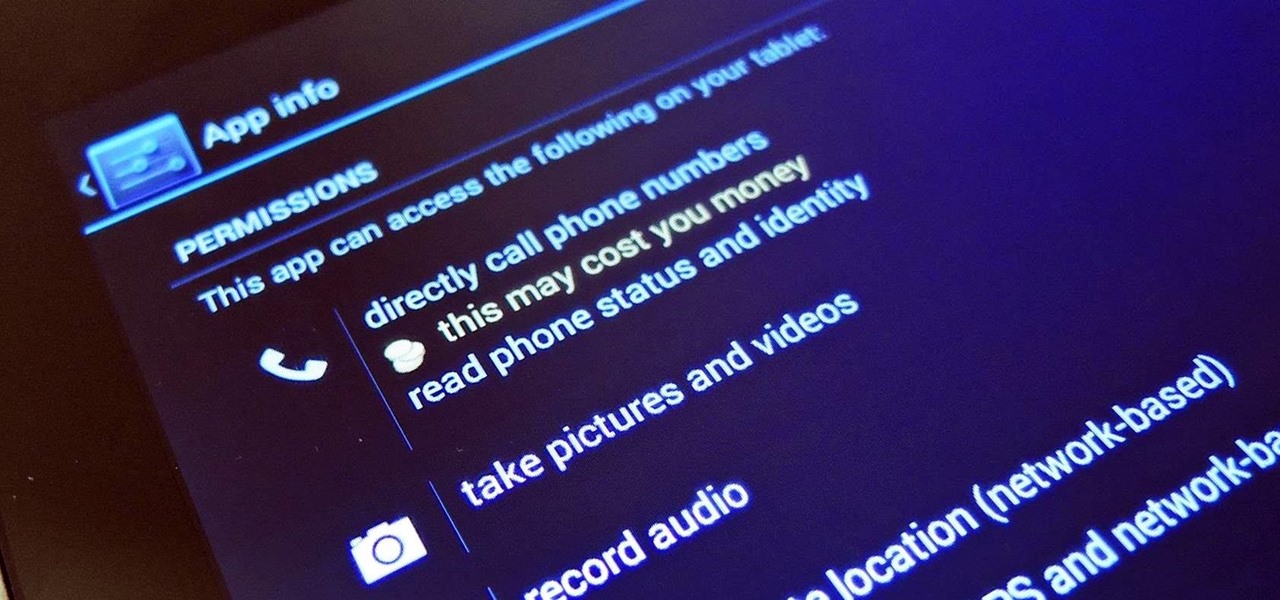
Samsung, like other OEMs, partners with third-party companies to include their apps on Galaxy devices. For example, Microsoft pays Samsung millions to pre-install certain Office apps. But one of these partners might not be on the up and up.

While modern browsers are robust and provide a lot of functionality, they can be unlocked to do some pretty spectacular things with browser extensions. For hackers and OSINT researchers, these tools can be used to defeat online tracking, log in to SSH devices, and search the internet for clues during an investigation. These are a list of my top ten favorite browser extensions for hackers — and how to use them.

While keeping your iPhone out of the bedroom might help to avoid unnecessary distractions before bedtime, it could be better served right by your side to help diagnose sleeping issues you may be experiencing each night.

Attention all Redditors: Between June 14 and June 18, Reddit experienced a data breach. The popular website claims it discovered the breach on June 19 and has since made the necessary moves to contain and eliminate the threat. Unfortunately, there isn't much they can do about the data was that accessed and stolen — your user data.

Most users don't realize how much valuable data is in their network traffic. With a few simple tools, an attacker can quickly pick out cookies, passwords, and DNS queries from a macOS device as it covertly streams the victim's network traffic to the attacker's system. Here, we will cover two methods for analyzing packets flowing from a Mac.

When BlackBerry made the move to Android OS, they were aware of the limitations it presented. Unlike with BB10, they didn't create the operating system and would have to deal with the vulnerabilities already included. As a result, they added numerous security enhancements, and at the heart of this is DTEK.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

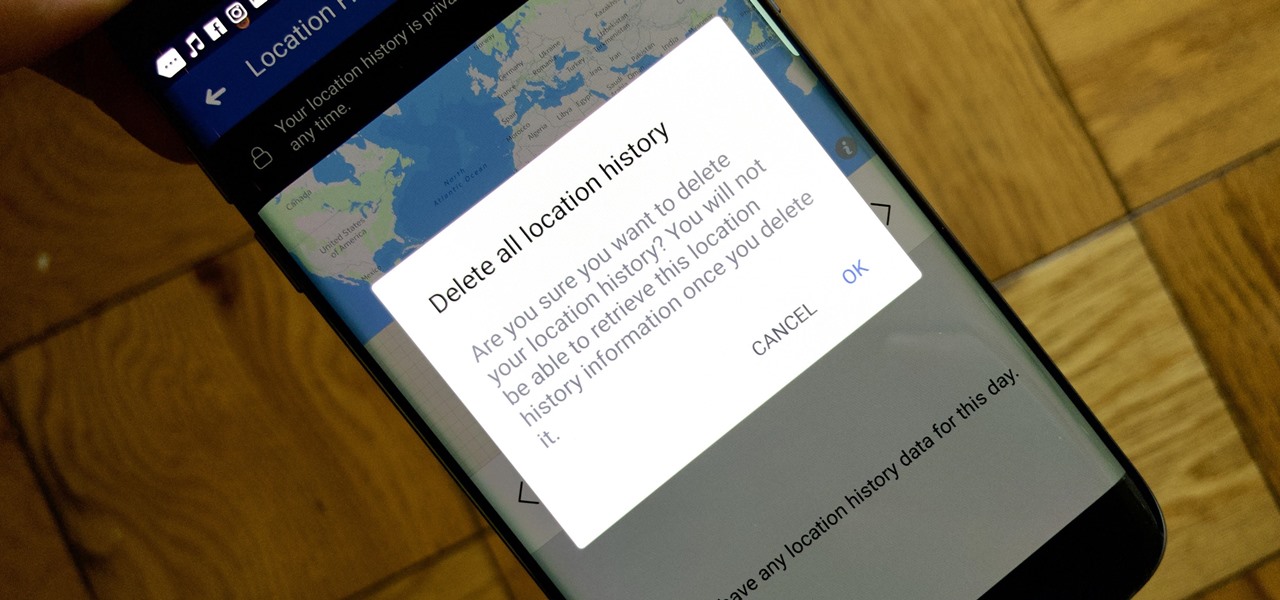
Facebook's shadiness when it comes to user privacy has never been much of a secret. The Cambridge Analytica scandal, however, has thrown the company and its practices into the limelight, with users taking their data more seriously than ever. If you're one of those users, you might want to check your "Location History" to see if and how Facebook's kept tabs on your whereabouts.

With over 1 billion downloads on the Play Store alone, Google Maps has become a staple for those traveling. Its popularity is the result of Google consistently improving its accuracy and adding new functionality. And this was only achieved with help of you — specifically, your data.

Google collects an enormous amount of personal data. While some of this data is used for targeted ads, others tidbits of info such as our location are used to improve our mobile experience. While it is natural for us to distrust Google's intentions, by allowing their data collection, we can add new functionality to our favorite apps.

When it comes to security, Apple is usually at the top of the pack when it comes to your personal data, minus a few embarrassing flaws here and there. However, a new iOS security concern has been discovered that protects your data less than it did before — and Apple designed it like that.

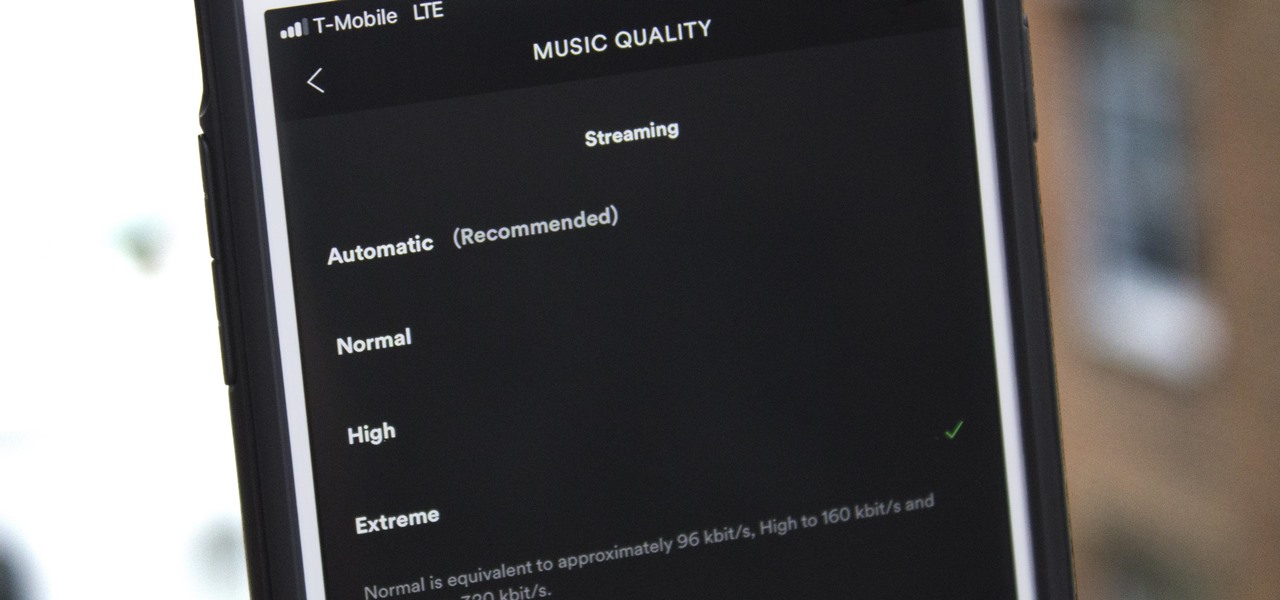
Spotify's massive song catalog can be streamed in decent quality on iPhone or Android without any tinkering. But if you're an audiophile, you've probably noticed that the sound quality can fluctuate from time to time.

Open-source data scraping is an essential reconnaissance tool for government agencies and hackers alike, with big data turning our digital fingerprints into giant neon signs. The problem is no longer whether the right data exists, it's filtering it down to the exact answer you want. TheHarvester is a Python email scraper which does just that by searching open-source data for target email addresses.

There have been a number of rumors about the iPhone 8 over the past couple of months, but the latest speculation about the device's dual FaceTime camera, that could take 3D selfies, has definitely grabbed our attention.
Hello everyone! This is my first attempt at a tutorial here. There are a couple great assembly tutorials here, and I wanted to toss my coin in the fountain.

There's a common bug that affects many Samsung Galaxy S5 users, myself included. The software that drives the fingerprint sensor can randomly fail to load, leaving you without one of the most unique features of your beloved smartphone.

Losing your phone is a much bigger ordeal today than it was just 10 years ago. Our smartphones carry with them lots of sensitive data that, in the wrong hands, is capable of being used for identity theft and fraud.

Welcome back, my greenhorn hackers! In a previous tutorial on hacking databases, I showed you how to find online databases and then how to enumerate the databases, tables, and columns. In this guide, we'll now exfiltrate, extract, remove—whatever term you prefer—the data from an online database.

Privacy has been a heated topic in recent months, with everyone now up in arms over unauthorized leaks and exposures. And guess what—tablet and smartphone users are just as vulnerable.

We don't generally think of medicine as being very relevant to Steampunk, but it was a big part of Victorian science fiction. Notable examples that you may be familiar with would be Frankenstein and The Strange Case of Dr. Jekyll and Mr. Hyde.

This video teaches us how to prevent those pesky paparazzi from invading our privacy. It suggests buying a pair of safety glasses that have lights attached at the sides. Then, remove the lights, and replace the existing resistors with higher-powered ones, and the lights with infrared LEDs. When the press tries to film you while you're wearing these at night, the cameras will see bright, menacing lights where your face should be. This how-to is presented as a joke, but it would be hilarious to...

Okay, we're going to be honest here and let you know up front that the eagle yoga pose ain't no walk in the park. In fact, unless you've already been practicing basic yoga for a while and have gained a decent amount of flexibility and strength you probably shouldn't even attempt this pose for fear of falling down.

Add depth to your 2D pack shots with the After Effects Vanishing Point tool! This video will teach you everything you'll need to know. Whether you're new to Adobe's popular motion graphics and compositing software or a seasoned video professional just looking to better acquaint yourself with the program and its various features and filters, you're sure to be well served by this video tutorial. For more information, including detailed, step-by-step instructions, watch this free video guide.

In this tutorial, we learn how to change your body features with makeup. To enhance the cleavage, you can purchase a product called Beautiful Breasts. You will first take the matte color and start to define where the breasts and cleavage are. Make the angles natural and make sure the makeup is blended so it's undetectable. Apply shimmer to the collar bone and shoulders to give a glow as well. The products work for any size and any shape and will give you extra enhancement. There is also a pro...

Are you planning to throw a big party soon and really want to surprise your guests with an unexpected and unusual food? Then this chicken kofta curry is just the thing for topping rice or couscous. Kofta just means a Middle Eastern or South Asian meatball, usually made from beef or lamb (though obviously the meat is chicken in this recipe).

Instead of picking up a Digiorno pizza from Albertson's tonight, try doing something a little different for a change. As many a good cook knows, fresh always tastes better, enhancing the overall flavor of your dish (not to mention offering heftier amounts of nutrients).

What's the difference between Kim Kardashian and January Jones? Both are clearly gorgeous women who have men drooling over them wherever they go, but these two starlets have very different body types.

In this video tutorial, viewers learn how to play glissando on the piano. This task is very easy, fast and simple to do. Glissando is basically playing all the notes of the piano. When playing glissando, use the tip of the thumb to slide down the piano. When going up the glissando, use the tip of the middle finger and slide it up the piano. The fingers might hurt at first, but you will eventually get used to it with the more you play the glissando. This video will benefit those viewers who en...

Are you a budding potter who's looking for a skilled tutor but can't afford taking pricey classes every week? Then watch this kiln conversion tutorial by master potter Simon Leach.

You know how in art class one of the main principles of drawing realistically is shading an object to establish its shape and contours? The same idea applies to makeup application. While our faces have natural dimension and contours, their hills and valleys can be further emphasized with strategic contouring via highlighters and bronzers.

In this video tutorial, viewers learn how to light-scribe with a Nimbie BB11 disc burner. This device is an auto disc loading system that allows the user to light-scribe multiple disc without manually inserting them one-by-one. Simply load the disc into the machine with the labels faced down. On your desktop, double-click on the Q-Q-Box icon to start the program. Start up the labeling function, select a desires image and quantity up to 100. Then click on Print. The machine will then product l...

In this video, we learn how to change the color of clothing in Photoshop. First, click "enhance", then "adjust color", then "saturation". Now place a magnetic lasso around the shirt color you want to change. You can now use a slider to go through all the different colors, and pick that one that you want to use in the picture. Play around with the saturation, hue, and brightness to change what the color looks like in the picture. If you want to add more contrast, it will look more real like it...

NTFS? What is it? It stands for New Technology File System, but what does that mean? Well, it's the standard system for filing in Windows NT, including all later versions, up to the current Windows 7, but Mac users can take advantage of this file system, too. If you’re confused when it comes to your hard drive’s format, this guide will show you the way to get the most out of your system.

There's nothing like spending time outdoors with loved ones. Whether it's a hot summer evening or a coo, brisk spring morning, the outdoors can be a great place. You can enhance your experience with the outdoors, by building yourself something that everybody is sure to love: a fireplace. In this helpful tutorial, you'll be finding out how to build an outdoor fireplace in your yard for those cold winter nights. So good luck and enjoy!

Getting the perfect shot is difficult, so when you finally get that perfect picture of yourself, you want to enhance it as much as possible. But if this perfect picture took place in a humdrum location like the bathroom or your living room and you want to glorify your face even more by surrounding it with, say, an island paradise, you can transplant your head (and body) using Photoshop.

Popularized by the likes of Andy Warhol, pop art has long been an art genre associated with the glittery excesses of Studio 54 and a modern aesthetic.

CSTools are free plug-ins that are available for your Cinema 4D application. In this tutorial, Nick will show you how to use the plug-in called Flicker. Flicker is a fun add-on, although you may not use it often. It can be used to add a "flicker" to things like campfires, candles, lights, etc. So, if you need to enhance some light effects in your program, check this out.

Many schools of makeup teach that one should use makeup only sparingly, flattering her face with neutral tones that enhance without obscuring. But one school teaches that, like Oscar Wilde, one should paint the body with diamonds and exude raw flamboyance.

Photoshop is capable of doing so much in such a single program, it's amazing. You can easily create images as well as edit and enhance some of your own photos. But another great thing is that you're able to save certain files a certain way, that you couldn't normally do without using Photoshop. So in this tutorial, find out how to make a hdr image (high dynamic range) from a single raw file. Enjoy!

Photoshop is one of the most powerful and widely used program out there on the market. Not only can people use it to make their own photos look better, but they are able to take other pictures and images and enhance them to whichever way they want. That can be seen as both bad and good. Somtimes, to do so it involved using the layers and moving a picture to a new image. In this tutorial, you'll find out how to move a layer to a new image using Photoshop. Enjoy! It's quick, easy, and will be a...