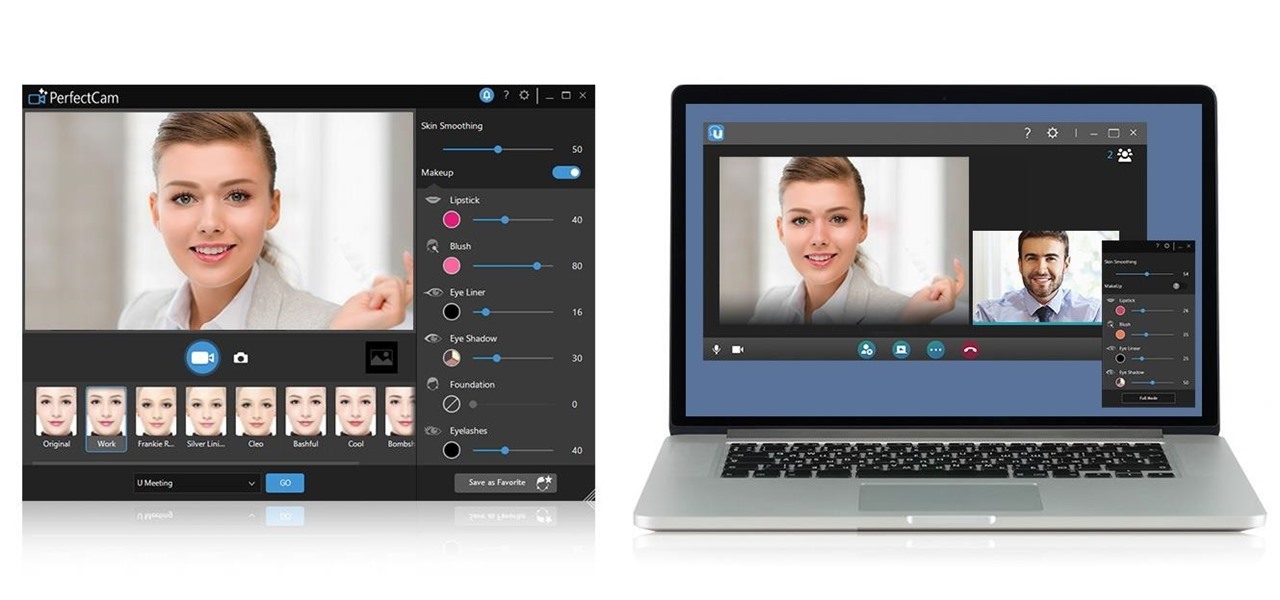
Brief Reality: Halliburton, New York Jets, CyberLink Join the Augmented Reality Movement
A survey by ABI Research revealed that only 25 percent of businesses have implemented augmented reality technology in some form or fashion.


A survey by ABI Research revealed that only 25 percent of businesses have implemented augmented reality technology in some form or fashion.
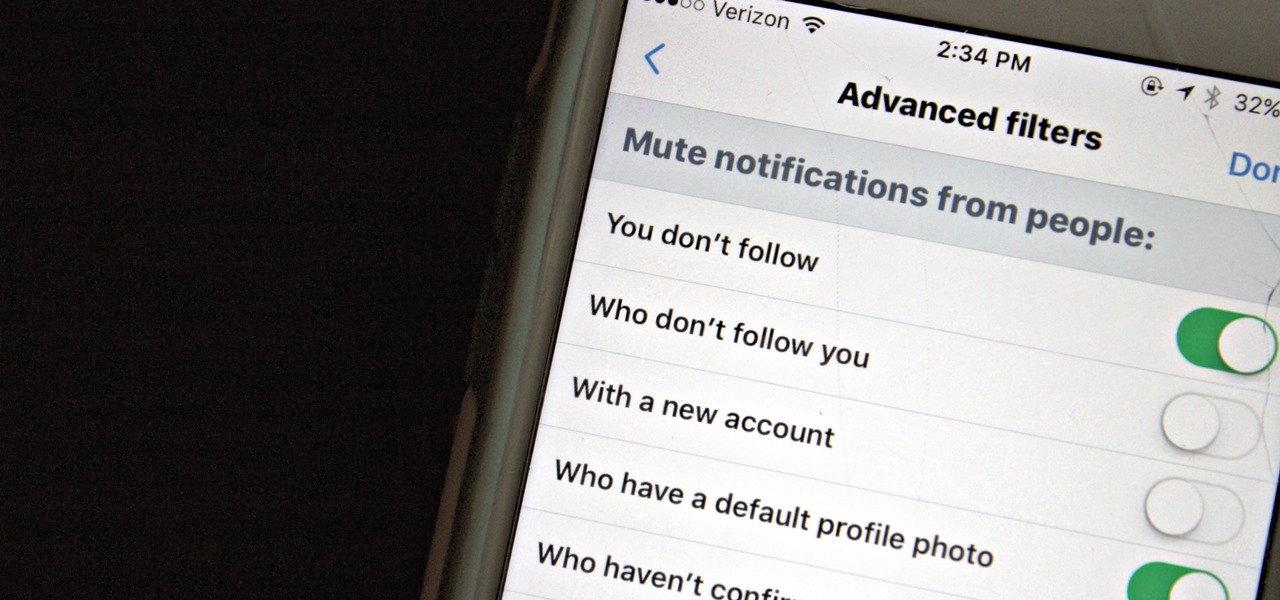
Twitter is a hotbed for abusive accounts. Because it's such an open app, strangers from all over the world can see your tweets. Obviously, not everyone agrees on everything, but sometimes things can escalate to the point where it's considered harassment from people you don't even know.

There are so many tips and tricks on how to improve your Instagram photos, but one really easy way is to use the HDR camera setting. HDR is high dynamic range imaging and takes three exposures of a photo — overexposed, underexposed, and one in the middle at the normal exposure. The end result is just one image of the three exposures combined.
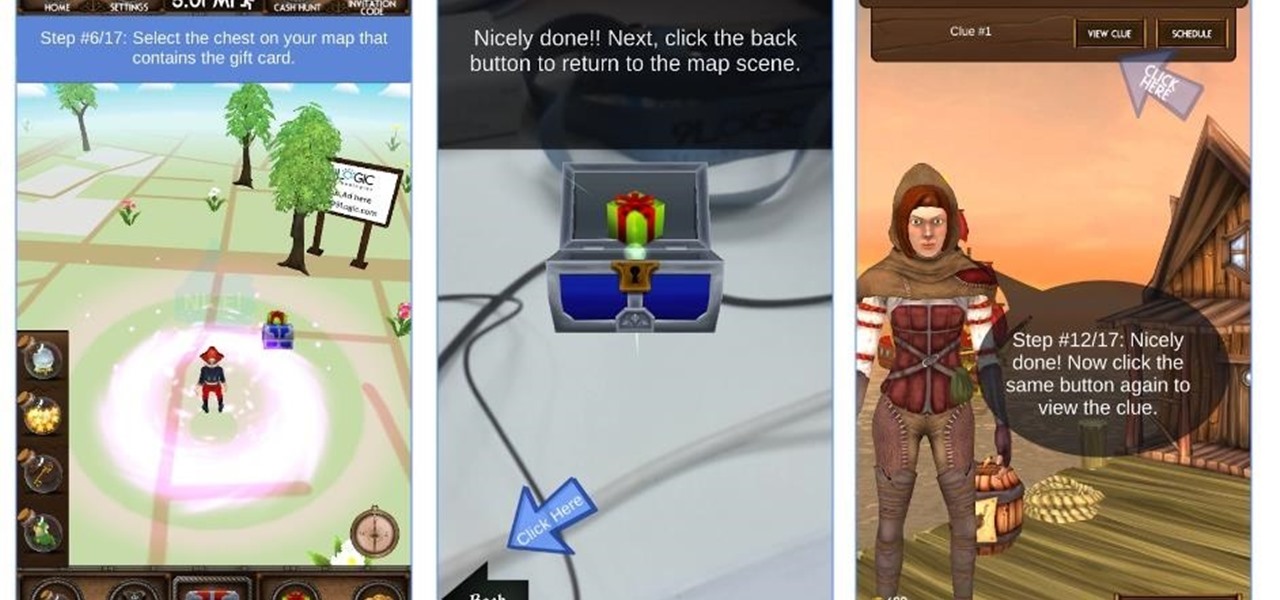
A Seattle development team is putting the "ARRRR" in AR with the maiden voyage of Captain Blimey, an augmented reality game for iOS and Android devices that puts a pirate premise on Pokémon GO.

In this tutorial I am going to look at what services are running on our Metasploitable machine and setup firewalls. This is more basic scanning of our machine to get an idea of how to get in. Obviously in a real engagement you would want to do research on Google and whatnot to find out as much as you can about your target but this series isn't about all of that.

There's a seemingly endless list of downsides that come with the coronavirus pandemic — ranging from canceled trips abroad and sunny days spent inside to limited communication with friends and family. But one of the undeniable upsides is that there's simply never been a better time to start your own online business since most people will be working from home for the foreseeable future.

If you're a regular Null Byte reader, you probably know your fair share of programming languages and have at least some experience with web or app development. But it's possible to apply your hard-earned coding and tech talents to other closely-related fields as well.

Over the past year, Magic Leap has teased its cross-platform vision of the AR cloud, which it dubs the Magicverse. While the company shared a timeline for its debut next year, it also served up new developer tools for the present.
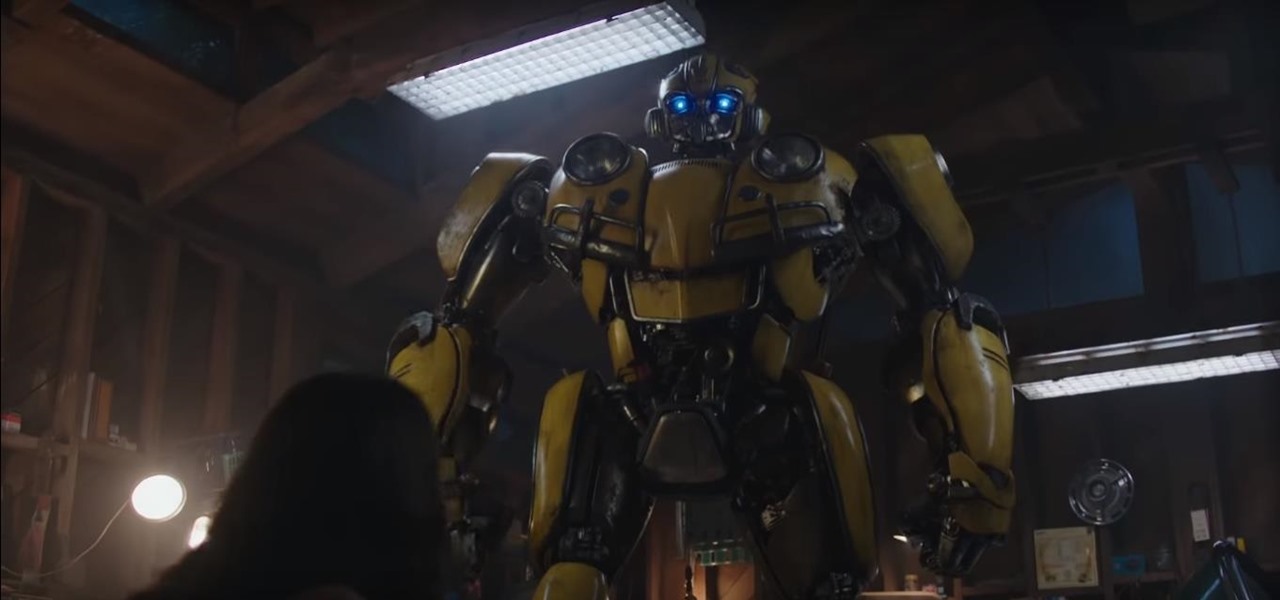
Fan favorite Transformer Bumblebee returns to theaters on Friday in a spin-off of the film franchise, so Paramount Pictures is bringing the car-robot back into the homes of fans via augmented reality.

Niantic's most successful app, Pokémon GO, has become the first app to integrate the company's Real World Platform, the developer's AR cloud technology that enables multiplayer AR, persistent content, and occlusion with physical objects.

There's more to recording calls than just protecting yourself against liability or an angry ex — oftentimes, this feature is the perfect tool to save momentous calls like breaking news of your recent engagement to loved ones. And with the prevalence of video calls, you can even capture memorable video chats such as your mom's first glimpse of your newborn on your mobile, courtesy of Skype.

It doesn't matter how cool or groundbreaking a particular technology is, if it doesn't offer the promise of big returns on investments, you'll have trouble drawing interest from both Silicon Valley and Wall Street. That's why we're increasingly seeing existing augmented reality players doing everything they can to focus in on revenue generation, which was the message coming from Snap Inc. this week.
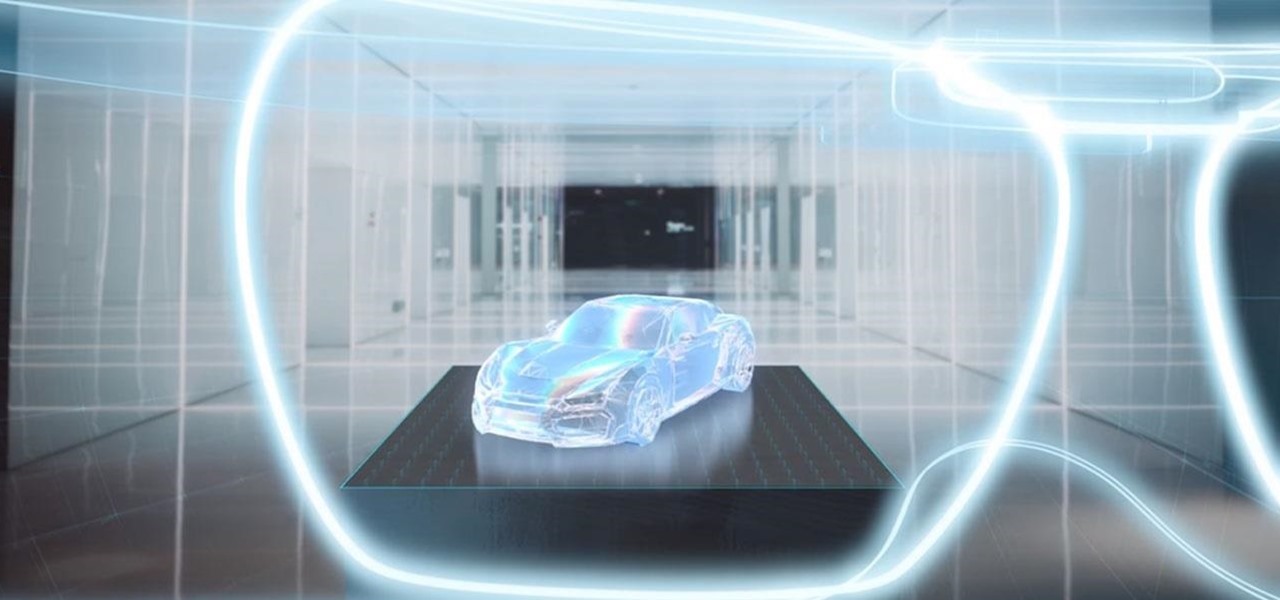
As the calendar year (and, for many companies, the fiscal year) comes to a close, it appears 2017 may stand as the new high-water mark for investment in augmented and virtual reality technology.

The next frontier for AR hardware is the consumer headset, and tech companies of varying size and tenure are working hard to strike the right mix between comfort, cool factor, and cost. How these companies handle the hype and flow of information vary wildly.

While ARKit and ARCore are poised to bring AR experiences to millions of mobile devices, one company is poised to anchor those experiences anywhere in the world with just a set of geographic coordinates.

The launch of the Audi A8 marks the world's first Level 3 car on offer in retail channels, except there is one catch: it can only take full control of driving at speeds of 37.3 mph or less.
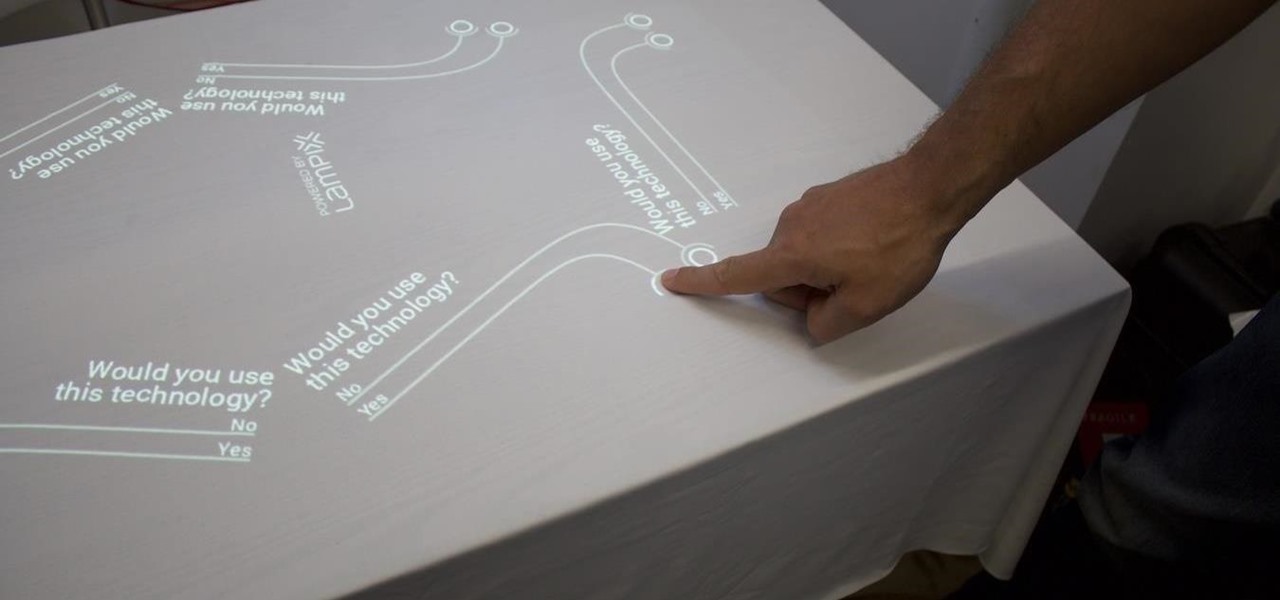
Over the past week, companies took a variety of approaches to investing in augmented reality. Lampix is backing its own effort to build an ecosystem for augmented reality platforms. Nokia and Xiaomi are teaming up on numerous fronts, potentially including augmented reality.

Making a custom location on Instagram is one of the best ways to generate traffic to your account. It gives you that extra uniqueness when it comes to standing out amongst other companies. It also allows people to check in at the same location, further promoting your account across other platforms.

Mixed reality display manufacturer Realfiction has developed a 64-inch display capable of delivering 3D holograms without a headset.

SET is great when you have a short space of time at hand, however sometimes you want to know whats actually going on under the hood or have found a site you can't clone with SET.

A Steampunk's Guide to Sex was the subject of a recent successful Kickstarter campaign, and I now hold the finished book in my hands. As such, I can say (mostly) unreservedly that you should buy this book. Allow me to tell you why, before I get into the nitty-gritty about the book itself. Sex is something of an odd topic in America because it's perfectly legal, and yet taboo. Unlike things that are illegal and not taboo, like drug use, murder, theft, etc. What this means is that children can ...

The gold standard in any business is reaching the front page of Google. You need to get your brand in front of audiences. While it can seem daunting, it's not impossible when you master SEO best practices.
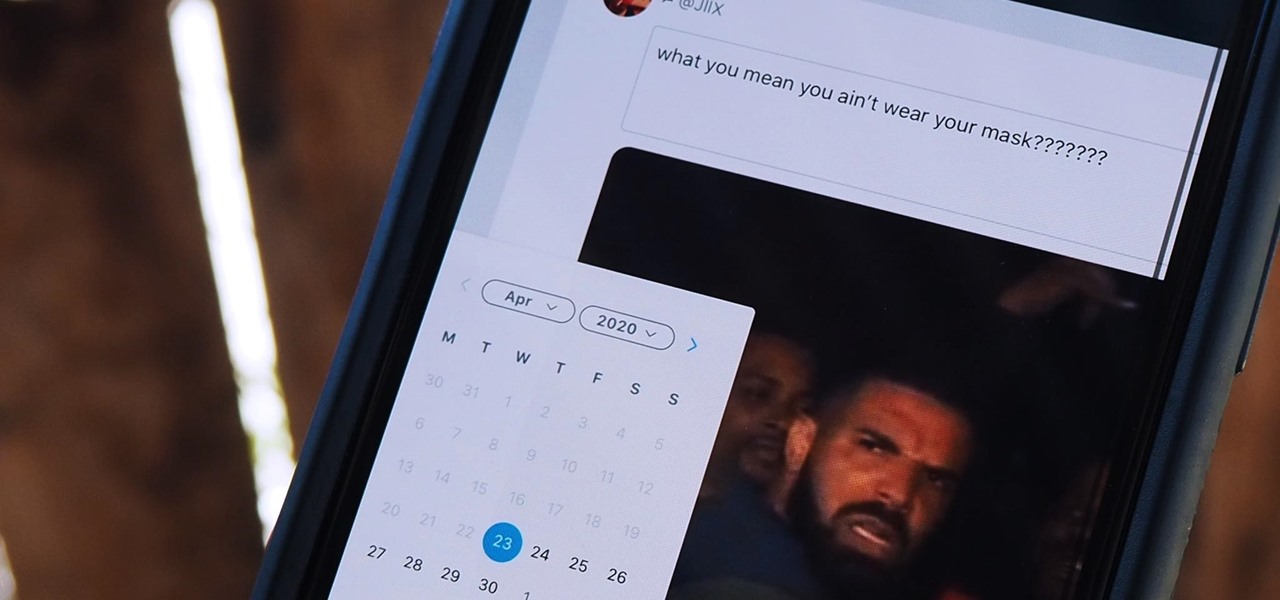
Twitter is a science. The smarter you post and engage with others, the better chance you have at building a bigger audience. Scheduling your tweets is one way to get there. Most engagement occurs at specific hours, but you may not be around then to post your tweet manually. While the official Twitter app on iOS and Android doesn't allow you to schedule, there is another way.

While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.

A convincing domain name is critical to the success of any phishing attack. With a single Python script, it's possible to find hundreds of available phishing domains and even identify phishing websites deployed by other hackers for purposes such as stealing user credentials.

Despite their sometimes fluffy reputations and occasionally ethically compromised viewpoints, tech evangelists are important, don't let anyone tell you otherwise. The right passionate voice behind the right technology platform or piece of hardware can sometimes spell the difference between fostering a community of potential users and watching a product die on the vine.

Last week, augmented reality startup Proxy42 released Father.IO, a multiplayer game that turns any indoor or outdoor space into a laser tag arena.

So much information exists online that it's easy to get lost in data while researching. Understanding the bigger picture can take a lot of time and energy, but narrowing the question to one that's easy to answer is the first step of any investigation. That's why analysts use open-source intelligence (OSINT) tools like Maltego — to help refine raw data into a complete understanding of a situation.

If you want to share a video to Stories — but it's over 24 hours old — it may seem like you can't, but there's actually a simple hack on how to do just that.

Not only has there been difficulty finding consensus on a name for driverless, autonomous, self-driving, or automated vehicles, there is also the issue of what we actually mean when we say a vehicle is self-driving, automated, and so on.

One app is continuing to make a name for itself as the go-to platform for celebrity art that transcends canvas and paint and moves in augmented reality.

After piloting the Nreal Light in South Korea and Japan via carrier partnerships and securing another round of funding, Nreal is now ready to begin selling the consumer edition of the smartglasses to the western world as well as introduce a version for enterprise customers.

Despite the unfortunate social media-driven association of Corona beer with the virus behind a global pandemic, beverage maker Constellation Brands has pushed its marketing forward like a lime through the mouth of a beer bottle.
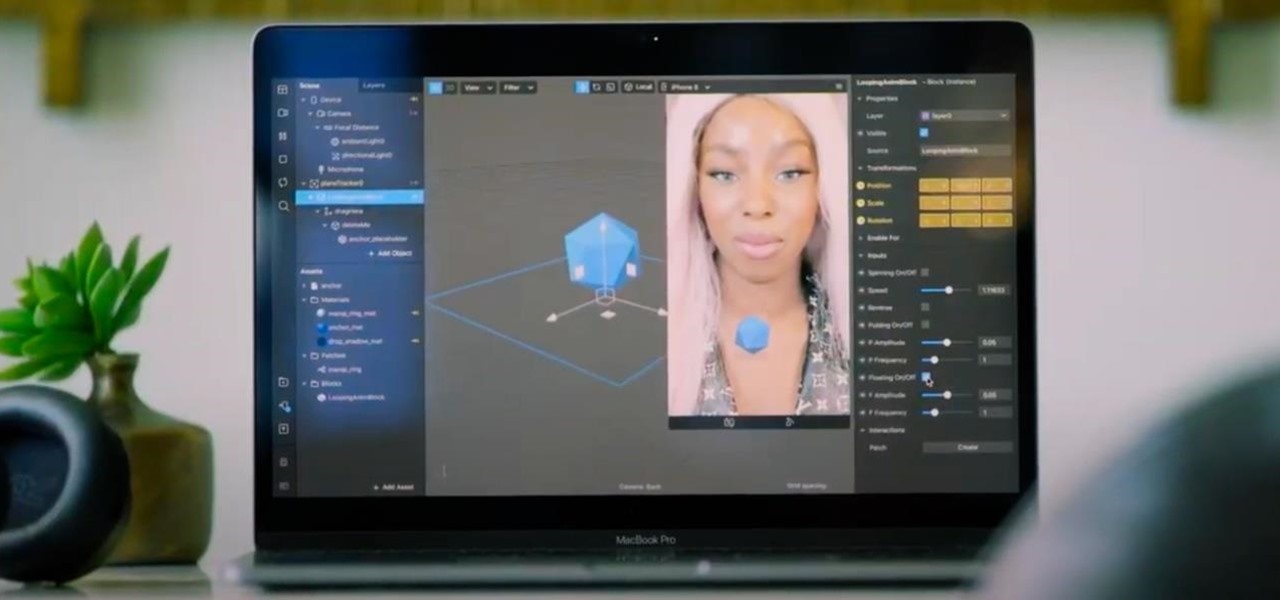
As Apple, Google, Snap, and Facebook wrestle for positioning to lure developers and creators to build augmented reality experiences for their respective tools, Facebook is looking at a learning approach for its Spark AR platform.

Back when I worked in the music industry, I never imagined there would be a day that I'd be able to sit in a room surrounded by virtual album covers while listening to beats, but that day is really here.

Websites and web applications power the internet as we know it, representing a juicy target for any hacker or red team. TIDoS is a framework of modules brought together for their usefulness in hacking web apps, organized into a common sense workflow. With an impressive array of active and passive OSINT modules, TIDoS has the right instrument for any web app audit.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodology behind an actual attack and demonstrate the proper way to practice on a VM.