
As it turns out, your Android apps are pairing together to share your data without asking for your permission first. Researchers from Virginia Tech developed a tool called DIALDroid to monitor exchanges of data between Android apps over the last three years, and what they've found is quite alarming.

When the mosquito that carries the malaria parasite (Plasmodium falciparum) bites someone, the parasite must travel to the liver where it undergoes part of its lifecycle before infecting red blood cells and spreading to its next host. Until now, the first step of how the parasite gets to the liver hasn't been clear.

A dangerous bacterial disease is infecting dogs in northern New Jersey, forcing owners to keep their pets inside.

Uber's driverless cabs began picking people up in Arizona in February, after its attempt at a pilot test in San Francisco. Now, one of these cars has been in an accident, and that's just the tip of the iceberg.

Baidu's self-driving car unit has had a tough week. Today, the company's leading artificial intelligence (AI) expert, Andrew Ng, announced in an optimistic blog post that he would be leaving the Chinese search engine company to pursue AI research on his own.
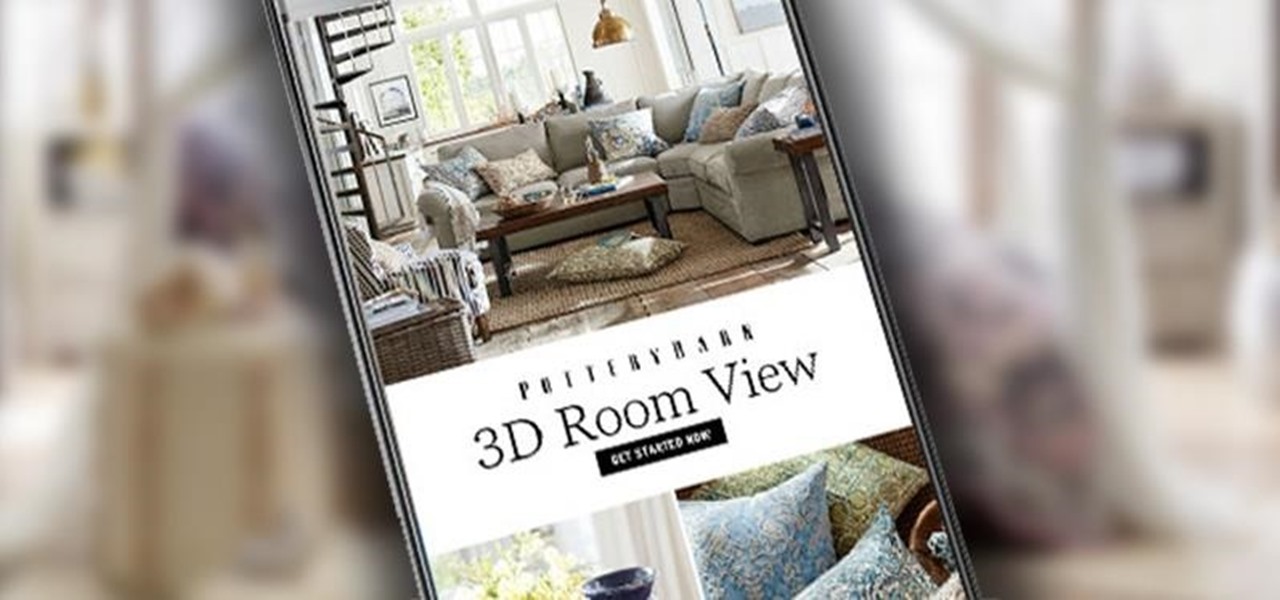
Pottery Barn has teamed up with Google to create 3D Room View, a new mobile app to allow all wannabe interior designers (like me) to pick out the perfect couch, table, or whatever, and then overlay it onto a spot in his or her house.

Dirty, malformed, and outright mischievous text strings have long been the enemy of interactive website developers. Strings contain any combination of letters, numbers, spaces, and punctuation, and are entered into text boxes on websites by users. These strings in particular can do everything from highlighting XSS vulnerabilities to soliciting 404 error pages.

Yes, bubonic plague—the Black Death that killed millions in the Middle Ages— is still out there. It even infects and kills people in the United States. Without treatment, half the people infected die, but the Food and Drug Administration approved ciprofloxacin in 2015 to treat plague, and it has just successfully been used to stop the infection in five people.

We usually associate Salmonella bacteria with a dangerous type of food poisoning, but they actually are pretty good at seeking out tumors. That trait made the bacteria a great candidate to deliver a protein that would help knock tumors out.

Since the 1960s, bacteria have been hopping a ride into space on space vehicles and astronauts, and have been cultivated within experiments on space shuttles and the International Space Station (ISS). The extreme growing conditions and the low gravity environment on the Earth-orbiting vehicles offers a stable research platform for looking at bacteria in a different light.

Last week, a new Kickstarter campaign arrived for a completely untethered, augmented reality headset for under $300 called Okularion. While at first glance, this unit looks very much like a Samsung Gear VR, one thing that sets it apart (aside from being untethered from a nearby computer) is that it does not require a smartphone. Well, that and it's an augmented reality headset as well.

Google's former Self-Driving Car project, now graduated from Alphabet's X division as Waymo, has found a collaborator and potential new partner in Honda. This is an interesting turn of events given traditional automakers' reluctance to work with driverless-car startups over the years.

Many new parents will tell you how hard it is to name a baby. Some have stories of how they knew what the name of their child would be from before conception, only to change their mind when they were born. Sometimes new babies can go weeks without a name since there is an endless selection to choose from.

Robots are always really cool, if you ask me. Sometimes they're made out of Legos, and that's even cooler.

Android device manufacturers may see the new Pixel "Phone By Google" devices as just another competitor, one that likely won't upset their entry-level margins. But that would be a mistake. Pixel is Google's call to action. With Google now offering as near to perfect an Android experience as we've had so far, OEMs that want to keep selling smartphones in a world flooded with them will need to start working for the privilege.

Summer is a sensational time for barbecues of all sorts, and sausages always seem to be in the limelight. From backyards to ball parks and picnic tables, crafting the best barbecued sausage is an art well worth mastering.

We like picnicking of all sorts, from picnics in bright, sunny weather to grey or rain-drizzled picnics. So it's not a stretch to say that we've become quite good at packing sandwiches to enjoy later. But we're always looking for a better way to do things, and that includes our sandwich making—and we think we've found the best way to make a sandwich ever.

This tutorial follows the same idea as my original tutorial for windows, but I've redone it to work with Mac OS X. Here's how to get a meterpreter session from your victim opening a malicious word document:

Cable TV providers were dealt a pretty significant blow on Thursday, February 18th, 2016, when the Federal Communications Commission decided that customers should have a choice in what type of device they use to watch cable, instead of being forced to rent a set-top box.

In my last tutorial, I talked about creating a virus inside of a Word Document in the scenario of a mass-mailer attack. In this post, however, I'm going to be covering creating a fake image or screenshot with a meterpreter backdoor hidden inside to be used in a similar scenario. Step 1: Creating the Virus

Every phone has its issues and quirks, and the Nexus 5 is no exception to this rule. One of the most common troubleshooting questions asked by its owners is "Why does my Nexus 5 keep shutting off or restarting?" where the device suddenly decides to reboot or power off randomly on its own.

Cast iron pans are a timeless treasure—they're an essential kitchen tool that will stand the test of time, and no home kitchen is complete without one. However, they do have a reputation for being difficult to care for... with arguments both for and against regular seasoning. In 2010, a blogger named Sheryl Canter claimed that she found the best way to season a cast iron pan that would keep the cast iron from rusting... or requiring re-seasoning! And after a few hands-on test by Cook's Illust...

Hello again, and welcome back to another tutorial on functions, this time, covering recursion. What Is Recursion?

First of all, Merry Christmas and Happy New Year to all Null-Byters that learn and teach in this wonderful site. In this article we will explore the basics of the meterpreter's IRB (Interactive Ruby Shell).

Welcome back, my greenhorn hackers! As expected with Null Byte's dramatic growth over the last year, we have added many new aspiring hackers who are still lacking in the basics of networking. In addition, with the new "White Hat" certifications coming out shortly, the exam will require some basic networking skills and knowledge to pass.

Do you ever thought that you can't control an Internet disconnected system? I saw a funny video in Chema Alonso's youtube channel (A well-known hacker of my country and creator of Fingerprinting Organizations with Collected Archives among other security tools), and decided to post something similar.

Greetings dear null byters, today we start a new series, we will start to attack users using social networking that are popular such as Facebook, Skype, and much more, and in part 1 of the series will engage users of Skype.

In part one of this tutorial we found out that your English teacher is a paedophile, by using a Man in the Middle attack to intercept his internet traffic.

There is no greater food to master than steak. If you can make a steak that's only marginally better than your neighborhood Applebee's, you'll still have friends waiting outside your door for steak night. And if you can make steak as good as that expensive gourmet steakhouse you went to for your birthday? Well, your popularity is about to increase dramatically.

When summer rolls around, I think of two things: grilling and ice-cold beverages. To me, nothing beats loading up the grill with charcoal, letting the smell of smoke get stuck to your clothing, and imbibing the most refreshing drink you can find.

There's something primal about the smell of smoking food. Somewhere deep in the recesses of our souls, we remember a time when humans only ate by the fire. Or perhaps that's just something I tell myself. Either way, it's hard to smell smoke and food and not feel like you should be eating. And, as chef Edi Frauneder said in a recent Saveur article, "Grilling is convivial. There's something about this act of coming together over an open flame that just says vacation."

Hello fellow grey hat hackers, as hackers it becomes necessary for us to be able to send emails anonymously. Whether for whistle blowing or pranks or social engineering or whatever, it just is necessary for us to do that.

Welcome back, friends! Many times, businesses, friends, and family will lock their zip files with a password to keep their files secure. It is reasonable, and understandable. Well, thanks to hackers, there are many ways to get past this wall of security.

If you read my last tutorial on using SEToolkit, you probably know that SEToolkit is an effective way to make malicious actions look legitimate. But, that was only the beginning... the truth is, Metasploit and SEToolkit belong together, and help each other very well.

I have a lot of favorite kitchen tools. My seven-inch Global chef's knife is my baby. My pasta maker is my dance partner on any given Friday night. My girlfriend's stand mixer is my favorite toy in the apartment.

There may be no kitchen appliance as controversial as the garlic press. Professional kitchens and many avid cooks despise it, while others staunchly defend it.

Hi everyone! In the previous part of this series, I introduced one way to hijack a program's execution flaw, though I only showed you how to crash the program and left you with a little mystery to solve. Today we are giving the solution of that and then introducing shellcode usage and remote command execution.

Hi everyone! Last time we finished analyzing the assembly representation of our vulnerable piece of code (have I ever told you it is vulnerable?). This time we are going to introduce some fundaments about exploitation by demonstrating how to crash a program's execution. If that sounds lame, next time we will see how this crash can in fact be useful to control the program's execution, achieving remote code execution!

Hi everyone! Last time we explained what roles Ebp and Esp registers have. We first introduced function's stack frame building, return address and calling conventions, but left some of the concepts floating without a full stop.








































