
News: Hacking SCADA
Welcome back, my hacker novitiates!


Welcome back, my hacker novitiates!
One of the biggest improvements in Mac OS X Yosemite came to the Spotlight search feature, allowing users to not only search through their applications, but also their emails, text messages, iCloud, and the web.
Google's text-to-speech engine is getting pretty good these days. In a recent update, the computerized voice that reads on screen text (like Google Now search results) got an audio quality bump that brought its clarity up to its highest level yet. And with each update, that robotic voice becomes a bit more human.
Prior to the release of Android 4.0, most devices had a dedicated search button. This functionality allowed you to search Google from your home screen and app-specific content from within any app. Eventually, though, this dedicated search button was ditched in favor of an icon in the action bar of apps, and a search bar on the home screen.
Google is widely renowned for its mastery in using data to tailor specific search results and ads. Their Android and iOS search apps put this ability to use in finding the most relevant pages for your query, and their desktop site is the most-used search engine on the web as a result of it.
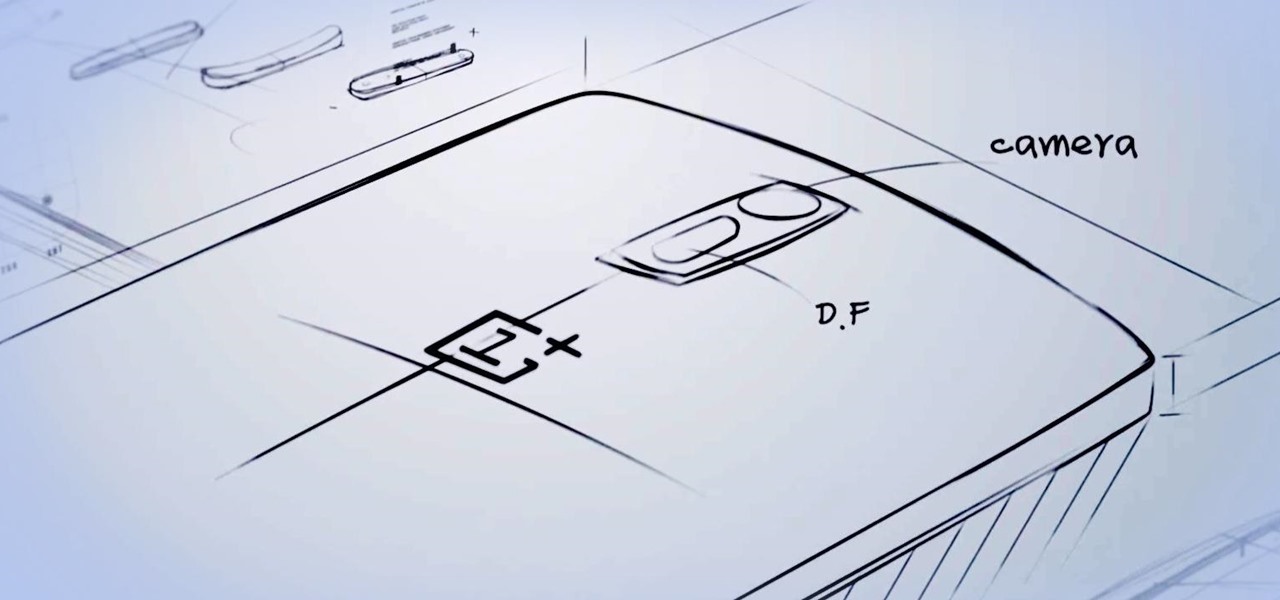
After lots of waiting and anticipation, the OnePlus One Android smartphone has been unveiled, and it's ready to take down the Nexus.

If I were a math major, I'd probably be rolling in dough somewhere in Silicon Valley right now, but since multiplying numbers and figuring out tangents gives me panic attacks, I went the English route... pays much better.

If you thought humans were reading your résumé, think again. Robots do, and their one solitary objective is to systematically crush the hopes and dreams of those who don't make the cut. Instead of paying a few humans to read thousands of résumés over a couple weeks, many companies use computer programs that can do the job in less than an hour. In fact, at least 90 percent of Fortune 500 companies use what they call an applicant-tracking system, aka rejection machines.

Remember that PSP you had? I pretty much dropped mine when smartphones became more prevalent in the mobile gaming scene. Why would I want to carry around a huge PlayStation Portable when I've already got an Android in my pocket?
The beauty of free apps is that, well, they're free. But as we all know, there is no such thing as a free lunch. Sometimes these "free" applications are only feature-limited mini versions, or they're so littered with ads that opting to pay for it is the only way to actually enjoy it.

Did you know that there's a way to start a fire by squishing air? In this project, I'll show you how to build a tool that does exactly that—and I'll give you a sneak peak into the principals of how a diesel engine operates!

This video shows you how easy it is to change the oil on a 2007 Suzuki Boulevard S40. Remove the drain plug and drain the oil into a drain pan. Remove the engine side cover and pull the comb filter out. Make sure the the o ring is on inside the filter before installing the new filter. There is also an o ring that goes onto the cover before installing the cover. Bolt the cover back on. Install the drain plug. Put the funnel inside of the refill and add 2 liters of oil(refill is above the oil f...

Bejeweled Blitz is a hard game to play, but easy game to cheat. These new hacks are sure to get you your next record breaking game for the whole Facebook community to admire.

Restaurant City is a Facebook game that allows you to create your own restaurant. Watch this video tutorial to learn how to cheat money in Restaurant City (09/30/09).

Tower Blocks is a Facebook game that allows you to test your speed at building the tallest tower ever! Watch this video tutorial to learn how hack Tower Blocks on Facebook (09/02/09).
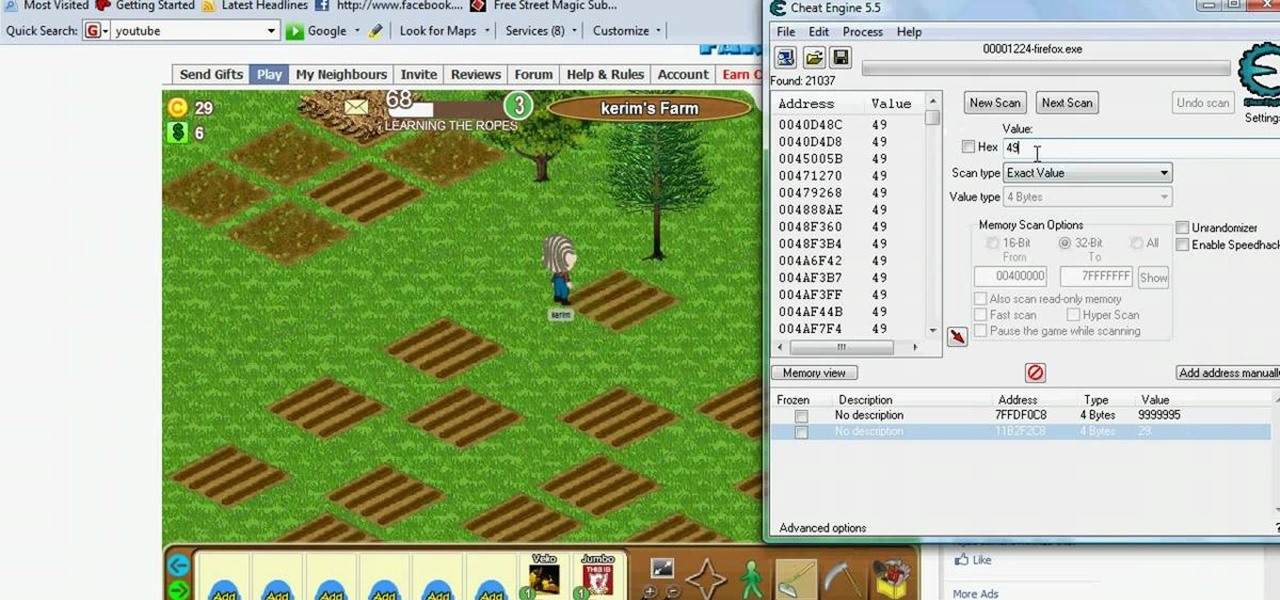
Farm Town hacks, cheats, glitches. How to hack Farm Town. Watch this video tutorial to learn how to hack Farm Town coins (09/14/09). You'll need Cheat Engine 5.5.

Unless you're a high-schooler building a nuclear fusion reactor, the hardest part of a science investigatory project often is coming up with a good idea. You want it to be cool yet feasible, novel but still useful.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

In this video demonstration you will see the work done on a GM 3.1 Liter V6; your instructor is replacing the cam cover seal. First raise the car into the air, remove the tire wheel assembly and place a jack stand underneath the car or vehicle on the side where you have removed the tire wheel assembly. Now remove the serpentine belt from the engine by using a 3/8ths breaker bar. Place it on the tensioner and lift up while removing the belt from the alternator. Keep lifting the belt out from t...

Too many people just drive their cars for a few years and then replace them. When treated right, cars can keep on running for decades. You may not be able to keep your car running forever, but you can definitely extend its life.
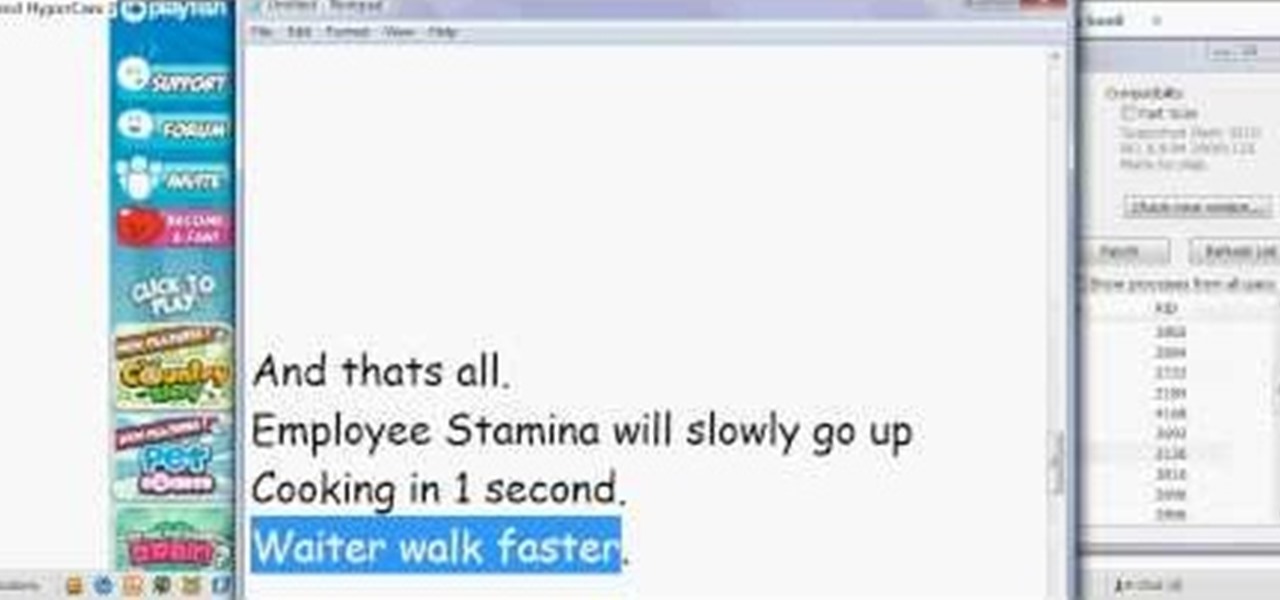
Want a cool 3-in-1 hack for Restaurant City? Go no further. You don't even need Cheat Engine for this one! Just Piaps Restaurant City Hack.
Want some easy to follow instructions on how to hack Icy Tower? They're right here. Hacking Icy Tower 1.4 has never been easier.
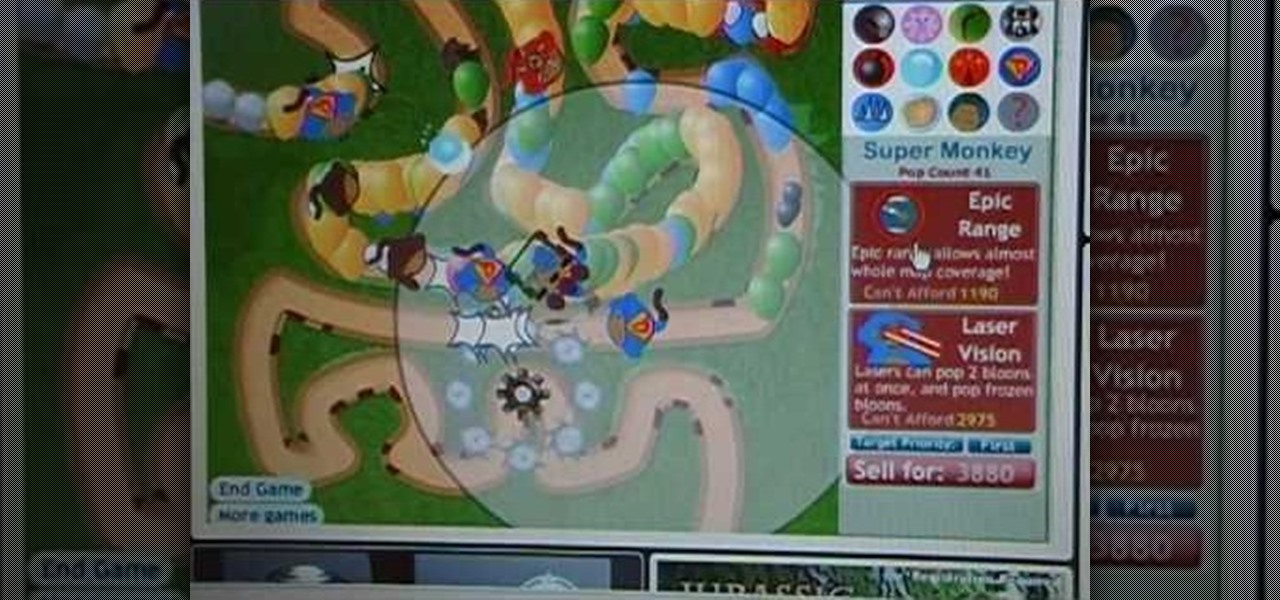
Believe it or not, it's still possible to play flash games without Cheat Engine. Like this BTD3 trick. Not sure if it's quite a cheat, but it is a handy tip to get you to your win.

Basic car fuel maintenance keeps an engine running and extends the life of a vehicle. Learn basic car fuel maintenance tips from a professional mechanic in this free maintenance video series.

The enterprise-focused category of augmented reality doesn't often get the headlines due to its relatively sedate profile as a mostly factory floor and training-based tool.
Apple no longer has an exclusive province to LiDAR for the purposes of augmented reality. This week, headset maker Varjo unveiled its new VR-3 and XR-3 headsets, the latter of which includes LiDAR sensors and stereo RGB cameras to enable depth sensing and inside-out tracking of real-world environments for "pass-through" mixed reality experiences.

The modern remote workforce faces many challenges, but perhaps none is greater than organizing calls and syncing tasks. Many platforms are convoluted and difficult to manage. Team members get bogged down by administrative tasks instead of staying productive.

When you receive a call on your phone, you likely don't think twice about the design when the notification pops up. Whatever the default UI is, that's what works best since there aren't any other choices to pick from. At least, that's how things used to be in the past — we're starting to see some new OnePlus mods that allow you to expand on it.

Despite some of the biggest players in tech still lagging in terms of offering smartglasses options, there are nevertheless a number of smartglasses makers, including North and Vuzix, with consumer-grade smartglasses on the market right now.

It's been said time and time again: reconnaissance is perhaps the most critical phase of an attack. It's especially important when preparing an attack against a database since one wrong move can destroy every last bit of data, which usually isn't the desired outcome. Metasploit contains a variety of modules that can be used to enumerate MySQL databases, making it easy to gather valuable information.

You may soon add feigning eye contact to the list of ways that augmented reality is improving our lives.

Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attacker can use these subdomains to serve payloads to evade network firewalls.

Your phone's keyboard is one of the most commonly used apps. Whether you're typing out status updates, sending private messages, or just bombarding everyone in sight with as many emoji as you possibly can, you probably couldn't get by without a good keyboard app.

The next libSSH or OpenSSH exploit may be just around the corner. Keep your SSH service out of Shodan's database before hackers find new ways to bypass the password protecting the server.

Apple CEO Tim Cook has said that augmented reality (or, AR for short) will "change everything." But what, exactly, is augmented reality?

Any internet user will need to download files eventually, and most simply have faith that what they are downloading is trustworthy. This doesn't give much clarity into the contents of the file, but if the file's author published the original checksum, comparing it to the SHA-256 hash of the downloaded file can ensure nothing was tampered with.

After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.

In the case of rotting food, microbes are not our friends. Now, scientists have developed a new food wrap coated with tiny clay tubes packed with an antibacterial essential oil that can extend the shelf life of perishable food, so we can waste less and eat more.

The bacteria in our gut — a community called the gut microbiome — have been in the spotlight a lot lately. What we're learning about how our intestinal bacteria adapt and grow with our bodies could help athletes perform better, according to researchers starting a company focused on creating probiotics that mimic athletes' microbiomes.

Nvidia's decades-long development of graphics processor units (GPU) for PCs has given it a major leg up in the driverless space.