After years of tantalizing drone video, and then brief glimpses from special guests sharing photos on social media, the Apple Park Visitor Center finally opened to the public on Friday, Nov. 17.

ARKit and ARCore generate excitement among various segments of the tech industry for spurring adoption of augmented reality with consumers via mobile devices.

Now that iOS 11 is officially rolling out to millions of iPhones, many users are upset with the fact that Apple has removed the 3D Touch multitasking gesture that we enjoyed in older iOS versions. Though not as fluid as this gesture, there is still a hidden way to quickly get into the app switcher without having to double-click the home button.

Andre was enjoying the carefree life of a 12-year-old with his friends, riding his bike and playing sports, like all kids that age. Schoolwork wasn't hard for him, and his grades showed that.

Two companies behind a number of augmented reality devices have joined forces to develop a 3D depth-sensing camera system that will facilitate computer vision capabilities for augmented/virtual reality experiences and more.

GE Aviation and their software partner Upskill are seeing success by giving their mechanics smart tools and smart glasses, the latter in the form of Google Glass.

Intel's driverless division will be managed by Israel-based Mobileye, as the chip giant emerges from relative obscurity in the driverless space to become a major supplier after completing its $15.3-billion purchase of Mobileye this week.

Cruise Automation, General Motors' (GM) driverless car arm, has hired two hackers who were once seen by many as a safety threat to help find vulnerabilities in its self-drive car network.

Mixed reality developer Arvizio has updated its MR Studio software suite to integrate processing of 3D light detection and ranging (LiDAR) point clouds.

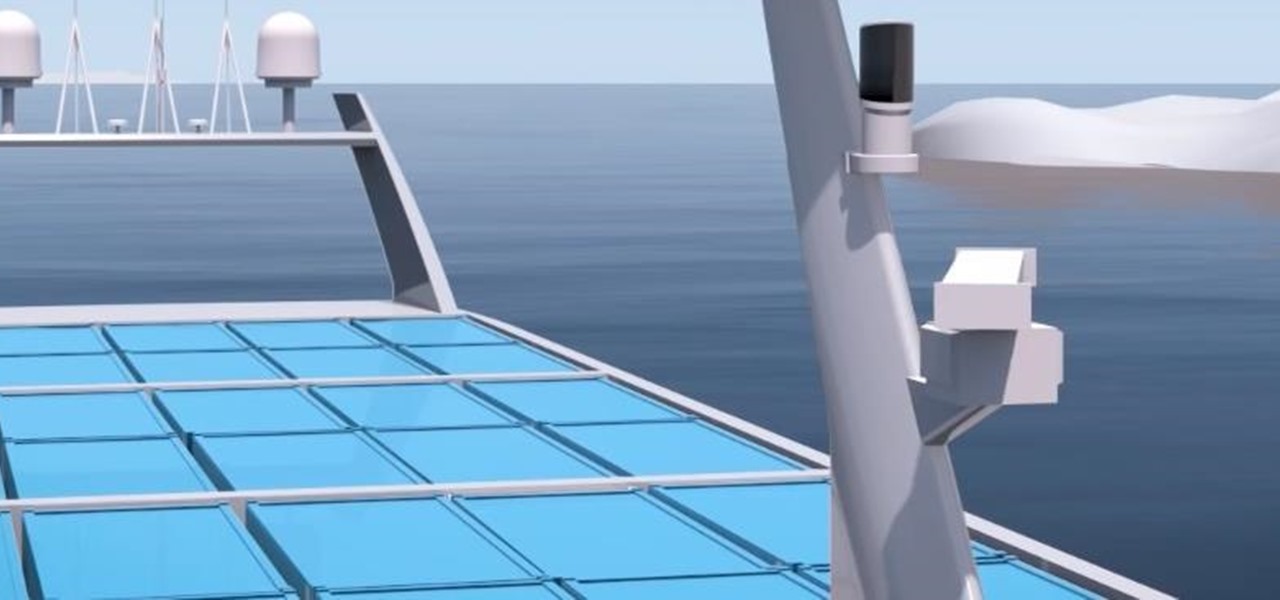
A Norwegian carrier's launch of a pilotless container ship next year could lead the way to a new era in sea transportation and shipping if successful.

Research group OpenAI, a research institute co-founded by Tesla CEO Elon Musk, says it is possible to trick driverless cars' neural networks into mistaking images for something else.

Drive.ai (a startup founded by Stanford University graduates), Waymo, General Motors, and serial entrepreneur and author Vivek Wadhwa are featured in today's top news.

General Motors (GM) has begun production of 130 Chevrolet Bolt EV driverless test vehicles at its Orion Township, Mich. plant as it expands its fleet to total 180 models deployed in San Francisco; Scottsdale, Arizona; and Detroit.

Uber's legal team may have finally sold their engineering golden boy down the river as their war with Waymo continues. Anthony Levandowski isn't your average sacrificial lamb either — given the alleged stealing and all that — but Uber seems set on distancing themselves from this whole fiasco as fast as they can.

Just like in the Spy Kids 3D movie, US soldiers may soon upgrade their mission planning from 2D to 3D. Welcome to the wonderful world of augmented reality, US Army.

Google Maps now allows users to share their location in real time and update their friends and family on their location and estimated time of arrival when making a trip.

If you're in the Windows Holographic community of developers, make sure to mark your calendar and set your alarms for February 8, 2017 because it's Windows Developer Day.

Merge VR, a company mostly known for its virtual reality experiences, is moving into and creating an augmented reality experience that combines an iPhone or Android smartphone, a set of goggles to put your phone in, and a box about the size of a Rubik's Cube which looks more akin to the Lament Configuration seen in the Hellraiser film series. When used in concert with the smartphone and goggles, the toy cube, called Holo Cube, becomes one of many AR experiences.

The Note7 fireworks bonanza was unprecedented in scope. A recent report suggests that Samsung could lose upwards of $20 billion in lost profit due to this fiasco.

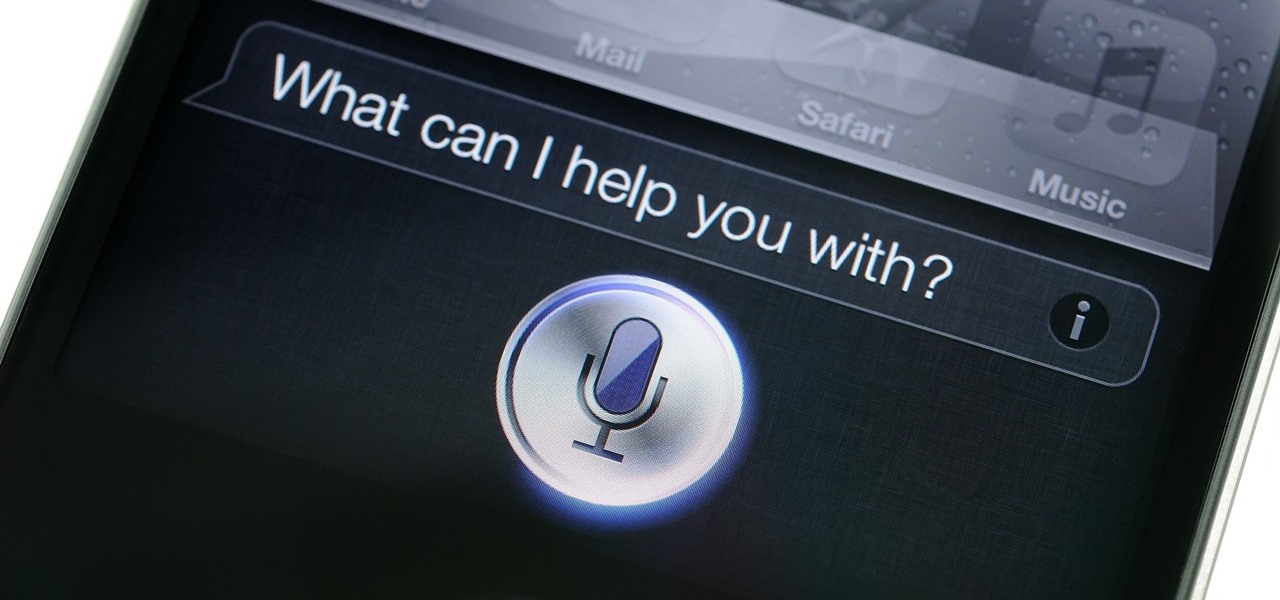
If you follow tech, you're probably familiar with Siri, Apple's personal voice assistant, which has been integrated heavily into iOS ever since iOS 5. But you might not have known that Siri is capable of performing some tasks when the iPhone is in a locked state. The default state of iOS is to allow access to Siri from the lock screen, most likely for the convenience of hands-free access to the phone.

At their annual I/O event, Google introduced their latest app to the public: Allo. The messaging app is the company's latest and most powerful entry into the expanding world of similar apps, with one twist—the inclusion of artificial intelligence.

In this article I will show you how to obtain victim's credentials without cracking any hashes. There are a couple of ways to perform this task (for example dumping the SAM file and cracking the NTLM hashes), but here I will explain how to do it using PowerShell and a bit of social engineering. We are going to create a fake login popup.

Hello, my fellow hackers. My name is cl0ck. I am a senior majoring in Computer Engineering with an emphasis is Security. I have been lurking the site for a while now reading and learning from the great minds that reside here. I, too, have some knowledge that I would like to share with all of you. This post actually comes from a personal problem I faced and had to find a solution for. Without further ado, here it is:

I found this article a while back and I found it underneath a bunch of junk. Anyway, it's a article on 9 notorious hacker including Walter O'Brien (You know the T.V. show Scorpion? Well that's him). Not to mention the weird names:

Though you can use the Social Engineering Toolkit to clone websites, this way is much more customisable.

With root access, you're granted greater control over your device, allowing you to do things that your Android system wouldn't allow otherwise. Things like installing Xposed mods are made possible with root, but other advantages address performance and security, like stopping your Android logging, which is exactly what we'll be going over today.

There are countless lock screens you can apply to your Android device, but very few offer more than just quick access to apps or advanced security functionality. Since you probably unlock your device a gazillion times every day, why not use this to your advantage and let it teach you something new?

I don't know many meat eaters who don't appreciate a good burger, but unless you eat it plain, it usually gets pretty messy. Toppings falling off and sauce running down your arms seems like it's all just part of the process.

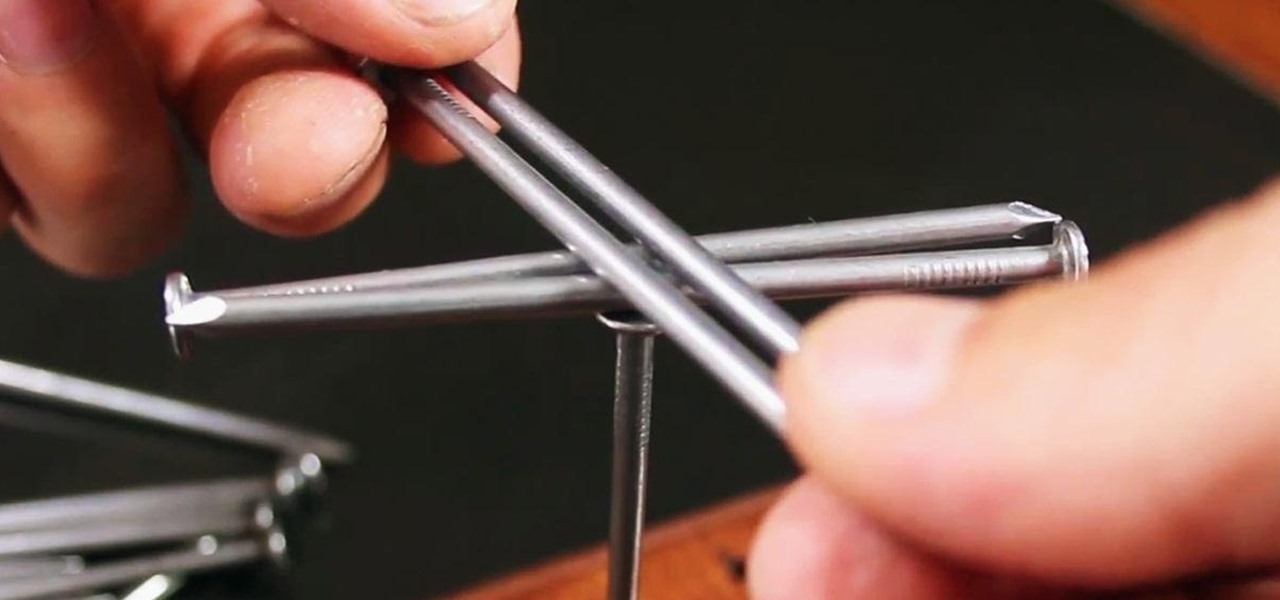
This little brain game is all about engineering a lower center of gravity. The idea has been around forever, but most people still don't know how to do it. Trying to stack nails above the balance point will raise the CG and make the structure unstable. Here's how you can lower the CG to make a very stable structure and impress your friends.

Snapchat may trail Facebook and Instagram in terms of daily active users, but a new partnership with Samsung may get those innovative AR Lenses onto the mobile devices of a lot more users.

Your smartphone stays with you everywhere you go, so it's only a matter of time before you spill coffee all over it or drop it on the ground. For some of you, it has already happened, perhaps even multiple times. That's why we thought it was important to find out which flagship phones are the most life-proof.

While Snapchat is no stranger to location-based AR scavenger hunts, the app's new world-facing game adds some environmental understanding to the mix.

One Instagram creator's augmented reality homage to Disney's deep bench of animated characters has earned him fifteen minutes of fame.

While Apple, Facebook, and Snapchat are still working on their first-generation AR wearables, startup North is already preparing to bring its second-generation smartglasses to the world in 2020.

We have seen Kickstarter-launched wearables before, but this one is particularly unique and may even have you blinking a bit in wonder when you see how it functions.

Despite hints hidden in internal iOS 13 code, Apple did not unveil its long-rumored smartglasses at its annual iPhone launch event on Tuesday.

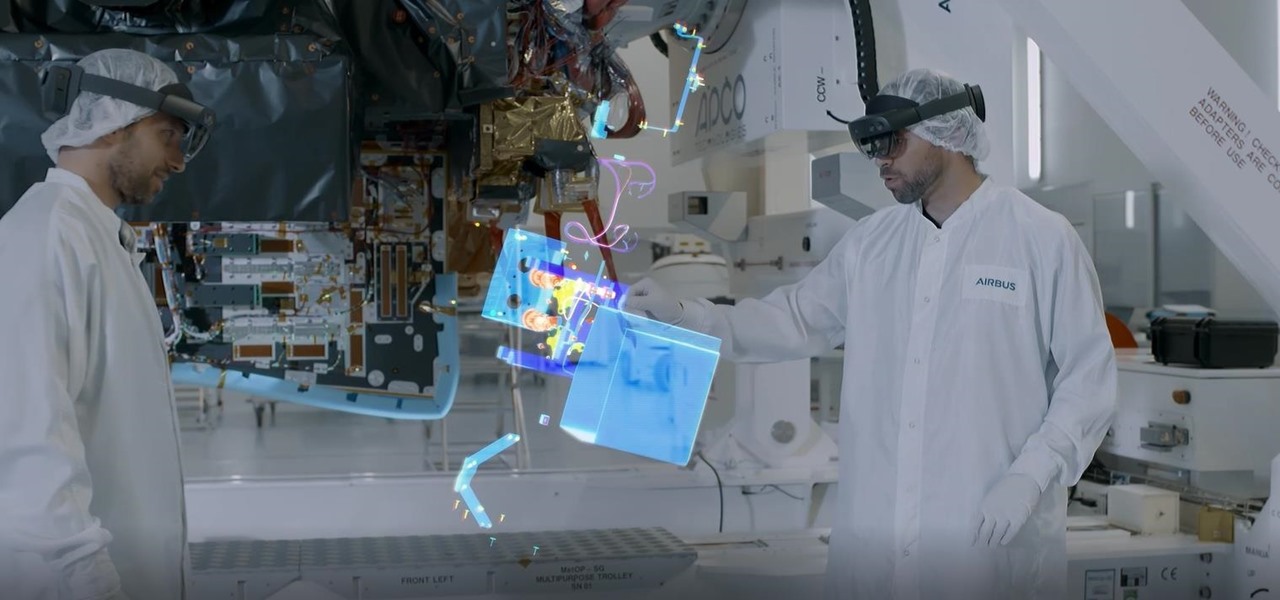
Aircraft manufacturer Airbus is so impressed with the boost in productivity it has gained from Microsoft's HoloLens, the company will begin offering augmented reality software to its customers.

Like clockwork, Apple has unveiled the latest additions to its ARKit tookit at the annual Worldwide Developers Conference, where ARKit first said hello to the world in 2017, as well as some new tools that take a direct shot at Unity, Unreal Engine, and others.

After announcing at Google I/O 2019 that augmented reality content would come to Search, Google revealed how it would make that happen with the latest round of updates to ARCore.

The long guarded veil of mystery surrounding Magic Leap for years was finally lifted last year when the company revealed its Magic Leap One device.