You may not know what HTTP is exactly, but you definitely know that every single website you visit starts with it. Without the Hypertext Transfer Protocol, there'd be no easy way to view all the text, media, and data that you're able to see online. However, all communication between your browser and a website are unencrypted, which means it can be eavesdropped on.
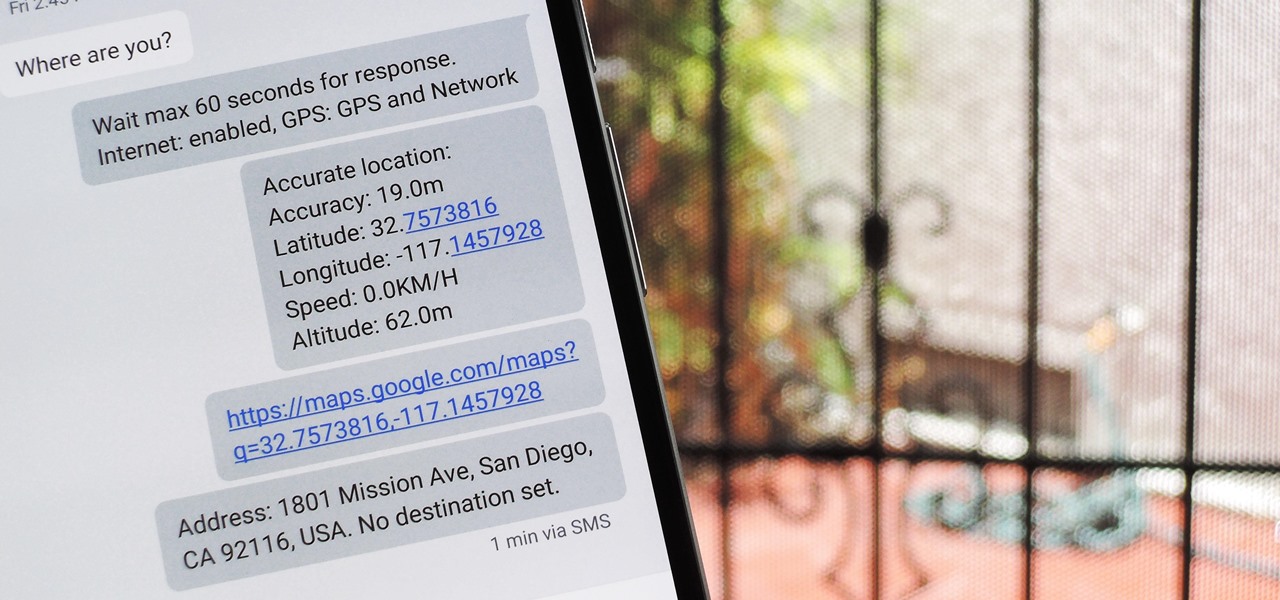
When you're driving, the last thing you need to be doing is messing around with your phone. But these days, people expect you to be available at all times, so the text messages continue to flow in while you're on the road. It's a terrible distraction, and one that is responsible for 25% of all car wrecks in the United States.
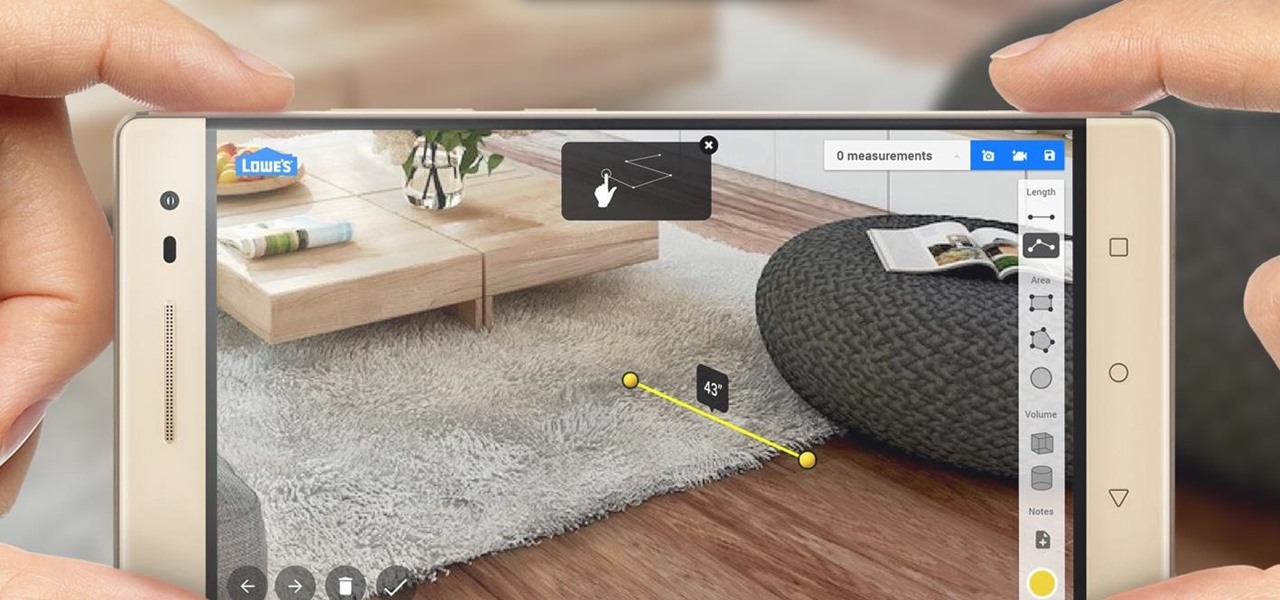
Augmented reality began on smartphones but technical limitations have prevented further development. Google's Tango (formerly Project Tango) aimed to change all that, and with Lenovo's help, they now have their first device.

Welcome back, my hacker novitiates! If you have been following this new Snort series, you know that Snort is the world's most widely used intrusion detection/protection system. Now a part of the world's largest network equipment company, Cisco, it is likely to be found everywhere in one form or another. This makes a compelling argument for learning how to use it, as it will likely be a necessity in any security-related position.

Welcome back everyone! It's been awhile hasn't it? Sorry for being so quiet, but my CCNA courses have really picked up recently. In the last article we covered how to import modules and how we can use them. In this article, we'll actually be covering a module that is essential to the hacking aspect of Python, sockets.

The first time a friend or family member asks if they can borrow your phone or tablet, you probably just hand it over without a second thought. But the second, third, and fourth times? Now it's starting to become a habit, and something probably needs to be done about it.

In a letter dated February 16th, Apple CEO Tim Cook responded to the FBI's demand that Apple create a "backdoor" to bypass the encryption on an iPhone used by one of the perpetrators of last year's terrorist attack in San Bernardino, CA. Cook began the letter by stating that Apple has "no sympathy for terrorists" and has cooperated in giving the FBI all of the information that it has available.

T-Mobile's "Binge On" service for streaming videos has received mixed reactions so far. On one hand, it gives any T-Mobile subscriber unlimited access to popular streaming video services like Netflix and Hulu without having to worry about going over their monthly data cap. On the other hand, it reduces video quality to 480p, which is 6 times lower than full HD.

Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic analysis. For those of you who are seeking career as a forensic investigator or security engineer, this can be invaluable training. For hackers, it might be life-saving.

Welcome back Java programmers! In this tutorial we'll being going over Variables/DataTypes and Type-casting

Welcome finally, to a tutorial on buffer overflows! At last we have reached an exciting part of this series where I will dedicate the entire article on explaining and exploiting the notorious vulnerability. Grab some popcorn, sit back and enjoy the show.

Do you have a file (or many files) that, in the wrong hands, may cause you trouble? Don't worry about it, because I'll show you how to wipe it (or them) from your computer in order to leave no trace behind.

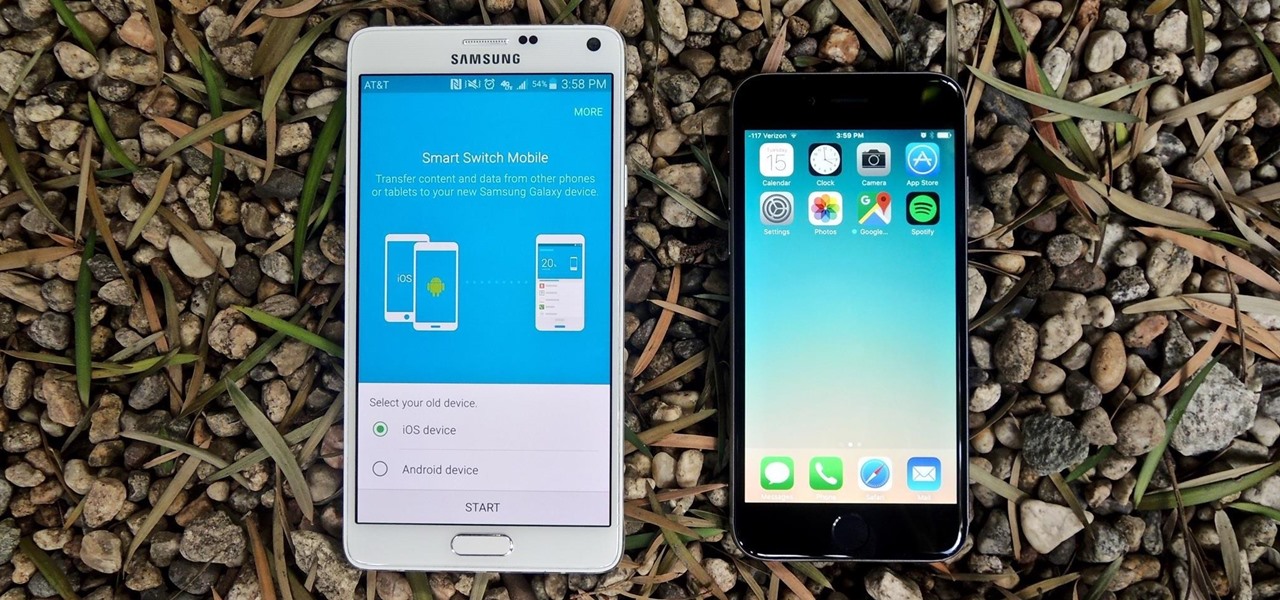
Thanks to Smart Switch, it's easier than ever now to ditch your iPhone for a brand new Samsung device, like the Galaxy S6 Edge+ or Galaxy Note 5.

Welcome learners, lets us proceed further with the information we already have. In this post we will explore more about finding hacked accounts online. We will look into how to find juicy info in pastes which are deleted on Pastebin.

If you have seen the movie Fast and Furious 7, you know what "God's Eye" is. Well this might spark interest to you.

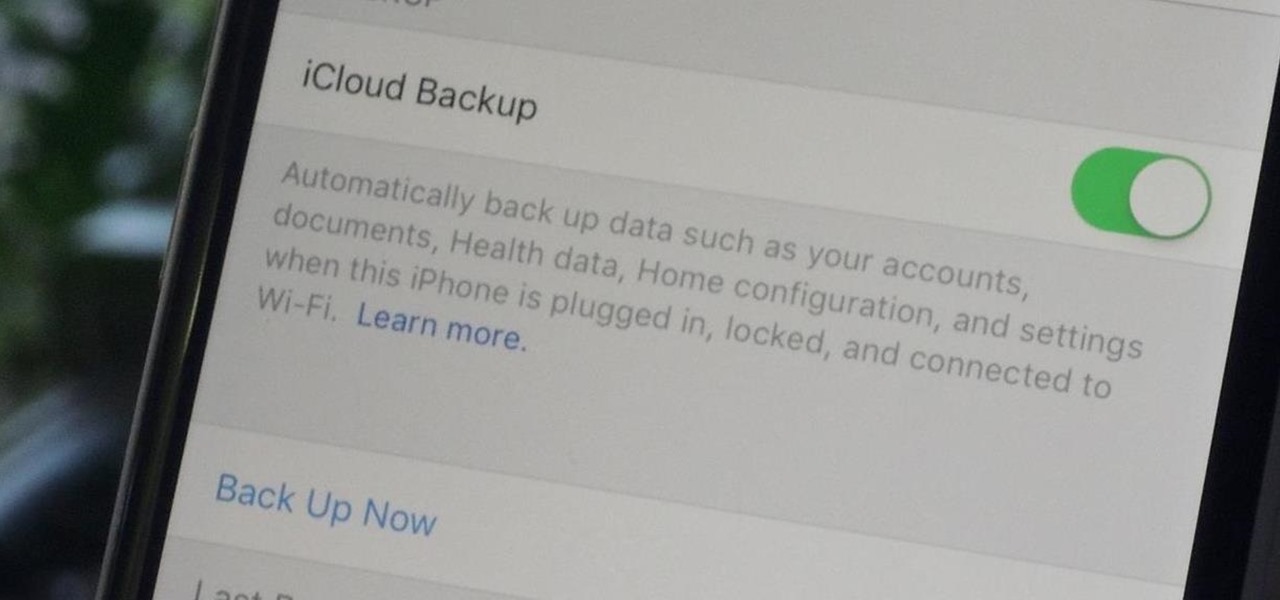
Enabled from the moment you first booted up your device, there's a feature deep in the iPhone's settings that automatically backs up your device in the background. As long as you're connected to Wi-Fi and a power source and your screen is locked, your photos, text messages, apps, and everything in-between gets safely stored to your iCloud account.

In the past, updating a rooted Samsung Galaxy device has always involved the complicated process of downloading the proper firmware for your variant, installing device drivers, then sideloading the update with Odin.

Update (February 2019): The methods below will help on older Android versions, but we've recently revisited this topic. So if you have a newer Android phone and you want to get rid of Google, head here.

Both the Galaxy S6 and S6 Edge have had root methods available to them before the phones were even released, but the problem with these existing root methods is that they would trip the KNOX counter on your device.

One of the few areas where Android lags behind iOS is a comprehensive backup solution for apps. Root tools, such as the popular Titanium Backup, are capable of backing up all of your apps and their data, but not everyone wants to root their device and potentially run into issues with voided warranties.

At the core of your Galaxy S5's hardware lies the central processing unit, or CPU for short. Practically every piece of data, every binary bit, has to pass through your CPU before it can be used to display a video or execute a game command.

When Google released Android 4.2, a new feature was introduced for tablets that allowed for multiple accounts to be used on a single device. In order to create a unique experience for each user, apps and personal data were kept separate, and switching between users became as simple as tapping your profile photo from the lock screen.

Welcome back, my rookie hackers! Most often, the professional hacker is seeking protected information from the target system or network. This might be credit card numbers, personally identifiable information, or intellectual property (formulas, plans, blueprints, designs, etc.). Most of my Null Byte guides have been focused on getting into the system, but this only begs the question—"what do I do when I get there?"

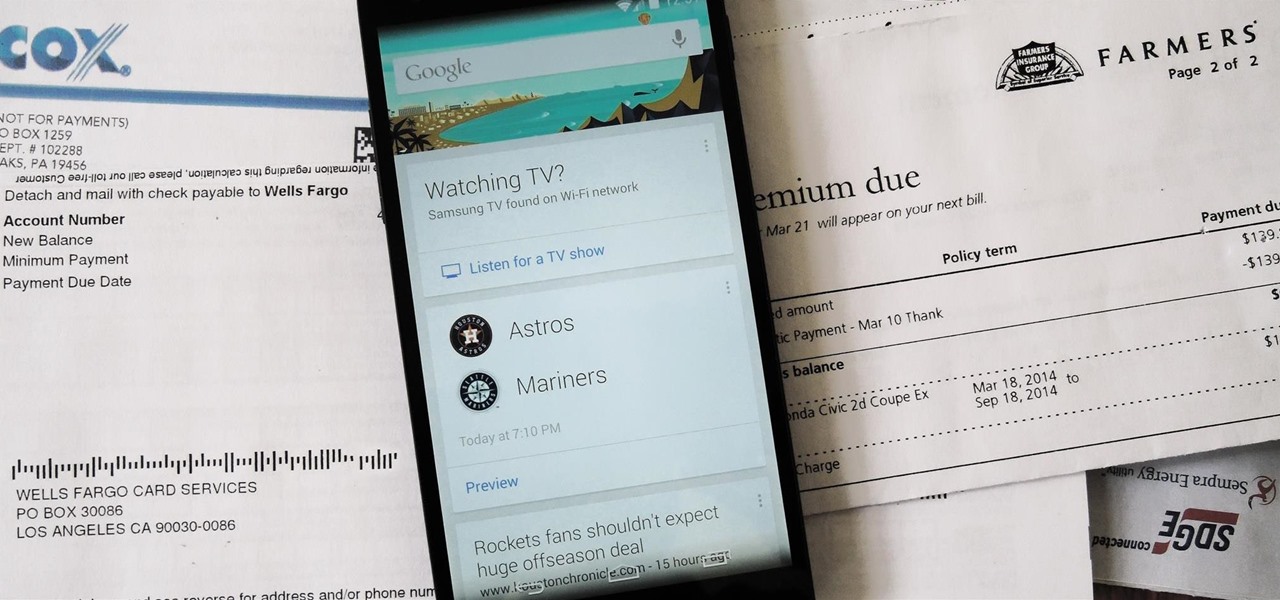
Google is widely renowned for its mastery in using data to tailor specific search results and ads. Their Android and iOS search apps put this ability to use in finding the most relevant pages for your query, and their desktop site is the most-used search engine on the web as a result of it.

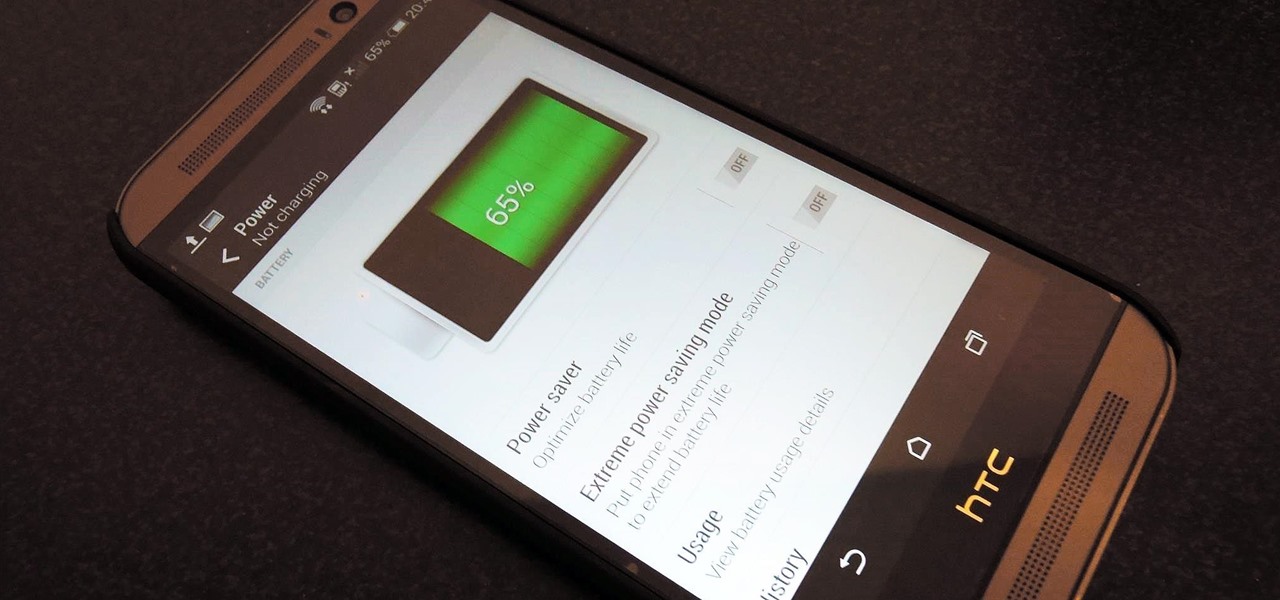
HTC claims to have improved the One M8's battery life by 40% over its predecessor, but there is always room for improvement.

If you've been using Google's hidden App Ops to lock down and prevent some of your Android applications from exposing your privacy, then think twice before updating to the new Android 4.4.2 software.

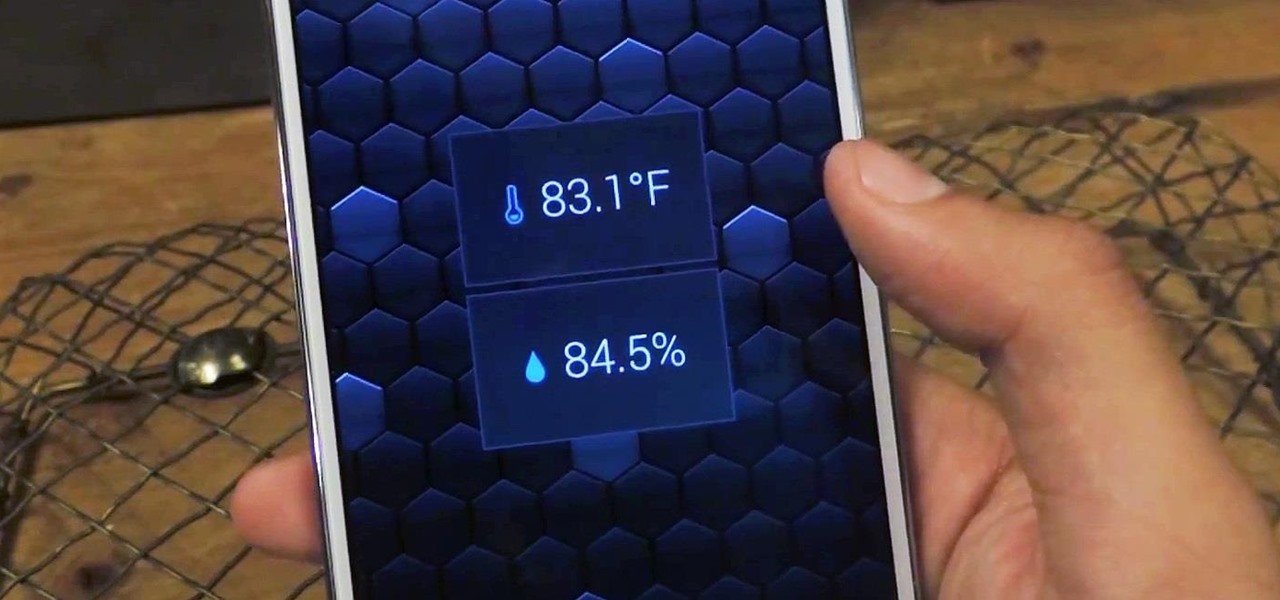
The majority of Android devices have built-in sensors underneath the hood that measure motion, position, and several environmental parameters that provide data needed to monitor your movements and adjust accordingly.

Since iOS 6 has been released, it's had its fair share of problems. From battery drainage, to photo uploading errors, to the Maps debacle, lots of users have been less than pleased. So much so that some are even downgrading.

People are always looking for ways to save money, and for the most part, saving money and cheating the system are synonymous when it comes to things like free internet access. Practically every new gadget is capable of connecting to the web, which means more and more people are looking for ways around those hefty internet bills.

All kinds of people pretend to be someone they're not on the internet, including scammers, people attempting to wind others up, hackers and web predators. Almost all of these people will leave bases uncovered and they're all easy to expose when you understand how to. Here are my favorite ways of finding out when somebody is lying quickly. Image Search

The first part of this tutorial will show you how to track and roto with foreground obstructions using Final Cut Pro. Then, you're shown how you can use Mocha Shape to import matte data into your video for a higher quality picture.

If you're not connected to the internet or don't have a data plan on your Android-powered Samsung Galaxy Tab, then chances are you don't have the right time and date. But don't worry, it's an easy fix! Simply go to MENU < SETTINGS < DATE & TIME and uncheck the AUTOMATIC to set the date and time manually. Choose SELECT DATE to change the date, SELECT TIME ZONE to change your area of the world, and SELECT TIME to adjust the hours and minutes of the day. Easy as can be.

In this video from AppleGenius0921 we learn how to sync a Blackberry with a Mac and iTunes. There is now Blackberry software for Mac. After downloading, start up the application. Take your USB cable and connect it from your Blackberry to your Mac. You can see all the applications on your Blackberry listed on your Mac. Here you can also check for updates and see your available memory. Also you can backup all of your data here. This will make a copy of everything on your Blackberry and put it o...

In this video, we learn how to make note cards for your research paper. Note cards will help keep your data organized and easy to organize. Take a pen and write out the title of the card on the top, then write out the pages you got the information from next to that. From here, start to write down information on the card, covering one topic per card. Use any notes that will help you out and have the most amount of information on them. After this, use a highlighter to highlight the different wo...

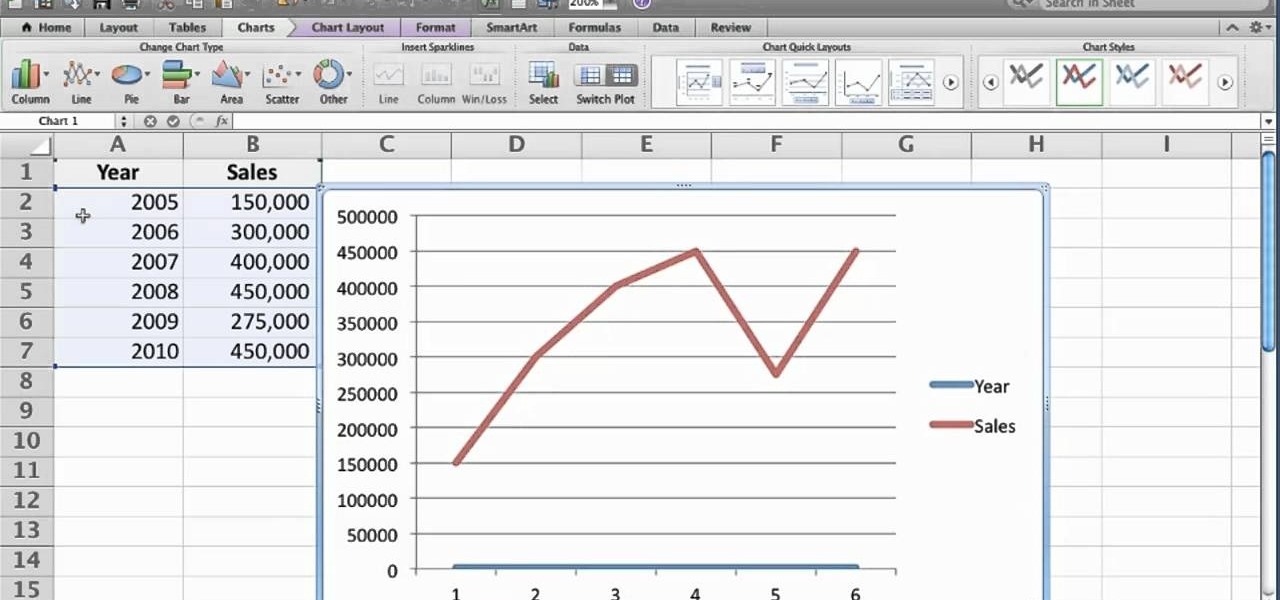
Want to generate a line chart in Excel 2011? This video will show you how it's done. Whether you're new to Microsoft's popular digital spreadsheet application, new to Excel 2011 or even an expert merely looking to brush up on the fundamentals, you're sure to be well served by this quality video tutorial from the folks at Lynda. For all of the details, and to get started creating and using line charts to visualize data in your own MS Excel '11 projects, watch the video.

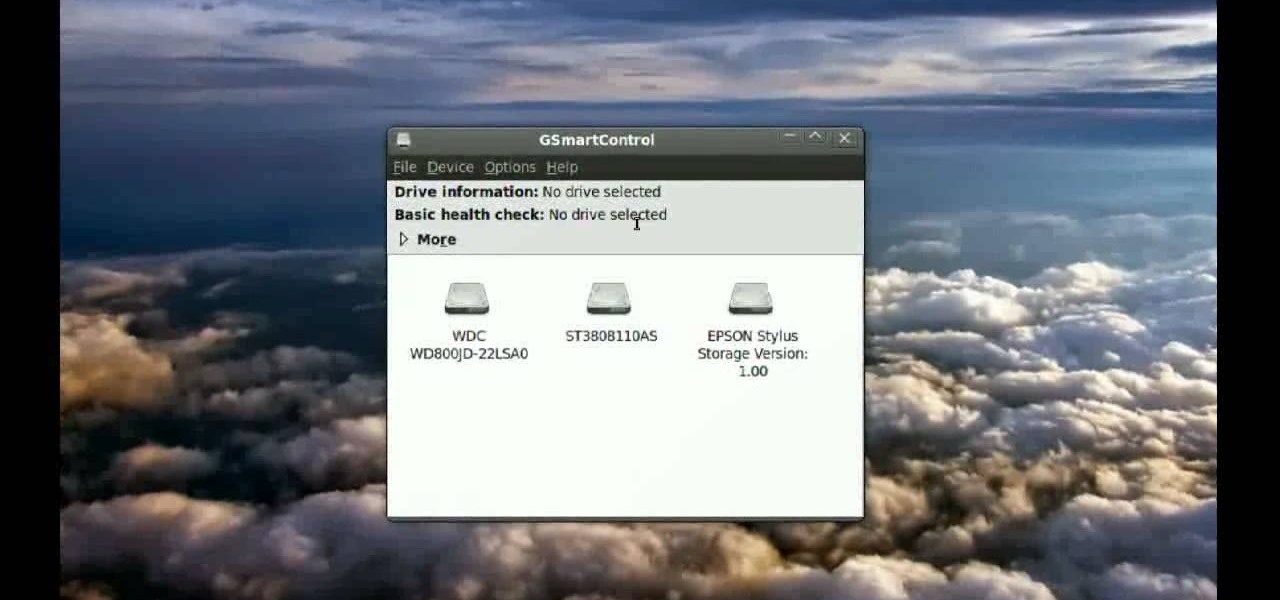
With this video, we learn how to tell if your hard drive is failing in Ubuntu Linux. If you have a failing hard drive, it will start making noises like clicking or grinding. If you hear these noises coming from your hard drive, you will need to get a new one before it fails completely and you lose all your data. You could have a failing hard drive but it doesn't make any noises. Hard drives come with a monitoring system so you can see what shape the hard drive is in. To see this, open up the ...

In this tutorial, we learn how to connect to Xbox Live with an iPhone & PC. You will need: jailbroken iPhone with data plan, laptop, PDANET on the phone, Ethernet cord, and Windows. First, launch the application on your phone and then plug it into your laptop. After this, you need the Pdanet software, which you can download online. From here, right click on the software and connect. Next, you will connect the laptop to the Xbox console with the Ethernet cord and going to the network settings ...

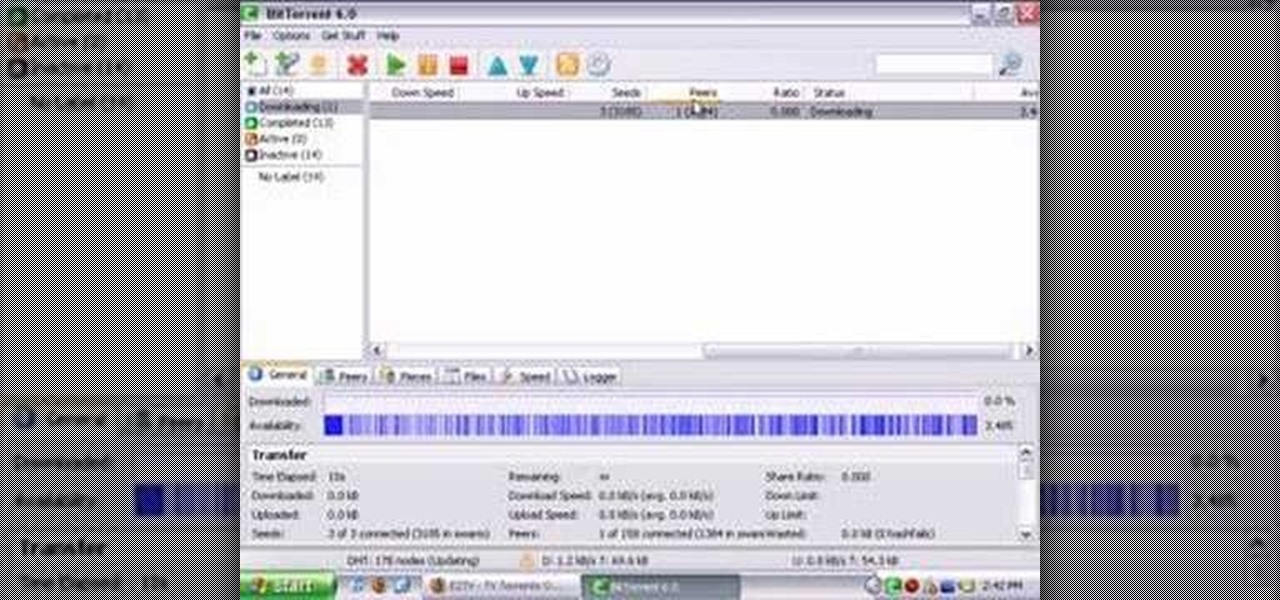
A torrent is a small file (usually less than 100 KB in size), which contains file details, URL details and other data, that enables peer-to-peer download using a torrent client.

In this video, we learn how to hack your iPhone 3G. To do this, you will need: iPhone 3G, Firmware 3.0 or 3.1 file, charger cable, and the Redsn0w program. First, connect your phone to the computer and then start up the Redsn0w program on your computer. Turn the phone off, then restart it. The phone will now connect to the program on the phone and it will say "downloading jailbreak data". You will see a pineapple walking around on the screen. After this, restart your phone again and it will b...

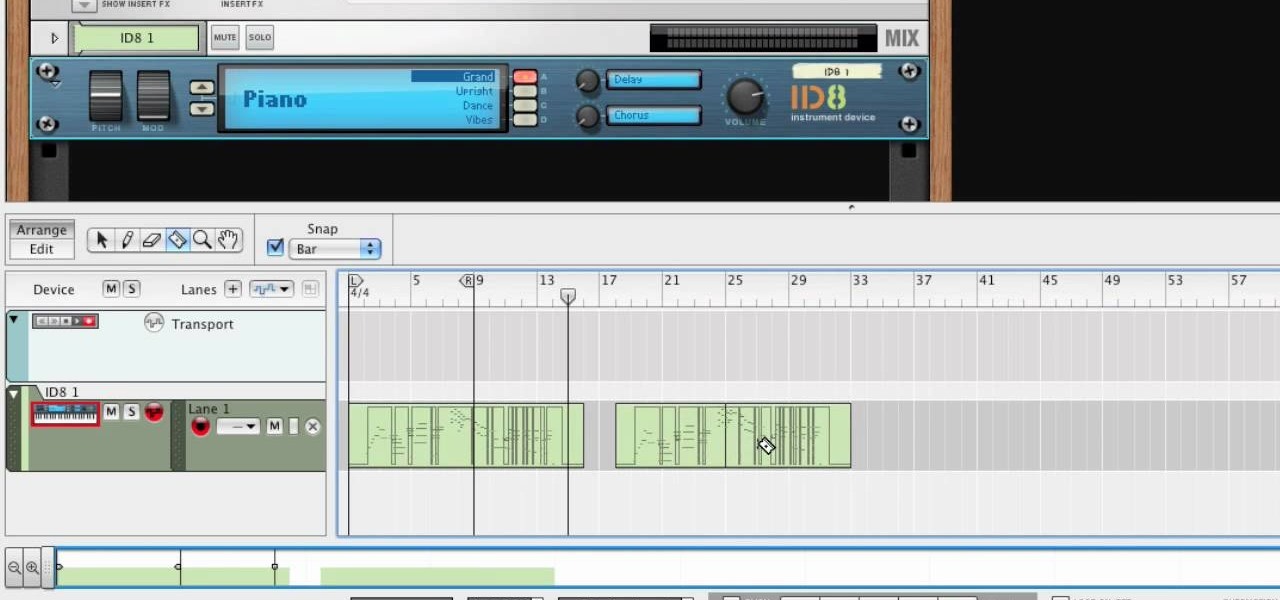
In this tutorial, we learn how to use MIDI in Record. First, automatically find your controller keyboard and set it up in your software. With this set up, create an ID8 instrument by clicking on the icon. Settle for a grand piano and record something to test it out. All clips are recorded and save mini notes, data, automation, and more. Clips can be moved, resized, duplicated, split, and joined through Record. These make up the arrangement and make the music. You can automate anything you wan...