
How To: Download and Install Minecraft 1.2.5 (Works on 1.2.4 Servers!)
Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!


Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!

VNC is a great protocol that you can use on Windows and Linux machines to remotely control computers. This is useful if you need to control your computer when away from home, help your grandma check her email, or help a client with a disk cleanup. VNC is secure in the sense that it requires authentication in order to make the connection, but after that, the data is sent over the internet unencrypted. This means that an attacker could sniff your traffic and snoop everything that's going on. Th...

Null Byte is looking for forum moderators! Welcome to the ninth Community Byte for coding in Python and completing the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to aspiring hackers.

Note: This shower is only visible in the Northern Hemisphere. The Quadrantid meteor shower is one of my personal favorites, mainly because of the amount of meteors it produces. You can sight more than 100 meteors per hour- that's more than 1 meter per minute. Even though that doesn't sound like much, it will make your observing experience much more exciting. The peak is short, typically lasting no more than an hour or so. It is more easily observed on the fourth, with its peak at 1:00 AM EST.

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

Welcome to the eighth Community Byte for coding in Python and completing the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to aspiring hackers.

Welcome to the seventh Community Byte for coding in Python and completing the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to aspiring hackers.

Welcome to the sixth Community Byte for coding in Python and beating the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and essentially grow together. Everyone is welcome, from novice programmers to aspiring hackers.
Hello everybody, I am Merrill Kazanjian (aka kazanjianm on YouTube). I will be your instructor. Before starting your figure drawing session. Please watch this short, funny video first to learn the basics of human proportion. The rules that you learn in this video will be very helpful once we start figure drawing (The second video).

Welcome to the fifth Community Byte for coding in Python and beating the challenges given to us from HackThisSite. These sessions are created to bring our community together, to learn from each other, and essentially grow together. Everyone is welcome, from novice programmers to aspiring hackers—even people that are nearly computer illiterate.

Skype is a great service. It allows a free solution for VoIP to VoIP calls, and cheap VoIP to landline calling. However, a very disturbing, little known fact that might push you away from Skype does exist. If you closely read the terms of service agreement, it clearly says that Skype is allowed to decrypt your messages whenever they please. Here at Null Byte, we tend to enjoy our anonymity, don't we?

Another Community Byte announcement from Null Byte! The Community Byte projects serve to teach people in a co-operative, hands-on manner. Learning from experience and immersing yourself in a subject is the best way to learn something foreign to you. In our sessions, we have started to both code and complete HTS missions. There is something for everyone here, so make sure you join in on the fun learning experience.

XSS stands for cross-site scripting, which is a form of web-based exploitation that uses client-side vulnerabilities in a web page to execute malicious JavaScript codes. JavaScript is referred to as "cross-site" because it usually involves an external website containing the malicious code. That code is most commonly used to steal cookies with a website that the attacker created and hosted on another server. The cookies can then be used to escalate privileges and gain root access to someone's ...
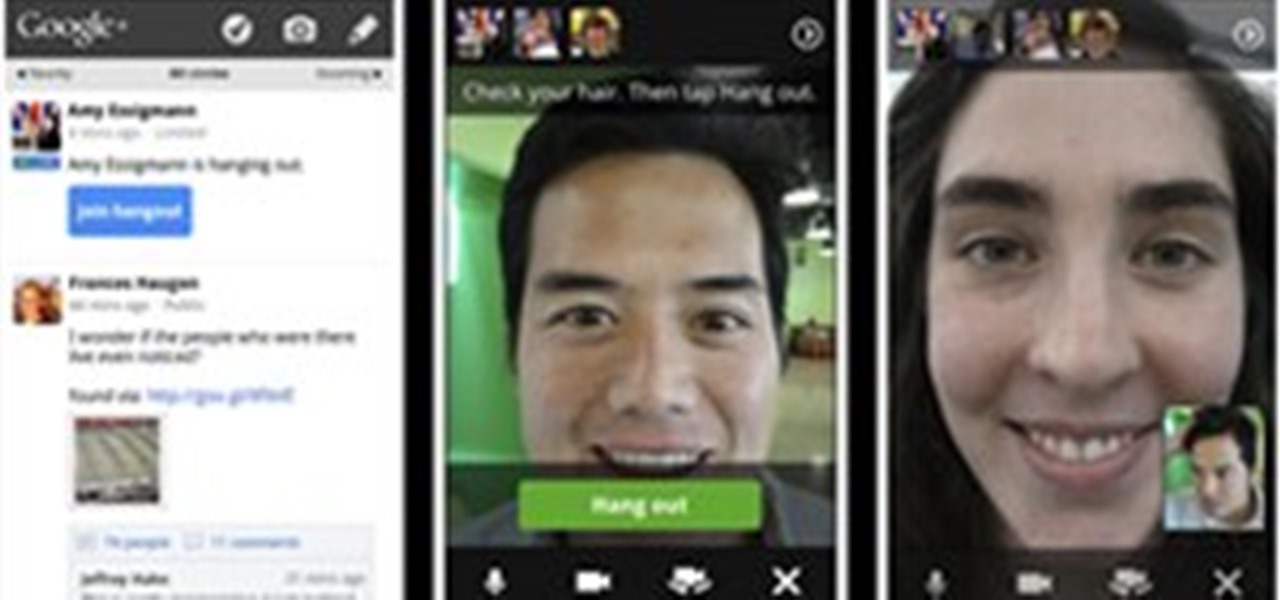
It may not seem like it, but it's been less than 90 days since Google+ was introduced to the world. Since then, we've seen many great features that have made Google+ one of the most attractive social networks around. Today, we've received even better news: major improvements and feature updates that are truly innovative.

Video game controllers are our windows into the soul of the machine, our sole means of interacting with them. More often than not, consumers seem displeased by their controllers; it's comforting to blame sticky, poorly laid out buttons for messing up your game than your own lacking skills. The original "fatty" Xbox controller was so large it caused mass consternation and prompted Microsoft to replace it with a smaller version in a matter of months.

The UK print media has been yellower than the middle traffic light for a long time now. The News of the World scandal has cast that into particularly sharp relief of late. The Sun, one of the biggest newspapers in the United Kingdom, demonstrated it again last week when they ran the front-page headline "DEATH BY XBOX".

Video game makers have never had great name recognition amongst the American public. Shigeru Miyamoto, Cliff Bleszinski, and Will Wright are names most Americans can't be bothered to remember, whatever their contribution to games have been. Most people are familiar with their work, but fail to recognize them by name or appearance.
Type: Digital, Theme Theme: Kid Toys Model
One of the common mistakes I see a lot of candidates make when they go to an interview is that they think it is a question and answer session. They approach the interview with a mindset that their role is to be prepared to answer a bevy of questions thrown at them. This puts you in a passive role, playing defense. A much more effective approach is to go into the interview with the mindset that you are a salesperson, and the product you are selling is you. You want to convince the employer tha...

There is an abstinence game being created by the University of Central Florida with $400k+ of taxpayer money. The game is directed at middle school girls to help them handle and cope with sexual advances.

Heat Illness in Young Athletes: Detection and Prevention From recreational activities to free-play to team sports to camps, outdoor activities during the

Kizeme This Japanese word, kizeme, means "spirit of attack." It is said of Miyamoto Musashi, the famed Japanese swordsman, that as he grew older he relied more on kizeme to defeat adversaries and, as a result, emerged victorious from challenges without taking the life of his opponent.

Review: Marmaduke I liked the part where the fake dogs danced.
Tips If you are taking a relatively uncomplicated flight to post, it may be to your advantage to take your pet along as excess baggage. Ask the travel agent to provide you with a cost comparison of excess baggage versus air freight shipment.(Remember also to save your receipts for shipment as a legitimate "moving expense" for the IRS.)

The entire Jackass gang are seated around a large conference table. They are seriously strapped down in the chairs and wires & electrodes are attached to all of them. In front of each them is are large unmarked push buttons. Each umarked button is linked to a certain Jackass member. When any button is pushed, some serious voltage is sent to a specific person. However the juice will be turned off, for most of the time, for a preceding event will be taking place will be well, SOME WEIRD STRANGE...

Step one. Find out who is most terrified of heights, someone inevitably will be!

Move over NASA— SpaceX is taking over. Well, not really. But today, the privately funded spacecraft company broke all expectations when their Dragon capsule fell to a soft landing in the Pacific Ocean, completing an undoubtedly successful demo flight of nearly two full trips around Earth. It was the first re-entry of a commercial spacecraft ever, bringing commercial space transportation closer to reality.

I would like to encourage you all to try something new in the kitchen area. Do you like the taste of sweet or sour? Or the delicious combination of both? You can make your own healthy walnut spread in just a few minutes and with the usage of only three ingredients. The spread can be used on a few slices of bread for a tasty sandwich.

Last time we took a look at some of the creatures of the pond, including the dragonfly nymph. Today, we examine the all-grown-up dragonflies in the field you are used to seeing on summer days! Dragonflies are not dangerous, but the extra large ones can bite you something fierce if you handle them wrong.

Hey, hackers! Now that you've hacked/owned your first "box" in my last article, let's look a little closer at another great feature of Metasploit, the Meterpreter, and then let’s move on to hacking a Linux system and using the Meterpreter to control and own it.

In this series, I'll be exploring electromagnetic weapons, how to build them, their function and application to the future, and the amazing possibilities electromagnetism has to offer. First, the electromagnetic pulse generator, or EMP. You've probably heard of these before, and their devastating effects on electronics. A simple EMP consists of a capacitor, transformer, trigger, and coil of copper wire. This, when triggered, would produce an intense magnetic field for a brief period, similar ...

If you've read Alex Long's last two articles in this series (Part 1 and Part 2), you know by now that making money rarely is risk free, and generally plays out to be a high risk-high gain/loss scenario. The best way to make money is to have money, so for this article, lets assume a financial backing of about $10,000 dollars. For the sake of simplicity, I'm going to be working with online trading systems in this article. Some stocks are traded on exchanges, where buyers meet sellers and decide...

In this article, I'll show you how to build a coil gun. A coil gun is a device that fires magnetic projectiles at high velocities, using electricity. Coil guns require no explosive propellant, therefor can be fired an infinite amount of time, providing that there is ammunition and available electricity.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. Harvesting items from animals no longer requires wasting precious time chasing after them. During last Saturday's Weekly Workshop, we built a few different kinds of animal harvesters that worked in different ways, but for this guide we will be building the most compact and easy to use harvesters we made over the weekend.

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

You're currently playing a heated game of Scrabble or Words with Friends. The game is close, too close for comfort. But you're not sweating because you're confident. You play a huge word that puts you in the lead, but then when your letter tiles are drawn...

By now, most of you have updated to the new Xbox look. Just as expected, it's got some great new features. The dashboard looks great and Bing integration is awesome, but I'm very unhappy about the new Netflix interface. It's awkward, slow, and half of the items don't even load correctly. I can't even play some movies. And the instant play feature is kind of annoying. When I first chose a video, I was hoping when it instantly started playing that it was a trailer, à la Zune. Alas, no.

WonderHowTo is made up niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

Filter effects aren't a new thing. But when Instagram hit the market, everybody began using them because it was simple. Take a picture, add an effect. It wasn't only easy, it was fun. It started a craze among smartphone users everywhere, prompting a slew of retro photo filter apps to pop up for Android and iPhone. One app that stands out from the crowd is FX Photo Studio.

This is my attempt to show people some cool things we can do with programming, and to give a small incentive for people to join the weekly Community Bytes. I wanted to make a tutorial on how to use Twitter from the command line with Python. This would have been an easy project to do not too far back, and a good bit of practice for a beginner to programming. It teaches that you can do useful stuff with programming. However, a while ago Twitter started using something called OAuth to access the...