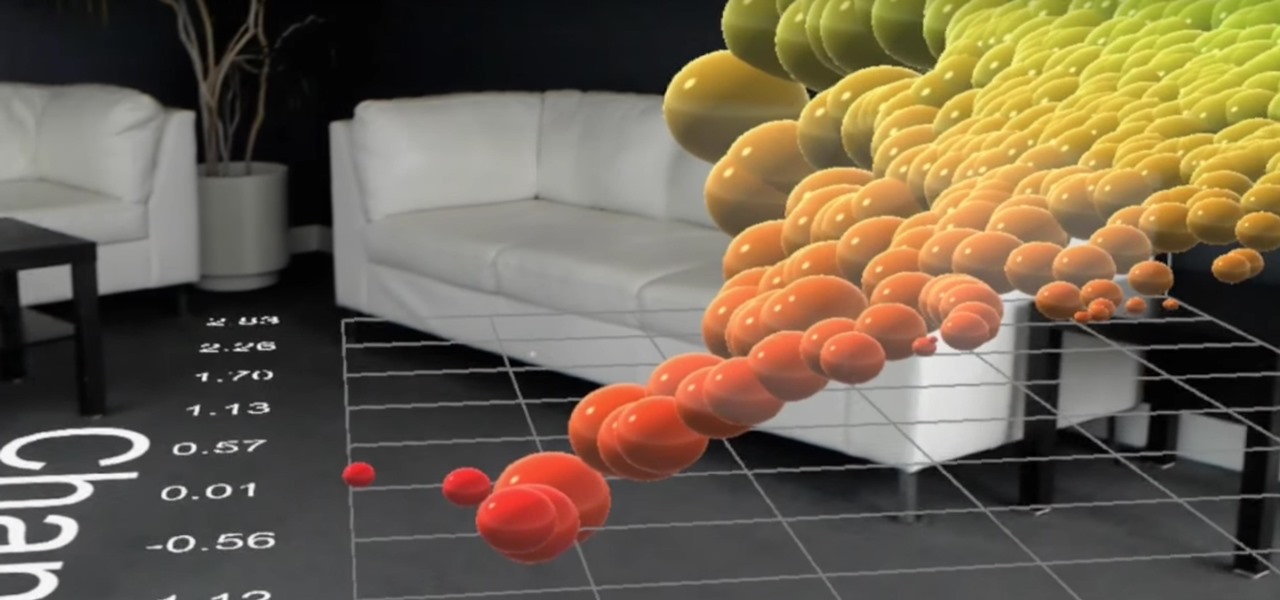
HoloLens developer Michael Peters of In-Vizible has released quite a few videos since receiving his HoloLens last year. Many of his experiments are odd and funny, but some include serious potential approaches to data visualization. In the videos embedded below, you'll specifically see stock market information beautifully rendered in different ways to help understand the data.

Everyone loves sharing pictures and quick video clips with Snapchat, but while the service itself is tons of fun, the Android app is one of the worst on the market. For one, Snapchat takes terrible photos even on high-end Android phones. And to make matters worse, the app is a notorious data-sucking battery drainer.

Our future technology has a lot of amazing possibilities, and few have more promise than augmented and mixed reality headsets. But these advancements come with several concerns over privacy, and if we don't understand them, we may lose control of our own data without even knowing.

If you tend to go over your data allotment each month, or are constantly afraid you will, Verizon Wireless is giving you chance to relax a little bit with up to 2 GB free data for two months.

Whether you are sending your phone in for repairs or finally selling it to upgrade to a new flagship, you are going to need to make sure all of your personal data is removed from your device.
As the protectors of all things good, the Federal Communications Commission is usually busy behind the scenes pissing off Slim Shady, giving out fines for indecent nipple exposure at certain halftime events, and warning the NSA about losing any "confidential" phone information they steal from us.

I use Google Chrome every day for my browsing needs, and I had no idea they were hiding something from me. So, I was pretty surprised to see that Chrome has an entire hidden experimental add-ons section. There are add-ons that work for Mac, Windows, Linux, and Chrome OS, so there's something for everybody.

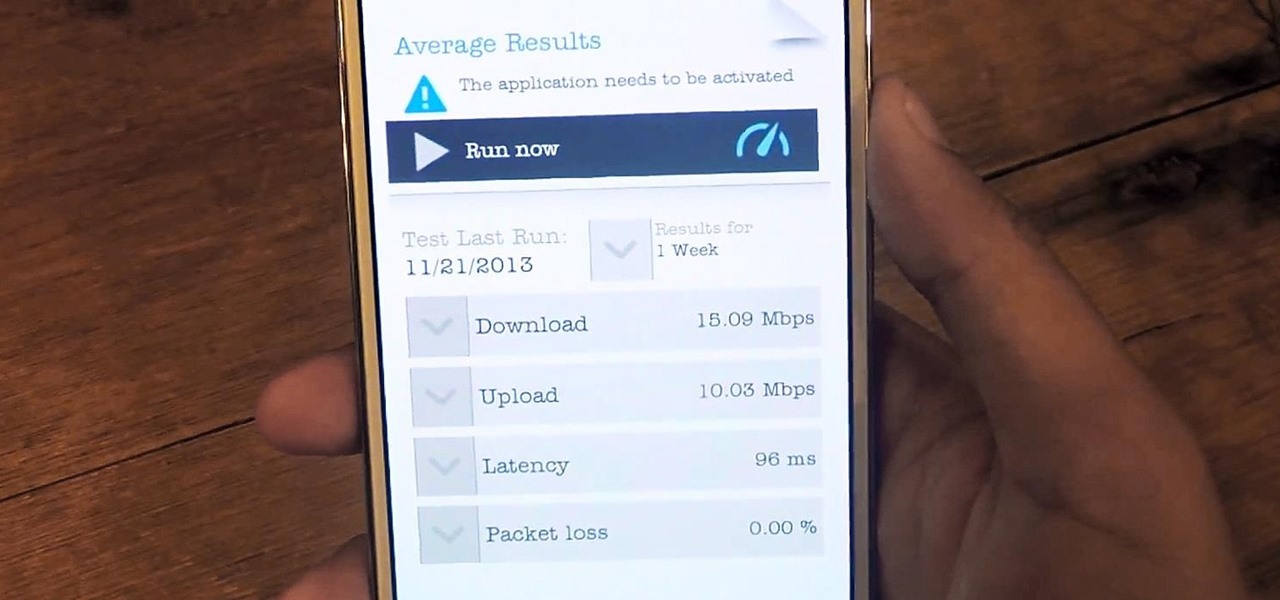
Tons of iPhone 5 users with Verizon Wireless hit the message boards last week complaining about their phones sucking down massive amounts of cellular data when they were actually using a Wi-Fi connection. Of course, that means Verizon customers could have been getting charged for cellular data they weren't actually using.

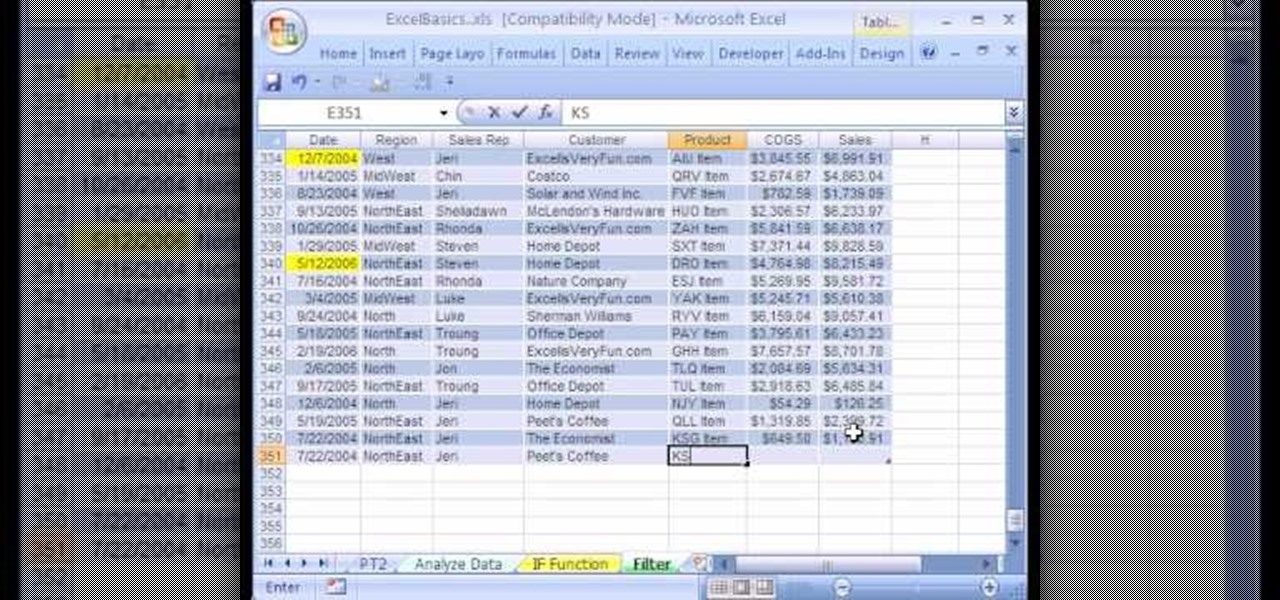
We're on sheet, tab, filter. We want to talk about filter, but we also want to talk about an Excel table or list. It is simply a data set with field names at the top, records in rows, no blanks anywhere and no other data sets touching this data set. When we convert to a table, it does a lot of amazing things. The new keyboard shortcut is "Ctrl T". If data is set up correctly, it will work. Click Ok. You can build a function based on a column of data, i.e. "Alt =" which is the shortcut for sum...

Noodles are the basis for many a Chinese dish, including the Americanized chow mien (or "cooked noodles" in Chinese), noodles in broth, noodles with wonton soup, noodles with air. After all, with a light, airy consistency they're the perfect complement for savory dishes like kung pao chicken and beef and broccoli with soy sauce.

Standing on thin is not perhaps the smartest thing to do during the winter, but miniature tableaus of cute chubby animals standing amongst evergreen trees on a layer of ice are just genius!

Mailboxes don't have to look all lonesome, with only the curb to cheer them up. If you have one of those street boxes on a post instead of a house box, the best thing to do to make a happy mailbox is to give it some company. To improve your home's curbside appeal, take your landscaping efforts to the curb and enhance the area around the mailbox. It's a great way to accentuate your landscape.

Make sure you're getting the best experience from your Blu-ray movies on your PS3 by optimizing your PlayStation 3's audio, video and display settings. Scott Lowe for IGN, shows you step-by-step, the exact process for an enhanced Blu-ray experience.

Data makes the world go round. It has gotten to the point that it's considered the most valuable resource, perhaps even more important than oil. Businesses use data to collect critical information about their users and improve their services; governments utilize it to improve things like public transportation; doctors analyze data to find more ways to save lives.

Data analytics is crucial to the operations of every modern business. This trend is going to continue: in three years, 71% of global enterprises predict a rapid increase in data analytics. Experienced professionals that can project manage data initiatives are in high demand.

We know our Null Byte readers would like to see some iPhone-hacking scenarios on the site soon, but until we get some of those up, we understand that some of you actually use an iPhone as your primary phone. If that's you, and you would like an easier way to get information from point A (your iPhone) to point B (your computer) and vice versa, there's an all-in-one tool that can help.

After reviewing the international plans for major US wireless carriers, it became obvious they're all pretty bad. Your data is heavily restricted, requiring a daily fee which can cost an extra $100+ on a seven-day vacation. That's when I learned about Google Fi, and how for most travelers, it's the best option.

If you're on iOS 11.4.1 or iOS 12 and go more than an hour without unlocking your iPhone, an "Unlock iPhone to Use Accessories" message will appear whenever you connect your iPhone to a computer or other device that tries to use the Lightning cable's data lines. This is to protect you, but it can be annoying if you have no reason to believe that law enforcement or criminals will have access to your iPhone.

The key to becoming a competent white hat is knowing how the technology that you are trying to exploit actually works. SQL injection is one of the most common methods of attack used today and also one of the easiest to learn. In order to understand how this attack works, you need to have a solid grasp of ... you've guessed it ... SQL.

Chrome is the browser of choice for millions of iPhone and Android users, largely thanks to its user-friendly interface and native Google support. But with concerns over sharing private information with massive companies growing, many people are starting to want a little less Google integration in Chrome.

With Gboard, Google created a keyboard with more functionality than just inputting words. The app includes features such as GIF search and live text translation, but it gets even better when you let it learn more about you. With this data, Gboard grows from a good keyboard to one that can complete your sentences.

After setting up your phone, there are a number of things you should do immediately before download your favorite apps. Specifically, now that your data is on the device, you need to take steps now to ensure it's both protected and retained. Fortunately, most of these steps are a one-time process.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

Mozilla's Firefox has always been a highly praised internet browser. Since it's open-source, users know what they're getting without any secrecy. It's got plenty of features that are unmatched by any of its competitors on mobile. However, speed and performance have always been a pain point for Firefox, but Mozilla went back to the drawing board to solve this problem with the release of Firefox Quantum.

Threats to your privacy and security are everywhere, so protecting your data should be the highest priority for anyone with a smartphone. However, one threat many people overlook is the company who supplies the operating system your Android phone runs — Google.

Verizon has long been king in the wireless provider market, but recently it has had to step up its game in the data department. A limited data plan — with supposedly superior service — was no longer cutting it for customers. Many of whom left to take up the sweet, sweet offers of competitors like Sprint and T-Mobile. This past fiscal year, Verizon had a net loss of customers in the first quarter. Something that has never happened to them before.

Welcome back, my greenhorn hackers! In many cases when a computer, phone, or mobile device is seized for evidence, the system will have graphic images that might be used as evidence. Obviously, in some cases these graphic images may be the evidence such as in child pornography cases. In other situations, the graphic images may tell us something about where and when the suspect was somewhere specific.

The highly anticipated VR headset hasn't been on the market long, but there's an issue that has some consumers, and even government officials, concerned about the Oculus Rift. You probably guessed the issue surrounds privacy and the extensive, not-so-secret way that it's collecting your personal data. The privacy concerns came about as various customers and media outlets took notice of the rather lengthy Terms and Services that pop up once you strap yourself into the Rift headset.

Ruby is a dynamic, general-purpose programming language created by Yukihiro "Matz" Matsumoto in Japan around the mid-90's. It has many uses but with it's flexibility, it makes a great language to write exploits in. In fact, the entire Metasploit Framework is written in Ruby! The sole purpose of this series is to teach hackers the basics of Ruby, along with some more advanced concepts that are important in hacking.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Welcome back, my tenderfoot hackers! Not too long ago, I showed how to find various online devices using Shodan. As you remember, Shodan is a different type of search engine. Instead of indexing the content of websites, it pulls the banner of web servers on all types of online devices and then indexes the content of those banners.

Today, I'm going show you how to back up all of your apps and their data using Android Debug Bridge (ADB)—an essential function for all softModders. These commands will be especially useful when you are updating your version of Android, since they don't require a third-party program to run on your device.

Normally, "restricted access" is something you despise. No one likes to be told they can't do something, especially when it comes to the Internet. Unfortunately, having web access at all times can not only eat away at your wallet, but make your day less productive overall, so some sort of moderation is needed.

The iPhone 5 will be here in no time. Pre-orders started at 12:01AM PST this morning and it's expected to start shipping in about two weeks. Verizon, AT&T, and Sprint are all handling unlimited data plans differently, so if you currently have an unlimited plan and are going to get the iPhone 5, you'll want to know what your carrier is doing before you upgrade so you don't end up with a very unpleasant surprise on your next phone bill. Verizon

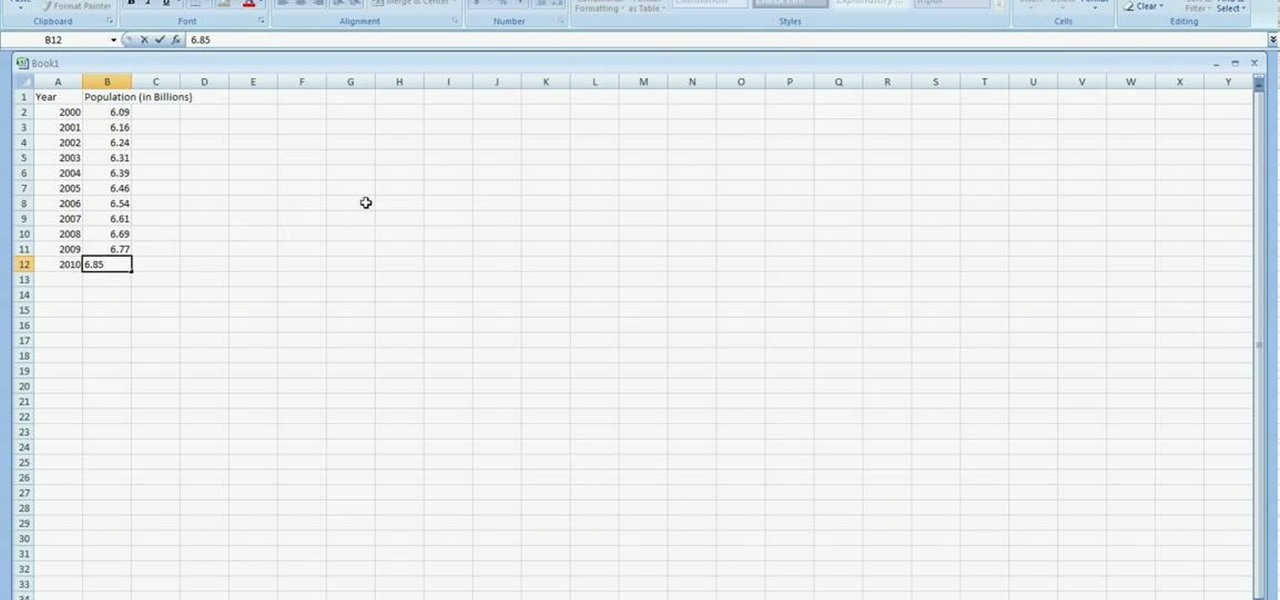
In excel a left click is made on box A1 and the X title is typed in as year. In A2 the year 2001 is typed and in A3 the year 2002. Both A2 and 3 boxes are highlighted and the bottom right hand corner is used to drag the work into a copied sequence down to A12. In B1 "population in billions" is typed. From the web site the data is copied and typed in as it appeared and the numbers are rounded off. A click is made on the "insert" tab and line is selected from the menu which appears. The upper l...

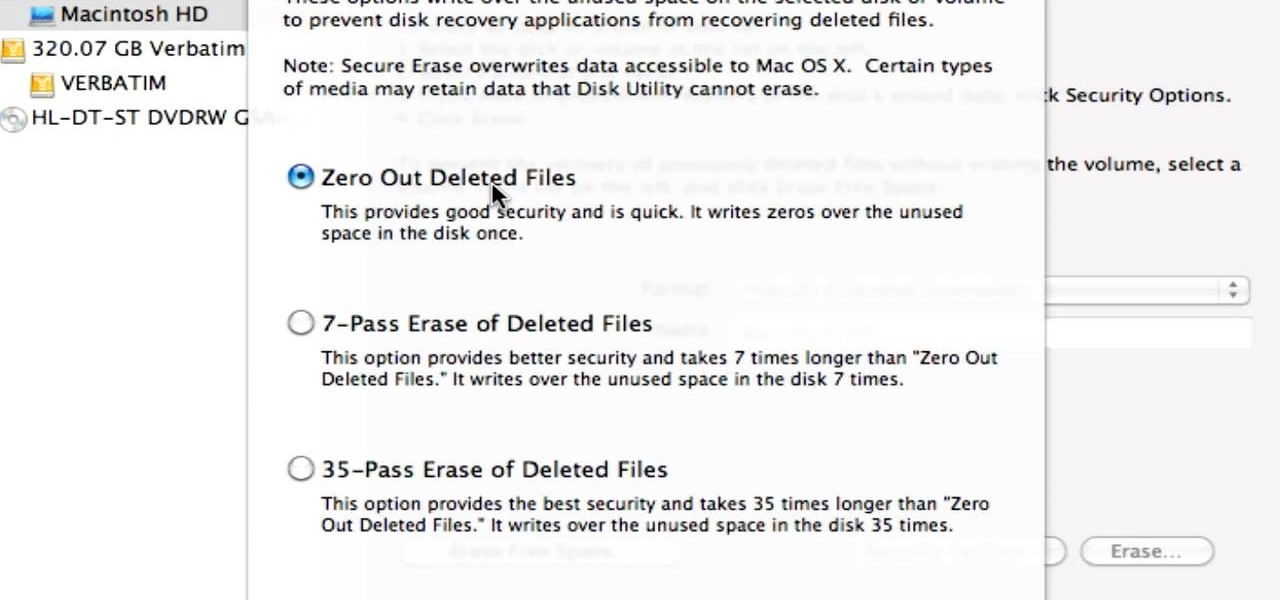
Did you know that even after you've emptied your Mac's trash can, the data still has not been permanently removed from your system? Anyone who knew where to look could easily unearth this data. You can prevent this by using the secure empty trash option on your Mac. Whenever you put something in the trash, instead of pressing delete, go into 'finder' up top and press 'secure empty trash'. What this will do is replace the data that is left behind on your hard drive with random ones and zeros. ...

Have you ever heard of tradigital art? Tradigital art incorporates traditional materials with digital media. This is a combination of such techniques as illustration with Decocolor Markers, Prismacolor Markers, pencils, and Photoshop. Watch this tutorial to learn how to enhance traditional art methods with digital media. It illustrates the tradigital process step-by-step. Make sure to pause the video after each step and look at the screen every few seconds while you are drawing.

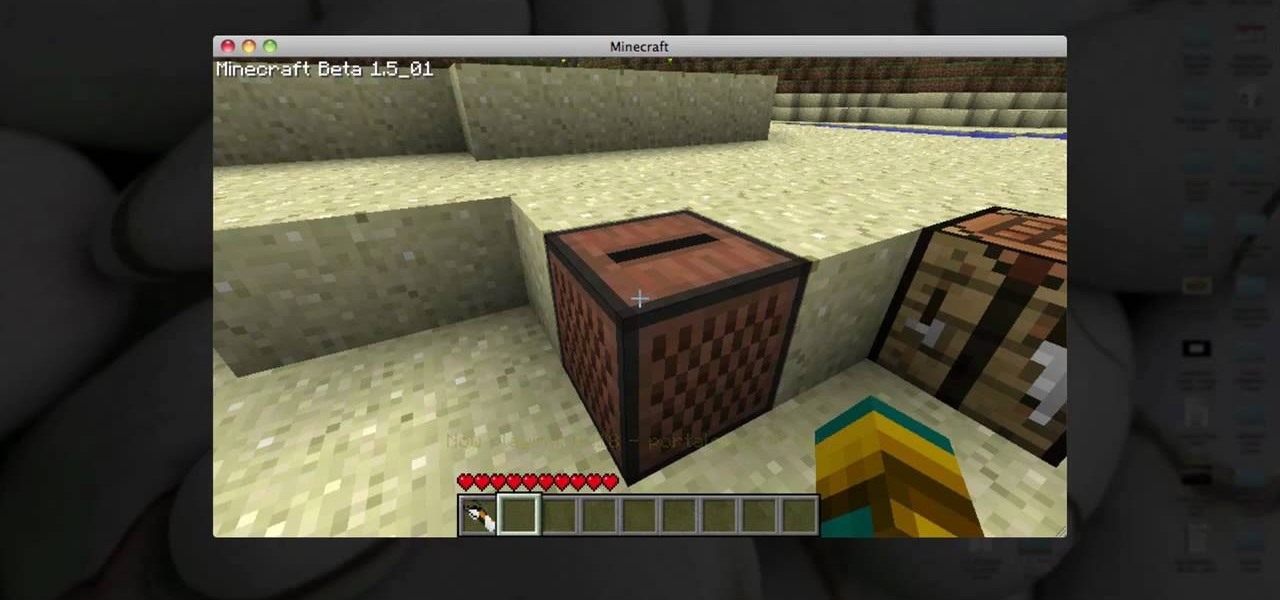
Looking to enhance your Minecraft experience with the Portal Gun mod? Start by watching this video. You'll have to download Modloader and Audiomod and the Portal Gun. Playing Minecraft on your Mac will just keep getting better. Have fun with the Portal Gun!

Filigree beads add a touch of intricate whimsy to any jewelry project. But if you're using run-of-the-mill metal filigree parts of one uniform color each time, then you're probably making necklaces and earrings that are more blah than impressive.

Okay, so you might not need a how-to for this one, but nonetheless, just in case, here you go— plugging in the data cable to your Samsung Galaxy Tab. It's basically the same way you plug in all mobile devices these days, and it's just like any other Android tablet, so you should be able to do it with little difficulty. Just don't force it in, or you risk damaging it and your device.