During a penetration test, one of the most important aspects of engaging a target is information gathering. The more information you have coming into an attack, the more likely the attack is to succeed. In this article, I'll be looking at SpiderFoot, a modular cross-platform OSINT (open-source intelligence) gathering tool.

Welcome to my very first tutorial ever. Today I will be teaching you how you can use Arachni to scan vulnerabilities of web applications. I welcome all criticism good or bad as a teaching method for myself.

If you enjoy spending your time outdoors, but hate that you don't have a decent place to sit, this video may be for you. In this tutorial, you'll find out how to build a southern pine garden bench from scratch. It's perfect for the front or backyard and will give you a nice place to sit. When tackling this project, make sure you're careful when working with power tools. So check out the tutorial, be careful, and enjoy!

If you enjoy spending your time outdoors and tend to a garden, then you need a workspace to call your own. Don't have one, then either buy one or build it. Buying one may be easy, but if you build it you'll appreaciate more.

The iPhone has always been hamstrung by its alignment with AT&T, the worst of the big 4 US cell service providers. If you have an iPhone and are planning on unlocking it for use with another provider, or just want to use it without being connected to AT&T's network, this video is here to help. It will show you how to activate an iPhone instantly without a service plan using any AT&T SIM card.

When Martha Stewart's daughter, Alexis, was a young girl, her favorite pie was the sweet potato pie from a restaurant down the street. But as Alexis got older, she started not enjoying the overly sweet taste. In an effort to still enjoy her favorite pie, she adapted the recipe.

In this video, learn how to build your own mini-terrarium at home and enjoy the beauty of the outdoors from inside your own home. This is super easy and only requires items that you probably already have at home, so it's cheap too! Enjoy your little terrarium everyday with help from Elizabeth Gleeson. Elizabeth teaches you how to build a garden inside a soda bottle, aluminum can, wine bottle and jar! Beautiful!

In this tutorial, we learn how to make a homemade delicious protein shake! There are two different recipes that both have good nutritional content. The first shake is a strawberry-banana cheesecake shake. First, take 1 c of frozen strawberries and place them into a blender. Then, add in 1/2 c of milk and blend this until it's slightly mixed. Now, add 3 ice cubes, 1/2 of a banana, 1 scoop of whey protein , 1 tsp of cheesecake pudding powder and 1 tsp of sugar free strawberry jello to the blend...

If you enjoy arts and crafts, pop-up, scrapbooking and origami, you will enjoy these craft projects too. Like origami, kirigami is the craft of paper, with the added technique of paper cutting. Kirigami will enhance any origami, pop-up and scrapbook projects and scrapbook and origami techniques will enhance kirigami. Kirigami pop-up blossoms, butterflies and puppets make unique gifts or cards for any occasion and the recipient will enjoy seeing their gift, card or pop-up take form before thei...

training with a head target wall mirror. Learn how to use target mirrors to practice jabs and hooks in this free video for boxers.

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.

Learn how to mingle. If the idea of walking into a room full of strangers strikes fear into your heart… welcome to the club. But there are ways to overcome this common social phobia.

Getting a good break in life is always nice. But when you're playing pool, it's essential. You Will Need

TWRP is the premiere custom recovery for Android because of how many devices it supports and how simple it is to use. But installing it in the first place hasn't always been the easiest thing to do — until now. With the help of a Magisk module, you can finally use one Android device to flash TWRP on another.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

If you or someone you're shopping for has a newer iPhone model or an Android smartphone like the Galaxy Note 9 or Pixel 3, they come with wireless charging capabilities. Problem is, they don't come with wireless chargers. But there's no better time to snag one than on Black Friday, and we've found the best deals out there for 2018's holiday season.

Russian cyber disinformation campaigns have many missions, but one of particular interest is using technology to monitor, influence, and disrupt online communications surrounding culturally sensitive topics or protests. The ability to watch these events, and even filter positive or negative tweets to amplify, gives rise to the ability to execute a number of disinformation campaigns.

Thanks to its advanced cameras, the Galaxy S9 can capture videos at an astonishing 960 frames per second (fps). To put it in perspective, you now have you the ability to record the world around you in ways that previously required expensive professional camera equipment. And that's just the tip of the iceberg.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

Cross-compilation allows you to develop for one platform (like Kali) and compile to run on a different platform (such as Windows). For developers, it means that they can work on their platform of choice and compile their code for their target platform. For hackers, it means we can compile exploit code for Windows from Kali.

Sharing your Wi-Fi password is like giving an unlimited pass to snoop around your network, allowing direct access even to LAN-connected devices like printers, routers, and security cameras. Most networks allow users to scan and attempt to log in to these connected devices. And if you haven't changed the default password on these devices, an attacker can simply try plugging them in.

A new study just out reveals that HIV takes hold in the human body with the help of cells that usually work to heal, not kill.

Welcome back to this series on making physical objects come to life on HoloLens with Vuforia. Now that we've set up Vuforia and readied our ImageTarget and camera system, we can see our work come to life. Because in the end, is that not one of the main driving forces when developing—that Frankenstein-like sensation of bringing something to life that was not there before?

Welcome back, my tenderfoot hackers! One key area on the minds of all hackers is how to evade security devices such as an intrusion detection system (IDS) or antivirus (AV) software. This is not an issue if you create your own zero-day exploit, or capture someone else's zero-day. However, if you are using someone else's exploit or payload, such as one from Metasploit or Exploit-DB, the security devices are likely to detect it and spoil all your fun.

Welcome back, my hacker apprentices! Several of you have written asking me how you can check on whether your boyfriend, girlfriend, or spouse is cheating on you, so I dedicate this tutorial to all of you with doubts about the fidelity of your spouse, girlfriend, or boyfriend.

This year, like every year before it, Black Friday sales are starting earlier than ever. A lot of stores will be opening their doors as early as 5pm on Thanksgiving to get a head start on the madness (and it really is madness). As we've discussed in the past, one of the keys to emerging victorious on Black Friday is to plan, plan, plan. So, we've compiled some of the best deals in tech, gadgets and appliances to help you prepare for battle.

For over 20 years, a tiny but mighty tool has been used by hackers for a wide range of activities. Although well known in hacking circles, Netcat is virtually unknown outside. It's so simple, powerful, and useful that many people within the IT community refer to it as the "Swiss Army knife of hacking tools." We'll look at the capabilities of Netcat and how the aspiring hacker can use it.

An internet connection has become a basic necessity in our modern lives. Wireless hotspots (commonly known as Wi-Fi) can be found everywhere!

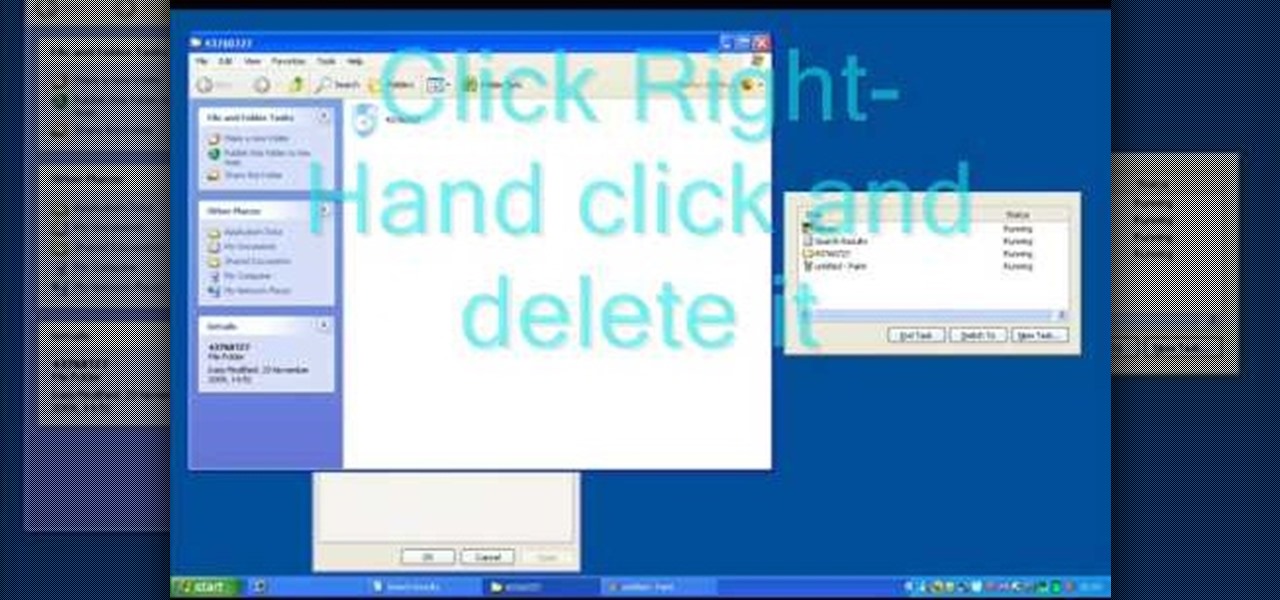
In this tutorial, we learn how to remove security tool in less than one minute. First, restart your computer, then press "ctrl+alt+del" when your new window starts up. After this, wait for a few seconds, then if you see the security tools pop up, end the task for it. Then, go to the start menu, then all programs, then look for any security tools. Right click, on "find target" then delete it! After this, your security tools will be deleted and will stop annoying you. You will be able to delete...

No matter what kind of business you have, small or big, online-based or not, when you're dealing with email marketing, the number one things your targets will see is the subject line, and if your subject line looks spammy or uninteresting, it's not going to help you one bit.

In this tutorial, we learn how to throw a crazy gyroball in wiffle ball. You will first stand still with the ball in your hand grasping it lightly, when you go to throw the ball, throw with force and spin your body around. This should make the ball go straight into the target almost every time you throw it. Keep practicing this until you have the hand placement correct. Try moving your hand in different positions around the ball so that the grasp makes the ball move in the right direction. Af...

In this Golf video tutorial you will learn how to avoid slicing with your driver off the tee in golf. First and foremost make sure that your grip is correct. The next point is allowing the club to sit on the ground the way the manufacturer wanted it. The next important lesson is to ensure that your feet and your shoulders are aligned straight down the target. And the last and the most important point to remember is to swing back to the ball with your hips first. Don’t use your arms first. If ...

Jim McLean shows us how to do an eight step swing in this video. You start the swing in the "address" or universal position. The first step is to move the club three feet back from the ball in a uniform motion. Position two is moving the club half way back where the club is pointing down the target line. Position three is a three quarter golf swing is when your elbows are level and the shaft of the club is pointing into the plane line. Position four is preparing to swing forward. Position fiv...

This video is on Golf and will show you how to use the variable tee drill to cure a pull shot in golf. This video is from Golf Link. A typical problem for somebody who tends to pull the ball is they position the ball too far forward. So, when they are setting up, the shoulders are actually looking left. By the time the club head reaches the ball during the swing, they are swinging around to the left producing the pull. The variable ball position drill will cure this problem. Place a club on t...

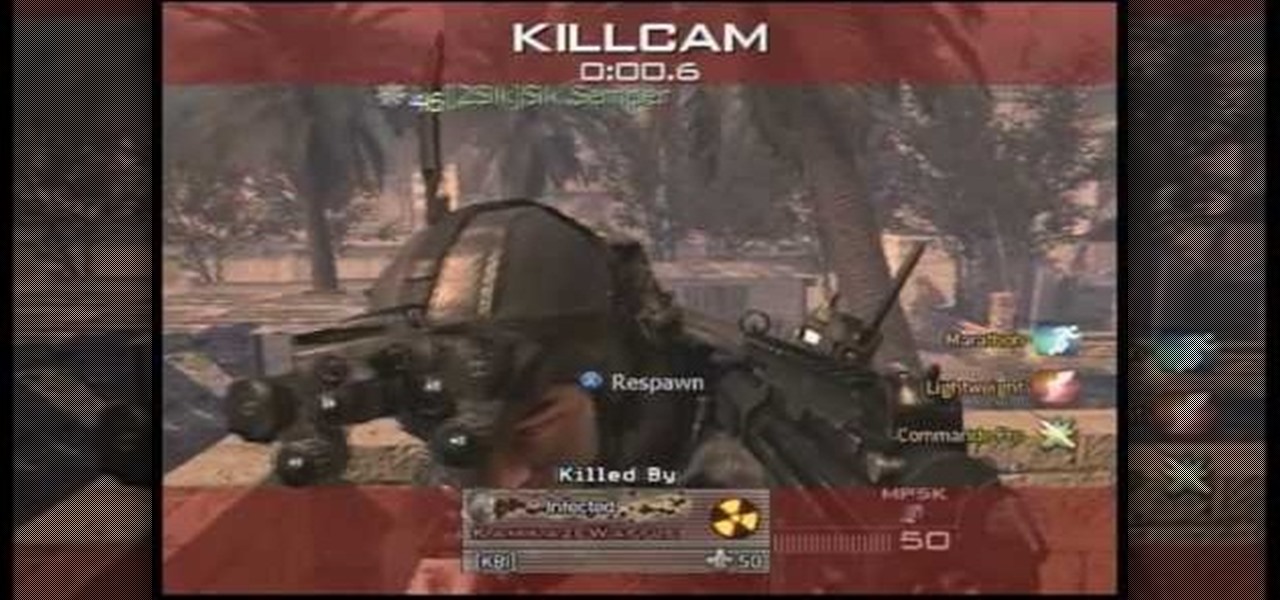
This video shows you how knives can be much more than a short range weapon in the online mood of the game, Call Of Duty: Modern Warfare 2. KamikazeWaffle and other players show you 50 ways of killing you enemy using the knife. Some of those tricks involve throwing the knife across a map and still hits its target. They also demonstrate how any objects around you can be used to change the direction of the thrown knife to the desired destination. Kill cam is recorded for each of the 50 tricks so...

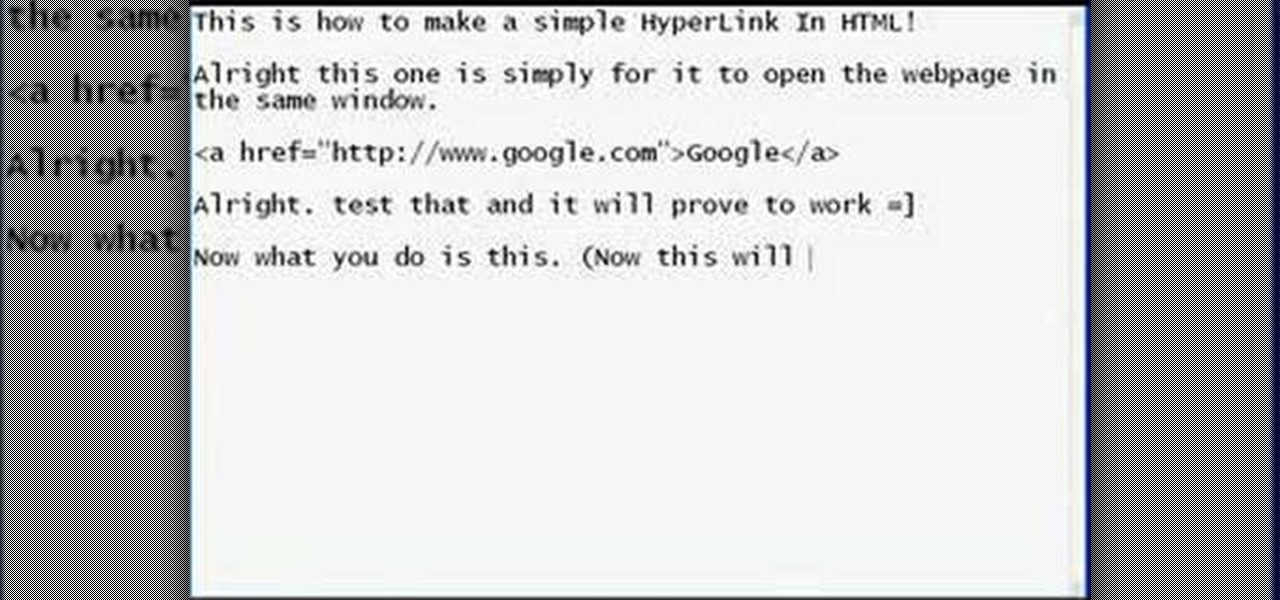
This how to video shows how to put an HTML hyperlink on a web page. It starts with the basic code to simply insert the link and have that link open in the same window. The code appears as follows: <a href="http://www.website.com">Text that will show up on the page </a>. The example used is Google, so it would be, <a href="http://www.google.com">Google</a>. The video then explains how to create a hyperlink that shows up in a new window. Sticking with the Google reference it would read <a href=...

In this sports how-to video, Farmington HS boys basketball coach Shane Wyandt explains how he teaches the BEEF method of shooting. The work BEEF is an acronym for a ball shooting concept in basketball. The B stand for balance, the E for eyes, the second E for elbows, and the F for follow-through. To have good balance it is important to have you feet about shoulder width apart. Your eyes should always be focused on a target, and your elbows should be in line. Finally follow through means it sh...

This how to video shows you a six pack abs workout that will help you tone and tighten your stomach. Learn three of the best abdominal sculpting exercises to target your midsection.

This pilates how-to video illustrates the Swimming exercise. This pilates exercise is good for core stabilization, upper back extension and hip extension. This is good to improve back strength and those deep abdominal stabilizers.

This video pranking tutorial shows how to make a ketchup bomb out of ketchup and aluminum foil. The ketchup bomb will explode on contact with the target and make a sticky, staining, red mess. It's easy to make the ketchup bomb during lunch, saving the practical joke for whenever you're ready to strike. Learn how to make a ketchup bomb by watching this instructional video. Use this as inspiration for one of your April Fools Day pranks!