
How To: Learn fire techniques for making glass
Check out this video to learn techniques for making glass with fire. Enjoy the Pink Floyde tunes while you are at it.


Check out this video to learn techniques for making glass with fire. Enjoy the Pink Floyde tunes while you are at it.

This video will teach you how to dance like Michael Jackson and Khris Khaos. Be patient & enjoy Khris Khaos' dance demonstrations. In the last five minutes of this dance tutorial, Khris Khaos demonstrates several different Michael Jackson & Chris Brown dance moves. He does it slowly - so watch & learn!

Before making any of your favorite rice dishes, you'll need the basics of cooking white rice. This is what this video from StartCooking provides; it prepares you for any recipe that includes white rice. Enjoy!

An attempt to illustrate how one may start beat mixing 2 songs with different BPMs on a dual CD player (like most mobile DJs have). Today, we mix a little Chicago House. Enjoy!

Many people like to interview subjects outside because they enjoy the look of sunlight over tungsten lights. However, it can be difficult to work with such an uncooperative key light. In this Israel Hyman video are some ideas which can help you improve your outdoor interview imagery.

If you enjoy chips, but dislike store-bought salsa, this video is for you. While the time is obviously sped up, this is a simple Mexican salsa dish that can be made fresh with little effort.

Do you enjoy taking photos of exotic landscapes but not always getting the results you want? Software like Photoshop could help you solve your problem. In this video tutorial you will learn to improve dull landscapes using Adobe Photoshop.

This video teaches you the basic yet fundamental rolls of banjo. Among the rolls taught are the forward roll, the backward roll, the forward backward roll, and the alternating thumb roll. Enjoy.

Warm and crusty, this French bread is perfect for a baguette, or enjoy it with your favorite toppings and spreads. For this recipe you will need: water, kosher salt, yeast, unbleached flour, cornmeal and eggs.

Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will.

Sniffing packets over a network is an easy way for hackers to gather information on a target without needing to do much work. But doing so can be risky if sniffing packets on an untrusted network because a payload within the packets being captured could be executed on your system. To prevent that, Sniffglue sandboxes packet sniffing to provide an extra layer of security.

By using almost any packet-crafting tool, a hacker can perform denial-of-service (DoS) attacks. With the power to create just about any packet with any characteristics, a hacker can easily find one that will take down a host or network. Nmap and Hping are effective packet manipulation tools, but there's also Scapy, which is almost infinitely customizable.

The price of hacking Wi-Fi has fallen dramatically, and low-cost microcontrollers are increasingly being turned into cheap yet powerful hacking tools. One of the most popular is the ESP8266, an Arduino-programmable chip on which the Wi-Fi Deauther project is based. On this inexpensive board, a hacker can create fake networks, clone real ones, or disable all Wi-Fi in an area from a slick web interface.
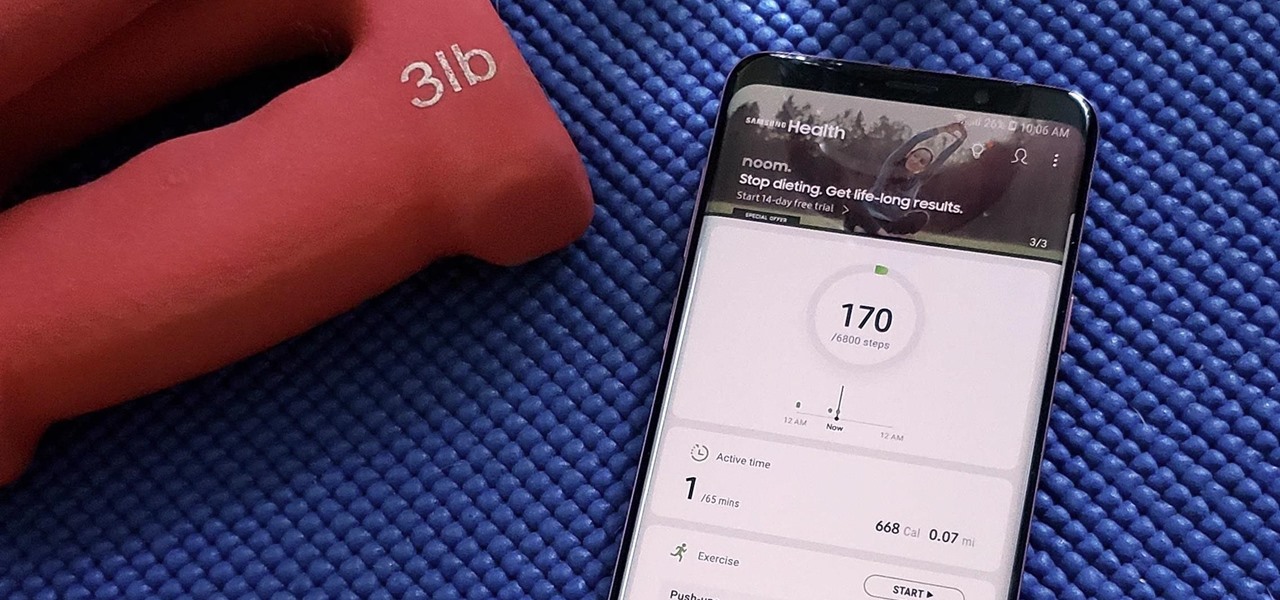
Samsung Health has become one of the most comprehensive wellness apps thanks to features that cover everything from step counting to nutrition logging and symptom diagnosis. But because the app has so much to offer, it can be easy to overlook some smaller, but useful features.

Hundreds of Windows 10, macOS, and Linux vulnerabilities are disclosed every single week, many of which elude mainstream attention. Most users aren't even aware that newly found exploits and vulnerabilities exist, nor that CVEs can be located by anyone in just a few clicks from a selection of websites online.

PUBG is currently taking the mobile world by storm, and it's easy to see why. The game has breathed much-needed life to the multiplayer shooting genre, primarily by adding an element of sheer terror as you scavenge for weapons in a hostile environment. With new players continually joining in on the fun, many players are looking for ways to gain an edge.

Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutorial, we'll use Python to target specific software vulnerabilities and extract vulnerable target IP addresses from Shodan.

Seriously, what's with all of the candy corn hate? I don't care what anyone says, candy corn is and always has been the perfect Halloween snack for me. Only recently did I realize that not everyone gets as hype as I do about small, sugary vegetables.

If you love sitting poolside with a slice of watermelon, then I've got a real treat for you. Picture yourself cooling off with a slice of juicy watermelon topped with fresh ingredients like soft cheeses, herbs, and fresh summer fruits. Watermelon pizza is a wondrous thing—a creative take on the classic watermelon salad, only pizza-fied!

Last week's tech roundup featured iPhone 6 clones, an all-in-one sleep tracker, Xbox One updates, and other cool gadgets. This week, there's a lot more to show off, and a bunch of stuff that I need to get my hands on! Everything from app updates to putting stickers on your favorite items, I can't help but squeal at how much the "future" is right now.

The discomfort and inconvenience that comes from knee and hip pain can prevent you from enjoying the things you love. As part of the Johnson & Johnson Family of Companies, DePuy is a global leader in finding solutions in orthopaedics, spinal care, sports medicine, and neurosciences. Check out this video from DePuy to learn how a real-life patient was able to enjoy one of DePuy's many movement solutions and return to living a normal life.

Updating from iOS 6 to iOS 7 on the Apple iPad mini is as easy as opening the settings, tapping on Software Update, then pressing Install now and agreeing to the Terms and Conditions.

Learn how to prepare absinthe, the classic drink of Van Gogh and many other depressed French painters! This video features a great and simple how to mix absinthe along with a cool soundtrack--it's sure to get you seeing the Green Fairie in no time! Absinthe has never been so simple to prepare and enjoy! Drink absinthe with caution, and enjoy!

A lot of you are enjoying a nice winter snowfall right now. Some of you aren't enjoying the snow at all, especially if your car's stuck in it or you have to grab the snow shovel, yet again. But perhaps you'll change your distaste for snow when you try out some tasty homemade snow cream!

There is nothing tastier than bleu cheese dressing, especially when it is made fresh! Bleu cheese goes well on salad, chicken wings, veggies, even bread! This recipe is incredibly easy to make and you can keep it in your fridge and use it for quite a while. Enjoy!

Check out this informative video tutorial from Apple on how to enjoy and organize videos in iMovie '09.

If you're looking for a solid defensive play while enjoying Madden NFL 12, try out this ultra fast nano blitz in the 46 bear formation. The adjustments on this play are very simple and allow you to sack the QB before he even knows what's coming.

If you have pictures, videos, or a presentation you want to share with a larger audience, or enjoy on a larger screen than the one that your Nokia Booklet 3G comes equipped with, grab an HDMI cable.
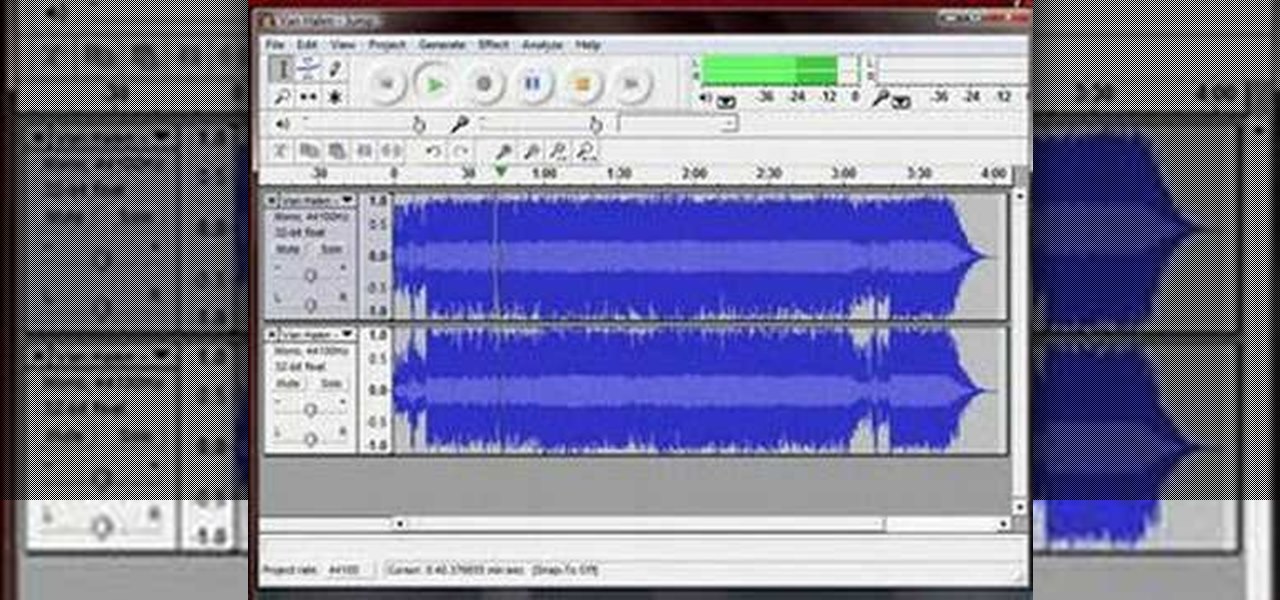
Edit your audio using the invert effect in Audacity. Once you follow this tutorial on applying a minus one to your track, you'll be good to go! You can download Audacity for free by going to this website. Enjoy!

Curious about Google's new social network, Google+? Get the rundown by watching this video and learn the ins and outs of Google plus, including the circles feature, the chat feature, photos and more. This is your video guide to Google+.

Keep your Runescape account safe from hackers by following the instructions in this video. Don't get hacked by giving your password away or using unsafe websites. Watch this video and learn how to take precautions against hackers so you can enjoy Runescape worry free.
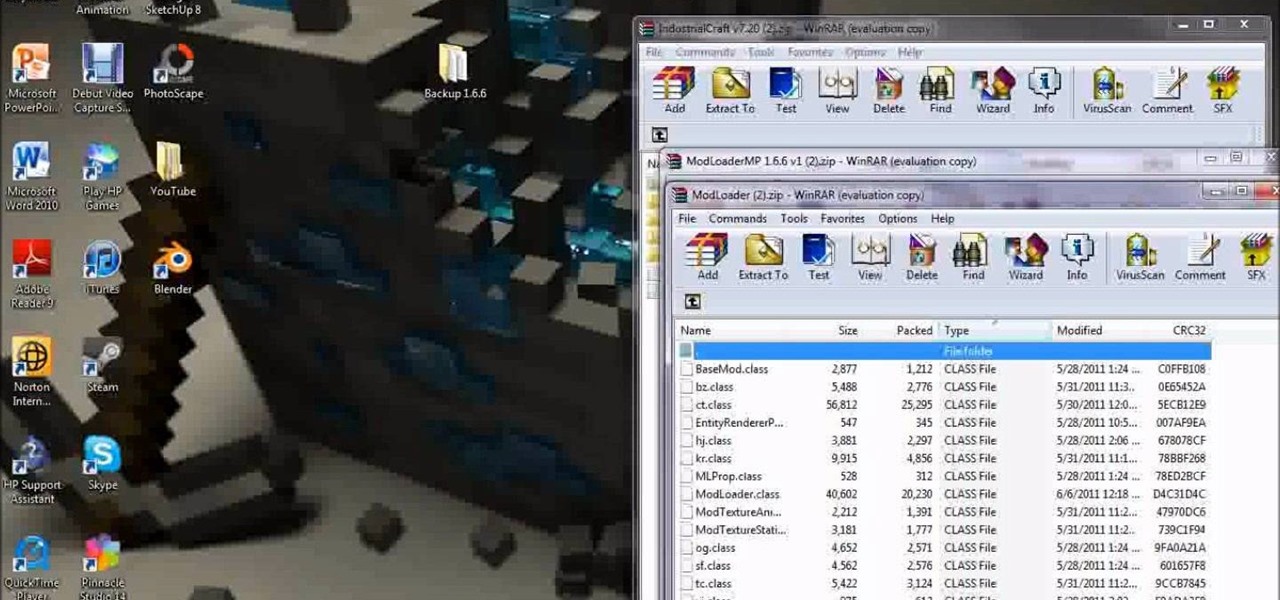
Explore a whole new Minecraft world with Industrial Craft. Watch this video to learn how to download and install the Industrial Craft mod for Minecraft beta 1.6.6. The Industrial Craft mod has all kinds of new items for you to enjoy, check it out.
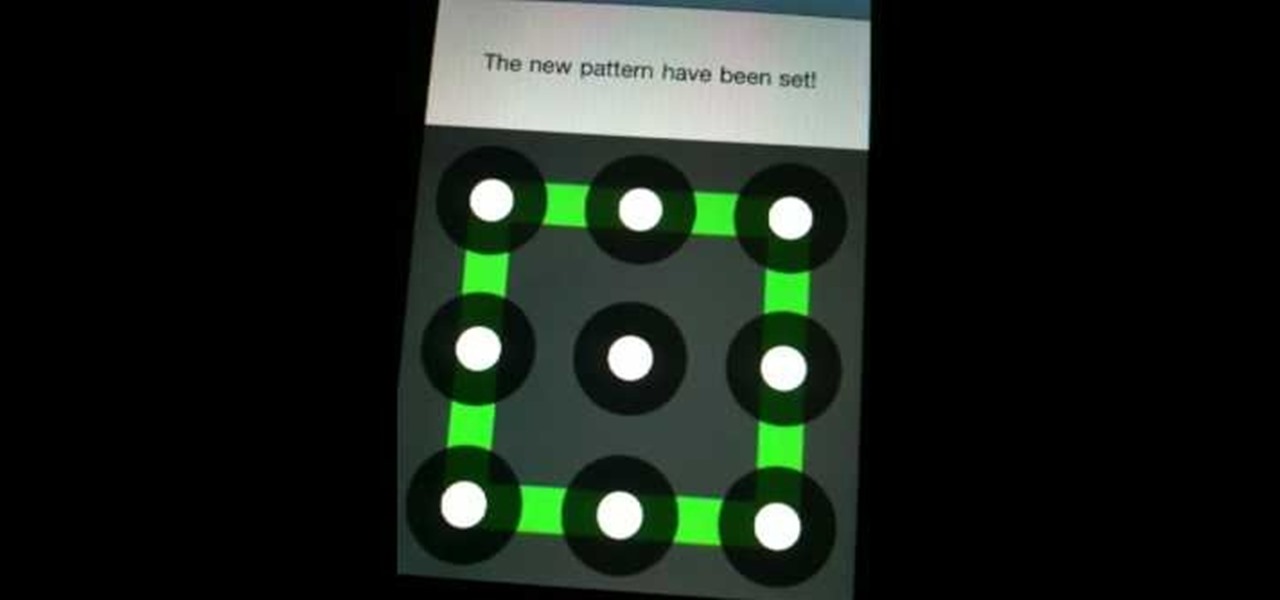
iPhone and Android both have a lot of great features. Enjoy the best of both worlds when you install Android lock on your iPhone. This is a great way to secure your iPhone. Use Android lock to get an extra layer of security.
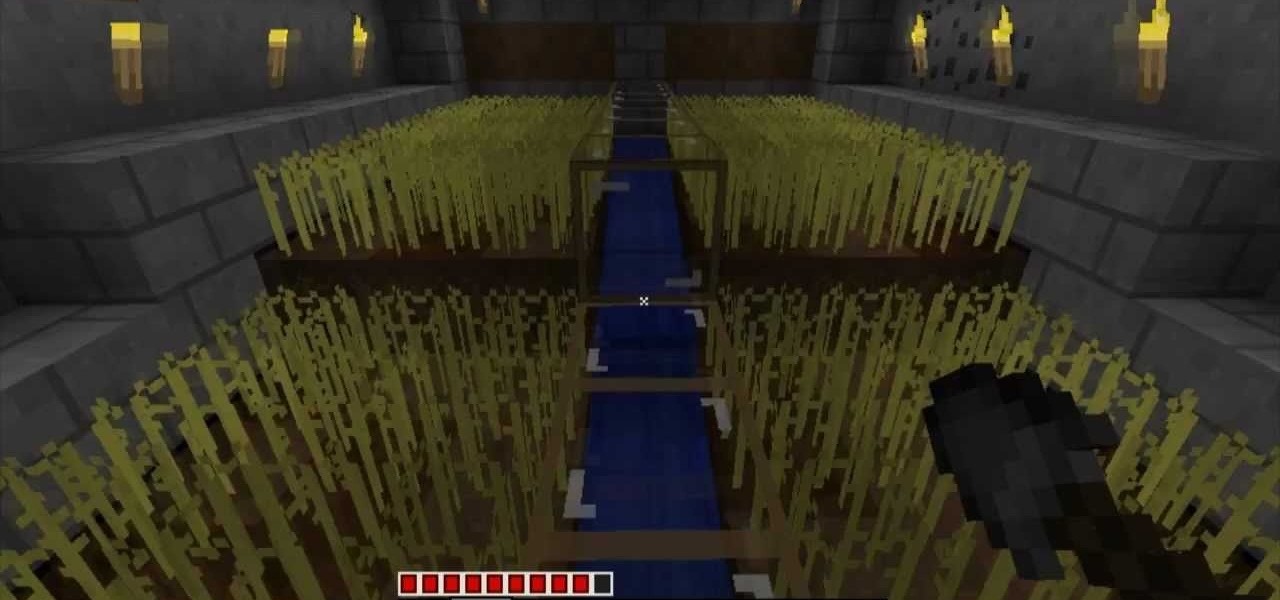
Looking for the most efficient wheat farm design in Minecraft? This might be it. Check out this video and learn how to build an automatic wheat farm, with self-harvesting technology. Enjoy all the fruit and none of the labor with this Minecraft build.
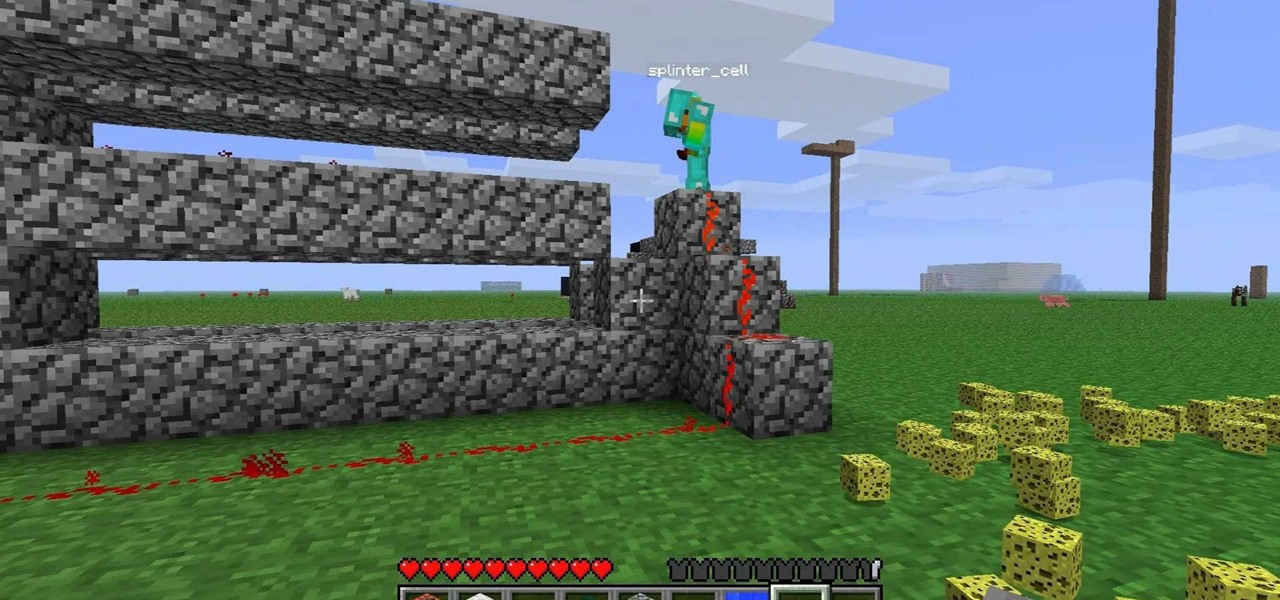
Since the dawn of Minecraft, Minecraft playing gamers have dreamed of flying through the skies. Now, the dream has come true. Watch this video to learn how to build a TNT powered person launching cannon. Strap yourself in and enjoy the ride.

Looking to get online with your Nintendo 3DS so you can play your favorite DS games with your friends? Watch this video to learn how to set up a Nintendo 3DS on a wireless network so that you can enjoy handheld online gaming.
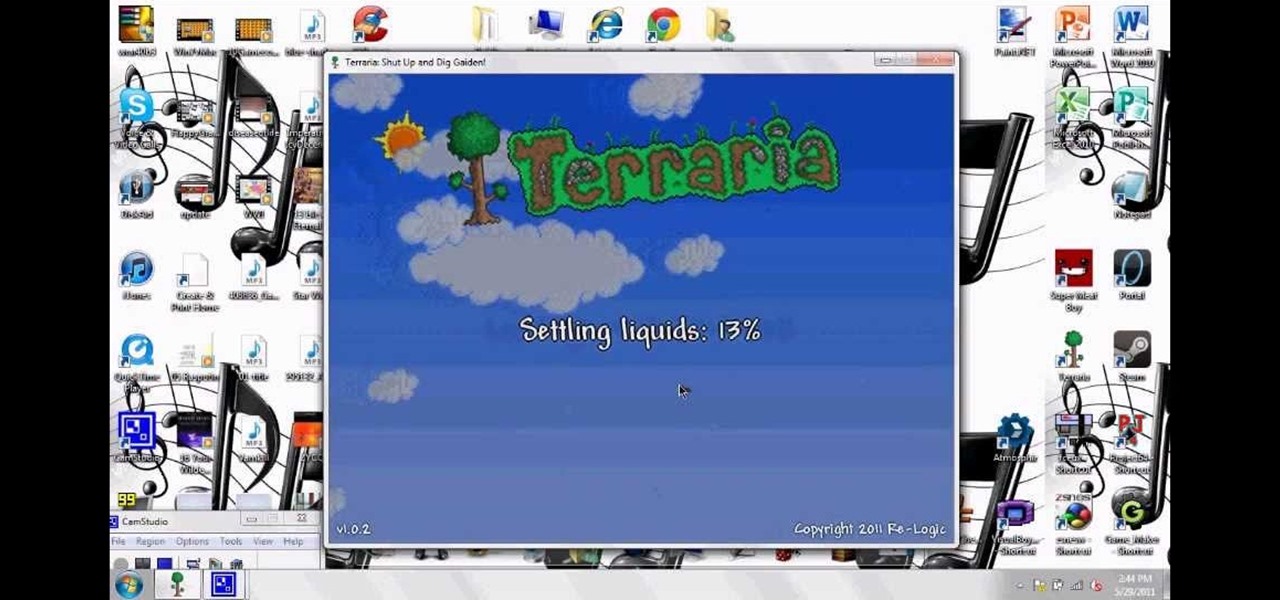
How much fun does multiplayer Terraria sound like? Get all your friends together to play Terraria on your own server, after watching this video and downloading Portforward and
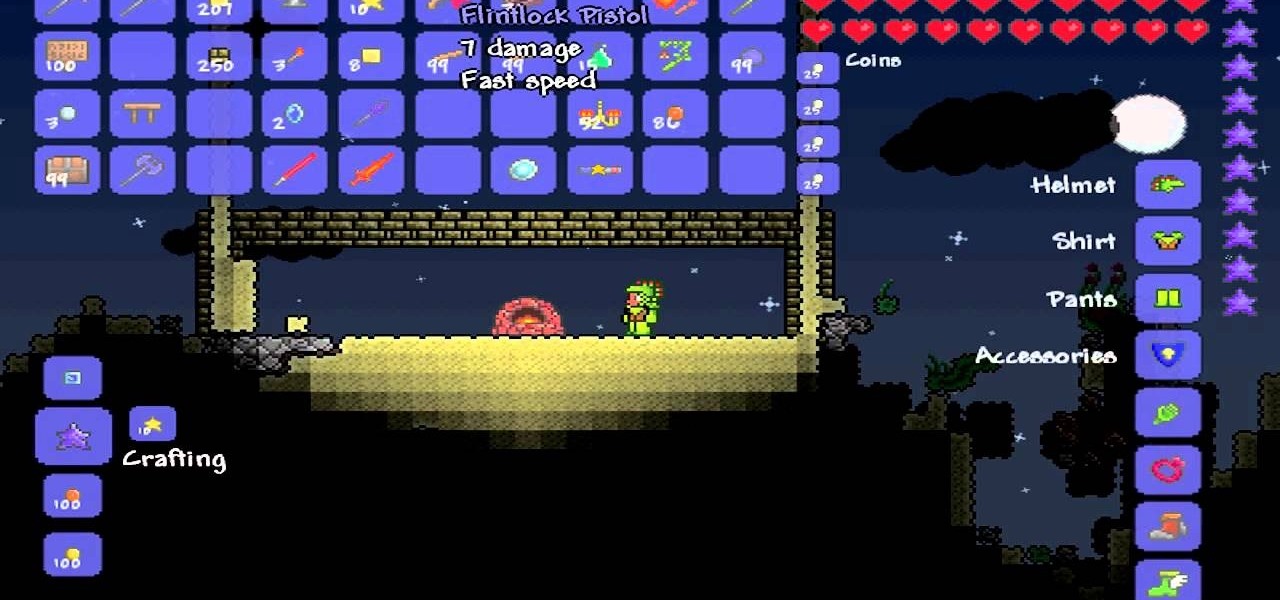
Whether it only exists in Terraria or not, you want a space gun. Watch this video to learn which materials are used in what combination to craft a space gun in Terraria. You will definitely enjoy having a space gun.

Check out this helpful video to learn how to configure the settings on your Samsung Epic so that you can enjoy Netflix streaming. The Netflix app won't work with just any Android device, unless you follow the instructions in this video.
if you've already seen this video and you are playing Minecraft on your own server, you're ready to start playing on custom maps. You can download maps here. Custom maps make playing Minecraft even more fun. Enjoying exploring these new worlds!