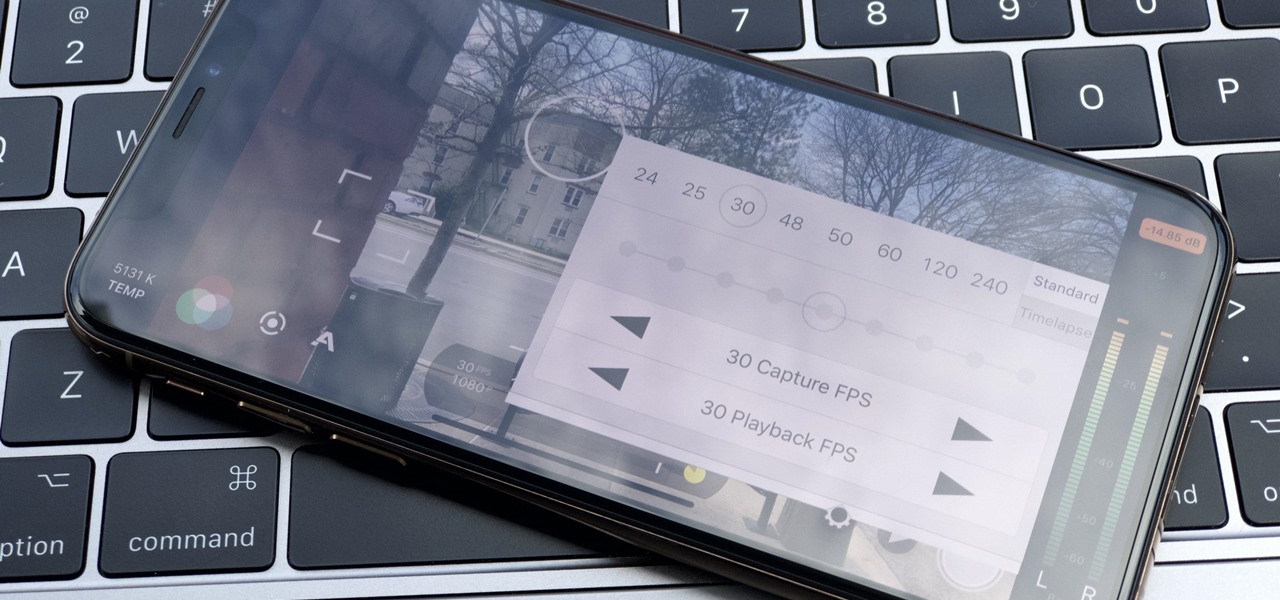
The days of bad smartphone videos are long gone. Your iPhone or Android phone is a capable video recorder, even offering different frame rate options in the native camera settings. Filmic Pro makes things a little simpler, however, and adds additional controls you wouldn't find on your device alone.

On Yelp, you have the option to check in to a business you're visiting. For you, broadcasting who you're with and where you're at is fun for social purposes, but for business owners, you're basically giving them free publicity. Well, almost free publicity. Since there's incentive to get you to check in, some businesses reward customers with special deals, such as 20% off your first visit.

You can mod every aspect of your phone's software with root, but if you want to make changes at the hardware level, you'll need a custom kernel. If you've looked into custom kernels before, one name undoubtedly kept coming up: ElementalX. It's easily the best custom kernel out there, and the reason for that is its awesome developer, flar2, aka Aaron Segaert.

Influencers of augmented reality demonstrate expertise in their fields and outline a strong vision for the future that they evangelize to others. They help define the direction of the industry and identify others who foster and create innovation in the field.

People say that money makes the world go 'round. And it's no different in the world of augmented reality.

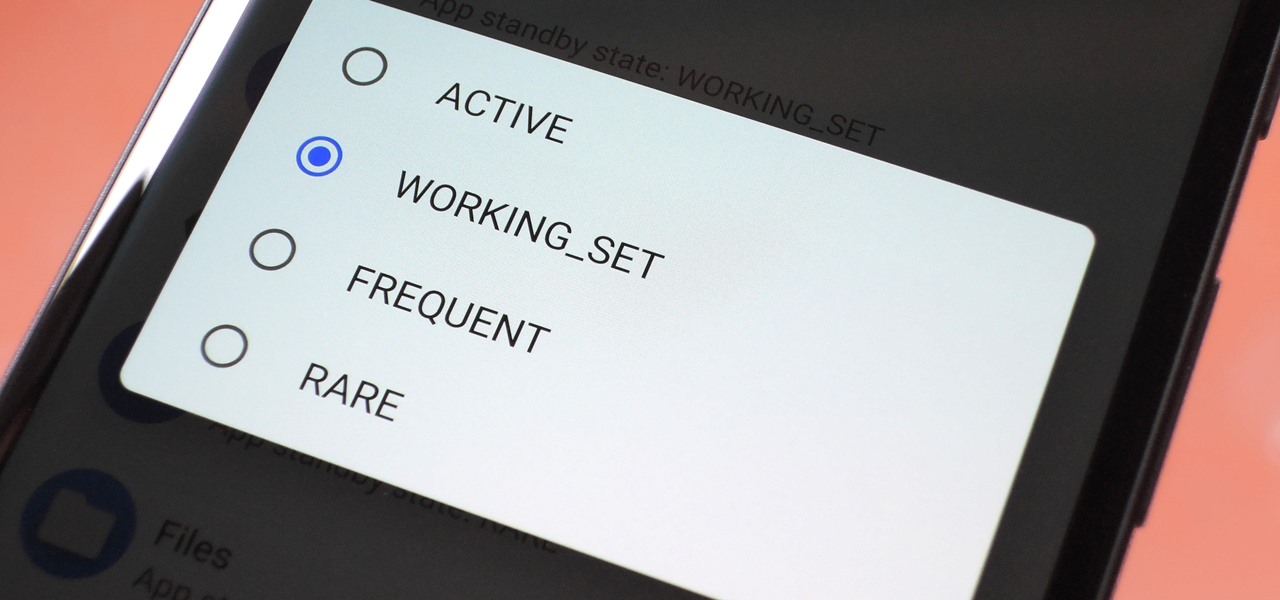
Battery drain is a major pain point for Android users, though that promises to change thanks to Android Pie's new Adaptive Battery feature. But Google hasn't said much about the inner workings of this feature, only publicly stating that it uses AI to boost battery life. So we dug in to find out what's really going on under the hood.

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.

This time last year, we got our first taste of what mobile app developers could do in augmented reality with Apple's ARKit. Most people had never heard of Animojis. Google's AR platform was still Tango. Snapchat introduced its World Lens AR experiences. Most mobile AR experiences existing in the wild were marker-based offerings from the likes of Blippar and Zappar or generic Pokémon GO knock-offs.

Give an 18-month-old a shoe, check back 10 minutes later, and it's a very big maybe he will have it on his foot. But give him your smartphone, and in a mere five minutes, he can take 100 pictures of the carpet, send weird messages, and delete essential apps. Imagine what your child could do if they were able to harness this technical aptitude and put it to good use — and they can, with learning apps.

Gmail conversations, Facebook private messages, and personal photos can all be viewed by a hacker who has backdoor access to a target's Mac. By livestreaming the desktop or exfiltrating screenshots, this information can be used for blackmail and targeted social engineering attacks to further compromise the mark.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.

With the announcement of ARKit 2.0 at WWDC 2018, Apple is bringing some powerful new capabilities to mobile augmented reality apps this fall.

Thanks to its advanced cameras, the Galaxy S9 can capture videos at an astonishing 960 frames per second (fps). To put it in perspective, you now have you the ability to record the world around you in ways that previously required expensive professional camera equipment. And that's just the tip of the iceberg.

Whether it's for your company, your professional image, or just your personal account, making a poll on Instagram is a great way to reach out to followers, friends, family, and other users to measure their thoughts and opinions about any given topic. Instagram for Android and iOS makes it fun and simple to do so, offering the same tools to professional and personal users alike.

The iOS App Store is a big place, offering over two million applications in total. However, there are actually some apps you can and should install on your iPhone that the iOS App Store doesn't include. And no, these apps do not require any difficult jailbreaking or complicated sideloading techniques — they are really simple to install.

While there are a variety of privacy-focused search engines available like StartPage and DuckDuckGo, nothing can offer the complete trust offered by creating one's own search engine. For complete trust and security, Searx can be used as free metasearch engine which can be hosted locally and index results from over 70 different search engines.

While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one. This forces the victim to connect to the fake network and supply the Wi-Fi password to regain internet access.

Screenshots taken from a compromised computer can provide hackers with access to private emails, photographs, and information found in sensitive documents. This data can be used by the attackers to build profiles of a target for social engineering attacks and blackmail or even just to release the information out in the wild.

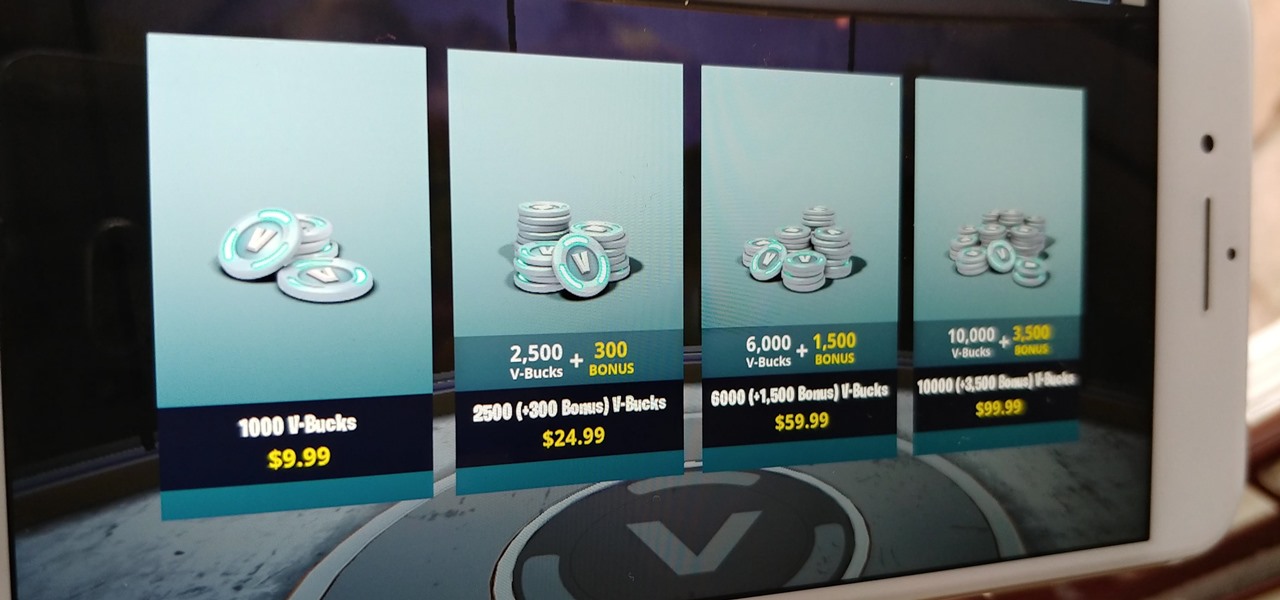
Thanks to its free-to-play strategy, many items in Fortnite Battle Royale require V-Bucks, the in-game currency. You can purchase V-Bucks with real-world money, but many would rather earn V-Bucks instead of getting nickeled and dimed by micro-transactions. While limited, there are a few ways to earn free V-Bucks in the game.

Local port forwarding is good when you want to use SSH to pivot into a non-routable network. But if you want to access services on a network when you can't configure port-forwarding on a router and don't have VPN access to the network, remote port forwarding is the way to go.

Unlike many browsers, Firefox gives a lot of control to the user. By default, Firefox does a great job of balancing security and performance. However, within the app's settings, you can modify options to shift this balance in one direction or another. For those looking to shift it toward security, here are few suggestions.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

Nintendo set the internet ablaze Wednesday night with two big announcements. First, Nintendo revealed that the Switch's paid online service will begin in September (boo), but it was the other report that really got fans excited — Mario Kart is coming to your iPhone.

Despite their sometimes fluffy reputations and occasionally ethically compromised viewpoints, tech evangelists are important, don't let anyone tell you otherwise. The right passionate voice behind the right technology platform or piece of hardware can sometimes spell the difference between fostering a community of potential users and watching a product die on the vine.

Chances are, you just point, shoot, and share photos and videos on your iPhone without a second thought about how your privacy is affected. It's fairly easy to do so since the Camera and Photos apps that Apple provides seem so innocent. But there are a few things you need to know when it comes to shooting media, sharing it, and even deleting it.

Starting your morning right is an essential first step to a productive day. Whether you're running late, rushing to catch up on the day's news, or lagging behind with early emails, little hiccups like these can have a trickle-down effect and ultimately ruin your day. Like with many problems, though, your smartphone can help.

Any internet user will need to download files eventually, and most simply have faith that what they are downloading is trustworthy. This doesn't give much clarity into the contents of the file, but if the file's author published the original checksum, comparing it to the SHA-256 hash of the downloaded file can ensure nothing was tampered with.

If you're a regular reader of Next Reality, you're more likely to spread the joy of augmented reality than most others. But it can be difficult to introduce newbies into the AR fold if you don't give them exactly the right starting point in terms ease-of-use and affordability. But fear not, oh gift-giving AR pioneer, we're here to help!

Proxies can be quicker to use than a VPN for specific applications, like web browsers or torrent clients. Both services will hide your true IP address, but a VPN is slowed down because it encrypts all data through a VPN network, while a proxy just acts as a middleman for fetching and returning requests from a server on your behalf. When speed is needed, go proxy.

Hak5's products get a lot of attention. Popping up in popular shows like Mr. Robot, their hacking tools are bold proof of concepts with space built into the design for the community to add their own tweaks and modifications. On Friday, Oct. 27, Null Byte attended the Hak5 release event in San Francisco to check out their latest devices, including the new Packet Squirrel.

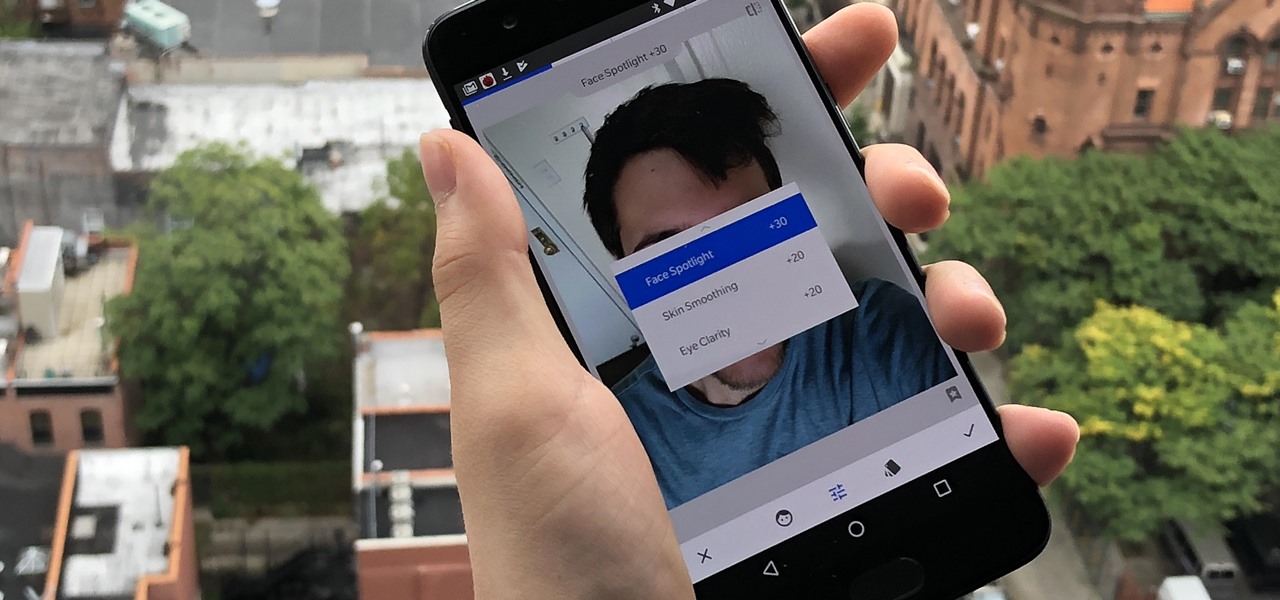
Google's Snapseed app has a plethora of editing tools to help make your photos even better. But did you know it has specific tools designed to edit your face? Not that it needs any help, of course!