You can do a lot with water guns. Have trouble waking up? Make a water gun alarm clock that (almost) no one could sleep through. Prefer real ammo? Turn your water gun into an airsoft BB gun. And if you don't have one, you can even make your own.

Whether you want to use it to keep your guests safe or just to see who's the most drunk, it's always fun to have your own breathalyzer at a party. We've seen DIY breathalyzers before, like this one by Craig Smith, but how about an Arduino breathalyzer?

Most of us have given up our big, bulky stereos in favor of smaller, sleeker models, but how many of us actually get rid of the old ones? If you don't like the idea of throwing out or giving away electronics you spent good money on, you can always upgrade them instead!

If you've ever been on your way to a party and felt that your outfit just wasn't flashy enough, engineering student 'Rambo' has got just the thing for you. His homemade LED suit lights up and dances to the beat of the music, and can even be controlled via Bluetooth.

For his thesis at Design Academy Eindhoven, artist/designer Tuomas Markunpoika Tolvanen created this incredible chair using tubular steel cut into thin rings. How did he get them to stay that way? He burned them. His project is called Engineering Temporality, and the inspiration came from his grandmother whose Alzheimer's disease is deteriorating her health and memories. Once he cut the rings, he laid them over an existing chair, only partially covering it. The fire acted as a varnish, creati...

Helping to prove that science is way awesome, an 18-year old electrical engineering student has successfully made a light bulb float. His name is Chris Rieger, and he's been working on his "LevLight" project for about six months now, with pretty amazing results. This feat of ingenuity was accomplished by using magnetic levitation, although that over-simplification masks how considerably difficult this undertaking was.

What appears to be an ordinary MP4 may have been designed by an attacker to compromise your Linux Mint operating system. Opening the file will indeed play the intended video, but it will also silently create a connection to the attacker's system.

In the first part of this series, we took a factual and technical look at the history of the Internet. I explained how all of these wires and servers got here in the first place. Obviously, a firm did not just create and build the Internet around 1995! Now that we know how the Internet came to be, we can get into the really fun stuff—what the Internet looks like now! Well, that's not quite the network design I was talking about, but it does show what the Internet looked like back in 2007 befo...

As I've mentioned in recent days, it was refreshing to discover that Microsoft's HoloLens 2 stage production was every bit as accurate as presented (check out my hands-on test of the device for more on that).

Mystery is a tricky thing. Used correctly, it can give onlookers the impression that wondrous and perhaps valuable things are afoot. However, once the veil of suspension of disbelief is removed in any significant way, that same mystery can quickly turn into not just skepticism, but outright anger at what may have seemed like an attempt to dupe trusting onlookers.

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.

Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.

While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one. This forces the victim to connect to the fake network and supply the Wi-Fi password to regain internet access.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

If you read my article on the OSI model, you got a good overview on communications from that model's perspective, but how does that relate to TCP/IP? We're going to take it a step further, getting into the idea behind the two address concept. How does an IP address and a MAC address work together? If you want to hijack sessions and all sorts of lulz like that, you need to understand these concepts. Let's get into it, mates!

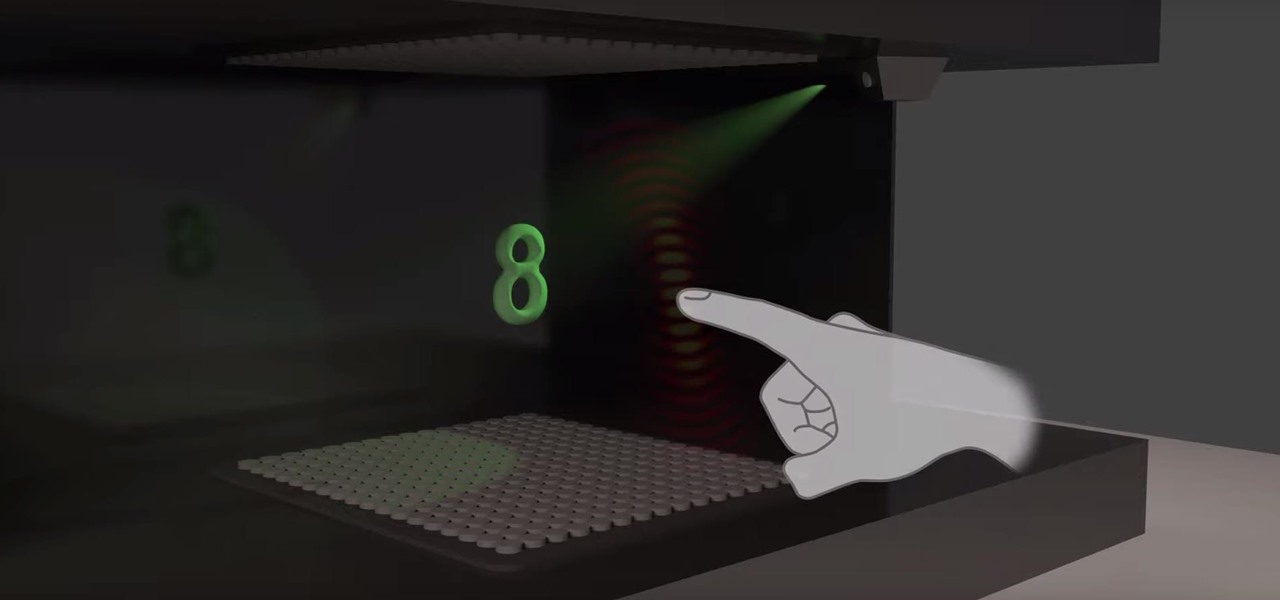
Most augmented reality experiences are purely visual, with spatial audio gaining in popularity to make visual experiences more realistic. However, leveraging the sense of touch may be the next frontier for AR experiences.

Does your iPhone always ring off the hook, with each call nothing more than a robocall, spammer, or scammer? It's not just you. Auto-dialing systems and phone scams are a growing issue that anyone with a phone number is likely experiencing throughout the United States. But Apple has added a super simple way to combat these calls in iOS 13, a feature we recommend everyone turn on.

We are in the midst of a mini-boom for communications tools designed for augmented reality headsets, with the introduction of Avatar Chat and Mimesys for Magic Leap One and Spatial for the HoloLens within the last few months.

Designing and manufacturing waveguides for smartglasses is a complex process, but DigiLens wants us to know that they have a software solution that partially solves that problem.

The Federal Communications Commission (FCC) has cleared a path for Google to move forward with hand-tracking technology that could pose a major threat to Leap Motion.

After joining Google and Huawei in underwriting the UW Reality Lab at the University of Washington in January, it appears Facebook is already seeing a return on its donation.

Augmented reality productivity software maker Upskill has expanded the reach of its Skylight platform with support for Microsoft HoloLens.

The latest business move by Magic Leap could result in a significant boost to its spatial computing platform's performance and headset design.

One could argue that, at least for the moment, software development is more important to the augmented reality experience than hardware. Since a viable augmented reality headset has yet to emerge for the broader, mainstream consumer market, currently, the same devices that make texting and selfies possible are leading the charge to enable easy-to-use AR experiences.

Leading augmented reality headset makers Microsoft and Magic Leap are among the companies now vying for a military contract for battlefield heads-up displays.

Facing mixed reviews for the Magic Leap One, Magic Leap has already returned to the lab to improve on the device's successor.

Online shopping giant Shopify literally cannot wait for ARKit 2.0 to arrive via iOS 12 this fall to implement its latest augmented reality feature.

With developers chomping at the bit to play with ARKit 2.0, Unity has updated its ARKit plugin to enable access to the new augmented reality superpowers of the toolkit.

Augmented reality headset maker Meta Company unveiled Meta Viewer, its first software application, during its keynote at the Augmented World Expo in Santa Clara on Wednesday.

A newly-filed patent application from Disney Enterprises, Inc. teases more augmented reality lightsaber duels, either for at-home gaming or for the media behemoth's forthcoming Star Wars theme park.

Hello, budding augmented reality developers! My name is Ambuj, and I'll be introducing all of you Next Reality readers to the world ARKit, as I'm developing an ARKit 101 series on using ARKit to create augmented reality apps for iPad and iPhone. My background is in software engineering, and I've been working on iOS apps for the past three years.

On Tuesday, at Google's I/O developer conference, the company announced a huge update to its ARCore augmented reality toolkit that matches the latest features of ARKit, and surpasses Apple's AR platform via support for shared experiences.

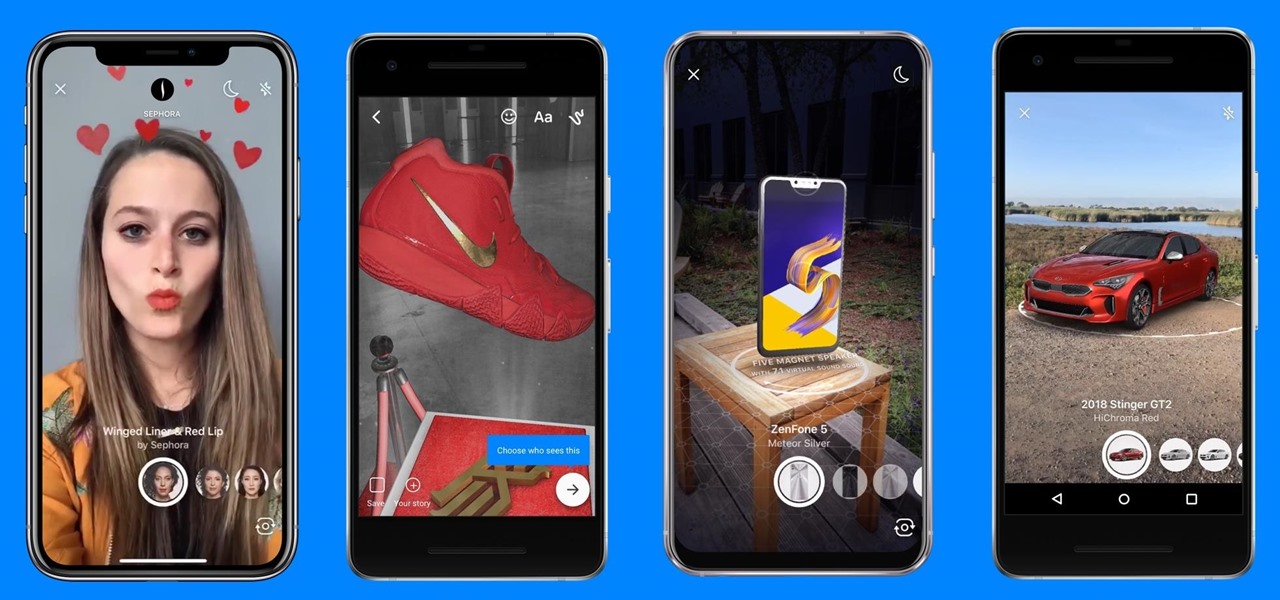
On Tuesday, on the one-year anniversary of the announcement of its AR Camera platform, Facebook founder and CEO Mark Zuckerburg revealed at the company's F8 developers conference that the platform will be extended to the company's Instagram and Messenger apps.

Snapchat has released three new augmented reality Lenses that boast uber-accurate face tracking courtesy of the TrueDepth camera on the iPhone X and ARKit.

This week, two companies preparing the most anticipated augmented reality devices for consumers were the subject of reports regarding strategic moves to put them in better positions to move those products forward.

Accused of violating whistleblower and age discrimination laws by its security director, Magic Leap has taken an internal situation to the US District Court to clear its name of the allegations.

With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer.

While the consensus among some in the augmented reality community is that the Microsoft HoloLens is the best device available at present, it also remains the most cost-prohibitive option, with the development edition costing $3,000.

After Vuzix's scorching hot week at CES, the future of AR is so bright, we have to wear (smart) shades. Luckily, Vuzix is making it easier for consumers to grab a pair.

In the wake of reports of slow iPhone X sales and a possible early end to its shelf life, Apple CEO Tim Cook is on a public goodwill tour of sorts, espousing the virtues of Apple AR.