When Google introduced the Pixel 3 on October 9th, one of new additions they briefly mentioned was the Titan M security chip. While they did talk about how it will improve overall security, they didn't expand on the number of changes it brings to the Pixel 3's security. Well, they finally shared more, and it's a pretty big deal.

Apple often cites its tight integration of hardware and software for its success. Startup Illumix is looking to do the same thing for AR gaming by building an AR platform for its apps.

They're finally here. Apple announced three new iPhone models at their "Gather Round" event in Cupertino, and they're all absolutely gorgeous phones. With bezel-less screens and polished titanium edges, the iPhone XS, XS Max, and XR are truly marvels of engineering — but perhaps the most impressive design feat Apple pulled off is the fact that two of these models are rated IP68 under the IEC standard 60529.

With the rise of website encryption (TLS), sniffing passwords from network activity has become difficult. However, it's still possible to quietly exfiltrate a target's network traffic in real time to extract passwords and sensitive information. Pertaining to macOS, there are two methods for retrieving traffic from a backdoored Mac.

The microphone in a Windows computer is accessible to most applications running on the device at all times and completely without security limitations. Information gathered from recorded audio conversations taking place in the surrounding area of a compromised computer can be used for social engineering, blackmail, or any number of other reasons.

The next frontier for AR hardware is the consumer headset, and tech companies of varying size and tenure are working hard to strike the right mix between comfort, cool factor, and cost. How these companies handle the hype and flow of information vary wildly.

When you run an augmented reality company worth billions of dollars, backed by some of the biggest names in tech, and you haven't even released a product yet, even late night tweetstorms rank as worthy of dissection. Such is the case with Rony Abovitz, CEO of Magic Leap, who decided to spend a little time on Twitter on Wednesday to outline his vision of the future of immersive computing.

For about a million Americans each year, a joint replacement brings relief from pain and restored mobility. But, 5–10% of those people have to endure another surgery within seven years, and most of those are due to an infection in their new joint. If doctors could treat infections more effectively, patients could avoid a second surgery, more pain, and another rehabilitation.

Cancer cells do a pretty good job of flying under the radar of our immune system. They don't raise the alarm bells signaling they are a foreign invader the way viruses do. That might be something scientists can change, though.

The launch of the Audi A8 marks the world's first Level 3 car on offer in retail channels, except there is one catch: it can only take full control of driving at speeds of 37.3 mph or less.

There are a lot of exciting improvements in store for Siri in iOS 11. Apple showed off some of the highlights at WWDC, but there are five changes in particular that you don't want to miss.

The leading platforms enabling augmented reality technology lead our headlines in Market Reality this week.

This week's Market Reality covers a variety of business news from acquisitions and partnerships to competitive and technology assessments to quarterly financial results.

We fight cancer in a variety of ways, but no matter whether drugs, biologics, or our immune cells are part of the battle, they can do a better job fighting back cancer if we can help them find the tumors.

Water makes up about 60% of your body weight. Whether you like it plain, flavored, bubbly, or in beverages or food, we all need water daily to avoid dehydration and stay healthy. For communities in need of clean drinking water, new research using bacteria may offer a simplified, lower-cost method for boosting potable water supplies.

The evolution of our infection-fighting systems may have something to teach modern scientists. That's what a group from the University of Granada in Spain found when they studied a protein that's been around for over four billion years. Their work, by senior author José Sánchez-Ruiz and colleagues in the Department of Physical Chemistry, was published in the journal Cell Reports.

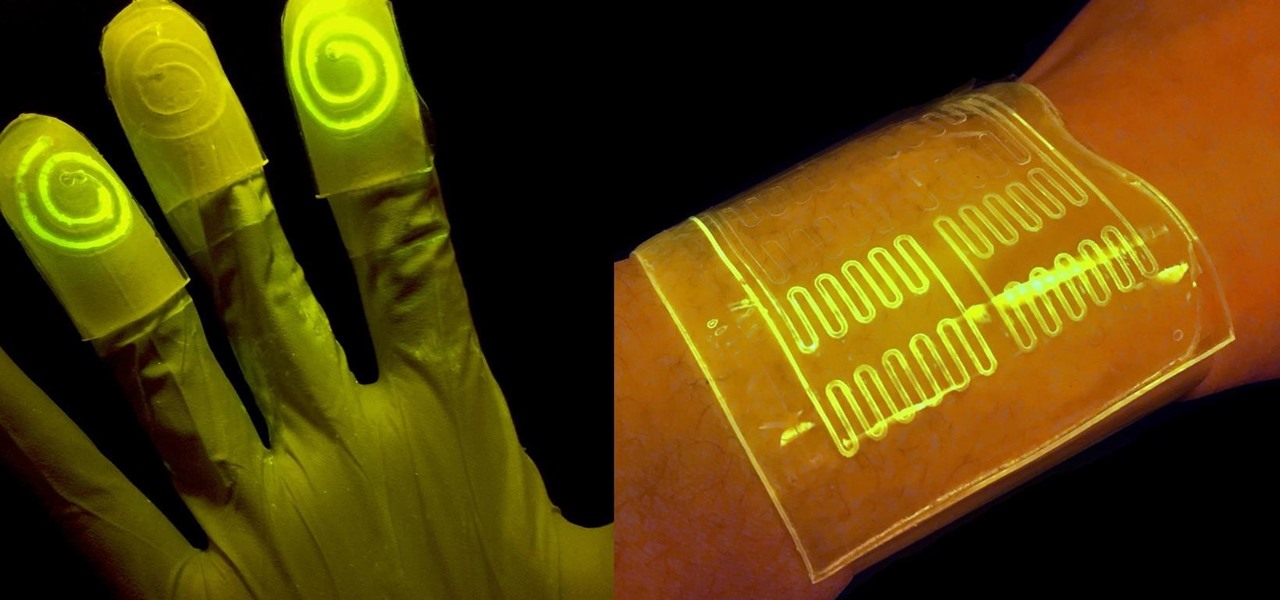
While at work, you notice your gloves changing color, and you know immediately that you've come in contact with dangerous chemicals. Bandages on a patient signal the presence of unseen, drug-resistant microbes. These are ideas that might have once seemed futuristic but are becoming a reality as researchers move forward with technology to use living bacteria in cloth to detect pathogens, pollutants, and particulates that endanger our lives.

Maybe you thought sitting behind a Mac gives you special protection when it comes to getting hacked. Thanks to a a new report from Check Point, you can kiss that theory goodbye. The cyber security company just uncovered the latest strain of malware — OSX/Dok — infecting all versions of macOS (previously Mac OS X).

Sophisticated hackers have been exploiting vulnerabilities in Chrome and Firefox to trick even the most careful internet users into logging into fake domains for sites like Apple, Google, and Amazon.

General Motors Co. (GM) is set to expand their fleet of driverless cars in San Francisco, Detroit, and Scottsdale, according to documents filed by the company.

A virtual design and construction services firm has built an augmented reality application that uses the Microsoft HoloLens to improve the efficiency of quality control on construction sites.

"Necessity, not novelty," is a phrase I use often when it comes to HoloLens development. It would be fair to call it my mantra, or mission statement, as I prototype and explore software creation on this new frontier of mixed reality.

Hello again, readers! In our previous crypter tutorial, we looked at how we could obfuscate our malware (or any program) by using a simple one-byte XOR key. In this quick tutorial, we will be looking at how a simple little tweak can create a better means of obfuscation. Let's get right into it!

Welcome to an introduction on writing basic malware, an optional sub-series in which I expose you to malware and its technologies. This is written for those who wish to seek a beginning in malware analysis or enlightenment on the subject. We will be justifying the writing and covering types of malware.

Welcome back to another tutorial on functions. Last time, we looked inside memory to see what functions looked like in the flesh and all that Assembly was pretty nasty. At least you have some exposure to it. This time, we will be examining how functions work with the stack.

SET is great when you have a short space of time at hand, however sometimes you want to know whats actually going on under the hood or have found a site you can't clone with SET.

A while back, I wrote review of my favorite hacking movies of all time. Two of my key criteria were; (1) how realistic was the hacking, and (2) are the hackers portrayed as the "good guys." This past winter, a new hacker movie was released, appropriately named Blackhat starring Chris Hemsworth (from Thor fame) as a blackhat hacker who is released from prison to stop a notorious and destructive hacker that only he can stop. Although the movie did very poorly at the box office, I thought it was...

So, we all probably know that when you run a trojan made by Metasploit, nothing will appear to happen. This is a sign for me to immediately check my Task Manager, but for an unsuspecting victim, it will just seem like a broken file. It is likely that they will delete this "broken file" once they see that it "doesn't work." In order to prevent this, we need to disguise the trojan.

Hi everyone! In the previous part of this series we introduced remote code arbitrary execution via buffer overflows using all of our past experiences.

Kitchen tools are a personal thing. One hard lesson for me to learn is that just because something is popular doesn't mean that it's right for me. Take the slow cooker, for instance. Many rave about it, but I never cottoned to the thing. However, the more research I do, the more I think the pressure cooker might be a game changer for my cooking style.

I'll admit it: I've spent many eight-hour workdays stuck at my desk, staring at my computer as my breaks slip past unnoticed. I frequently tell myself I'll take one in a few more minutes—but somehow, the entire day will pass and I won't have taken a single break.

What if someone asks you to do a Nmap scan but you left your pc at home? What if a golden opportunity shows during a pentest but you were walking around the building, taking a break?

Journals are a great source of hilarity and embarrassment, detailing everything from your elementary school crushes to those super awkward middle school dances. While rereading your old hand-scrawled entries might make you cringe, that old journaling habit could benefit you as an adult.

Welcome back, my greenhorn hackers! After the disaster that was Windows Vista and the limited and reluctant adoption of Windows 8 and 8.1, Windows 7 has become the de facto standard operating system on the desktop/client.

Welcome back, my fledgling hackers! In one of my recent articles, I showed you how to install BackTrack as a dual boot system on a Windows computer. In this tutorial, I will walk you through BackTrack, giving you a tour of the most salient features for the hacker-to-be.

I recently had my iPhone stolen at public park and did everything I could to locate it, but with Find My iPhone disabled (I know, what an idiot) and no exact address to give to the police, I had about a .00000001 percent chance of getting it back.

Welcome back , my fledgling hackers! Lately, I've been focusing more on client-side hacks. While web servers, database servers, and file servers have garnered increased protection, the client-side remains extremely vulnerable, and there is much to teach. This time, we'll look at inserting a listener (rootkit) inside a PDF file, exploiting a vulnerability in Adobe's Reader.

Apple doesn't include its Calculator app on the iPad and never did. One almost appeared over 12 years ago but was nothing more than a blown-up version of the iPhone app. Since then, the company still hasn't made an iPad-optimized calculator, and there is no shortage of third-party alternatives to fill the gap. It may happen one day, but for now, these are the best calculator apps for your iPad.

The year 2020 was a pivotal span of time during which the word "virtual" took on a brand new meaning. Instead of referring to VR or augmented reality, the term was hijacked to describe meeting across long distances through a variety of software tools, most often through video.