For anyone using open source information to conduct an investigation, a balance between powerful tools and privacy controls are a must. Buscador is a virtual machine packed full of useful OSINT tools and streamlined for online research. This program can easily be set up in VirtualBox, and once that's done, we'll walk you through some of the most useful tools included in it.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

Despite the rise of music streaming, the experience of immersing oneself in the artwork and lyrics of old school albums is alive again, as sales of vinyl records and CDs have outpaced digital downloads for the first time since 2011. Now, the latest album from Amsterdam-based Necessary Explosion evolves this experience through augmented reality.

As it prepares to ship its first product by the end of the summer, Magic Leap has managed to impress yet another high-profile investor in telecommunications giant AT&T.

A team of academics from three different universities and two private companies have just discovered a new vulnerability that affects almost every Android device since 2012. The vulnerability is known as RAMpage, and it could be used to gain complete control over the device.

The company behind Japan's beloved Gozilla, Japan's Toho Studios, has for years tried to give fans the sense of what a giant, nuclear-powered lizard invading Tokyo might feel like. Until now, those attempts have been limited to the movie theater, but now, with the help of the Microsoft HoloLens, Godzilla is finally getting its chance to invade the actual city, with terrified fans looking on from a safe distance.

New Balance is helping Liverpool Football Club (FC) fans see how they look in the team's new kits with an augmented reality experience in Snapchat.

For SQL injection, the next step after performing reconnaissance and gathering information about a database is launching an attack. But something seems off .. in the real world, it's usually not quite as simple as passing in a few fragments of SQL code to an input field and seeing all that glorious data displayed right in the browser. This is when more advanced techniques are needed.

In the arms race between ARKit and ARCore, Google scored a big win with the announcement of its Cloud Anchors shared AR experiences platform at Google I/O on Tuesday.

While Apple has generally been more bullish on augmented reality as opposed to virtual reality, the latest whispers about its purported AR headset suggests that it may be giving VR another look.

One of the most popular sports shows on television, Inside the NBA on TNT, gave viewers a tech-powered treat on Tuesday night by dropping them into a broadcast version of augmented reality.

We know Android 9.0 will have the formal designation of Pie, following Google's age-old tradition of naming their OS after items you'd normally find on a dessert menu. And thanks to a slew of new features that centers around your overall security, P could also stand for Privacy.

With the reveal of Magic Leap's developer documentation last week, many questions have been answered—and several new ones have been raised as well. But since the Magic Leap One (ML1) isn't simply called the "Leap One," these are questions that the company probably has no interest (at least for now) in answering. Understandably, Magic Leap wants to keep some of the "magic" under wraps.

Continuing with its new paradigm of using augmented reality to cover the news, The New York Times has published a feature story that takes a peek into the late David Bowie's eclectic wardrobe of on-stage outfits.

Now that we've had a chance to jump into the Lumin SDK documentation at Magic Leap's Creator Portal, we now have much more detail about how the device will function and utilize software than any single piece of content released by Magic Leap to date.

Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless attack framework called Airgeddon is used to find vulnerable networks, and then Bully is used to crack them.

Apple's TrueDepth camera made its debut in the premium-priced iPhone X late last year, and since then, the reviews have been pretty positive. Now, Apple might be preparing to make the Animoji-friendly sensors available in more iPhones, as well as the iPad Pro, later this year.

MoviePass may be popular with filmgoers on a budget, but it might not be with those of you who are concerned about your privacy, since MoviePass may be logging your location data even when you don't expect the app to do so.

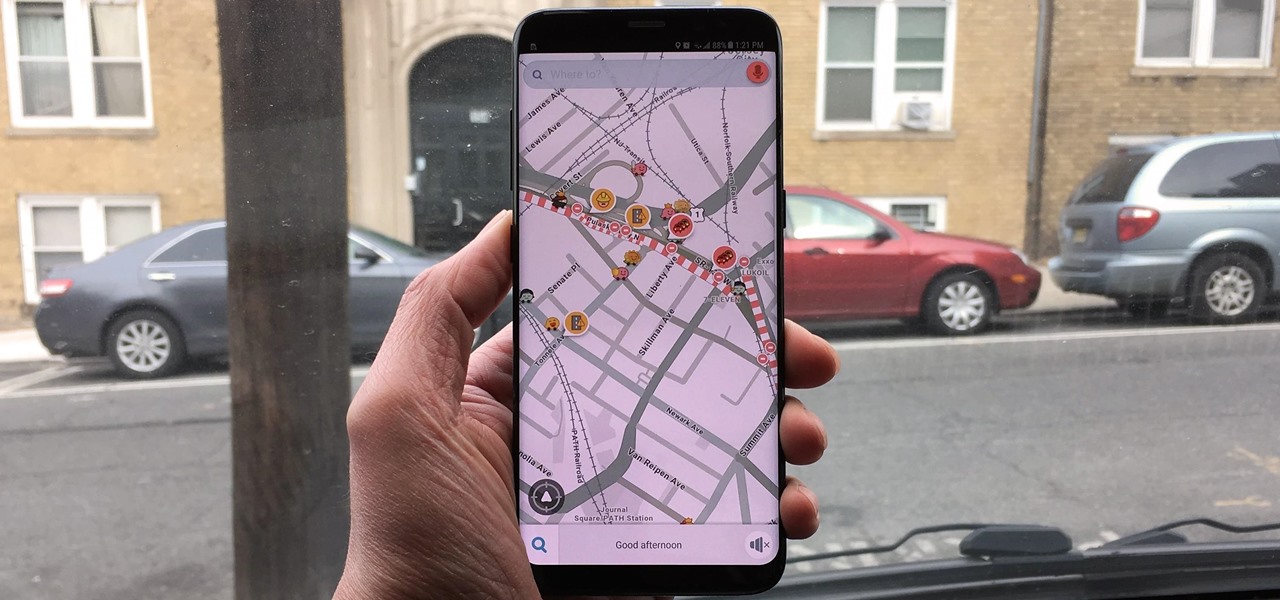
Because it sources a majority of its vital data from actual drivers on the road, Waze is easily one of the best navigation apps to use if you prioritize safety. Benefits such as crowd-sourced traffic data, police trap locations, and road work avoidance, when combined, help you anticipate traffic conditions with unprecedented accuracy and make adjustments accordingly.

Whether you're new to Android or you just haven't kept up on the app scene lately, we hand-picked over one hundred essential apps that are all designed to improve your experience. From custom launchers and icon packs to weather apps and file explorers, there's something for everyone in this list.

The same approach to augmented reality that some companies use to improve workforce productivity could also make it easier for car owners to operate and maintain their vehicles.

Now, when the weather outside is frightful, Pokémon GO players can expect it to be just as unpleasant in augmented reality.

One of the best parts of being an Android user is the countless awesome features. Many of these features are well-known and user-facing, like custom icon packs and launchers, but some get lost in the shuffle. Back at Google I/O 2016, Android Instant Apps were introduced to developers and enthusiasts. Since then, the feature has seen a wider rollout, but few users are aware of it.

Mobile game companies Hit Point Studios and Legacy Games have adapted their Color BlastAR augmented reality game for iOS with the ARKit platform.

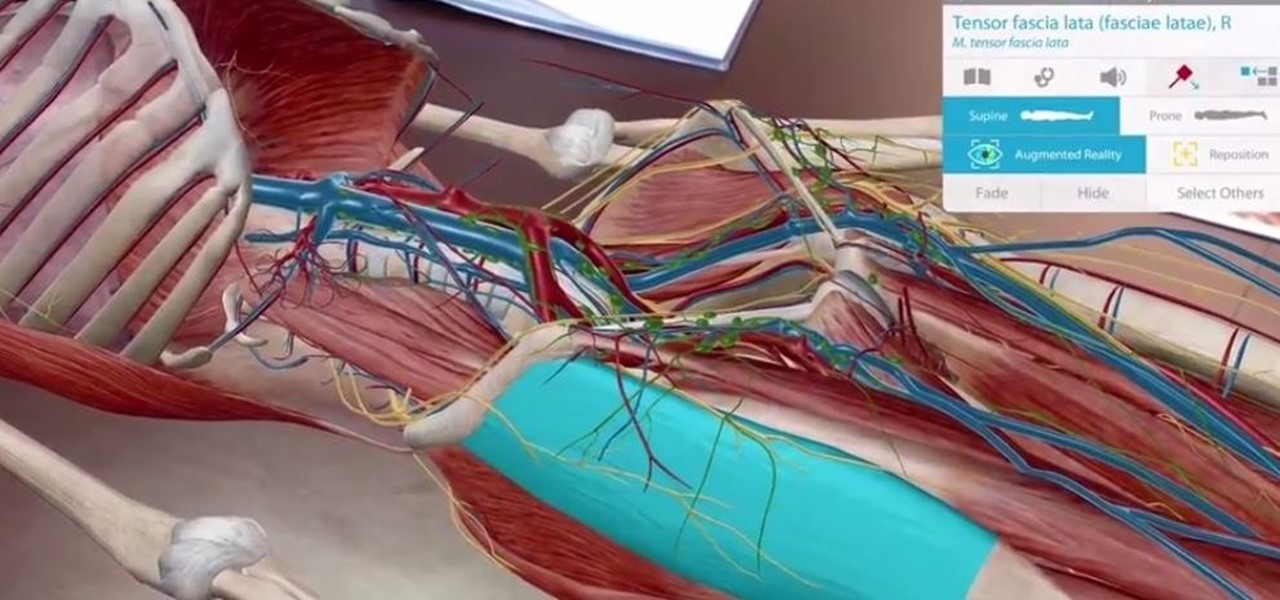
An update to the Human Anatomy Atlas 2018 enhances the study of the human body with augmented reality courtesy of iOS 11 and ARKit.

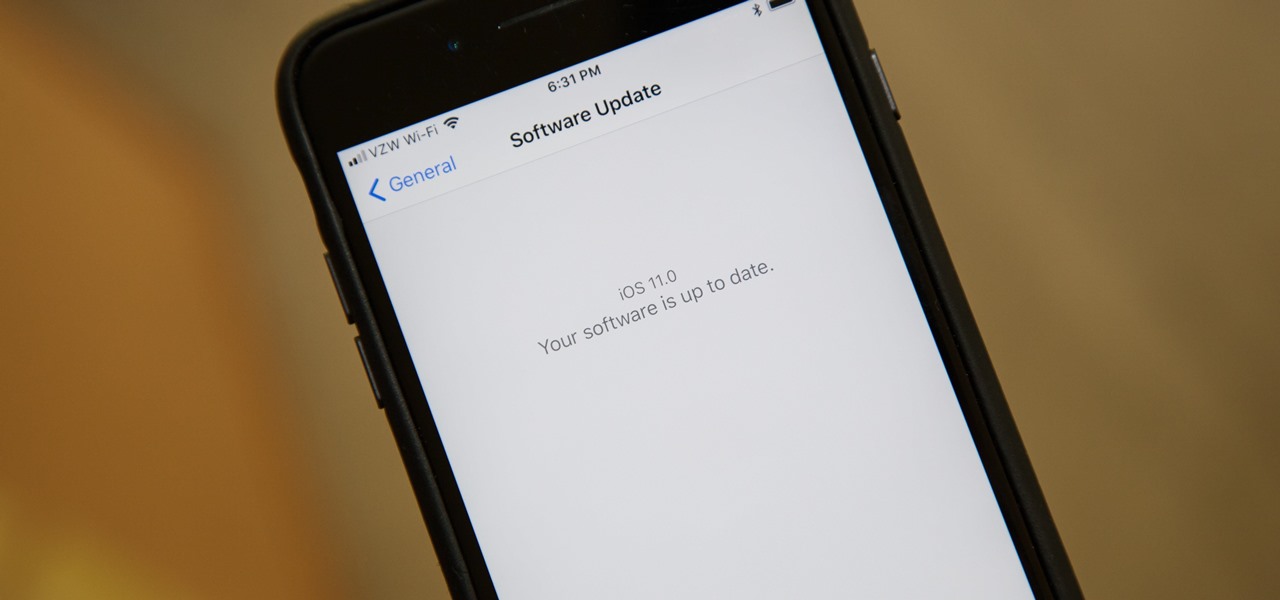
The final developer version of iOS 11 was leaked a few days ago, but Apple quickly stopped signing it so nobody else could install it. With Apple's Sept. 12 event now over, the Golden Master (GM) version of iOS 11, the same version that will be released to everyone around Sept. 19, is available to install again — and anyone can get it.

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

From all the demos we've seen, we know for sure that the marketing world is going to change drastically thanks to Apple's ARKit.

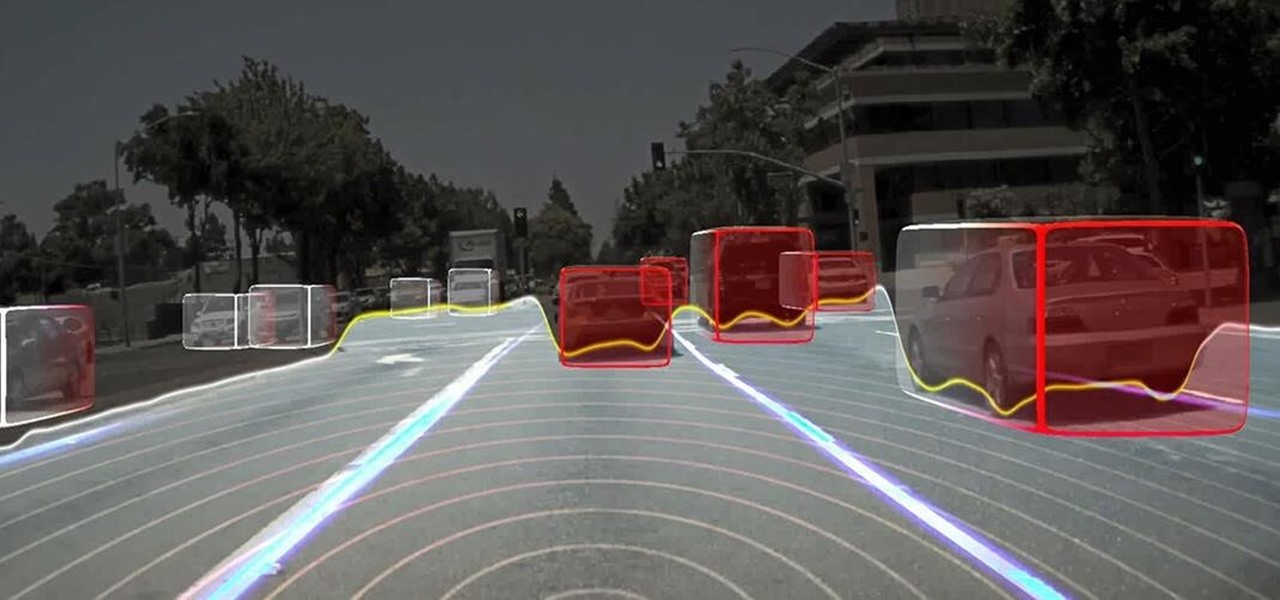
Long before Nvidia figured out how to embed neural networks in its graphics processor units (GPUs) for driverless vehicles, it and other chipmakers were already making the same kinds of devices for 3D games and other apps.

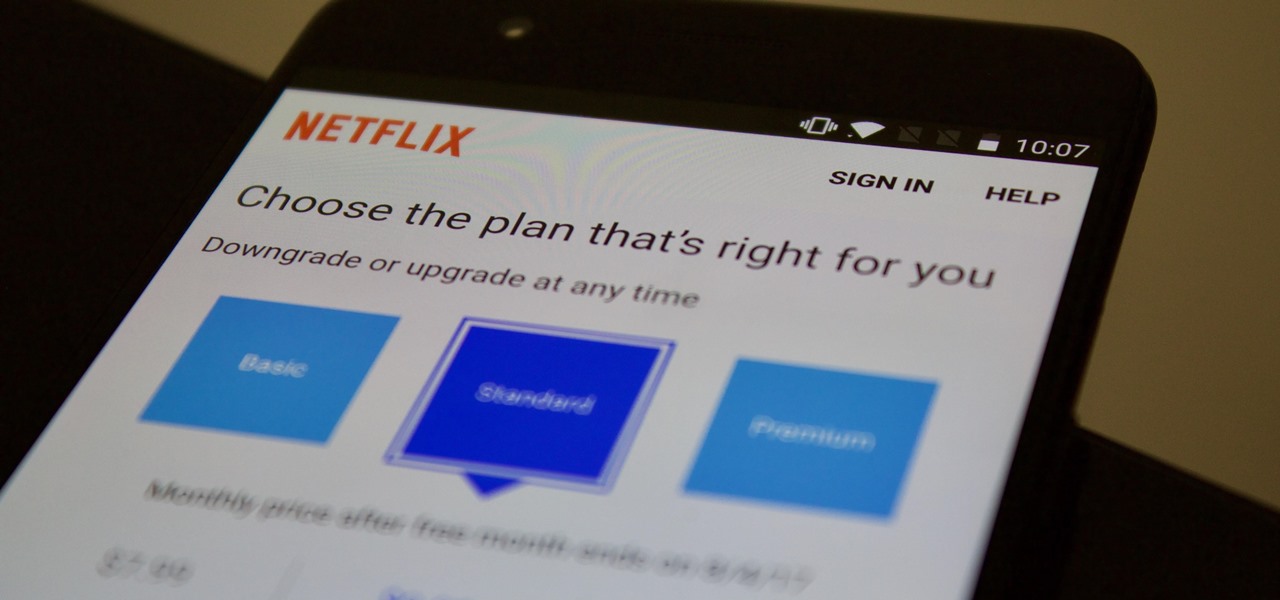
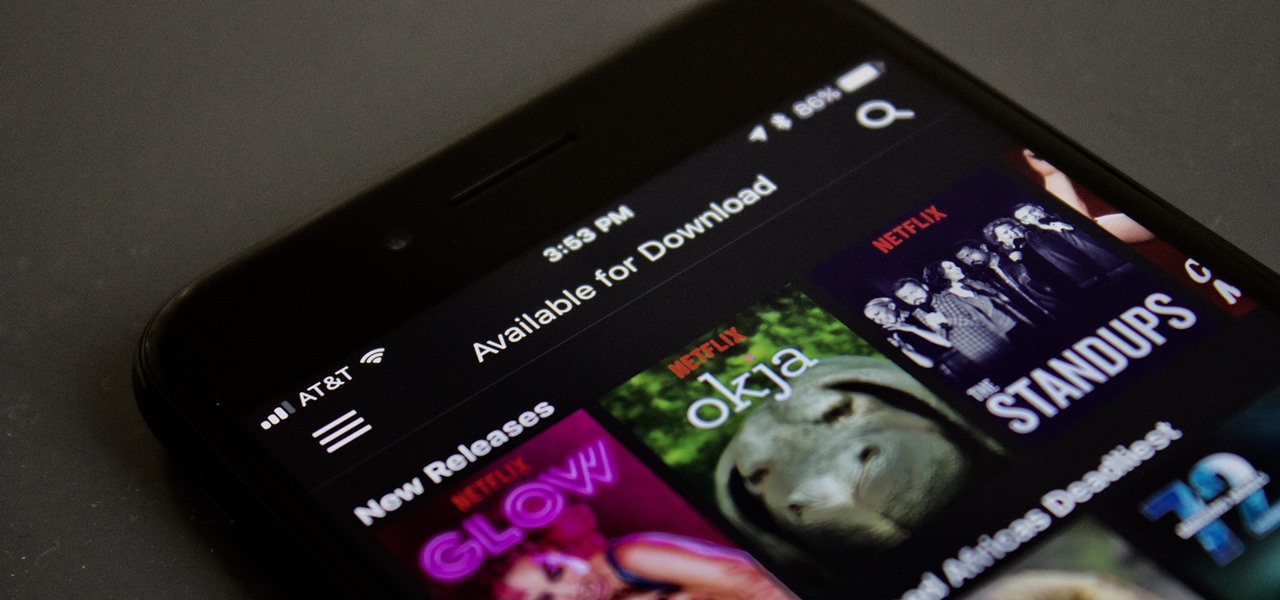
Netflix offers three different tiers of service. The good news is that no matter which subscription plan you choose, the available content is the same. Whether you choose the cheapest plan or the most expensive, you'll be able to watch any TV show or movie in Netflix's library. But there are other things to consider when choosing the plan that's right for you and your smartphone.

Netflix added the ability to download TV shows and movies on Android and iOS for offline binging back in Nov. 2016, and the process is the same as it is today. So if you anticipate having some downtime to catch up on Narcos or give Bright a try when you'll be away from a secure Wi-Fi connection, download videos onto your phone and save your data for more important things.

A pair of organizations recognized companies working in augmented reality for their innovative technologies over the past week. Meanwhile, another company used augmented reality for a sector that is overdue for a technology makeover, while another company has developed new camera modules that could usher in the next evolution of mobile AR.

It's no secret that devices leak data, but sometimes they do so in ways you may not expect. Your phone, laptop, printer, and IOT devices leak Wi-Fi information that can (and is) used to track you.

Buying a smartphone used is an excellent way to save money, but those savings come with a risk that your seller isn't as forthcoming as they claim. You don't want to end up buying a stolen smartphone because it might not work correctly ... and, you know, it's wrong. Luckily, there's an easy way to check if the phone you're about to buy is legit.

This week's Brief Reality is led by a pair of stories with an eye to the future of the augmented reality industry, first in terms of standards for the industry, then with regards to its future applications in the automotive realm. Finally, one company looks to boost its future sales with an executive hire.

A federal judge wants answers after an Uber engineer accused of data theft pleaded the Fifth in the ongoing Waymo versus Uber battle. This privilege would protect the accused, Anthony Levandowski, of self-incrimination and handing over specific documents demanded in a previous subpoena and forthcoming deposition.

No one is safe anymore, it seems. Google's Project Zero has just uncovered how easy it is for attackers to target your phone's Wi-Fi chip, which is essentially a mini processor for Wi-Fi that detects and processes networks.

Microsoft, even being Apple's fierce competitor, is no stranger to producing iOS apps—in fact, they've made 94 of them. But their latest iOS app may be their silliest yet: a goofy photo editor named Sprinkles.

Officials in Colorado are concerned as 61 cases of the mumps were reported so far this year, a significant increase in the prevalence of the contagious disease in the state.

LOOOK, a Seattle-based mixed reality and development studio, can now peer into the future with their new geotechnical engineering visualization application for Microsoft HoloLens.