So you've managed to get a shell on the target, but you only have measly low-level privileges. Now what? Privilege escalation is a vast field and can be one of the most rewarding yet frustrating phases of an attack. We could go the manual route, but like always, Metasploit makes it easy to perform local privilege escalation and get root with its exploit suggester module.

EternalBlue was a devastating exploit that targeted Microsoft's implementation of the SMB protocol. Metasploit contains a useful module that will automatically exploit a target, as long as it's vulnerable. But what if we wanted to exploit this vulnerability without Metasploit holding our hand? It can be done using a Python file to exploit EternalBlue manually.

It's easier than you might think to hack into Wi-Fi routers using just one unrooted Android phone. This method doesn't require brute-forcing the password, a Windows OS for converting PowerShell scripts into EXE format, a reliable VPS for intercepting hacked Wi-Fi passwords, or Metasploit for post-exploitation tricks.
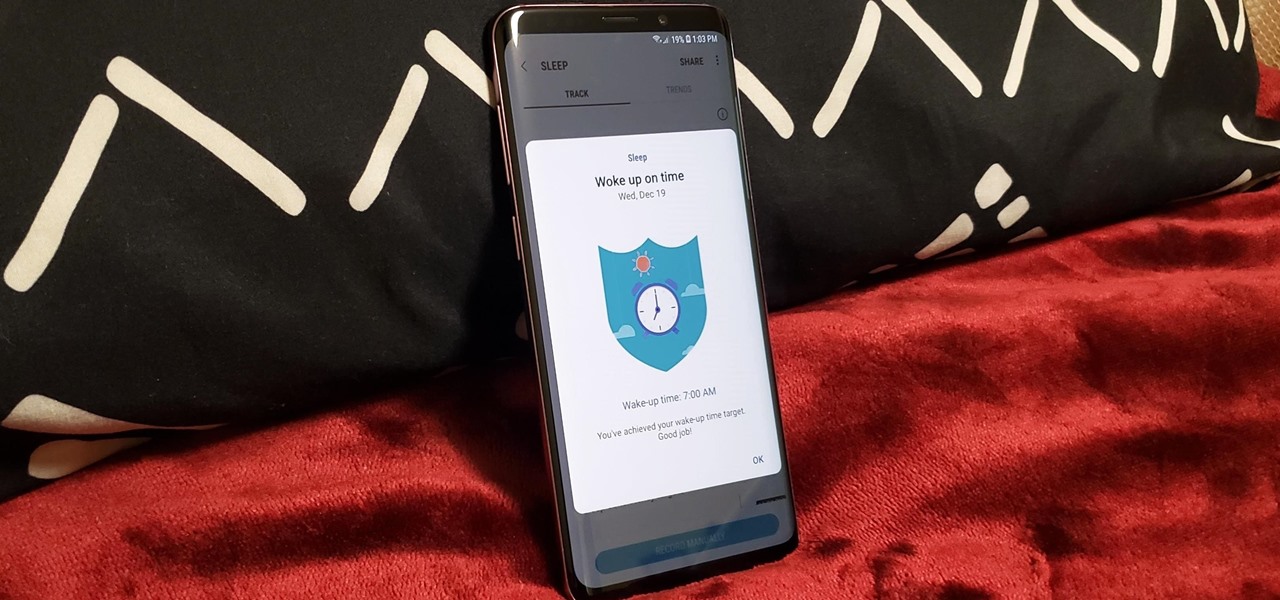
The quality and length of your sleep will almost always dictate how the rest of your day unfolds. Sleeping fewer hours increases your chances of spending the day in a tired and cranky state, while having a restful night's sleep contributes greatly to being alert and productive. Luckily, if you want to track your sleep patterns to figure out how you can improve your circadian rhythm, Samsung Health has you covered.
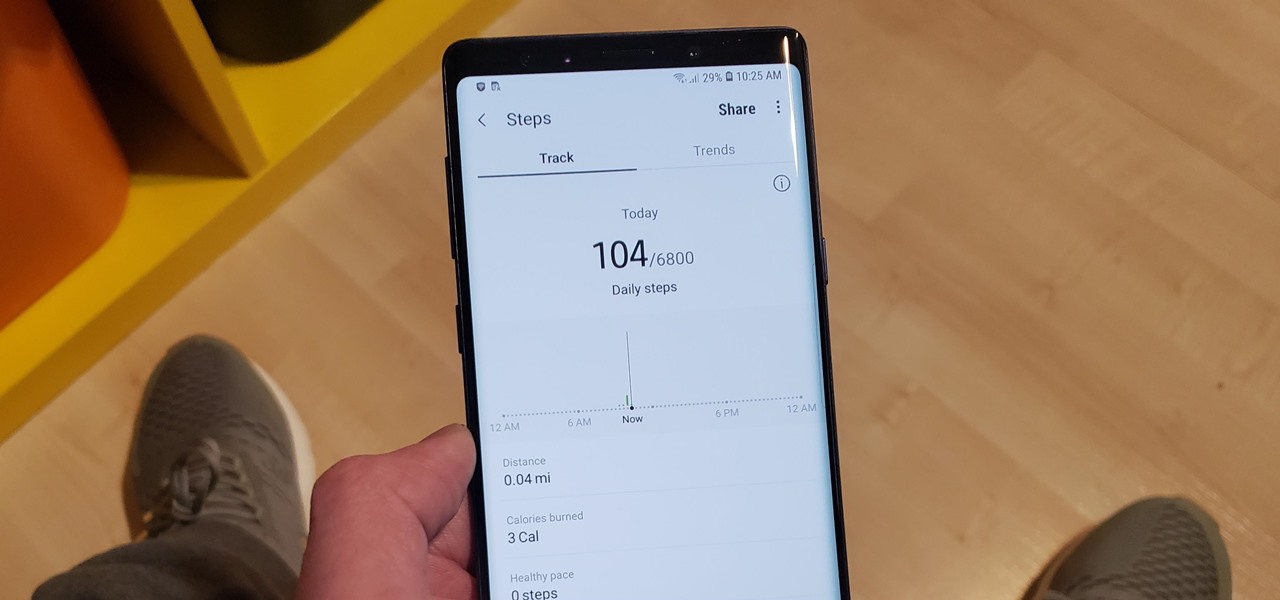
Once known as S Health, Samsung Health has become one of the most comprehensive health apps available for Android. In fact, we all can benefit from the features the app brings to the table — whether you're a marathon runner or a couch potato. If you're in the latter category, the app has a simple feature that can nudge you towards becoming more active.

Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless attack framework called Airgeddon is used to find vulnerable networks, and then Bully is used to crack them.

Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life.

Facebook really wants your phone number, nagging you for one as soon as you join. This isn't all bad since it can help secure your account with two-factor authentication. On the flipside, this makes it easy to reveal the private phone numbers of virtually anyone on Facebook, including celebrities and politicians. We're going to look at how a hacker would do this and how to protect yourself.

If you've ever wanted to hone your paintball skills, without spending a ton of money and making a huge mess, Show Me Virtual and Apple's ARKit have an app for you.

Anyone who paid attention to the Lavabit shutdown had a feeling it was connected to Edward Snowden, the high-profile NSA whistleblower. Ever since the government's case against Lavabit went public in late-2013, people have put two and two together.

Greetings dear null byters, today we start a new series, we will start to attack users using social networking that are popular such as Facebook, Skype, and much more, and in part 1 of the series will engage users of Skype.

Do you remember my last article on how to hook any web browser with MITMf and BeEF? Well, we are using the tool once again, but this time for auto-backdooring....

Hello, ladies and gents! Today I will be discussing the fun and excitement of backdoor on an OSX system.

In this how-to video, you will teach your dog how to target objects with its front paws. You will need a clicker, treats, and a target such as a yogurt lid or ball on a stick. Take a treat and hide it under the object. Click when the dog does any paw movements towards the object. After ten successful tries, pretend to put a treat. Once the dog paws the object, show that there is no treat but still give the dog a treat. Once this is done, wait until the dog paws the object, and give a treat. I...

A lot goes into making a hunt successful, and most of it happens before you take to the field--like making sure your rifle is properly sighted in. It's not hard to do if you follow a few simple steps: first, and this is the first step when you do anything with a firearm, make sure it's unloaded. Make sure your scope is properly mounted and the mounting screws are tight. Remove the bolt from the rifle and sight through the barrel to make sure you're lined up with a sight-in target placed at 25...

Your target in level 3-13 of Angry Birds is not so much a pig fortress but a series of pig-defended hilltops. Still no problem for a properly trained bird army. Watch the video for a guide to beating level 3-13 with three stars.

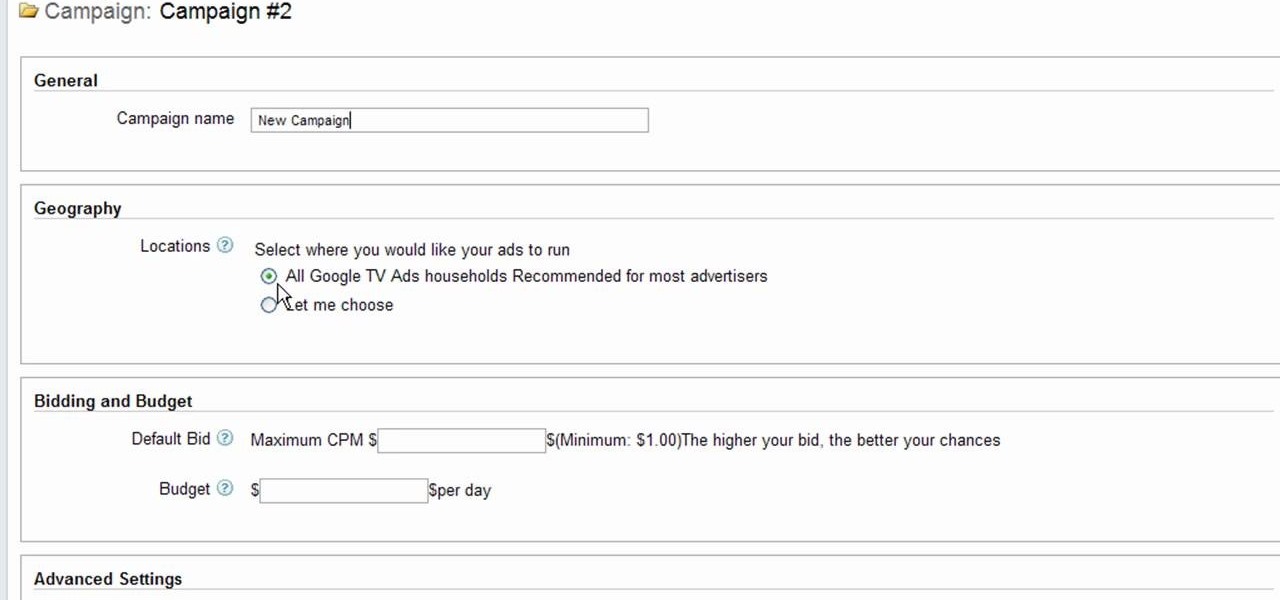
Interested to know how to start a new cable television ad campaign with Google AdWords TV Ads? This official video from Google will teach you how to use the new interface to determine just that. For all of the relevant details, and to get started creating your own televised advertising campaigns, watch this clip.

It's been a few years since Finding Nemo became the highest-grossing animated film of all time, but it's cultural appeal lingers on. If you want to capture some of that Nemo cuteness for your Halloween costume, watch this video to learn how to make a really cute Nemo costume with no sewing required.

The ground and pound is one of the most controversial aspects of MMA fighting, and is a great chance for you to do a lot of damage to your opponent. In this video UFC fighter Joe Lauzon will show you how to use an elbow technique from guard to defend yourself and get a solid elbow shot in at the same time, using Joanne from MMA Girls as his target.

Halo: Reach has so many tough to get achievements, but the easiest one that you can get pretty fast is the "Crowd Control" achievement, and you can get it on Courtyard using the target locator. In this video you will learn how to effectively kill off multiple Covenant drop ships to get the achievement in about five seconds!

Two Corpses in One Grave is a difficult achievement in Halo: Reach if you don't know where to look on mission 3. You will have your chance right after you acquire the Target Locator when two Wraiths show up for the killing! Just be sure to aim straight and true and you will be alright!

Thanks to modern technology, we don't have to visit our nearest Target or Rite Aid to get our pictures professionally retouched and printed. With many printers offering photo-quality ink and paper companies that offer photo-quality paper, you can use your home printer to create professional-grade photos.

If you're planning to become a veteran yogini, you'd better start practicing and loving the up dog pose now, because you'll be spending the greater part of your yoga flow doing up dogs and down dogs.

Sometimes searching Craigslist can be a real hassle if you're looking for something specific. You really have to sort your way through all the clutter in order to find whta you're looking for. If you are looking for email addresses of people who might fit your target market, you can scrape Criaglist for emails. This video will show you how.

In this episode of Hak5, Darren shows us a USB key, dubbed the USB Hacksaw, that instantly and silently installs on target Windows 2000 or higher computers with guest or higher privileges which will monitor USB ports for flash drives and automatically download their contents for silent archival and email. For detailed instructions on replicating this hack yourself, watch this video hacking tutorial.

Privilege escalation is one of the essential skills a hacker can have and often separates the newbies from the pros. With a continually changing landscape and a plethora of exploits out there, it can be a problematic aspect of any attack. Luckily, some tools can help expedite the process. Linux Exploit Suggester is just one of many to help you get root.

Arduino is a language that's easy to learn and supported on many incredibly low-cost devices, two of which are the $2 Digispark and a $3 ESP8266-based board. We can program these devices in Arduino to hijack the Wi-Fi data connection of any unlocked macOS computer in seconds, and we can even have it send data from the target device to our low-cost evil access point.

No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today, we will be covering three methods of patch enumeration, using Metasploit, WMIC, and Windows Exploit Suggester.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.

The ability to execute system commands via a vulnerable web application makes command injection a fruitful attack vector for any hacker. But while this type of vulnerability is highly prized, it can often take quite a bit of time to probe through an entire application to find these flaws. Luckily, there is a useful tool called Commix that can automate this process for us.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

Epic Games just released update v3.4 for Fortnite Battle Royale on all four platforms. This new version brings a number of UI changes, performance improvements, and bug fixes, but the addition that will get the most players excited is a new weapon: the Guided Missile.

RouterSploit is a powerful exploit framework similar to Metasploit, working to quickly identify and exploit common vulnerabilities in routers. And guess what. It can be run on most Android devices.

In an effort to make its services more accessible to users who live in developing countries, Facebook has released a streamlined version of its messenger app. Messenger Lite, at less than 5 MB, is much smaller than its regular 25 MB counterpart and was developed for use on older and lower-end phones. Finally, the app is now available for download in the US.

The search for a cancer treatment that selectively finds and kills only the cancerous cells has just made a giant leap forward.

Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scanning, with Nmap for port scanning, and with its numerous auxiliary modules, nearly unlimited other hacking related capabilities.

Five Phases of Hacking:- The five phases of Hacking are as follow:

Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this field will likely help you land a Security Engineer position or put you on the Incident Response Team at your employer.