
News: Magic Leap Is 'Racing Toward Launch' According to New CMO
Well, we have some potentially good news for those wanting to experience Magic Leap. The ultra-secretive company seems to be planning a big year in 2017.


Well, we have some potentially good news for those wanting to experience Magic Leap. The ultra-secretive company seems to be planning a big year in 2017.

Many new parents will tell you how hard it is to name a baby. Some have stories of how they knew what the name of their child would be from before conception, only to change their mind when they were born. Sometimes new babies can go weeks without a name since there is an endless selection to choose from.

The rumor train for Samsung's upcoming flagship phone is now running on full steam, and some of its cargo (or lack thereof) might not be warmly welcomed by many when it finally pulls into the station.

Designing for mixed reality, especially for the HoloLens, can present unique challenges. Dong Yoon Park, a Principal UX Designer at Microsoft with a passion for typography, recently gave a talk to the Windows Holographic Users Group Redmond (WinHUGR) about the pitfalls he ran into trying to convert what started out as a 2D iOS app 5 years ago to the newer 3D Holographic frontier with Unity.

Robots are always really cool, if you ask me. Sometimes they're made out of Legos, and that's even cooler.

With the holidays over, a lot of people with shiny new Google Homes are getting their first chance to explore the new Google Assistant. Before the Google Home's release, the Assistant was only available for the Google Pixel and Pixel XL, or in a text-based form with Google Allo—but now it's gone mainstream.

Before we dive any further into getting your Mac ready for hacking, I wanted to continue on with the concept of encryption. In the last part, we talked about full disk encryption on your Mac, but now I want to quickly cover the encryption of disk images before we dive into managing passwords, terminal emulators, etc.
Google's new Pixel phones are shaking things up in the world of Android, as the Nexus line is no more, and the Mountain View tech giant has now become a smartphone OEM. The long-term impact of these moves remains to be seen, but we already know that Google, the manufacturer, will be adding extra software and UI features to the version of Android that ships with its Pixels.
Android device manufacturers may see the new Pixel "Phone By Google" devices as just another competitor, one that likely won't upset their entry-level margins. But that would be a mistake. Pixel is Google's call to action. With Google now offering as near to perfect an Android experience as we've had so far, OEMs that want to keep selling smartphones in a world flooded with them will need to start working for the privilege.
YouTube has gotten so big over the years that it is now viewed by more 18-49 year-olds than any cable network in the United States. But even though online video platforms continue to gain ground on traditional TV stations, there's one aspect to the viewing experience that live TV still does better—it lets you tune into a channel, then just sit back and watch indefinitely.

The big day has finally come—the new iPhone 7 and iPhone 7 Plus have been officially unveiled. Apple debuted their new flagship devices at a keynote event in San Francisco on September 7, and as we've grown to expect, there are tons of changes in store for the world's top-selling smartphone.

Many midrange phones are being manufactured without a gyroscope sensor—the Moto X Play, third-generation Moto G, and several of Samsung's Galaxy Grand models, among others. It's not exactly an essential smartphone sensor, and leaving this out keeps the phone's price point down, so it's an understandable omission.
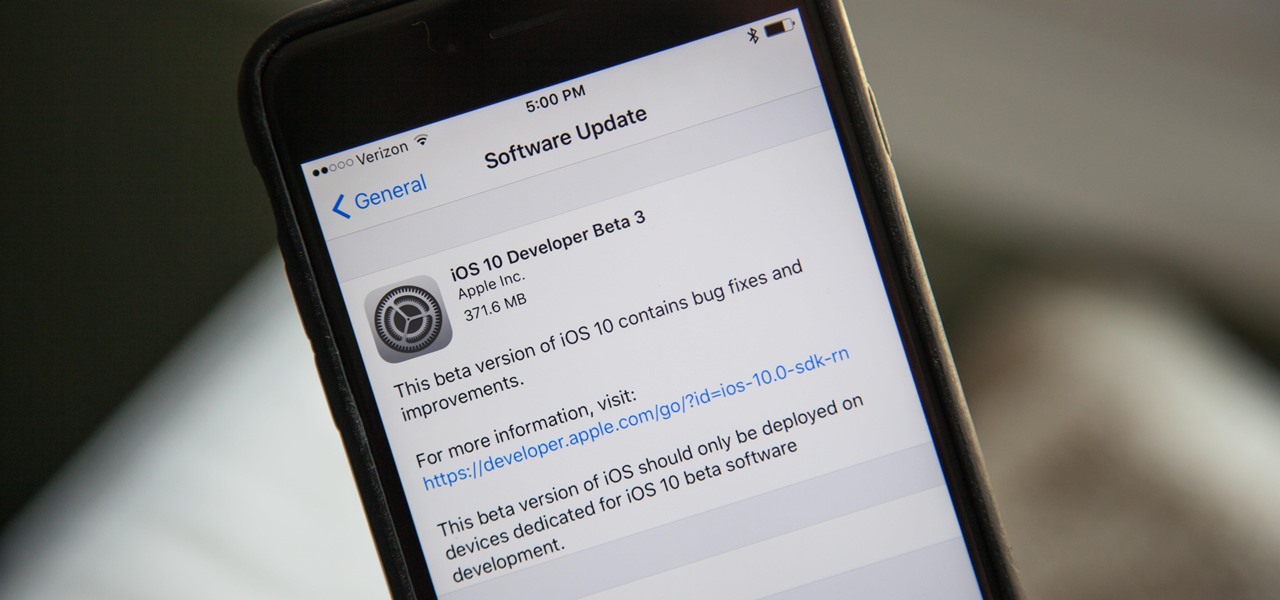
With the next iPhone release around the corner, Apple is hard at work getting iOS 10 squared away. On Monday, July 18, they issued the third beta of iOS 10 to developers, which should be released within a few days to those using the iOS 10 public beta.
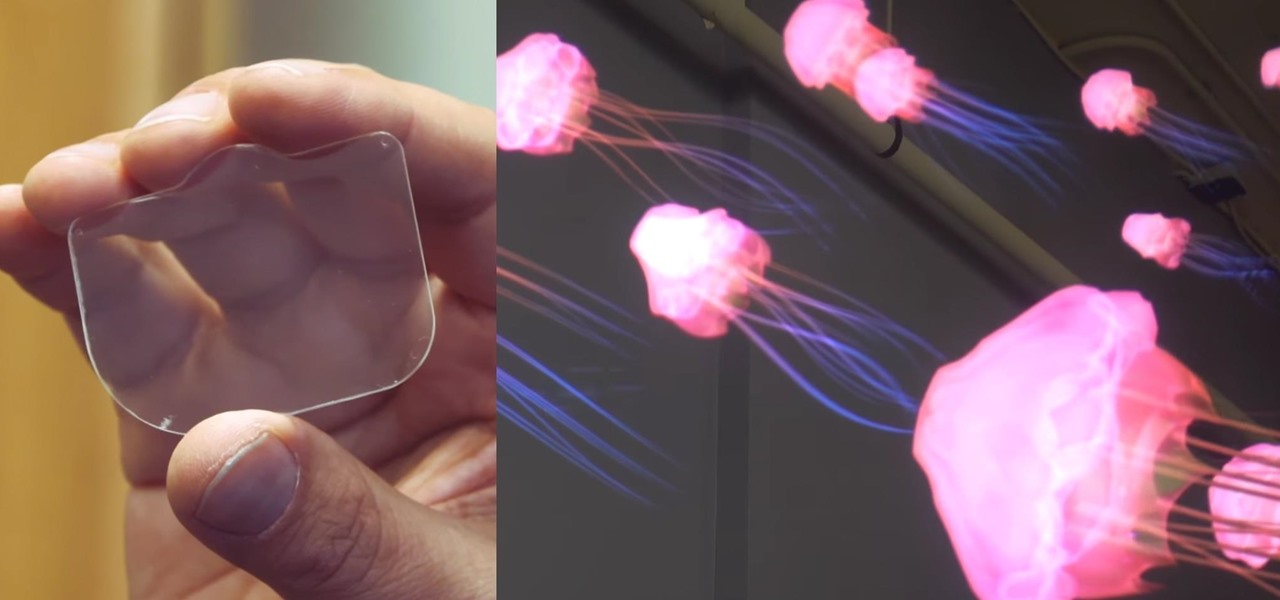
Virtual reality headsets are all the rage these days, and among the menagerie of tech companies gunning for the top spot, there's one mysterious startup that is ahead of the game—Magic Leap—and you can tell just by watching their latest demo video of their product in action.

We like picnicking of all sorts, from picnics in bright, sunny weather to grey or rain-drizzled picnics. So it's not a stretch to say that we've become quite good at packing sandwiches to enjoy later. But we're always looking for a better way to do things, and that includes our sandwich making—and we think we've found the best way to make a sandwich ever.

This tutorial follows the same idea as my original tutorial for windows, but I've redone it to work with Mac OS X. Here's how to get a meterpreter session from your victim opening a malicious word document:

If history holds true, we'll see the iPhone 7 arrive this September, and just like many times before, there are already a ton of rumors about its features. As usual, many claims are pure speculation, but there are some trustworthy reports and lots of good information we can use to make some educated guesses regarding Apple's upcoming flagship.

Now is the time to act if you've been in the market for some must-have Android apps but felt like the price was a little out of your range. The Google Play Store is running a sale so you can pick up some high-quality paid apps—including the popular Nova Launcher Prime and Poweramp Music Player, among many others—for just $0.99 each. While there are quite a few solid apps here you should try—and with a two-hour refund window, why not try them all—here are our favorites you should seriously con...

Ever been in an argument, only to have the other person cop out by saying "I never said that," when you know full well they did? Or how about one of those times when you're sitting in the lecture hall, half dozing off to your professor's monotone ramblings, when your ears perk up because they somehow know you missed something important that was just said?

Cable TV providers were dealt a pretty significant blow on Thursday, February 18th, 2016, when the Federal Communications Commission decided that customers should have a choice in what type of device they use to watch cable, instead of being forced to rent a set-top box.

In my last tutorial, I talked about creating a virus inside of a Word Document in the scenario of a mass-mailer attack. In this post, however, I'm going to be covering creating a fake image or screenshot with a meterpreter backdoor hidden inside to be used in a similar scenario. Step 1: Creating the Virus

Every phone has its issues and quirks, and the Nexus 5 is no exception to this rule. One of the most common troubleshooting questions asked by its owners is "Why does my Nexus 5 keep shutting off or restarting?" where the device suddenly decides to reboot or power off randomly on its own.

Hello again, and welcome back to another tutorial on functions, this time, covering recursion. What Is Recursion?

Hello World ! Well, welcome in my post. This will be in series, and this is first part. Throughout the series, I will share my research and findings with you. And that will be on topic, Encryption Is Not Enough. We will see, how Encryption is broken & what countermeasures should be implemented to secure it. Let's begin, Why do we encrypt ?

First of all, Merry Christmas and Happy New Year to all Null-Byters that learn and teach in this wonderful site. In this article we will explore the basics of the meterpreter's IRB (Interactive Ruby Shell).

Welcome back, my greenhorn hackers! As expected with Null Byte's dramatic growth over the last year, we have added many new aspiring hackers who are still lacking in the basics of networking. In addition, with the new "White Hat" certifications coming out shortly, the exam will require some basic networking skills and knowledge to pass.

Do you ever thought that you can't control an Internet disconnected system? I saw a funny video in Chema Alonso's youtube channel (A well-known hacker of my country and creator of Fingerprinting Organizations with Collected Archives among other security tools), and decided to post something similar.

This is my first tutorial on this website. So, if you think anything to be wrong, just place it in the comments.

Greetings dear null byters, today we start a new series, we will start to attack users using social networking that are popular such as Facebook, Skype, and much more, and in part 1 of the series will engage users of Skype.


In part one of this tutorial we found out that your English teacher is a paedophile, by using a Man in the Middle attack to intercept his internet traffic.

At night, no matter how dim my Android's screen gets, it never seems to be enough—especially when I'm in bed. In fact, in pure darkness, the lowest brightness setting on my Android devices end up giving me a headache that keeps me up for hours.
If you ever need to spice up a party, drinking games can really get things started quickly. The objectives are generally to complete tasks or challenges, but it's really all a thinly-veiled excuse for increasing everyone's alcohol intake in a hurry while testing levels of inebriation.

Video: . Being one of the most popular DIY/maker projects around, Musical Floppy Drives are nothing new. However, myFloppyDriveOrchestra includes a few unique features, which separate it from the crowd.

Programming is an essential thing in hacking/pentesting, and at times, I do not feel that it is being addressed enough here, at Null-byte. I understand that this is a forum dedicated for hacking, but I'll address some of the stuff I feel is muy importante about programming. I am not a professional programmer, but I do have experience and I do want to share some of the stuff professionals have taught me.

Hello fellow grey hat hackers, as hackers it becomes necessary for us to be able to send emails anonymously. Whether for whistle blowing or pranks or social engineering or whatever, it just is necessary for us to do that.

Welcome back, friends! Many times, businesses, friends, and family will lock their zip files with a password to keep their files secure. It is reasonable, and understandable. Well, thanks to hackers, there are many ways to get past this wall of security.

A good chef's knife is a thing of beauty and, with proper care, a joy forever. It can totally change the way you cook and turn even the dullest prep work into a glee-filled task.

If you read my last tutorial on using SEToolkit, you probably know that SEToolkit is an effective way to make malicious actions look legitimate. But, that was only the beginning... the truth is, Metasploit and SEToolkit belong together, and help each other very well.

Hi everyone! In the previous part of this series, I introduced one way to hijack a program's execution flaw, though I only showed you how to crash the program and left you with a little mystery to solve. Today we are giving the solution of that and then introducing shellcode usage and remote command execution.