With technology giants like Apple and Google finally entering the fray, the move toward mass adoption of augmented reality is ramping up. Apple's ARKit and Google's ARCore will allow entirely new categories of apps to be made. Unfortunately, in a world of heavy competition, getting these two frameworks to work together wasn't a priority for either company.
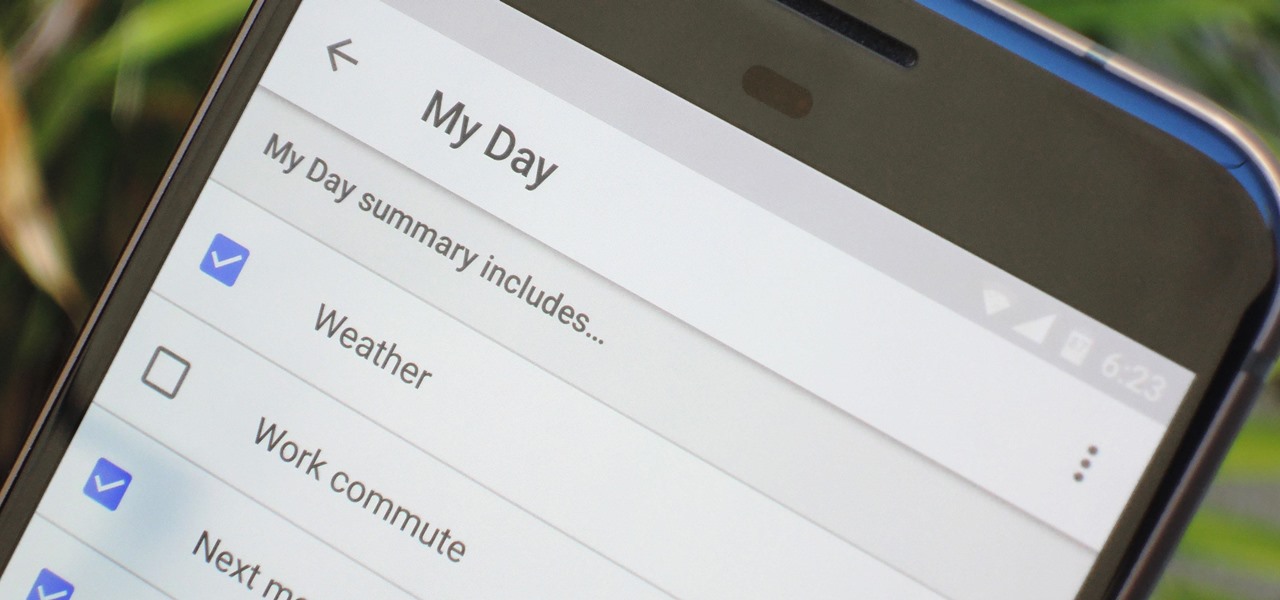
The Google Assistant comes in several different flavors. There's the baked-in Google app on Android, the dedicated Google Assistant app on iOS, and the Assistant-powered Google Home smart speaker. But no matter how you access it, your Assistant will only get better if you take some time to personalize things.

If you need a tiny, flexible attack platform for raining down human-interface-device (HID) attacks on unattended computers, the USB Rubber Ducky is the most popular tool for the job. By loading the Ducky with custom firmware, you can design new attacks to be effective against even air-gapped computers without internet access. Today, you'll learn to write a payload to make "involuntary backups" through copying a targeted folder to the Ducky's USB mass storage.

Tesla says the new version of Autopilot is now as good as the previous one, after having completed over-the-air updates of the driverless software during the past few days.

During the opening keynote of their Worldwide Developers Conference today in San Jose, Apple introduced the ARKit for the new iOS 11 that will bring augmented reality apps to millions of compatible iPhones and iPads.
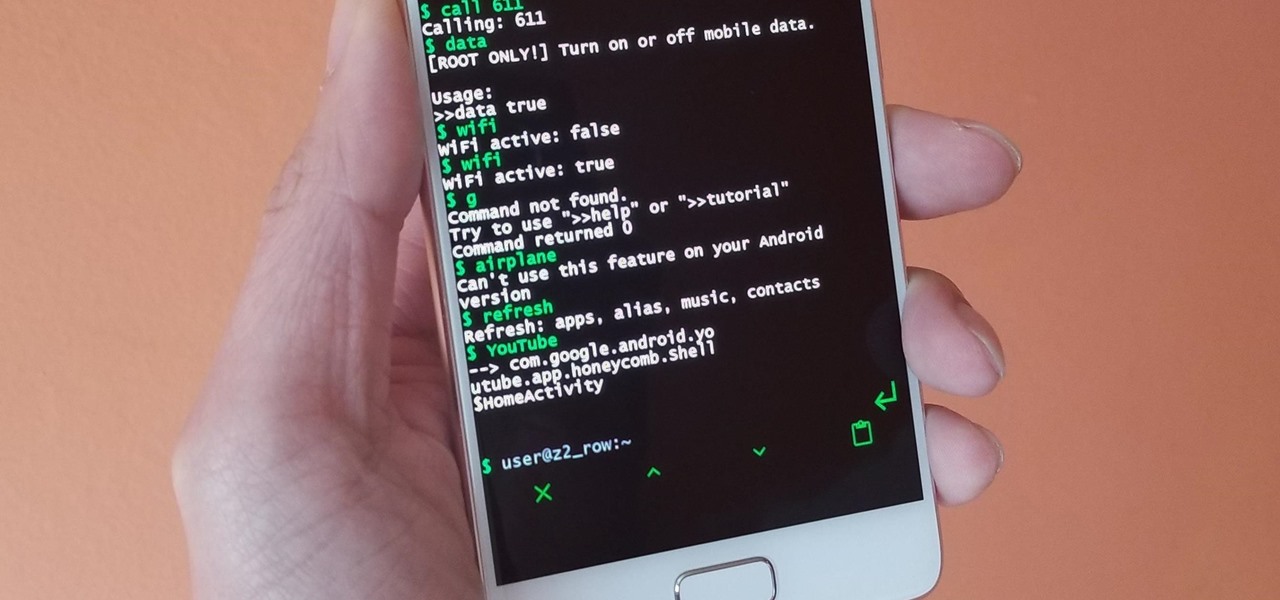
Running commands on Linux seems so complicated for the layman that it may as well be a foreign language. But for the die-hard terminal users, or for those who are just curious about the Linux experience, there's a new Android launcher that gives your home screen a command line makeover.

When Kaci Hickox, a Doctors Without Borders nurse, returned to New Jersey from working with Ebola patients in West Africa in 2014, she was surprised by her reception. Instead of a quiet return to her home in Maine after four weeks on the front line of Ebola treatment, she was quarantined by the State of New Jersey in Newark. She later filed a lawsuit in U.S. District Court for violation of her civil rights, false imprisonment, and invasion of privacy.

3D modeling is usually a very long and complicated process. Manipulating the thousands to millions of vertices, faces, and triangles to the correct shape you want is just the first part of the process, and can take a good while depending on the level of detail needed. From there, you need to texture the model by applying the UV coordinates and placing the textures in the correct places. And all of this isn't even including the process of creating normal maps.

Metasploit is an extremely popular pentesting tool capable of enumeration, exploitation, and injecting shell code, and is a part of almost every hacking toolkit. So there's no way I could leave this out of our series on getting your Mac set up for hacking.

Emojis, for better or for worse, have essentially taken over online forms of communication. And now, thanks to a recently discovered feature in iOS, they are going to change the way you search for nearby places.

What's up guys? Welcome to a sort of general walkthrough on how one might approach a reversing and analysis on a crypted malware. This is by no means a universal technique so don't assume that this will occur in every scenario, it's more of a demonstration than anything really.

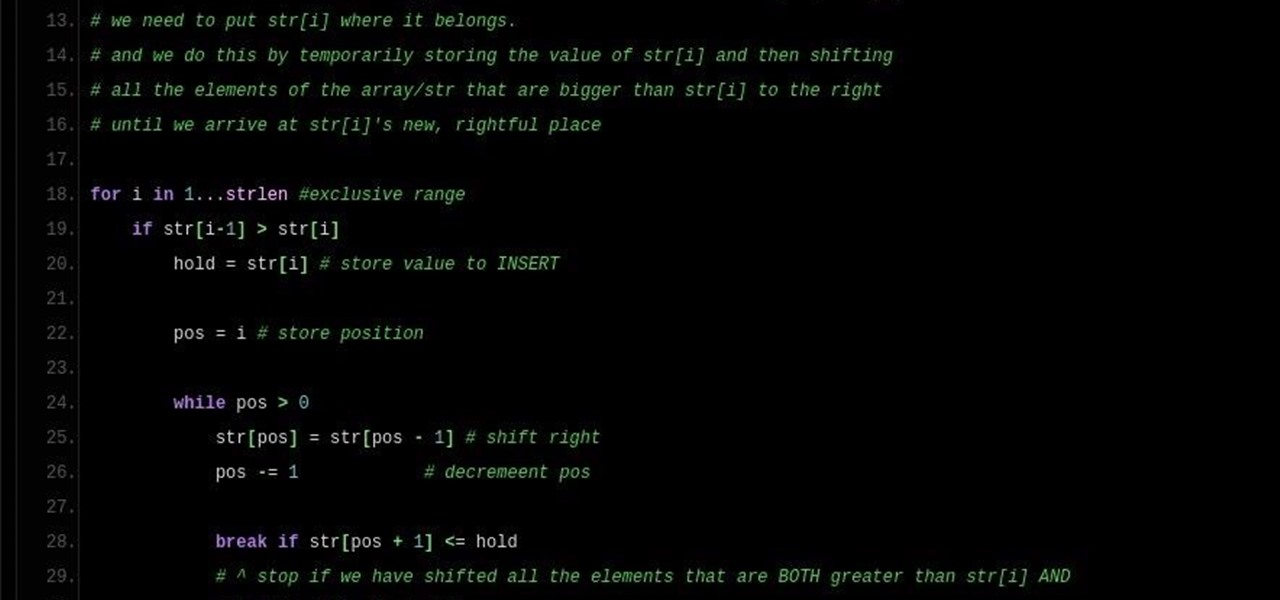
Note: a bug was found in the Insertion Sort implementations. The bug was corrected in each language. Please refer to the pastebin links for the most up-to-date versions of the sample code. Any screenshots may be behind. More about the bug can be found here.

Hey everyone, this guide will show the process of stealing your victims Facebook credentials. This is a followup to my previous post.

In this series you will learn how to use PHP to perform attacks, gather information, and setup backdoors. Along with performing attacks you will learn how to protect yourself from them. In this part you will learn about PHP as well as install Apache and PHP. What you'll need for this series

Hello friends! This tutorial will teach you how to build a local pentesting lab on your Linux machine which will enable you to easily install common web applications so you can practice locating and exploiting their known vulnerabilities (or discover new ones!). In particular, this is an excellent way to learn how to hack Wordpress, Joomla, and Dupral plus many more!

Instead of suffering through long, dull meetings with your supervisors and coworkers, you can turn those office table sessions into your very own psychological experiment.

Welcome back Java programmers! In this tutorial we'll being going over Variables/DataTypes and Type-casting

I saw many people asking for a Tutorial about writing their own Remote Administration Tool, so I now introduce you in a basic kind of RAT. This program is not for real use, but for learning how you could write this kind of tool. It will be basicly coded and not very refined. I used Python 3, so you have to install it if you want to use this program unchanged. Also this RAT is for Windows and almost all features won't work under Linux.

First of all, Merry Christmas and Happy New Year to all Null-Byters that learn and teach in this wonderful site. In this article we will explore the basics of the meterpreter's IRB (Interactive Ruby Shell).

BlackBerry has yet to find a home amongst the iPhone and popular Android phones, with sales plummeting over the last couple years, but this might be a thing of the past thanks to their latest device, the BlackBerry Priv. It has decent numbers so far and was even sold out on Amazon shortly after its initial release.

Hello fellow training hackers. I do not know if many of you are familiar with ruby, but since it is a useful scripting language, that hasn't been covered too much here on Null Byte, I thought why not do some How-tos about it now and then.

Programming is an essential thing in hacking/pentesting, and at times, I do not feel that it is being addressed enough here, at Null-byte. I understand that this is a forum dedicated for hacking, but I'll address some of the stuff I feel is muy importante about programming. I am not a professional programmer, but I do have experience and I do want to share some of the stuff professionals have taught me.

hello my dear colleagues, I made a visit to nullbyte and found that there is not a complete tutorial about the google dorks, so I felt the need for this tutorial, and seeing that there are many newbies around, so here's a tutorial that will teach you how to use google to hack.

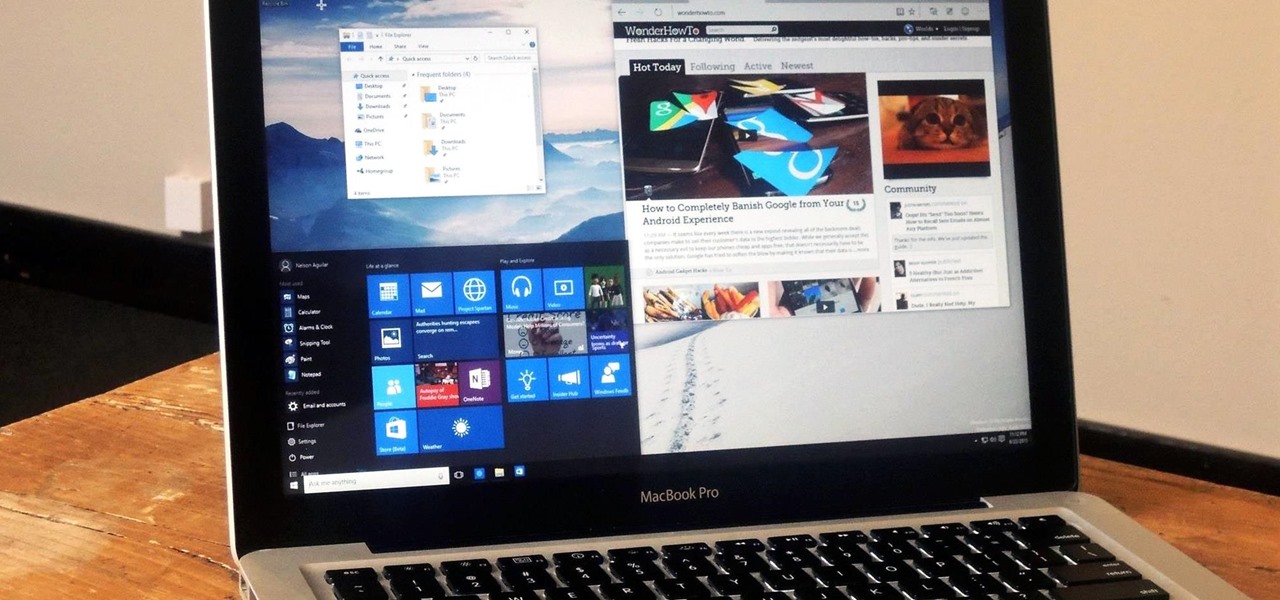
While Windows 10 is still a few weeks away from a public release, that doesn't mean you can't enjoy its brand new features right now. Anyone with an Insider Preview account can install Windows 10 on their computer. And that doesn't just go for those that own a Windows PC—Mac users can get their hands on Windows 10 as well.

Hi there, Crackers, Welcome to my 7th post (Part-1), this tutorial will explain about the basics of Batch Scripting.

With our internet-connected devices growing in number by the year, it would be nice if they could somehow all be interconnected. This is becoming commonplace for our tablets, smartphones, and laptops, but our media streaming boxes still seem to be isolated in their own little worlds.

The Apple Watch is finally here! We'll have loads of guides and videos for you guys to check out in the following week and beyond, but we thought it'd be best to start off showing you how to set up and pair that brand new beautiful Apple Watch of yours to your iPhone.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Hi everyone. Recently I've been studying some topics about Assembly, memory and exploitation, and thought I could write something nice, easy and fast about it, just because I like to share what I learn, and probably sharing what you learn and trying to explain it to a stranger is the best way to learn it better. It worked for me, and I hope it will be useful for you too.

Heartbleed, move over. There's a new bug in town, and this time it's also affecting Mac and Linux computers. It's called Shellshock (its original official title is CVE-2014-6271), and it's currently got a 10 out of 10 severity rating over at the National Cyber Awareness System. While some updates have been issued to fix this bug, they were incomplete, and your system is probably still vulnerable, as it has been for the last probably 20 years.

As soon as third-party keyboard compatibility was announced for iOS 8, Apple loyalists and the newly curious both looked to the popular Android third-party keyboard developer, SwiftKey, to see if they'd be offering their services to iOS.

At the core of your Galaxy S5's hardware lies the central processing unit, or CPU for short. Practically every piece of data, every binary bit, has to pass through your CPU before it can be used to display a video or execute a game command.

Google's upcoming Android release hasn't even received a name or version number yet, but the third-party development community is already having its way with the firmware.

As Matias Duarte and the team over at Google's Android Design department ready their wares, they've given us a preview version of the upcoming "L" release of Android to try out.

Developing an imperceptible lie is difficult, especially when you're lying right to someone's face. Thanks to smartphones, getting people to trust you is now easier than ever. You can craft a lie in seconds and hit send, all without ever seeing their untrusting faces.

I am not a morning person. This is a fact that has been proven with science. I need every bit of help to get me out of bed in the morning—multiple alarms, extremely loud tones, Pandora—I've tried everything.

Imagine that you're the last person alive. After losing all of your loved ones, you thought you'd never see another human being in your life. Then, they arrive. The hoard of 15-year-old zombies looking for a cute British YouTuber so they may feast on his brains.

A friend of mine has a crazy amount of Reddit karma and gold, and yesterday he let me in on his secret. This person, who will remain unnamed for obvious reasons, created a Python script called Reddit Karma Crawler that finds rising posts before they get too popular.

I'll freely admit that I'm a SwiftKey diehard. I've used the keyboard since its inception in 2010, and it was one of the first apps I ever paid for back in the days of my beloved Sprint Evo 4G. Since then, I've kept up with all its beta iterations, and have unabashedly installed it on various friend's devices.