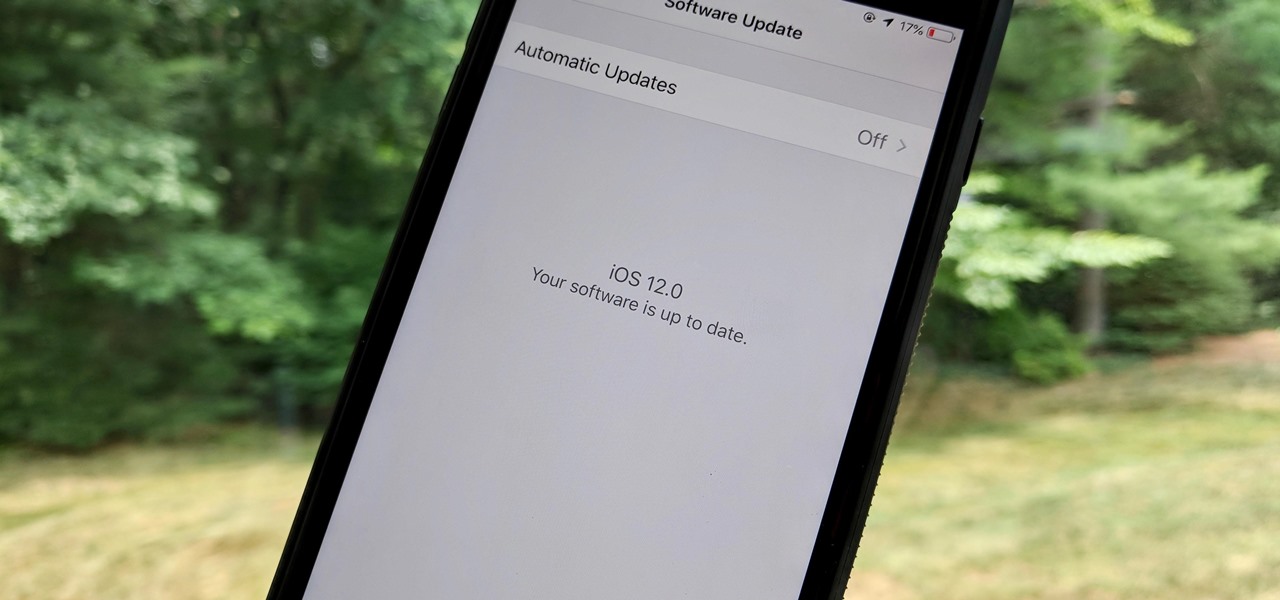
As the official release of iOS 12 nears closer each day, Apple continues to update its betas. The company released the fourth beta of the upcoming software to developers Tuesday, July 17, exactly two weeks after the release of the third developer beta which came out just a few days before the second public beta.

If you are an active player of Pokémon GO, you may soon be capturing more than just virtual pocket monsters.

Ever since the announcement of The Walking Dead: Our World game last fall, publisher AMC and developer Next Games have been quiet about the title. Almost too quiet.
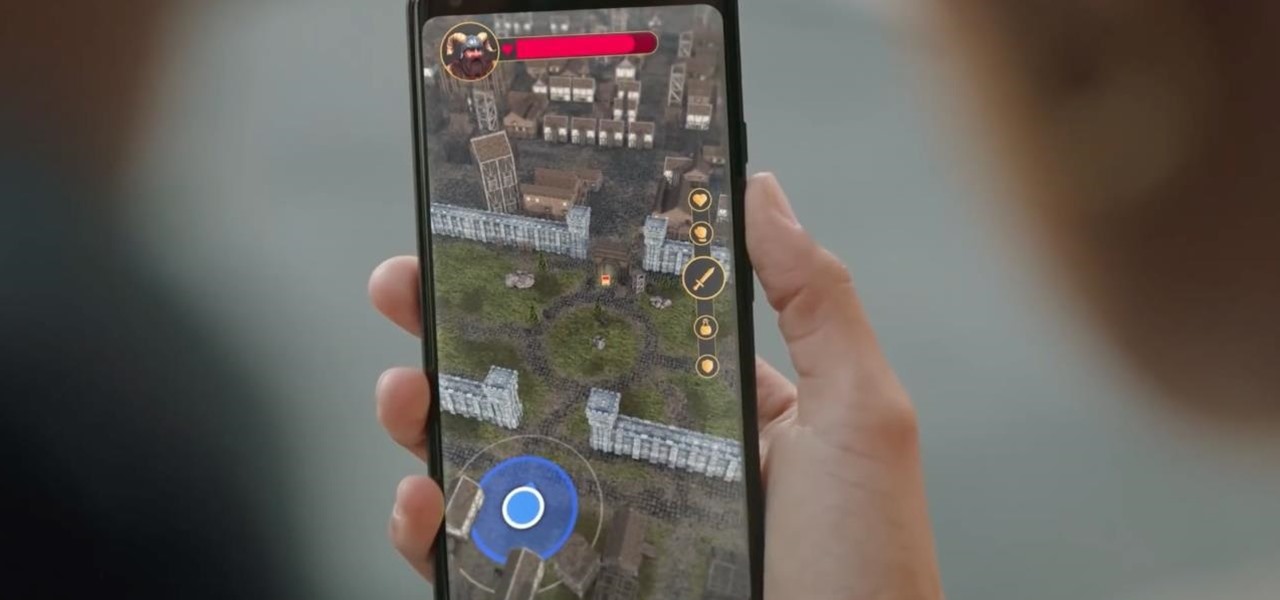
Franchises left and right are releasing Pokémon Go-style augmented reality games, and Google is making it even easier to churn out the apps.
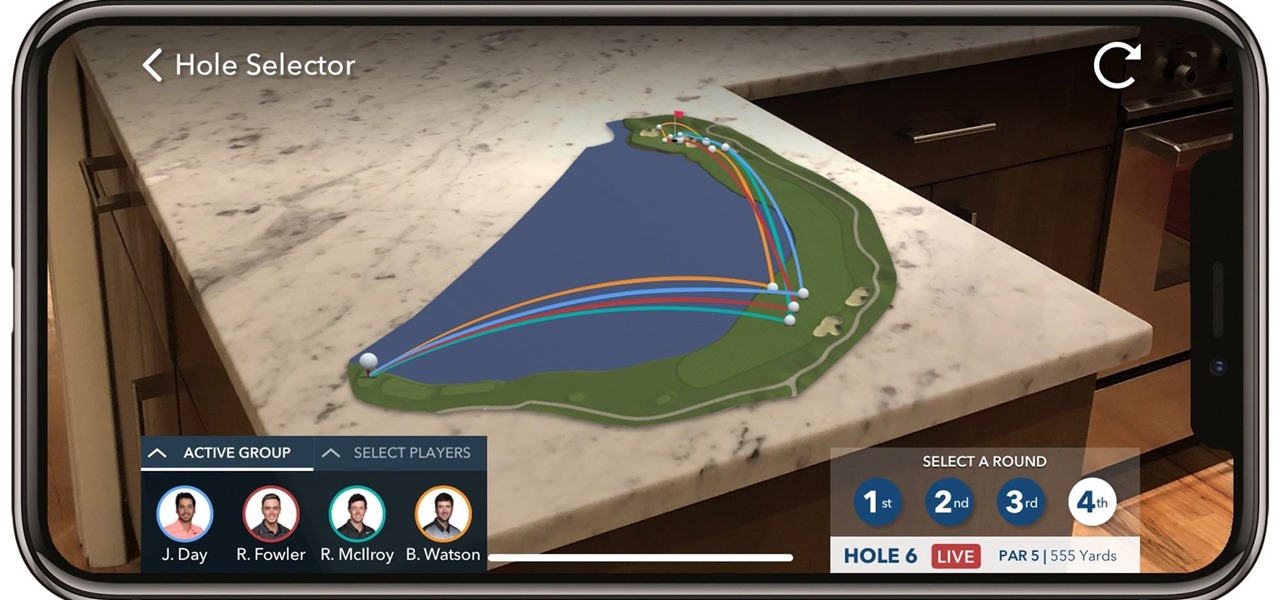
If you're a golf fan who can't attend the Arnold Palmer Invitational in person, you can still follow the next stop on the apparent Tiger Woods comeback tour in augmented reality with an iPhone or iPad.

After two years of poor sales, LG decided to shake up its mobile division. New executives are at the helm, and changes to their flagship lineups are already underway. Specifically, the V series is expanding, as LG announced the second new device in the series, the LG V35 ThinQ.

As the third-largest smartphone manufacturer in the world, Apple devices are a constant target for hackers everywhere. While iOS has seen fewer common vulnerabilities and exploits (CVEs) in recent years, iPhones still aren't hack-proof. Fortunately, you can strengthen your security with the help of a few apps.

Format strings are a handy way for programmers to whip up a string from several variables. They are designed to save the programmer time and allow their code to look much cleaner. Unbeknownst to some programmers, format strings can also be used by an attacker to compromise their entire program. In this guide, we are going to look at just how we can use a format string to exploit a running program.

As the level of data being generated grows exponentially, past the Information Age and into the coming Hyper-Information Age of immersive computing — as resistant as many of us are to the idea — personal data security is becoming a necessary consideration in our everyday lives. Recognizing this, Mastercard, Qualcomm, and Osterhout Design Group have teamed up to show what secure shopping could look like in the very near future with iris authentication.

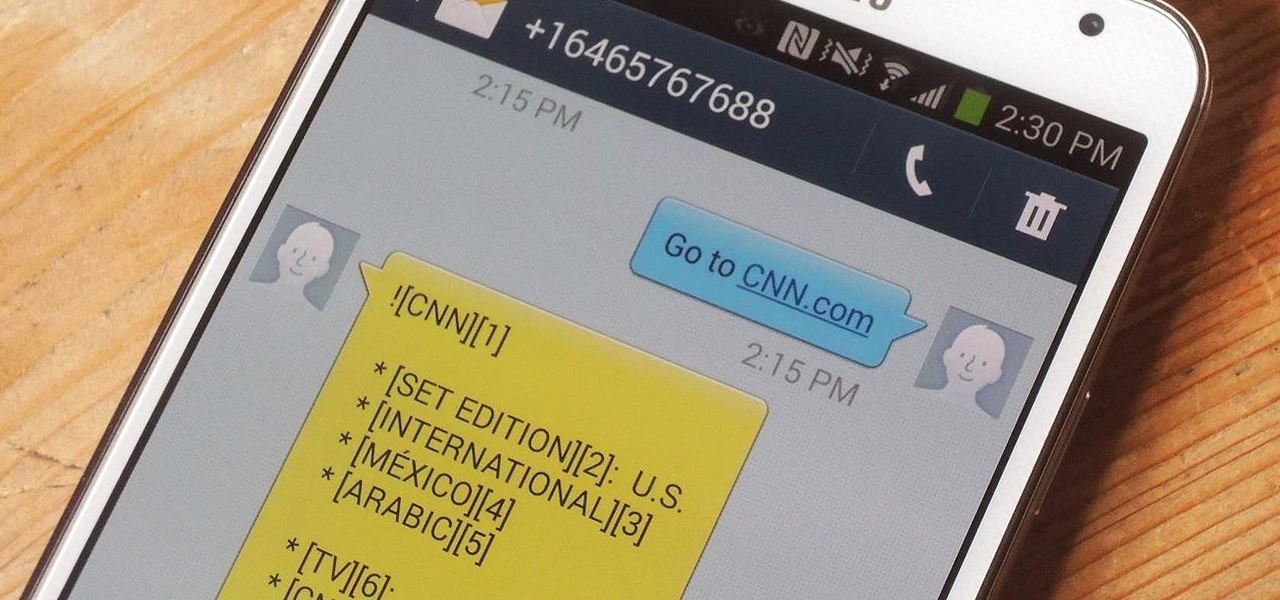
Due to the overnight success of smartphones, millions of people are connecting with others. Currently, over 15 million text messages are sent every minute worldwide. Most of this communication is happening in the open where any hacker can intercept and share in the discussion unbeknownst to the participants. However, we don't need to communicate insecurely.

Apple took a giant step forward in terms of user customization with the new Control Center in iOS 11. With an improved design, buttons you can pick and choose from, and even a new default Cellular Data toggle, it's definitely a better iPhone experience. However, Apple also took a giant step backward with the confusing Bluetooth and Wi-Fi toggles.

Spotty cellular reception is a fact of life that we all have to deal with, especially when you're traveling. For those of us who rely on our smartphones for navigation, driving through areas with bad mobile data service can be a cause for major headaches.

Mixed reality developer Arvizio has updated its MR Studio software suite to integrate processing of 3D light detection and ranging (LiDAR) point clouds.

The OnePlus 5 had been in the hands of the public for a meager twenty hours before developers on XDA released a custom recovery image for it, and the 5T had a similar trajectory. The installation process is simple enough, but it can be somewhat confusing if you're new to modding Android.

Apple's been hard at work adding new features and finishing touches to iOS 11, and there's evidence of it everywhere. But there's one place where these changes are more noticeable than perhaps anywhere else — Safari.

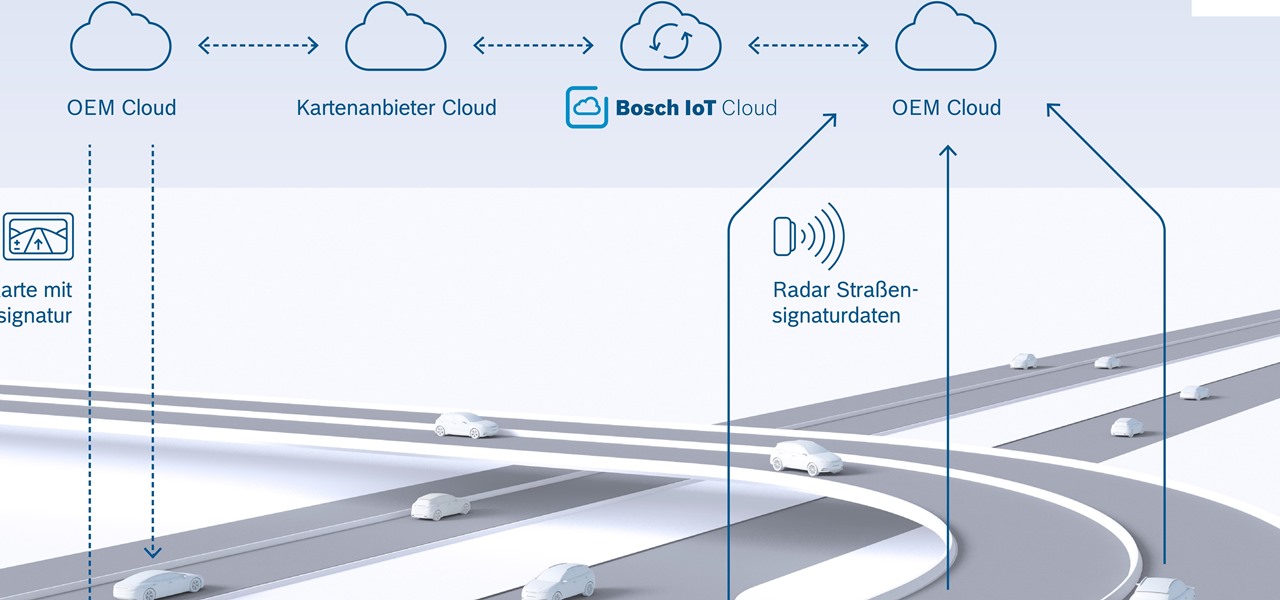
New "radar road signature" technology from Bosch will be used to create maps for high-accuracy self driving. The new map is the first to use radar signals for a localization layer.

Today at Microsoft Build 2017 in Seattle, Washington, ScopeAR announced that their mixed reality smart instruction development platform, Worklink, will now work with the Microsoft HoloLens in addition to the mobile devices that are currently supported.

Whether you're a professional mechanic, a hobbyist, or someone who just wants to know why their check engine light came on, your Android device and an OBD-II adapter can provide insight as to what's going on with your car. Most adapters sell for less than $10, and once you plug it into your vehicle, you'll just need a good app to help you make sense of all the data it can gather.

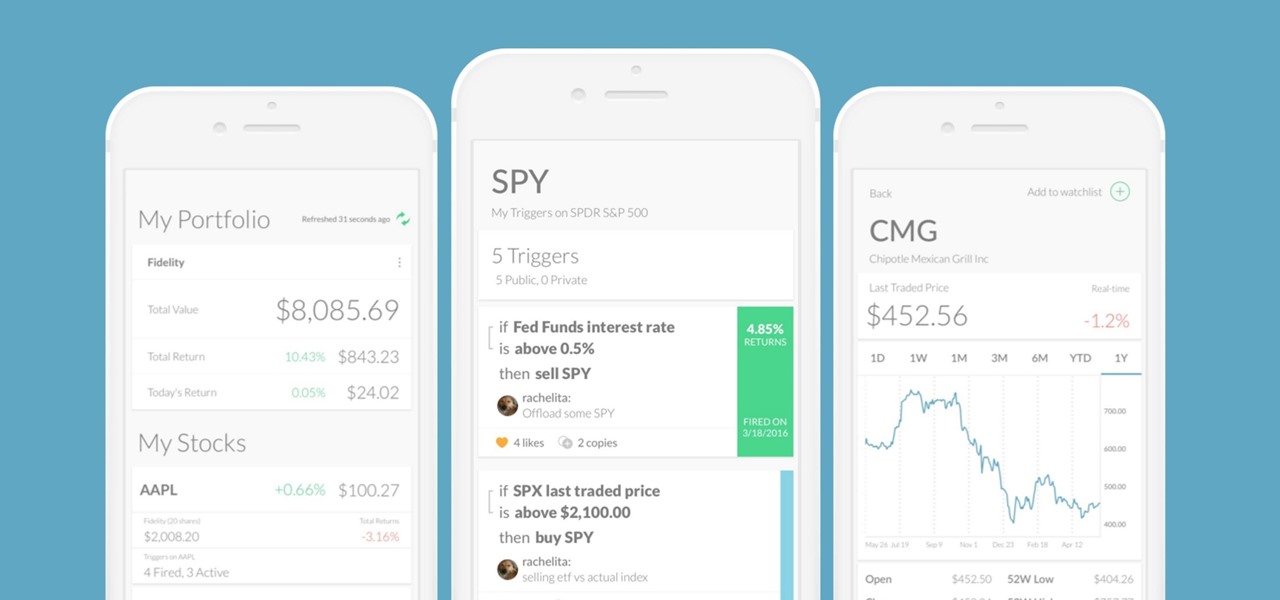
Every time Donald Trump tweets about a stock you own, Trigger Finance, or just Trigger—the app founded on the "if this, then that" rule to track and invest in the stock market—alerts you with a notification for real-time analysis of financial data.

The V20 is an amazing phone from LG powered by Android. Packing impressive features such as a removable battery, expandable storage, and the latest Android version straight out of the box, the V20 is a tough phone to beat.

Immigration and immigration policy are some of the biggest discussions happening in international and domestic politics right now. From building walls to opening borders, a definitive plan has not been made about how to deal with the large number of people who are fleeing their home countries in hopes of a different life.

As we reported first here on Gadget Hacks, the Google Pixel and Pixel XL have unlockable bootloaders, with the exception of models purchased from Verizon. This means that once the TWRP custom recovery is installed, you can flash ZIPs and even root your device in a few taps—as long as you unlock the bootloader beforehand.

Microsoft has the HoloLens and Google has their money on Magic Leap (as well as their own Tango and Cardboard, among others), but we've heard next to nothing about how Apple plans to enter the virtual/augmented/mixed reality space. A new patent offers some clues.

Welcome back everyone. I apologize for the lack of training articles, but I've been rater busy lately. I've recently picked up a second job and my college courses are now back in session, so I'm a bit strapped for time.

Google dropped its opposition to T-Mobile's Binge On service due to some favorable policy changes at the magenta carrier. From now on, YouTube and Google Play Movies will happily work with the feature. Binge On rolled out late last year, allowing many customers to receive unlimited video streaming at 480p. That's not a great offer if you care about video quality, but it's nice if you want to save money.

The Android Nougat preview build for Nexus devices comes packed to the brim with new functionality: multi-window mode, a dark theme, and a data-saver toggle, just to name a few. However, unless you have a Nexus device, it will be a while before you get these exciting new features by default.

Hello there! This will probably be the final tutorial on functions where we will be looking over a method called pass by reference. This technique allows us to modify large amounts of data without the overhead and return multiple values. Let's go!

Smartphone cameras are so good nowadays that there's almost no reason to own a point and shoot. Once the megapixel spec race was finally settled (hint: more isn't always better), manufacturers started focusing on the quality of their camera sensors, which has led to a huge jump in color accuracy, dynamic range, and image clarity.

If your iPhone can't last a full day without being recharged multiple times, something's wrong—but it might just be working harder than it needs to.

If you've just ditched your Android phone for a new iPhone, you're in luck, because Apple has a way to make your transition as simple as possible with their Move to iOS app for Android. To help make things even easier on you, we've outlined the process of using Move to iOS to transfer images, messages, contacts, mail accounts, calendars, and more over to your iPad or iPhone running iOS 10.

You must have read news about hackers dumping the data online, recent one was Ashely Madison. It's only the big companies' data, which gets noticed once it is out. There are many other small leaks which don't even get a mention. So this article is the first one of my series which will help you to find hacked accounts. Some of you must already know about this, but this post is intended for the new learners. This also serves as an example of my learning how a good service can be used in other w...

When we hack a web server, we usually want to be able to control it in order to download files or further exploit it. There are many websites that let you upload files such as avatar pictures that don't take the proper security measures. In this series, I will be showing you how to gain root access to such a web server.

Thanks to Verizon Wireless, I pay over $220 a month for my phone bill. It's just me on the plan—no family members, and it's not even unlimited data. So, when I receive that data alert message telling me that I've used up 90% of my plan and that I've still got a few more week until my billing cycle starts over, you know that I'm left scrambling to connect to some Wi-Fi.

When you're trapped at your desk before a jumble of data just waiting to be categorized, or zoning out during an important meeting, your mind wanders and, chances are, you feel a little guilty because of it. Yet you shouldn't try to reign in that distracted thinking. Instead, let your brain get distracted, and you'll unconsciously strengthen your memory.

In places like underground bars or national parks, your phone's Internet service is sure to slow down to a very sluggish pace, making it difficult to surf the web. Or worst case, data will be non-existent, leaving you with only low-level network support for calls and SMS text messages.

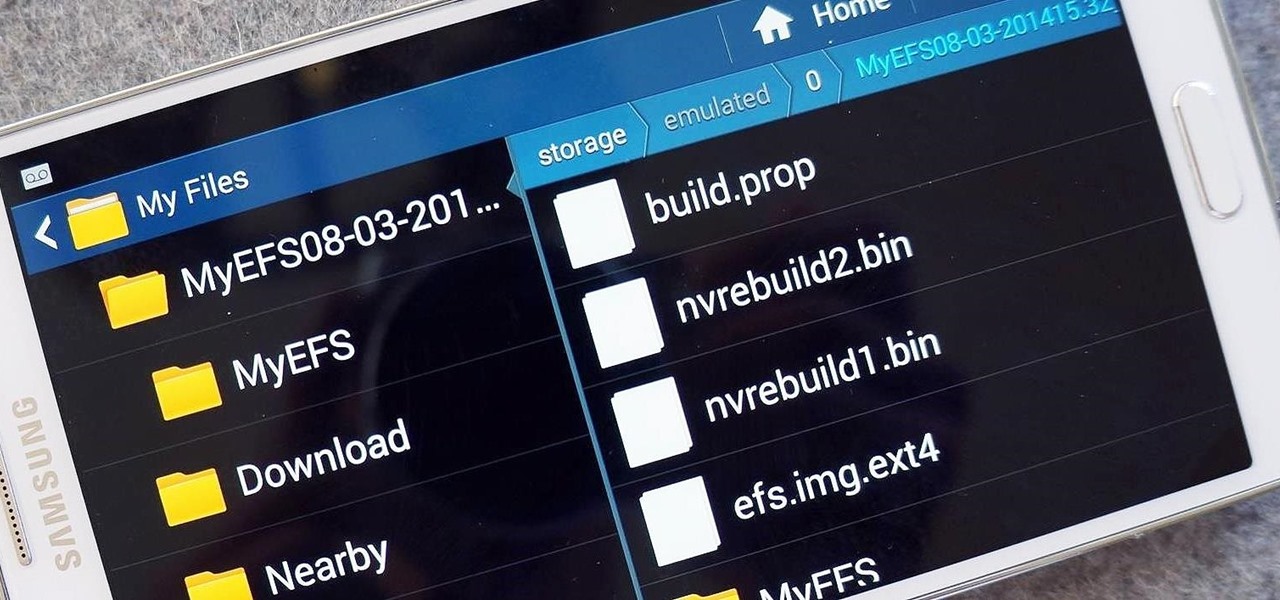
The options for customization are virtually endless when you're rooted and have an unlocked bootloader and custom recovery. However, there is always risk involved when flashing new mods or installing new ROMs. I always make backups in case something happens, but when I'm testing certain mods out, I sometimes get a damaged EFS partition.

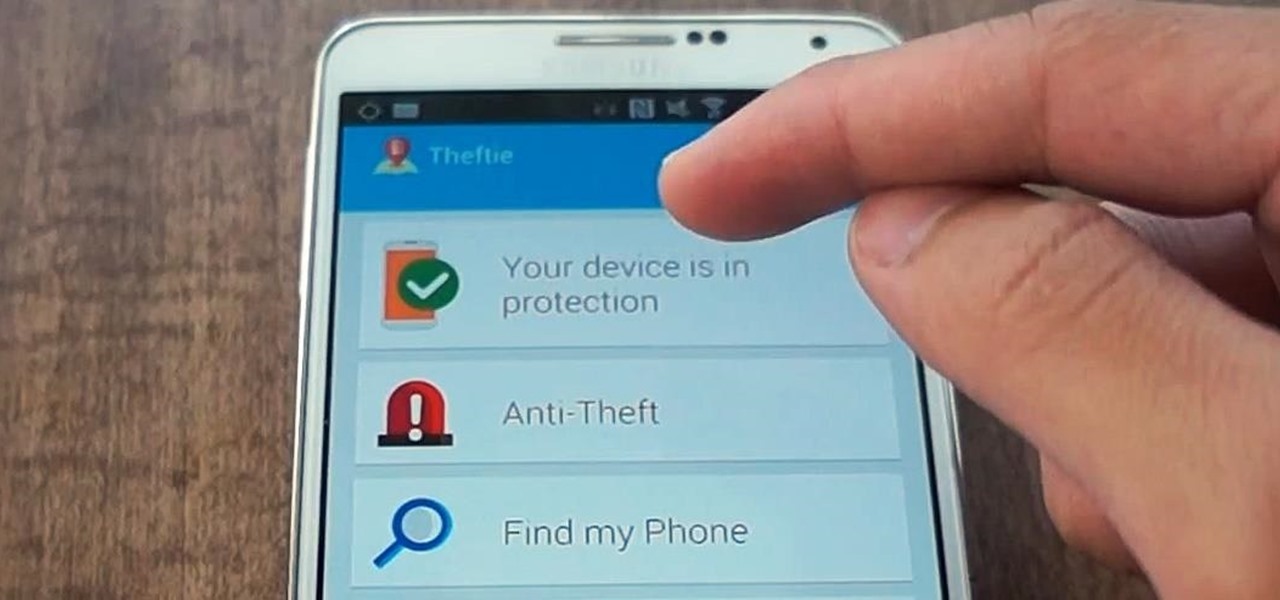
When you misplace your Android device, finding it with the Android Device Manager, or even better, Whistle Me, can help you find it no problem. But what about when your phone is not just hiding under the couch cushions? Your worst nightmare just came true. It's officially gone.

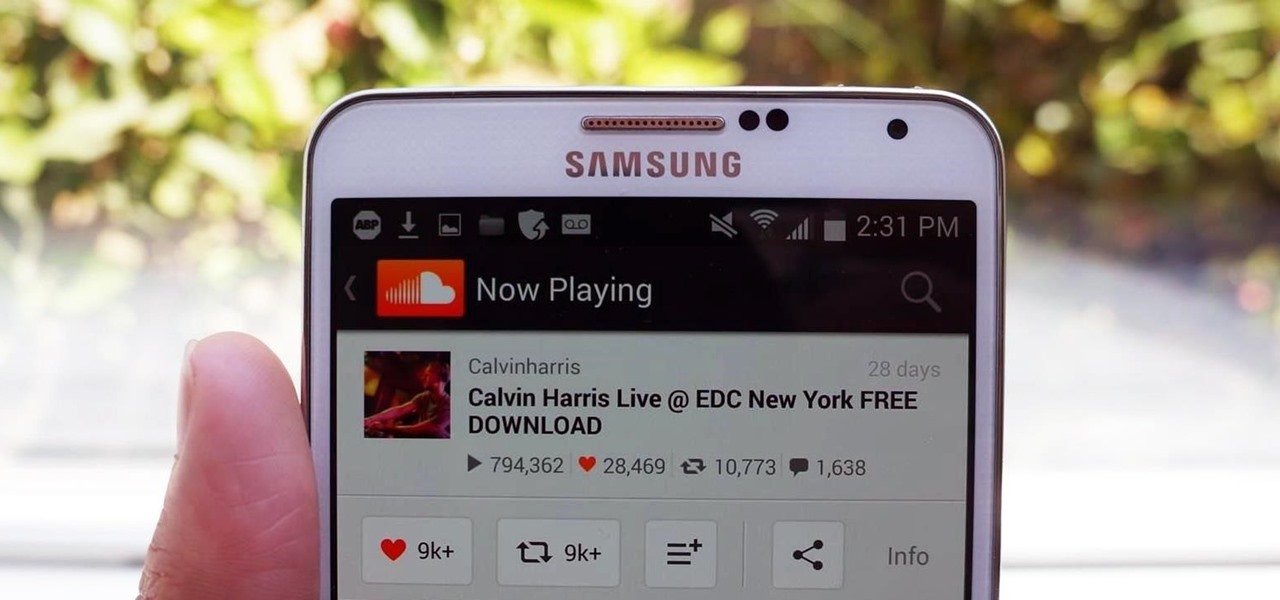
I love finding new artists on SoundCloud and listening to the tracks they put up. While some artists allow fans to download their tracks, others don't, leaving you to constantly load up their webpage to have a listen.

Welcome back, my aspiring hackers! In recent tutorials, I have made reference to the name and location of the Linux devices in the file system, such as sda (first SATA or SCSI drive). Specifically, I have mentioned the way that Linux designates hard drives when making an image of a hard drive for forensic purposes.