Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

It is almost indisputable that smartglasses and head-worn displays are the future of augmented reality. However, at this precise moment, they are still a very niche market.

If you need to hack an Android device, try a remote administration tool. Known more familiarly as a RAT, there are open-source RATs that are barebones and exorbitantly priced RATs that are more polished. There are also low-cost and polished RATs that aren't intended to be RATs at all, such as Cerberus, an anti-theft solution available right on Google Play.

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic

Customization has always been the main draw of Android for me, but Apple has an impressive feature on iOS 16 that lets iPhone users create customized emoji wallpapers for their home and lock screens. While Android doesn't have something like that built-in by default, it's easy enough to make emoji wallpapers for your Android phone.

Spoofed phone calls originate from one source that's disguising its phone number as a different one, and you probably get these calls all the time. Maybe they're numbers from your local area code or for prominent businesses, but the callers are just hijacking those digits to fool you into picking up. Turns out, making a spoofed call is something anybody can do — even you.

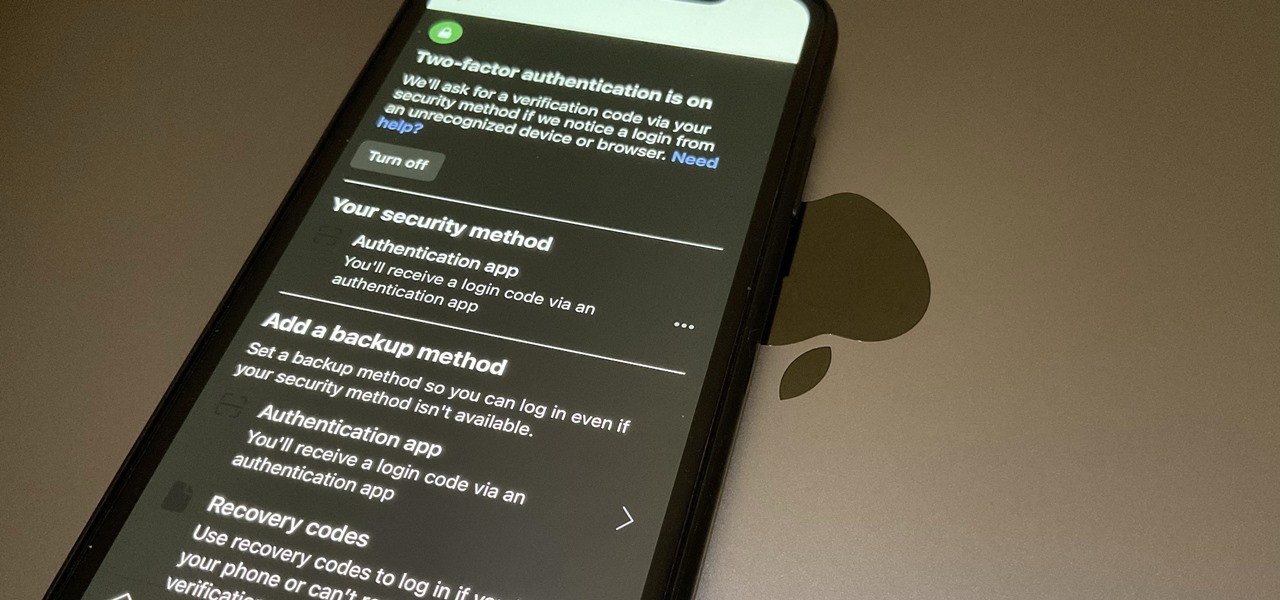
Most websites and apps support two-factor authentication (2FA), which adds an extra layer of security to your accounts by requesting another form of identification beyond username and password. The second factor can be a recovery code, physical security key, or one-time password (OTP) that only you can access, even if someone else has your password. This process is easier than ever thanks to iOS 15.

Malevolent hackers can divert your incoming calls and texts to any number they want, and they don't need to be a criminal mastermind to do it. Even friends and family members can reroute your incoming calls and messages so that they know exactly who's trying to reach you, and all it takes is seconds of access to your iPhone or wireless account. These secret codes can help uncover them.

Apple's first big iOS 17 point update for iPhone just came out, and it includes some of the features initially planned for the iOS 17.0 release last September. But there's much more to iOS 17.1 than that — exciting new features and changes are hiding within Books, Music, StandBy, App Store, Lock Screen wallpapers, Apple Wallet, and more.

Data can be injected into images quickly without the use of metadata tools. Attackers may use this knowledge to exfiltrate sensitive information from a MacBook by sending the pictures to ordinary file-sharing websites.

OpenBSD implements security in its development in a way that no other operating system on the planet does. Learning to use the Unix-like operating system can help a hacker understand secure development, create better servers, and improve their understanding of the BSD operating system. Using VirtualBox, the OS can be installed within a host to create a full-featured test environment.

Apple's latest big software update includes an entirely new Apple app, a controversial change in the TV app, better Siri control, an improved Shortcuts app, interesting Safari upgrades, Apple Music Sing, and more. Keep reading to see what iOS 16.2 has to offer your iPhone.

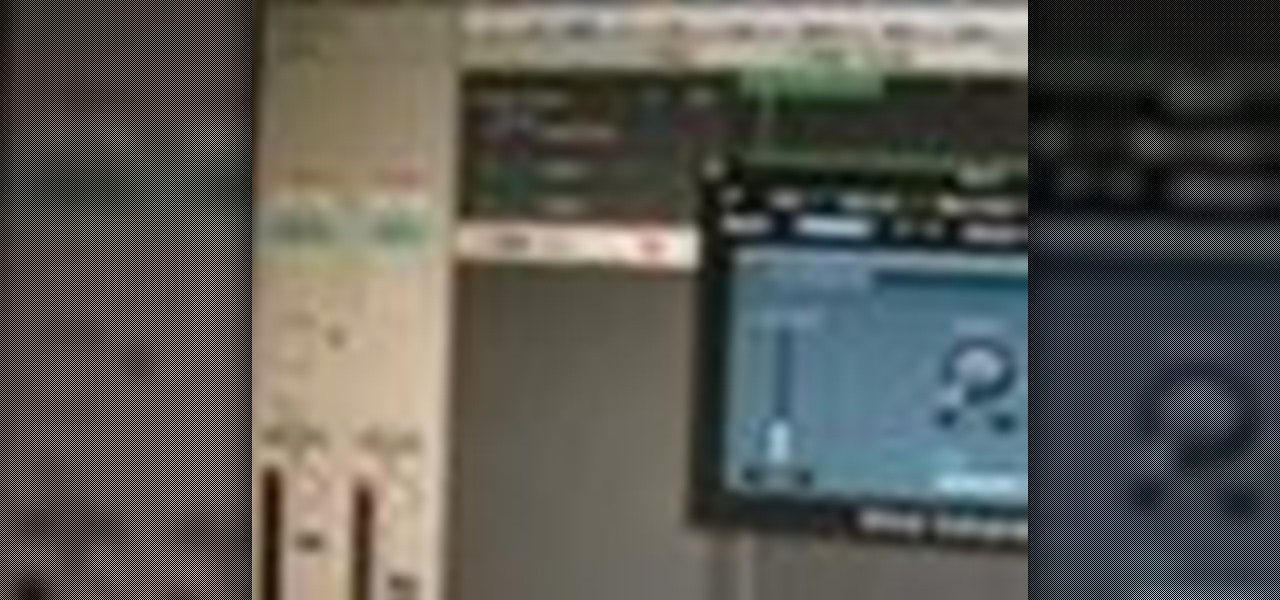
n this episode Academy and Grammy Award winning engineer Les Brockmann will share a little from his upcoming HowAudio.com title on MOTU Digital Performer 5.1. Here Les is talking about the audio set-up.

Create beats with the music program Dr. Dre and Kanye West use to write songs! Learn how to make beats with the Logic Pro 8 Ultrabeat drum machine in this free music production tool tutorial from a professional audio engineer.

Self-recording and mixing music today is easier than ever with programs such as Apple's Logic Pro 8. Mix any piece of multi-track music easily and quickly with tips from an experienced studio engineer in these free recording videos.

Apple Loops is a pre-recorded library of beats in Logic Pro. Learn how to use Logic Pro 8 software to make music in this free music production tool from a professional audio engineer.

Correct the pitch of your vocal and instrument tracks with this innovative software program. Learn more about digital pitch correction in this Logic Pro software tutorial from a professional recording engineer.

Correct the pitch of your vocal track with this innovative software program. Learn more about digital pitch correction in this Melodyne software tutorial from a professional recording engineer.

Create funky beats in the same program used by Dr. Dre and Kanye West. Learn how to use Logic Pro 8 software to make music in this free music production tool from a professional audio engineer.

Make your mix sparkle with Logic Pro! Learn how to use Logic Pro 8 software to fine-tune your music mix in this free music production tool from a professional audio engineer.

Borrow a few sounds from other songs to make your mix stand out. Learn how to use samples with Logic Pro 8 software in this free music production tool from a professional audio engineer.

Equalizing (EQing) instruments, vocals and effects is an important part of the mix process. Learn how to use Logic Pro 8 features to mix your recordings in this free music production tool from a professional audio engineer.

In this online video series learn how to install electric garage doors from licensed engineer and licensed home inspector Drew Finn as he demonstrates electrical garage door installation including: mounting the door bracket, attaching the rail to the head, installing the drive belt, mounting the wall bracket, attaching the rail to the wall, attaching the head to the ceiling, attaching the door to the rail, installing the electric eye, wiring the head, installing the wall switch, testing the d...

In this video series, watch as professional sound engineer Kip Bradford teaches how to make and repair audio cables. Learn the tools needed to repair and make audio cables, learn what kind of solder to use, learn the types of connectors and wires to use, how to solder audio cables, how to remove solder from a solder joint, and how to roll audio cables.

Creating drum beats is a crucial part of making a great song. Learn how to use Logic Pro 8 Ultrabeat drum machine feature to create and mix your recordings in this free music production tool tutorial from a professional audio engineer.

Create your own mix with the music software program used by Dr. Dre and Kanye West! Learn how to use Logic Pro 8 plug-ins to make music in this free music production tool from a professional audio engineer.

In this series of video clips you’ll learn how to build a music recording studio in your own home. Expert musician and studio engineer Arie Pytel shares tips on the various types of microphones, monitors, headphones, and computer recording software that are available. He takes you step-by-step through the process of connecting the mics, MIDI components and other devices you’ll need to start recording your own music. By following the simple steps in these free videos you can build a home recor...

Cubase is digital audio workstation great for making MIDI sequences and recording digital music. Learn MIDI sequencing in the Cubase DAW from an audio engineer in this free Cubase tutorial video.

It's currently 2011, but when you fire up your game console, put your hands on the controller and play the new Dead Space 2 video game, you're warped into the future— into the year 2511— just 3 years after the events that took place in the first Dead Space. And it's sure to be a beautiful, frightening, futuristic experience.

It's somewhat funny that the HTC ThunderBolt smartphone would be released around the same time as Apple's new Thunderbolt technology. Mainly because HTC's smartphone isn't exactly something I would compare to a flash of lightning, which averages around 60,000 miles per second. But Apple's new interconnect surely deserves the Thunderbolt designation.

In this episode, Chief Engineer Eran Stern works furiously to get his Starship's transporters back on-line to rescue a fellow crew member trapped on a hostile planet. But time is running out. Will Eran be able to build the transporter in After Effects in time?

The Kinect is sure to swarm the homes of Xbox 360 gamers this holiday season. Even though some of us are amazed at the hands-free gaming capabilities it offers, others feel it to be frustratingly limited. Adafruit Industries is one of them.

Are you having problems because the game was released a long time ago and the more experienced players are better than you? Then you should be very excited to find out that I will be giving you some general tips & tricks about the different classes that I have learned the hard way.

"Connect via Facebook" — these words are coated on over a million websites nowadays, but Facebook Connect poses a risk of leaking personally identifiable information to those third parties. If you're not convinced Facebook Connect is safe, then turn off the flow of personal data to those websites!

Moving a 2000 pound safe isn't easy... I was working as manager for a construction company that was performing an up fit on a century old building in downtown Concord, N.C. The owners wanted us to move a two thousand pound (that's a ton!) safe up to the second story so that it could be displayed in their new office. The safe was located between the first and second floors in a small office that was used for accounting purposes in the old days when said building had been a hardware store.

We've provided Google insiders, Google's community managers, authors, and celebrities for you to add to your circles. This week, we've discovered over 100 brilliant photographers for you to follow.

PopSci has compiled an amazing list of 30 college labs that would tempt anybody to re-enroll. If you know any high school juniors or prospective grad students, pass this along. They just might reconsider their initial choices.

Wired posts a gallery of the original models of now iconic devices, with some fun tech-fetish facts. Did you know the first cell phone weighed a whopping 4.4 pounds? Or that the world's first super soaker was invented completely by accident? Examples below; click through for Wired's complete gallery.

Watch this video tutorial to learn how to troubleshoot central heating problems. Step 1:

The crew from NASA's International Space Station wish planet Earth a heartwarming Merry Christmas and a Happy New Year. (Check out flight engineer Cady Coleman's hair. Zero gravity is awesome.) For the nostalgic, the legendary Apollo 8, the first manned mission to the Moon, wishes the world Merry Christmas in s live television broadcast from lunar orbit, December 1968: