All of the new iPhones from 2018 were released with dual-SIM support, but none of them were capable of actually using the eSIM in iOS 12, only the physical nano-SIM. But on iOS 12.1 and later, you can finally take advantage of eSIM so you can have, say, a business and personal plan on your iPhone XS, XS Max, or XR at the same time.

If there's one strength of Apple's that iOS and Android fans can agree on, it's the company's dedication to user privacy. With each new iteration of iOS, Apple builds upon these foundations, enhancing and increasing each iPhone's ability to protect its user's data. In iOS 12, Apple has added many new features to Safari, most of which have their own unique way of keeping you safe online.

Net neutrality is dead and your internet service providers can collect all the data they want. While VPNs are a great way to protect some of that privacy, they're not perfect. There is another option, though, called Noisy, which was created by Itay Hury. It floods your ISP with so much random HTTP/DNS noise that your data is useless to anyone even if they do get it.

While privacy and security are cornerstones of Apple's ecosystem, your iPhone isn't bulletproof. Creating a strong passcode will protect you from most threats, but there exist tools that can break through even the toughest passcodes via the Lightning port. Luckily, Apple has implemented a new security feature to disable your Lightning port and keep your data safe and secure.

There are a number of options and hidden menus within Android that provide users more control over their device. With this control, you can better manage how your phone operates. We came up with a list of tips and shortcuts that, when used, will slowly put you on a path to becoming an Android power user.

Although the HoloLens is still primarily the domain of developers and researchers, the device is nevertheless on the cutting edge of showing us what will be possible with augmented reality in the coming years. The latest example comes via Microsoft Japan and a new concept video that shows off how the HoloLens will be used in the relatively near future to pilot autonomous ships.

The augmented reality and VR arm of Verizon, Envrmnt, wants to make it really easy for anyone to create AR apps.

Your email inbox is a treasure trove of personal data. The people you contact, your writing style, which messages you flag as spam — all of this information and more can be used to paint a clear picture of you. Google knows this as well as anybody, so they use this data to constantly improve your experience in Gmail.

Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a buck at the expense of your privacy.

Although The New York Times may have won the race in terms of presenting coverage of the 2018 Winter Olympics through augmented reality first, The Washington Post is nevertheless working to compete in AR in a different way—via gaming.

Unlike many browsers, Firefox gives a lot of control to the user. By default, Firefox does a great job of balancing security and performance. However, within the app's settings, you can modify options to shift this balance in one direction or another. For those looking to shift it toward security, here are few suggestions.

As smartphones become more accessible, billions of people have come to depend on their features for daily life. One of the most important aspects these days is the camera. OEMs have been working for years to improve camera quality, and they seem to have finally figured it out — the best way to achieve DSLR-quality photos wasn't just with better sensors, but with better intelligence.

As smartphone users, we live in dangerous times. The value of phones continues to rise, making them prime targets for thieves. In 2015, the FCC estimated that one million phones are stolen each year, and with several devices starting to hit the $1,000 mark now, these numbers are sure to rise. But what do you do if you fall victim to phone theft?

The Franklin Institute is rolling out the augmented reality carpet for the arrival of the Terracotta Warriors of the First Emperor exhibit, which will open on Sept. 30 in Philadelphia.

With so many apps being cloud-based, cached data has started to become a problem. This is particularly true if you're low on storage, so developer Dhi decided to do something about it.

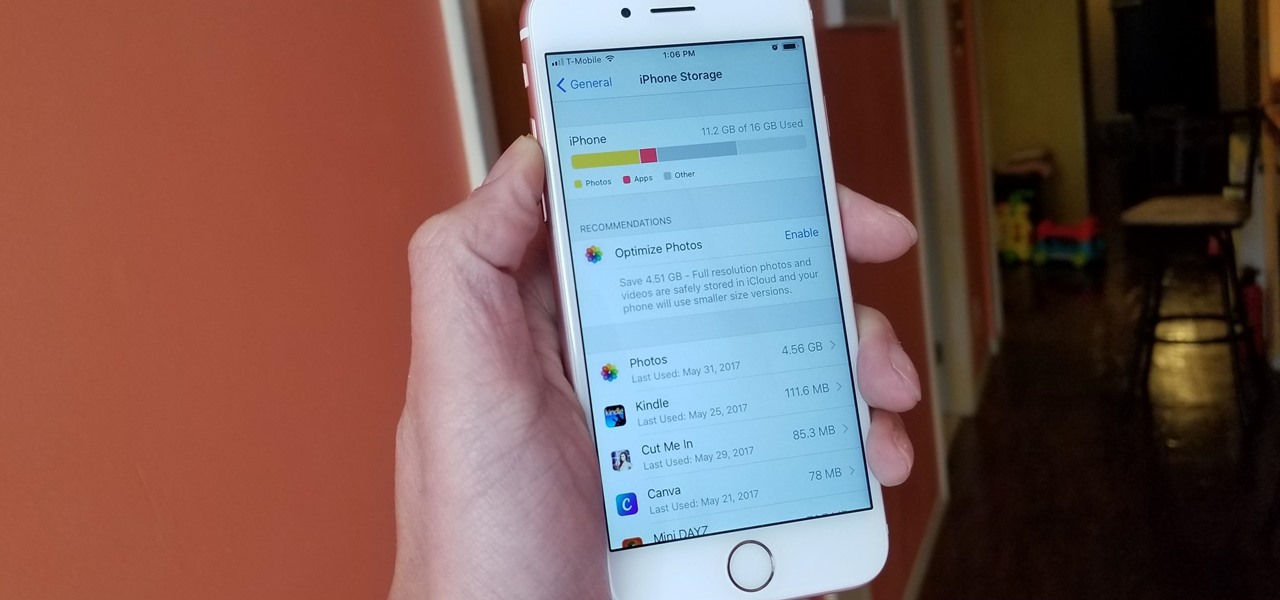
When Apple revamped the storage management system in iOS 11, it built in a feature that lets you free up space on your iPhone in a more efficient manner. The option allows you to remove an app while preserving its data and documents should you choose to reinstall it later — and it can even do so automatically for unused apps when you're running out of space.

Over the past week, we are seeing more companies capitalizing on services leveraging augmented reality. One company secured funding to expand their service, while two other companies grow its own services through acquisition.

Most of us skip through documents like privacy policies and EULAs (end-user license agreements) because they're long and boring. But, as Congress just passed the SJR34 bill in early April, you're probably a little concerned about your personal data, so we summarized the privacy policies for major ISPs and mobile carriers in the US.

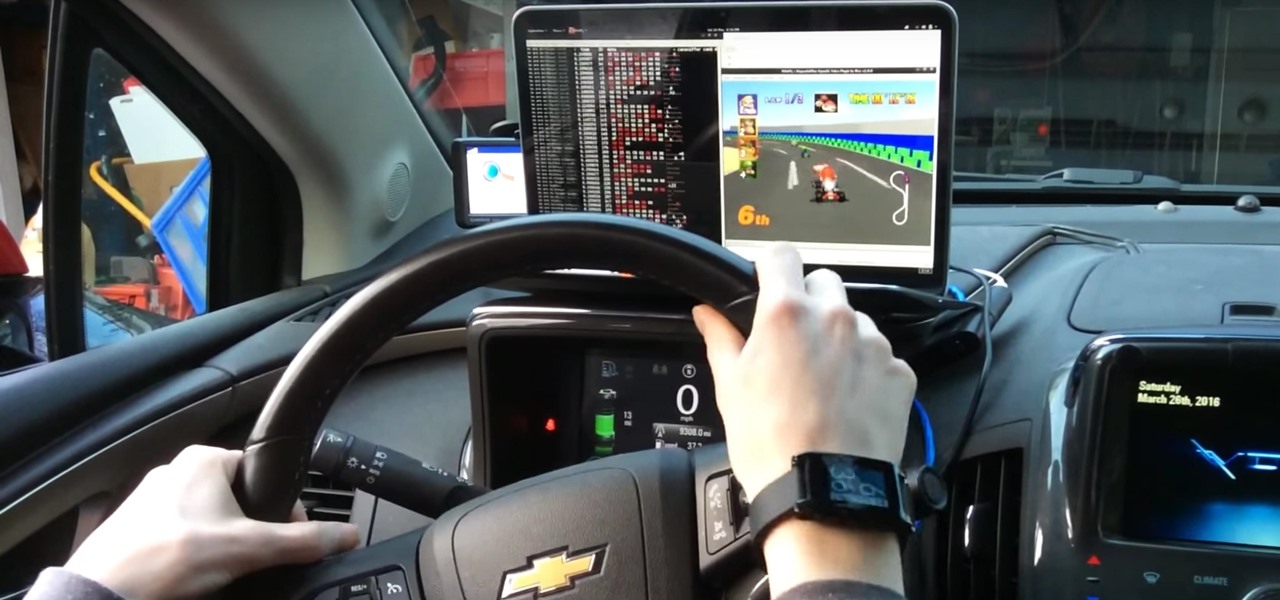
Oh, Mario. The guy that's been a part of our lives since as long as we can all remember. Well, Adam Ringwood and his friends did something pretty cool with one of Mario's most exciting games at the HackIllinois event in February 2016—they hacked a Chevrolet Volt's steering wheel into one big Nintendo 64 controller for Mario Kart.

Hey guys, in this tutorial, we are going to learn about the heap segment and how to use it for storing data in our programs. We will also go into the details of its use in conjunction with the char pointer and struct data types.

You've probably heard the old joke about how Ford is an acronym for "Found on Road Dead." Well, the Detroit automaker on Monday announced a new and much better way to help you find your parked vehicle, as well as a whole host of other features—just use your smartphone.

What's up readers? Today I'll be introducing to you a new vulnerability called the Format String vulnerability (in case you missed the title). It won't be much, just a little motivation to keep you guys going. A little teaser, if you may.

Samy Kamkar, the security researcher known for the MySpace Worm and his combination lock cracking skills (using an online calculator), is back—and this time, he's after your credit cards!

Video covering how to set up a Venn diagram. The video covers how to draw the diagram and then look at a set of data and place the data in the correct part of the Venn diagram. The sample problem is as follows.

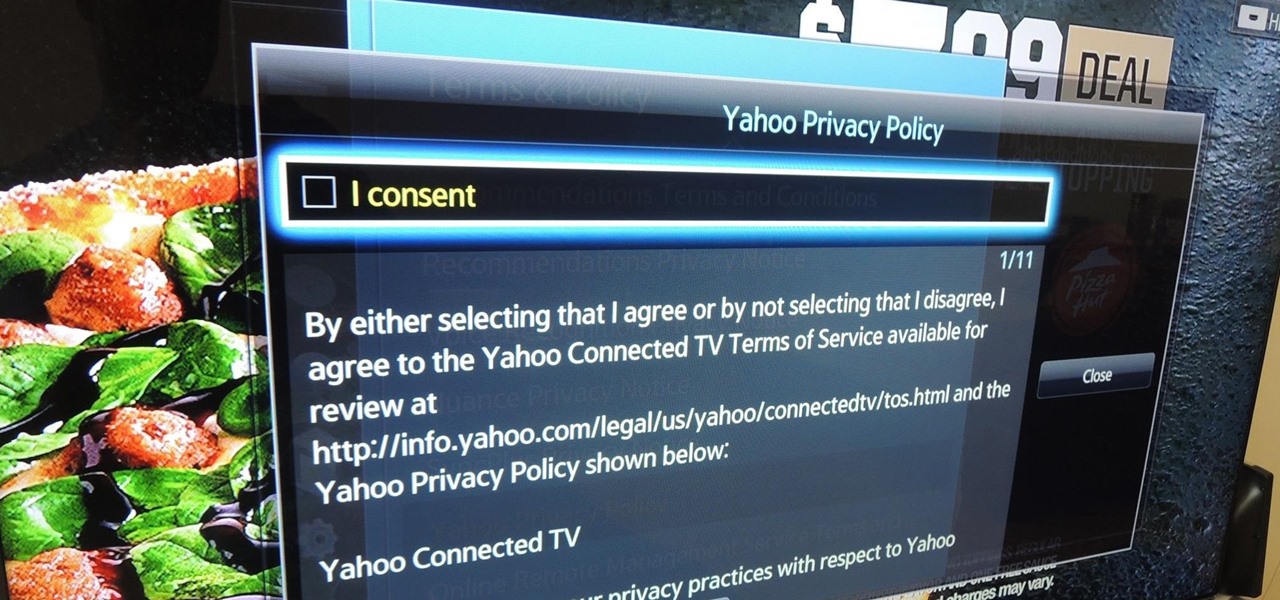
Televisions used to be great for just one thing—watching TV. But a more connected world brought with it Smart TVs, devices that can access the web, stream Netflix, and even mirror your smartphone's display. And with this level of connectivity, OEMs like Samsung saw it fit to place targeted and interactive ads on your screen.

For people that live outside of the United States, how many times has this happened when surfing through U.S. streaming services? If you're outside of the U.S. market and want to stream stateside services like Hulu, MTV, CBS, Pandora, and others—you're in luck. Tunlr is an application that re-addresses certain data envelopes, tricking the receiver into thinking the data originated from within the U.S. by using its own DNS server's IP address. You can even watch some non-US shows stateside, li...

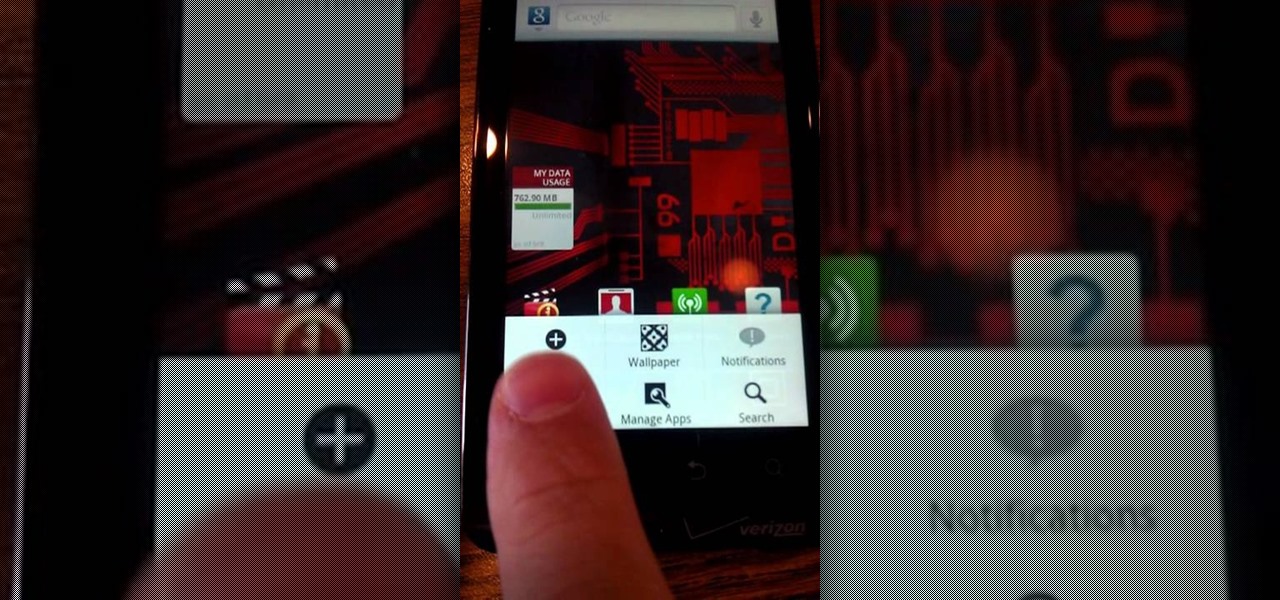
Verizon Wireless has a data cap on the 4G LTE connection that the Motorola Droid Bionic uses to connect to the internet and download information from its apps. If you want to stop your phone from hitting these caps and causing you overage fees, you can turn off the 4G connection by looking at this guide. It will save your smartphone's battery life as well!

If you are looking for a data storage solution that's portable, but also durable, you should watch this video to learn how to build a USB hard drive. Take apart your external hard drive to find out what kind it is and then build a new one.

In these days of mobile technology, losing your iPhone or iPod Touch is almost worse than losing your car keys. It becomes one of the most frantic searches you've ever had to endure. But you can relax now, because you can use Apple's Find My iPhone, iPad or iPod Touch service to locate your lost device.

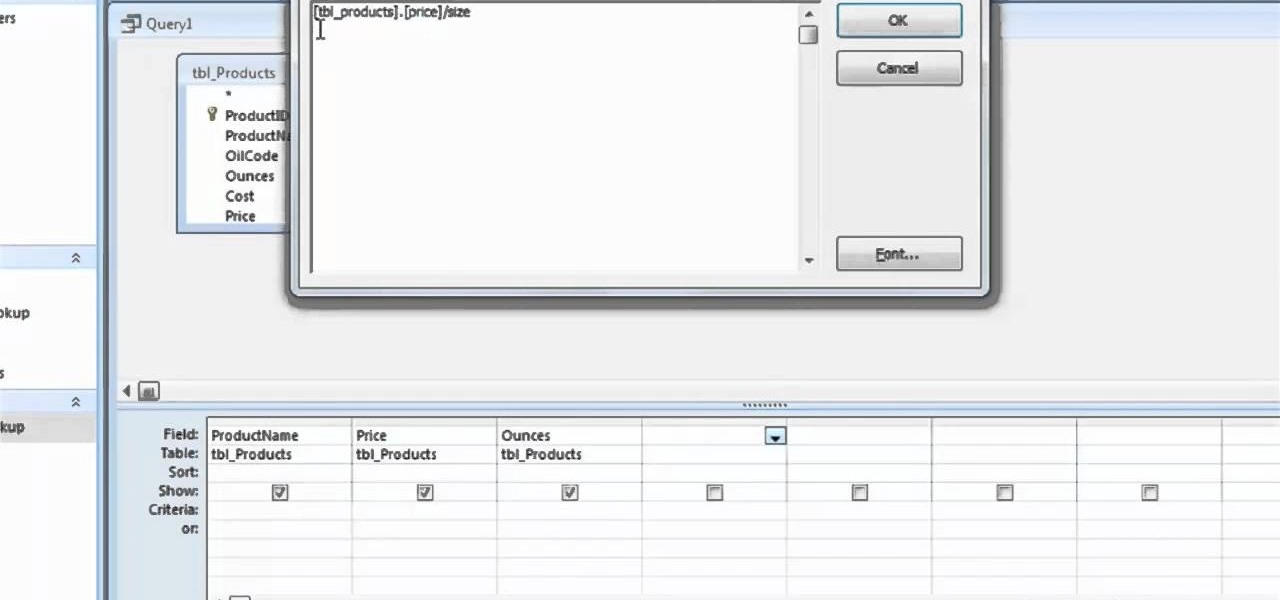
In this clip, you'll learn how to employ mathematical operators when running queries in MS Access 2007. Whether you're new to Microsoft's popular data management application or a seasoned MS Office professional just looking to better acquaint yourself with the Access 2007 workflow, you're sure to be well served by this video tutorial. For more information, including step-by-step instructions, watch this free video guide.

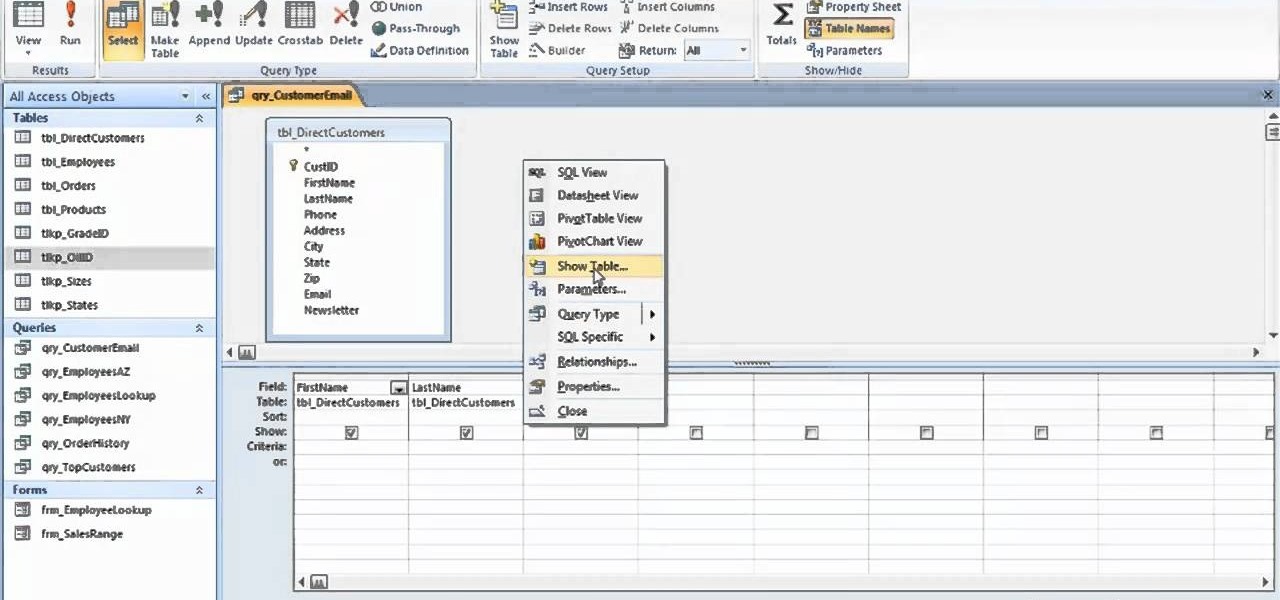
In this clip, you'll learn how to take advantage of the Microsoft Access QBE interface. Whether you're new to Microsoft's popular data management application or a seasoned MS Office professional just looking to better acquaint yourself with the Access 2007 workflow, you're sure to be well served by this video tutorial. For more information, including step-by-step instructions, watch this free video guide.

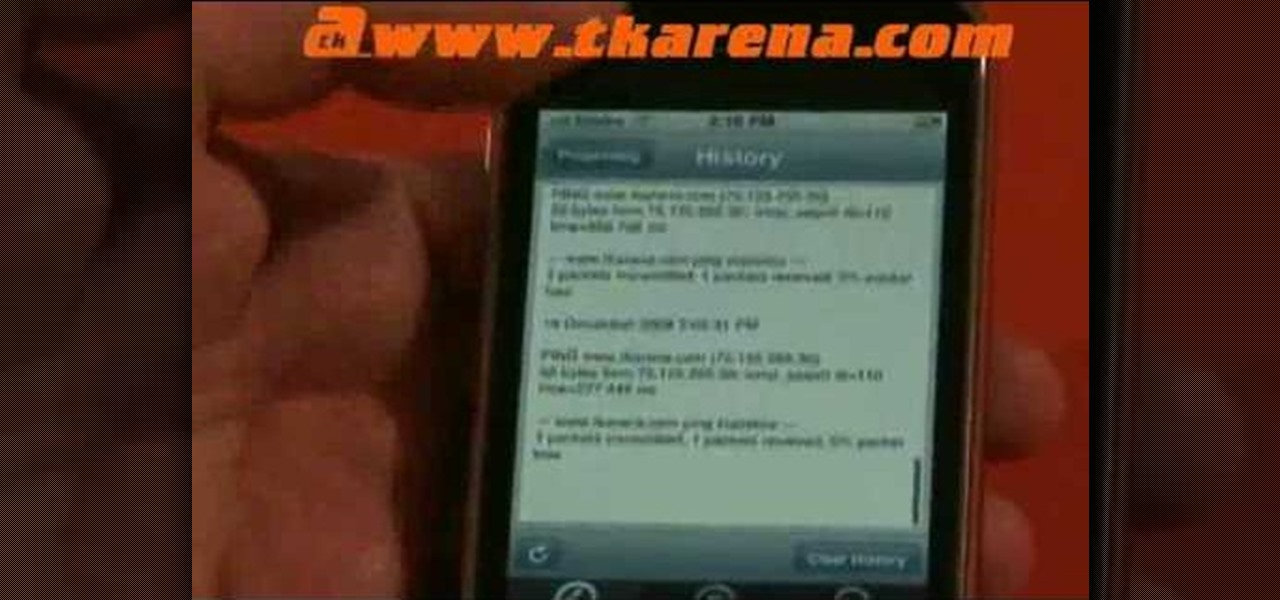
A great tool for any system administrators, the iPhone (or other Apple wifi device) app Ping a Majig allows you to enter in the IP addresses of websites. Then you can keep checking on them to make sure they are running smoothly and operating correctly. You can click on the website for more data regarding pings and site health.

Cordell Connect is useful software for managing projects for your business. One of the functions of this program is being able export your reports to either an Excel spreadsheet or a PDF document for a greater ease of data manipulation and communication.

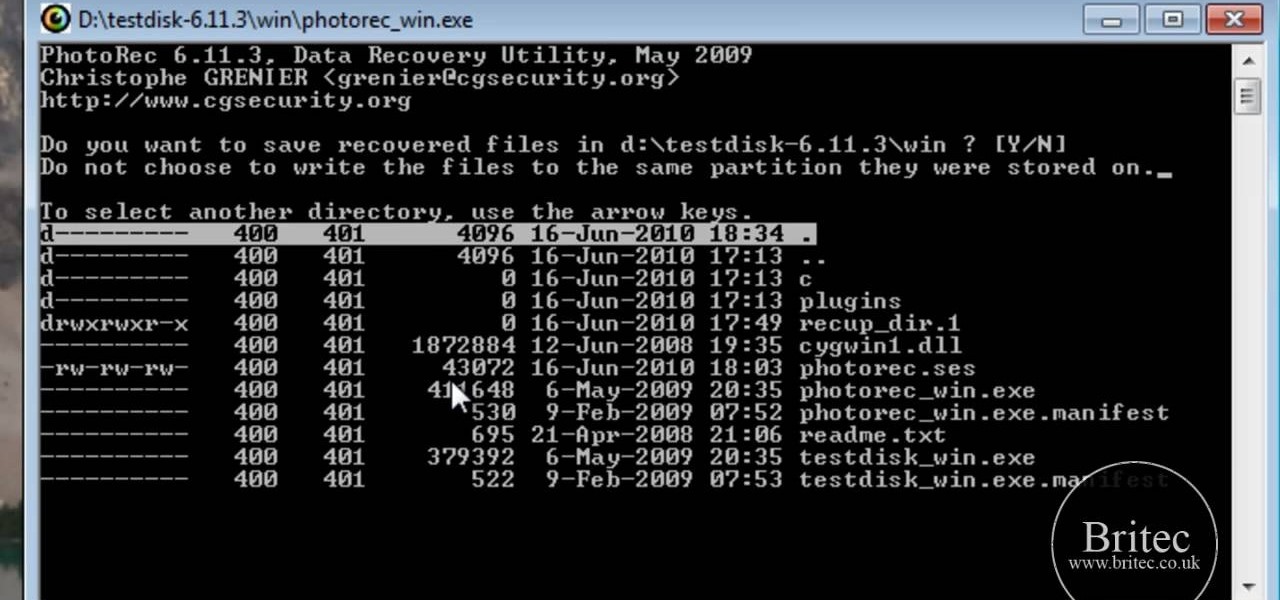
Looking for instructions on how to use TestDisk to recover files from a formatted hard drive on a Microsoft Windows PC? It's easy! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over six minutes. For more information, including step-by-step instructions, take a look.

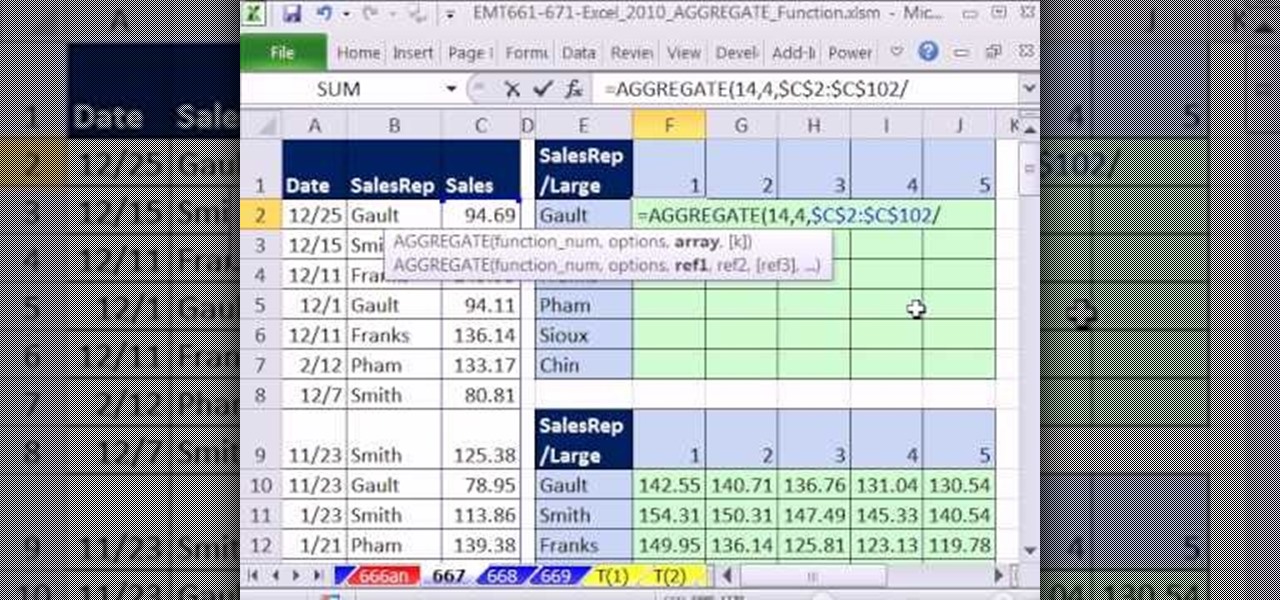
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 568th installment in their series of digital spreadsheet magic tricks, you'll learn how to calculate the five largest values for each a data set using the new AGGREGATE function.

Want to delete your data once and for all? This clip will show you how it's done. It's easy! So easy, in fact, that this home-computing how-to from the folks at Butterscotch can present a complete overview of the process in about three minutes' time. For details, and to get started erasing your own PC hard drive, take a look.

In this clip, learn how to trade phones and iPads back and forth by customizing your SIM card. This video will walk you through how to size and cut your SIM into the right shape for different devices. By customizing your chip, you will be able to move your data from one device to another with no problem. Use your old 3G SIM in your new iPhone 4 with this awesome hack.

In this tutorial, you'll see how easy it is to bring your footage into PFTrack and then quickly take that data into Cinema 4D to begin to add your elements. Whether you're new to MAXON's popular 3D modeling application or are just looking to get better acquainted with Cinema 4D and its various features and functions, you're sure to enjoy this free video software tutorial. For more information, including complete instructions, watch this 3D modeler's guide.

In this tutorial, learn how to mod your MW2 game into split screen using your PC and a data transfer cord. This clip will show you step by step how to get up and running with this neat modification.

Want to share your Windows Mobile phone's high-speed data connection with your laptop over Bluetooth? It's easy! So easy, in fact, that this home computing how-to from the folks at CNET TV can present a complete (and somewhat talky) overview of the process in just over a minute's time. For the specifics, and to get started tethering your own Windows or Mac laptop to your Windows Mobile phone, just watch this handy how-to.