The transcribing app can be an invaluable tool, especially if you're a student or are in a profession that relies on audio journals or interviews. These apps can convert important recordings like lectures and meetings into text for you to carefully read through to better comprehend.
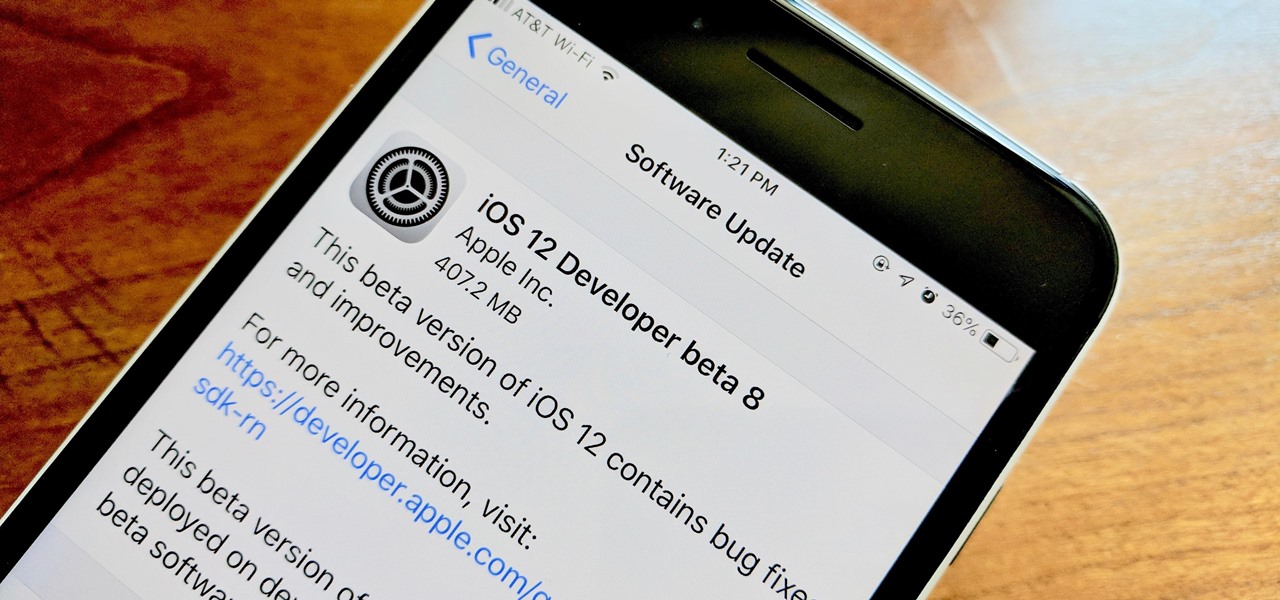
Apple developers, check your iPhones — Apple released the eighth developer beta for iOS 12 on Wednesday, August 15. This update arrives just two days after the release of dev beta 7, which Apple quickly pulled after complaints of unusual performance and stability issues.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.

Right on the heels of the iOS 11.4.1 beta 3 release, Apple pushed out iOS 12 beta 2 to registered developers on Tuesday, June 19. Public beta testers received the same version, labeled as iOS 12 public beta 1, six days later on Monday, June 25. Last year, the iOS 11 public beta opened up just five days after the release of iOS 11 developer beta 2, so iOS 12 is pretty much right on track in that regard.

Database technology has vastly improved the way we handle vast amounts of data, and almost every modern application utilizes it in one way or another. But the widespread use of databases naturally invites a slew of vulnerabilities and attacks to occur. SQL injection has been around for awhile, and as such, there are many defense methods in place to safeguard against these types of attacks.

The key to becoming a competent white hat is knowing how the technology that you are trying to exploit actually works. SQL injection is one of the most common methods of attack used today and also one of the easiest to learn. In order to understand how this attack works, you need to have a solid grasp of ... you've guessed it ... SQL.

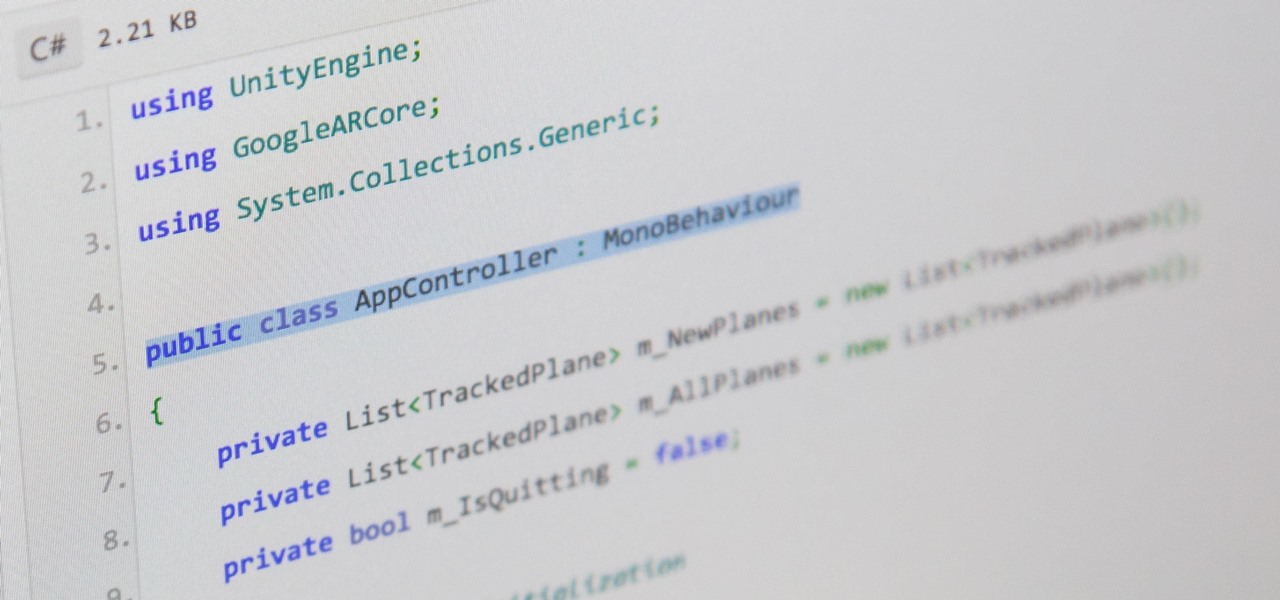
There are hundreds, if not thousands, of programming languages and variations of those languages that exist. Currently, in the augmented reality space, it seems the Microsoft-created C# has won out as the overall top language of choice. While there are other options like JavaScript and C++, to name a few, C# seems to be the most worthwhile place to invest one's time and effort.

Tesla hopes high-level personnel changes will help it gain an edge in neural network knowhow for its models' self-drive features, following the replacement of its Autopilot chief and the appointment of a recent Stanford grad to head its AI and Autopilot vision research.

Kuru is called the shaking disease, its name derived from the Fore word for "to shake." Caused by an organism that infects the part of the brain that controls coordination, people afflicted with kuru shake uncontrollably.

Welcome back, everyone! In this lesson, I'm going to go over the use of the echo function and variables, as well as basic syntax.

I mentioned in one of my earlier articles something about ghost hackers, and very shortly stated a thing or two of what they do.

First of all, I would like to apologize for a week long absents for the tutorials of this newly series, Raspberry Pi. But obviously I'm back and I present all you guys a article on turning your Raspberry Pi into a hacking platform. I'm gonna use the platform Kali Linux for the Raspberry Pi. I should note that I'm not gonna go into detail on how to install Kali Linux since OTW already has done a tutorial on how to turn your Raspberry Pi into a Hacking Pi. The point of this particular tutorial ...

to stay secure, you dont just need Tor, and a VPN. You need good browsing habits. What are Browsing Habits You Ask?
I see many people posting the same thing on the internet. "How do I become a hacker? Where do I commence?"

I am very new to Null Byte but I find much of its content and community incredibly interesting. I spent quite a bit of time just chronologically going through the posts and I noticed a common theme in many of the beginner posts. Many people seem to want to know the 'secret' or a paragraph on "How to Hack" and become a hacker in a few minutes. I started off this post as a reply to a question from a beginner but thought it might be beneficial to have for those stumbling across this site.

Sweaty palms, stuttered speech, and terror blackouts: if you're someone who absolutely despises speaking before audiences, you've probably experienced side effects like these. No matter how well prepared we are, or how familiar our audience is, giving a presentation can be an experience more terrifying than death, according to psychologists. Unfortunately, it's impossible to avoid public speeches, but you can make these events less frightening with a few simple hacks.

Audiobooks are great because they require little-to-no effort on your behalf. When driving in traffic, why not listen to George R.R. Martin's lengthy A Feast for Crows instead of repetitive, commercial-laden radio? Maybe it harks back to prepubescent bedtime readings, but having things read to me is a very satisfying experience.

The autocorrect feature in Apple's default iOS keyboard is anything but perfect. Sometimes it can't autocorrect things on your iPhone to want you want, while other times there's a software bug that just flat out gets it wrong. These autocorrect issues can get even worse thanks to Apple's predictive text feature, QuickType, and the inability to edit your custom dictionary.

Welcome back, my budding hackers! When we are looking for ways to hack a system, we need a specific exploit to take advantage of a certain vulnerability in the operating system, service, or application. Although I have shown you multiple ways to exploit systems here in Null Byte, there are still many more exploits available that I have not yet shown you.

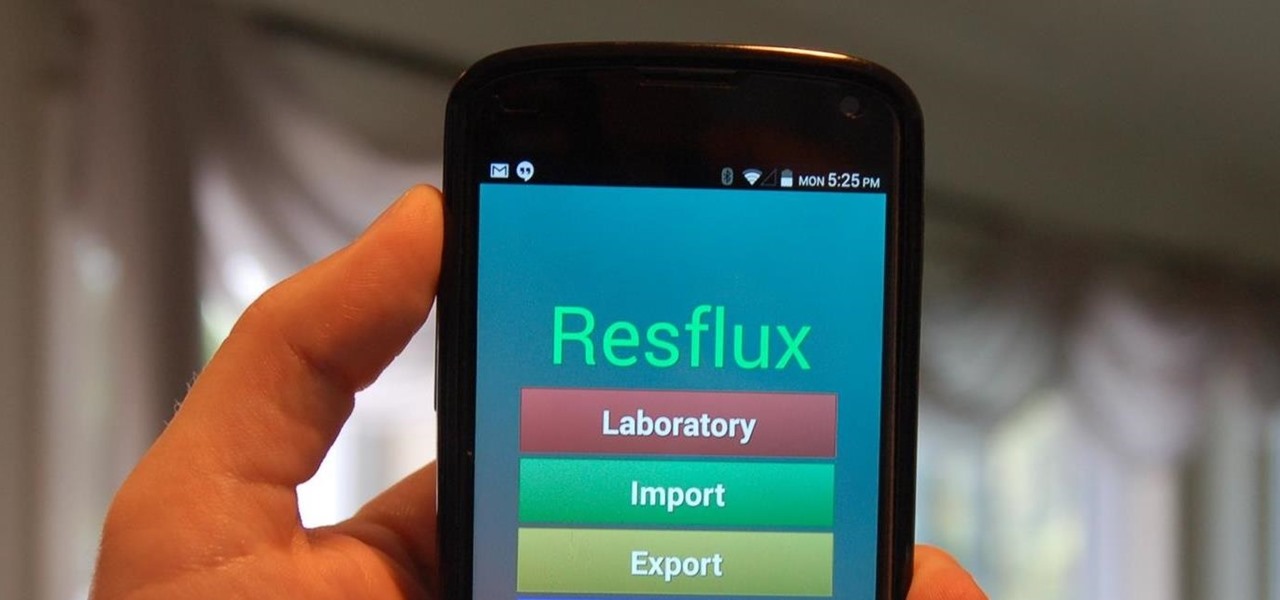
Resflux is an Xposed mod developed by Julian Paolo Dayag, aka WisdomSky, that provides users with a straightforward and functional way to customize and theme almost every aspect of the packages (apps and system components) installed on their Android device.

It's the biggest day of the year for all things Google. Their developer conference, dubbed Google I/O, gives us a peak at what the guys at Mountain View have been working on over the course of the past year, and this year, Android was center stage.

Welcome back, my hacker apprentices! To enter the upper echelons of hackerdom, you MUST develop scripting skills. It's all great and well to use other hacker's tools, but to get and maintain the upper hand, you must develop your own unique tools, and you can only do that by developing your scripting skills.

Welcome back, my budding hackers! As you know, I firmly believe that to be a true professional hacker, you need to be proficient in Linux. This is for a number of good reasons.

With all of the new features and third-party apps out there making Android better and faster every day, it's quite frustrating to me that keyboard advancements remain relatively static.

Watch this video tutorial to learn how to use hand signals on a bicycle. Bicycles don't come with turn signals and brake lights. Fortunately, there's already a universal language for indicating turns and stops on a bike.

In this language tutorial teaches how to say numbers one through five in Mandarin Chinese. This lesson is perfect for children or beginners learning Mandarin Chinese.

Learn how to sing this simple children's song, "Twinkle Twinkle Little Star" in Mandarin Chinese with this language tutorial. This is a fun lesson for someone who is learning Mandarin Chinese.

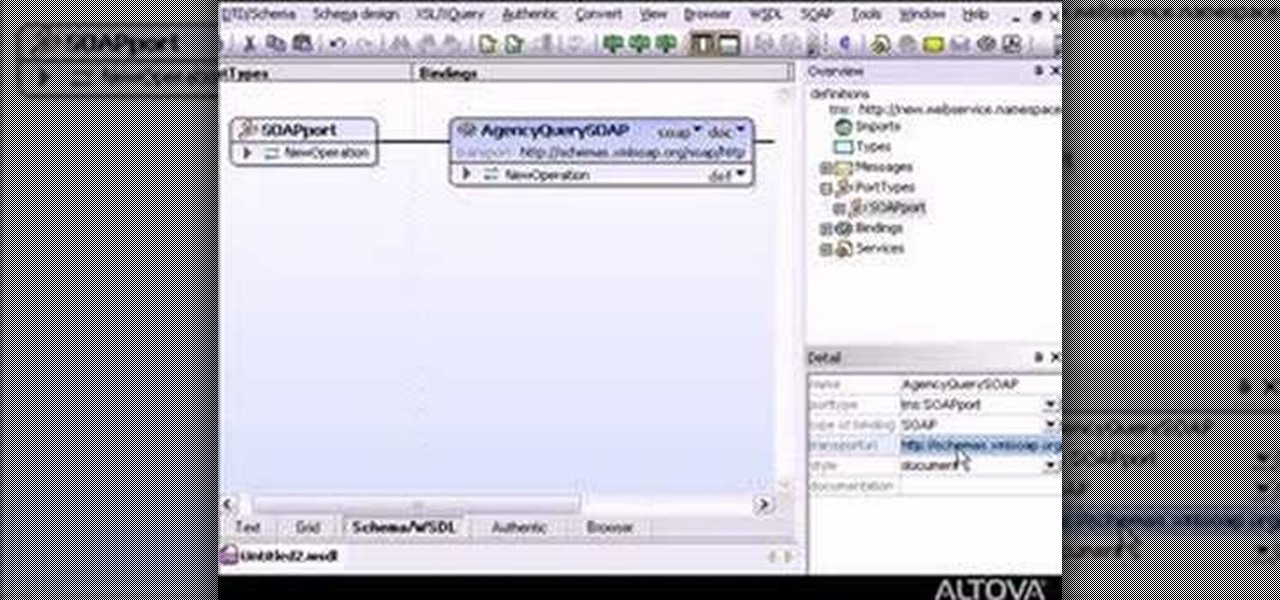
If you want to do some easy XML editing, then this markup language video is the one to watch, for XMLSpy. The graphical WSDL editor allows developers to design the interface for Web Services in an intuitive manner.

Altova XMLSpy 2007 includes powerful viewing and editing tools that simplify the creation and editing of XML documents for your markup languages. This video will show you the general rules on how to use XMLSpy for XML programming.

This language tutorial teaches you how to create words with the letters from the Arabic alphabet. Write, read and understand the structure of words in modern standard Arabic with this how to video.

This how to video will teach you to speak simple greeting and the days of the week in Arabic. Learn some basic words in modern standard Arabic that can help you when you travel to Arab countries with this language tutorial.

Let's practice some finger spelling this time faster! Look at the signer and write down the words he finger spells in American Sign Language (ASL).

Watch this video to learn different phrases and verbs to communicate your grasp of the language while speaking French.

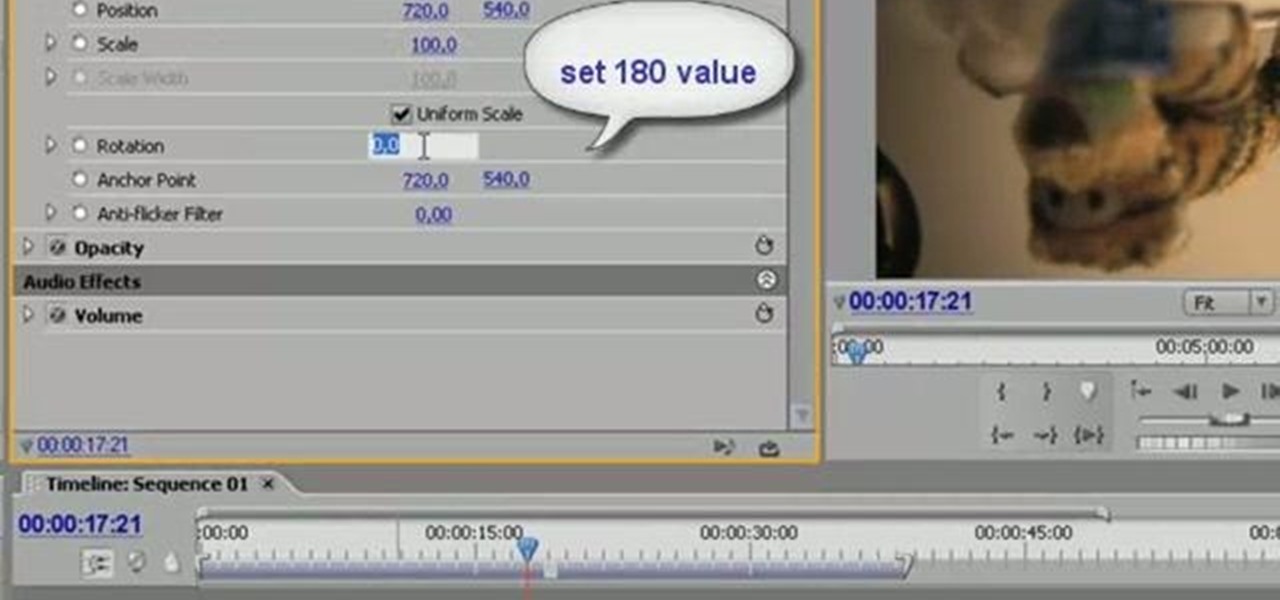
Learn to rotate a video clip 180 degrees (or any arbitrary angle measurement) using Adobe Premiere Pro in this tutorial. The audio portion is in Italian, however callouts have been added in English to make the tutorial easy to understand.

To hit this shot, you must use right hand English with a tip of top and a firm stroke. It is harder than it looks.

To hit this shot, you have to thinly cut the object ball using high left English with a soft stroke.

This video covers the basics of Jewish blessings - how to say each word in Jewish, what it means in English and then how to put them together in different blessings.

This is a video of Peter Gade demonstrating moving to the net on the backhand side, sorry no English translation of it.

This is a video of Peter Gade demonstrating backhand defense for going to the backhand side of the court, sorry no English translation of it.