
News: Waymo Accuses Uber of Withholding Secret LiDAR Device
The drama continues! In the latest installment of the feud that has rocked the driverless vehicle industry, Waymo is now accusing Uber of withholding a secret LiDAR device.


The drama continues! In the latest installment of the feud that has rocked the driverless vehicle industry, Waymo is now accusing Uber of withholding a secret LiDAR device.

Asobo Studios, one of the first companies to partner with Microsoft on HoloLens development, is applying their expertise towards building applications for various business verticals through their internal HoloForge Interactive team.

Udacity, the online education startup that set out to train a school of self-driving car engineers, is now spinning off into its own autonomous tech company called Voyage.

Upskill, an enterprise software developer for industrial augmented reality applications, recently received an influx of funding and a major vote of confidence from two of their top customers.

As it turns out, your Android apps are pairing together to share your data without asking for your permission first. Researchers from Virginia Tech developed a tool called DIALDroid to monitor exchanges of data between Android apps over the last three years, and what they've found is quite alarming.

Uber's driverless cabs began picking people up in Arizona in February, after its attempt at a pilot test in San Francisco. Now, one of these cars has been in an accident, and that's just the tip of the iceberg.

A development team in Silicon Valley is nearing early access release of a new hardware-independent augmented reality platform called Phantom AR.

Robots are always really cool, if you ask me. Sometimes they're made out of Legos, and that's even cooler.
Android device manufacturers may see the new Pixel "Phone By Google" devices as just another competitor, one that likely won't upset their entry-level margins. But that would be a mistake. Pixel is Google's call to action. With Google now offering as near to perfect an Android experience as we've had so far, OEMs that want to keep selling smartphones in a world flooded with them will need to start working for the privilege.

This tutorial follows the same idea as my original tutorial for windows, but I've redone it to work with Mac OS X. Here's how to get a meterpreter session from your victim opening a malicious word document:

Hello again, and welcome back to another tutorial on functions, this time, covering recursion. What Is Recursion?

First of all, Merry Christmas and Happy New Year to all Null-Byters that learn and teach in this wonderful site. In this article we will explore the basics of the meterpreter's IRB (Interactive Ruby Shell).

Do you ever thought that you can't control an Internet disconnected system? I saw a funny video in Chema Alonso's youtube channel (A well-known hacker of my country and creator of Fingerprinting Organizations with Collected Archives among other security tools), and decided to post something similar.

Greetings dear null byters, today we start a new series, we will start to attack users using social networking that are popular such as Facebook, Skype, and much more, and in part 1 of the series will engage users of Skype.


In part one of this tutorial we found out that your English teacher is a paedophile, by using a Man in the Middle attack to intercept his internet traffic.
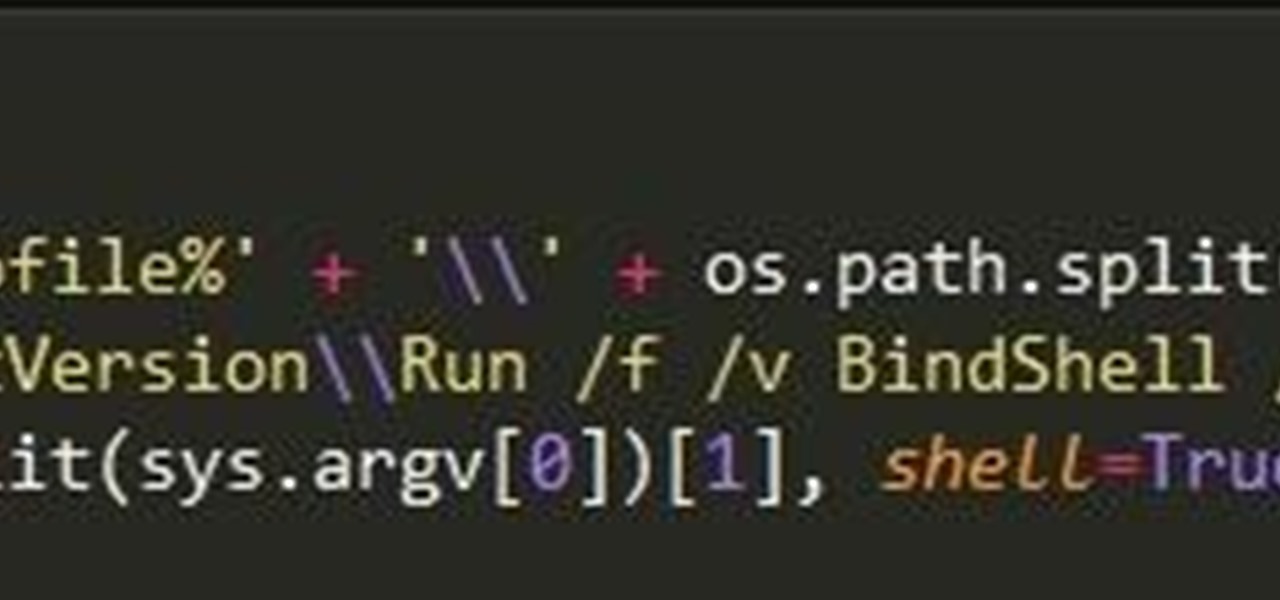
Hi guys, I'm gonna keep this short because I got assignments and a lot of notes to study and also other how-tos and forums to reads. lol...Since I'm keeping this short...no story time just scenario. And I want to thank n3stor for giving me the idea to post this.

Hello fellow grey hat hackers, as hackers it becomes necessary for us to be able to send emails anonymously. Whether for whistle blowing or pranks or social engineering or whatever, it just is necessary for us to do that.

If you read my last tutorial on using SEToolkit, you probably know that SEToolkit is an effective way to make malicious actions look legitimate. But, that was only the beginning... the truth is, Metasploit and SEToolkit belong together, and help each other very well.

Hi everyone! In the previous part of this series, I introduced one way to hijack a program's execution flaw, though I only showed you how to crash the program and left you with a little mystery to solve. Today we are giving the solution of that and then introducing shellcode usage and remote command execution.

Hi everyone! Last time we finished analyzing the assembly representation of our vulnerable piece of code (have I ever told you it is vulnerable?). This time we are going to introduce some fundaments about exploitation by demonstrating how to crash a program's execution. If that sounds lame, next time we will see how this crash can in fact be useful to control the program's execution, achieving remote code execution!

Hi everyone! Last time we explained what roles Ebp and Esp registers have. We first introduced function's stack frame building, return address and calling conventions, but left some of the concepts floating without a full stop.

Hi everyone! After messing around a little bit with IDA and Hopper disassemblers and briefly introducing you to memory, registers and Assembly, we are going to understand what happens when a process is running, which variables join the play and especially what happens when a function is called and why is this procedure-logic so interesting and useful along with the concept of stack.

Inspiration for tutorial: Foxtrot's "How to Trap a Tracker"

Although this century is still young, with little fanfare we may have just witnessed the "Hack of the Century." AV software developer Kaspersky of Russia recently announced that they found that some hackers have stolen over $1 billion from banks around the world!

Like many others, I like a good cocktail every now and then, and I've always been impressed when my cocktail enthusiast friends would come up with a new drink or even just remember how to concoct a Clover Club (FYI, it's made with gin, raspberry syrup, lemon, and egg white). There's a secret bartenders and craft cocktail aficionados know, though: It's all about math, the simplest and most intoxicating math. Pythagoras would be so proud.

You've had your Xbox 360 for a few years now and your game collection is pretty extensive. Maybe it's not that extensive, but it's still substantial. Now imagine that you live in Europe and you're moving to the United States. I don't know why—maybe your dad got a job offer. Don't ask me, ask your parents. They're the ones that are making you move. Anyways, as most Xbox users know, games are coded by region. Games that work in Europe might not work in the United States. Does this mean you shou...

Is "Last Resort" Steampunk? Well, no. I mean, how could it be?
It can seem as though there's a virtually endless number of essential programming languages to choose from these days. And complicating matters even further for aspiring or even established programmers, developers, and hackers is the fact that most languages are a bit esoteric and suited for only a certain number of relatively finite tasks.

Invented by Motorola engineer Bill Smith in 1986, Six Sigma's methodology defines a series of steps with specific value targets. These targets can be used, for example, to eliminate costs and process cycle time while increasing profits and customer satisfaction.

In years past, the Consumer Electronics Show (CES) mostly dabbled in the future as far as the long-term vision for augmented reality was concerned. This year, however, objects in the future are much closer than they appear.

While consumer-grade smartglasses are the holy grail for tech companies, smartglasses maker Vuzix knows where its bread is buttered, and that's in the enterprise segment.

Apple's ARKit has built a considerable lead in terms of features over Google's ARCore, but Google's latest update to ARCore adds a capability that makes the platform a bit more competitive with ARKit.

Investment in augmented reality remained robust in 2019. For the third consecutive year, we looked back on the biggest funding deals in the AR industry this week, and a familiar name came out on top.

There's a direct correlation between the proliferation of augmented reality apps and the demand for 3D content, and PTC just quantified that in dollars.
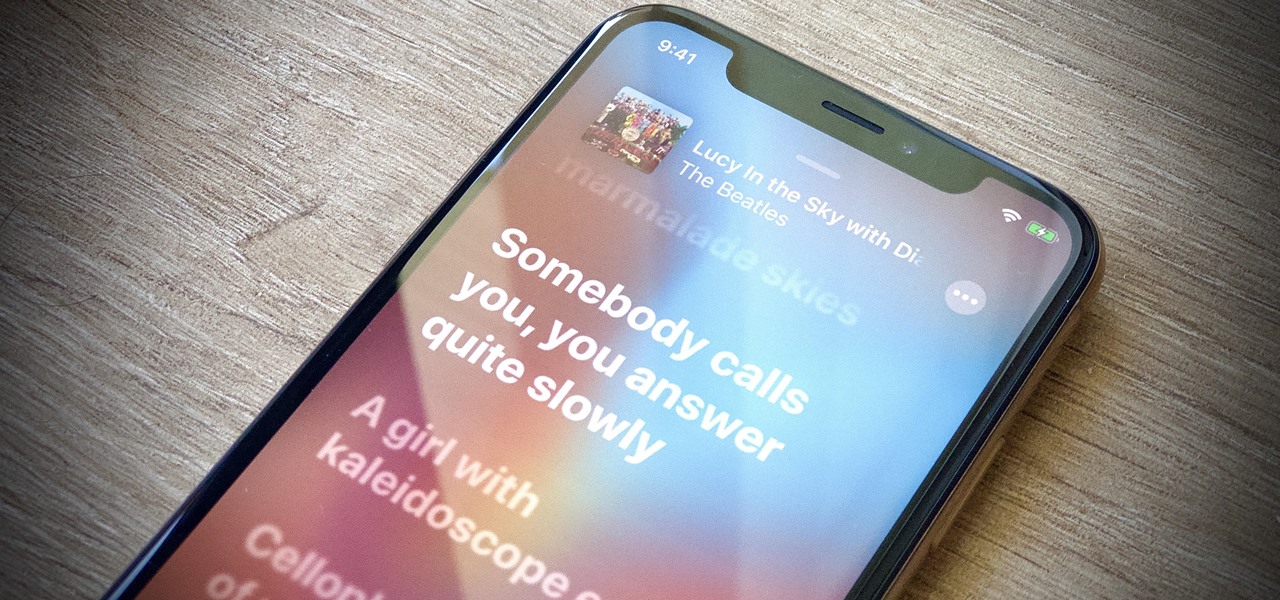
There are a lot of songs out there, so it's tough to remember all of the words to every song you like. If you're like me and have a less-than-perfect memory, visual aids will ensure your Apple Music jams aren't interrupted with incorrect or forgotten lyrics. That's why Apple's update with time-synced lyrics is so cool, essentially turning your iPhone into a portable karaoke machine.

Apple had its Worldwide Developers Conference on June 3, 2019, which showcased big software announcements for all of Apple's hardware, and anyone can watch the keynote as it happened.

Developers in the augmented reality industry got a lot of love this week.

Augmented reality startup Nreal was a hit at this month's CES event, with some even calling the device a worthy challenger to the Magic Leap One.

Augmented reality and computer vision company Blippar has a new lease on life, as previous investor Candy Ventures has completed a successful bid to acquire the assets of the beleaguered company.