A federal judge wants answers after an Uber engineer accused of data theft pleaded the Fifth in the ongoing Waymo versus Uber battle. This privilege would protect the accused, Anthony Levandowski, of self-incrimination and handing over specific documents demanded in a previous subpoena and forthcoming deposition.

So you want to create a meterpreter virus, but you keep getting caught by AV. How do you create one that will go undetected? In this tutorial, I'll teach you how to code your own simple virus that will download a powershell payload from an apache webserver and execute it - bypassing antivirus.

This how to is about making a fighting game and pretty much anyone can do this! We will also be using Game Maker to create it.

What if the code you are trying to reverse engineer is obfuscated or somehow corrupted? What if no way is left? Here comes what I like to call (wrongly and ironically) the "brute force of reverse engineering".

Video: . Iconici Tv MMA Host Naiya Marcelo caught up with with Bellator middleweight fighter Brian Rogers "The Professional Predator" at Factory X Muay Thai/MMA/BJJ Gym in Englewood CO.

Fireworks are synonymous with holidays like Fourth of July and New Year's, but rarely do you ever hear about fireworks or explosives going off during a Christmas celebration—until now.

Welcome back, my tenderfoot hackers! So many readers in the Null Byte community have been asking me questions about evading detection and hacking undetected that I decided to start a new series on digital forensics.

Use the Xara Web Designer 7 Premium Mould tool to mould, re-shape and change perspectives of objects. The Xara Web Designer Mould tool will allow you to create some very interesting effects to make your website stand-out and have depth. Even the thumbnail shown for this web design video tutorial was created with the envelope tool. If you have ever seen the software boxes shown on various those are usually created with an envelope tool to give the box its perspective.

In this Windows 8 Tutorial you will learn how to pin application to the task bar. If you work with certain programs very often it will be beneficial to pin those Windows 8 applications to your task bar in the desktop view. Once you pin an application to task bar in desktop view it will always be visible too you and with one click you will be able to launch application. Thank you for viewing our Windows 8 tutorials. If you need help with a certain area of Windows 8 and would like us to make a ...

In this video series, learn from expert mechanic Nathan McCullough as he teaches and demonstrates how to tune-up a car and do a complete vehicle overhaul. Learn how to check your transmission fluid, air filter, power steering fluid, clutch fluid, brake fluid, radiator and coolant hose, drive belt; how to change your spark plugs and your distributor cap; how to replace your windshield wipers and washer solvent; how to check for tire wear; how to change your oil and check for leaks.

Whenever a new Apple event invite arrives, the entire tech industry begins tearing the invite's graphics apart in a bid to decipher what the company may be planning on releasing in the coming weeks.

Designing and manufacturing waveguides for smartglasses is a complex process, but DigiLens wants us to know that they have a software solution that partially solves that problem.

Location-based gaming pioneer Niantic has been preparing its flavor of AR cloud, the Niantic Real World Platform, to bring more realistic and interactive augmented reality experiences to mobile apps. And now the company is looking for a few good developers to help execute its vision on the platform.

The latest business move by Magic Leap could result in a significant boost to its spatial computing platform's performance and headset design.

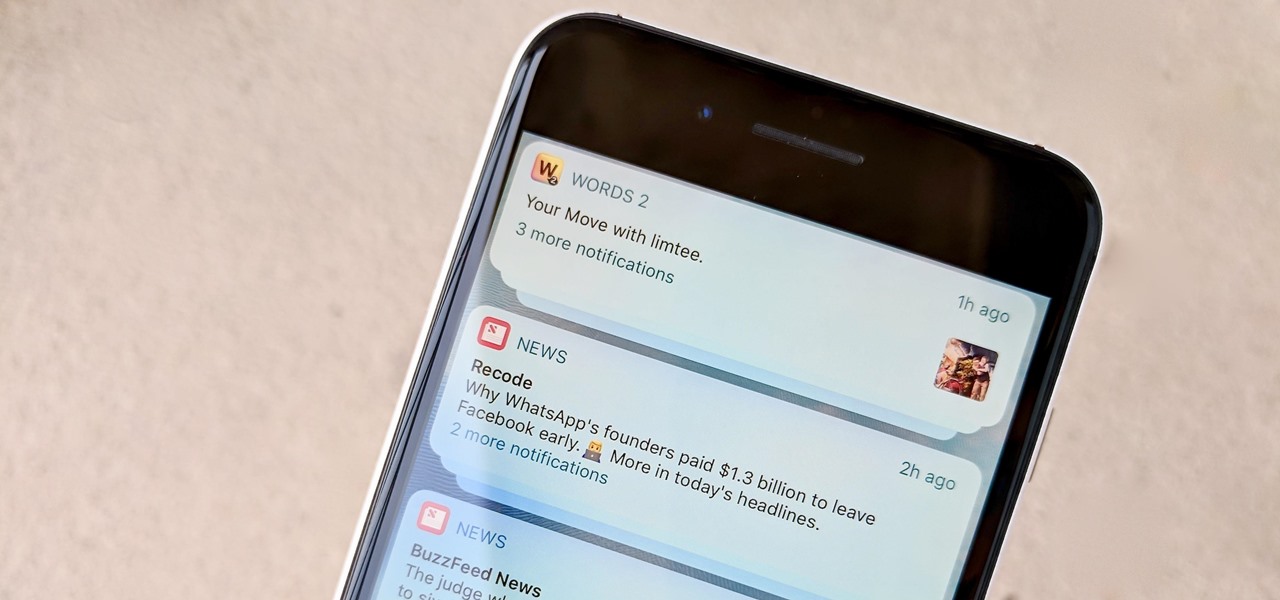
While iOS 11 was famous for its instability, performance issues weren't the only factor holding it back. The OS overhauled the notification system on iPhone, but not necessarily for the better. iOS 12, however, improves upon these changes, bringing critical features that make viewing and interacting with notifications on your iPhone on par with Android.

Locating and abusing files containing unsafe permissions is an easy and surefire way to elevate shell privileges on a backdoored macOS device. This time around, we'll be more aggressive and attempt to phish a user's login password by prompting a convincing popup message merely asking the target for their password.

Developers can now publish augmented reality experiences that are viewable through the experimental version of Chrome and ARCore.

The next big event Apple is holding is WWDC 2018, its Worldwide Developers Conference, is about to happen. If you want to see the first glimpse of iOS 12 for yourself, as well ARKit improvements, Apple Watch news, and maybe even some macOS announcements, here's how you can tune into the event right at home from your computer or mobile device.

While Magic Leap may have plans to eventually introduce sign language translation for smartglasses in the near future, students at New York University have demonstrated that such a feat is possible today with a smartphone and a prototype app.

Now that we have our payload hosted on our VPS, as well as Metasploit installed, we can begin developing the webpage which will trick our "John Smith" target into opening our malicious file. Once he has, we can take over his computer.

ARKit and ARCore generate excitement among various segments of the tech industry for spurring adoption of augmented reality with consumers via mobile devices.

Two companies behind a number of augmented reality devices have joined forces to develop a 3D depth-sensing camera system that will facilitate computer vision capabilities for augmented/virtual reality experiences and more.

Intel's driverless division will be managed by Israel-based Mobileye, as the chip giant emerges from relative obscurity in the driverless space to become a major supplier after completing its $15.3-billion purchase of Mobileye this week.

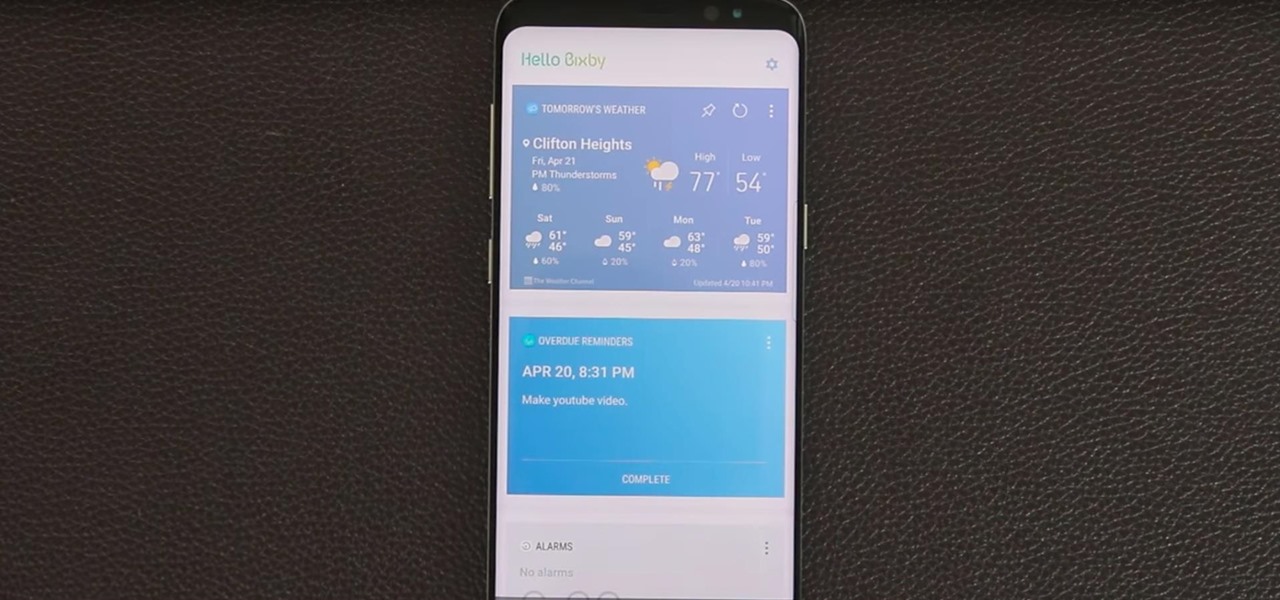
Bixby — Samsung's voice-activated digital assistant — has been delayed again because the software still can't recognize English. Although Samsung claims Bixby can execute 15,000 tasks, it appears it's inability to master English is a major obstacle that's preventing its full release in the United States.

Modern warfare takes on a more literal translation with the advent of new augmented reality displays revealed recently by the US Army to improve soldiers' situational awareness on the battlefield.

Drive.ai (a startup founded by Stanford University graduates), Waymo, General Motors, and serial entrepreneur and author Vivek Wadhwa are featured in today's top news.

Uber CEO and co-founder Travis Kalanick is taking an indefinite leave of absence from the company, as Uber's recent upheaval has far overshadowed any developments in its driverless initiative during the past few days.

Waymo's transfer of its driverless car know-how to commercial trucks will likely pose few challenges for the self-driving unit of Alphabet, which owns Google.

Apple staff will be put through their paces now that the company's "Automated System" for driverless cars is in motion.

Apple is combining internal and external talent in an effort to give them in edge in the augmented reality market, though we still don't know what form their foray into alternative realities will actually take.

With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!

When developing for the HoloLens, keeping a constant 60 fps (frames per second) while making things look beautiful is a challenge. Balancing the processing power to display complex models and keeping the frame rate where it needs is just a straight up painful process, but a solution seems to be on the horizon.

The Note7 fireworks bonanza was unprecedented in scope. A recent report suggests that Samsung could lose upwards of $20 billion in lost profit due to this fiasco.

Hello friends. This is actually my first how to.

While password cracking and WPS setup PIN attacks get a lot of attention, social engineering attacks are by far the fastest way of obtaining a Wi-Fi password. One of the most potent Wi-Fi social engineering attacks is Wifiphisher, a tool that blocks the internet until desperate users enter the Wi-Fi password to enable a fake router firmware update.

Edit: Some of the methods I show you may be difficult, or not work at famous or high quality hotels.

On most Android devices, the various volume levels are comprised of either 7 or 15 steps between minimum and maximum. For voice-call volume, alarms, and notifications alike, 7 presses of a volume button will bring you all the way from silent to full-blast. With media controls, you get 15 steps between mute and max.

For some, there's nothing more thrilling than carrying an armful of bags while wandering the mall; for others, there's nothing more annoying. No matter what category of shopper you fit into, the truth is that you aren't always in control of what you buy.

If you've recently joined the ever-growing ranks of the cable cutters, you're far from alone. More and more people (myself included) are getting fed up with service providers' outdated subscription models and absurd pricing—and canceling their service.