A macOS computer can reveal a lot of information about the owner, including which Wi-Fi network they have permission to access. With an Arduino-based attack, we'll use a five-dollar setup to inject a rogue Wi-Fi network and steal the list of trusted Wi-Fi networks, allowing us to see where the computer has been.

While Snapchat is no stranger to location-based AR scavenger hunts, the app's new world-facing game adds some environmental understanding to the mix.

Pyrit is one of the most powerful WPA/WPA2 cracking tools in a hacker's arsenal, with the ability to benchmark a computer's CPU speeds, analyze capture files for crackable handshakes, and even tap into GPU password-cracking power. To demonstrate how quickly it can hack a WPA/WPA2 password, we'll use it to play a Wi-Fi hacking CTF game anyone can practice for less than $10.

Silicon Valley-based startup 8th Wall has spent much of the last few years building a reputation for enabling AR experiences that are platform agnostic via web browsers and mobile apps. Now, 8th Wall is promising to give developers the freedom to build and host AR experiences from anywhere via a simple web browser.

Viewing and reading content on websites is inherently harder to do on an iPhone due to the relatively small display. Even if you have an iPhone XS Max or 11 Pro Max, you'll probably struggle sometimes to read through tiny text while browsing online. Thanks to a feature found within Safari's view menu in iOS 13, your eyes can rest a little easier.

Google is going all in with Childish Gambino as its musical champion for augmented reality, as the duo has now dropped its second AR collaboration of the year.

What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, a tool called Airgraph-ng can visualize the relationships between Wi-Fi devices from only a few seconds of wireless observation.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

After getting confirmation from Tim Sweeney, CEO of Epic Games, we now know Fortnite Battle Royale will not be available on the Play Store when it's finally released for Android. Instead, users will have to download the APK directly from Epic Games' website — and quite frankly, this is a bad idea.

Wi-Fi tools keep getting more and more accessible to beginners, and the LAZY script is a framework of serious penetration tools that can be explored easily from within it. This powerful and simple tool can be used for everything from installing new add-ons to grabbing a WPA handshake in a matter of seconds. Plus, it's easy to install, set up, and utilize.

Don't think because your MacBook is using FileVault disk encryption your device is secure or immune to hackers. Here's how to find out if that FileVault password is strong enough to withstand an attack from a motivated attacker.

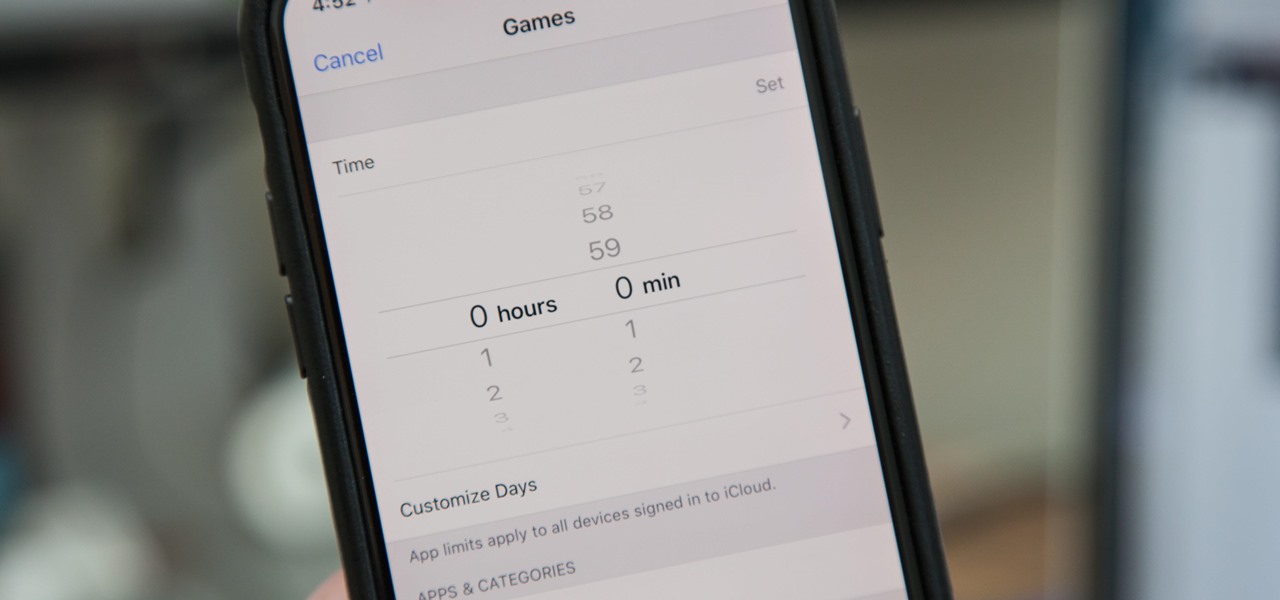
Most of us have, at one point or another, found ourselves glued to our smartphone in a trance-like state, totally unaware of what's around us. Well, Apple has a way to curb overuse with an awesome tool for iPhone starting in iOS 12. It can help nudge us away from our phones to spend more time attending to real-life matters.

Developed by Open Whisper Systems, Signal is a free, open-source encrypted communications app for both mobile and desktop devices that allows users to make voice calls, send instant messages, and even make video calls securely. However, a vulnerability was recently discovered for the desktop version that can be turned into a USB Rubber Ducky payload to steal signal messages with a single click.

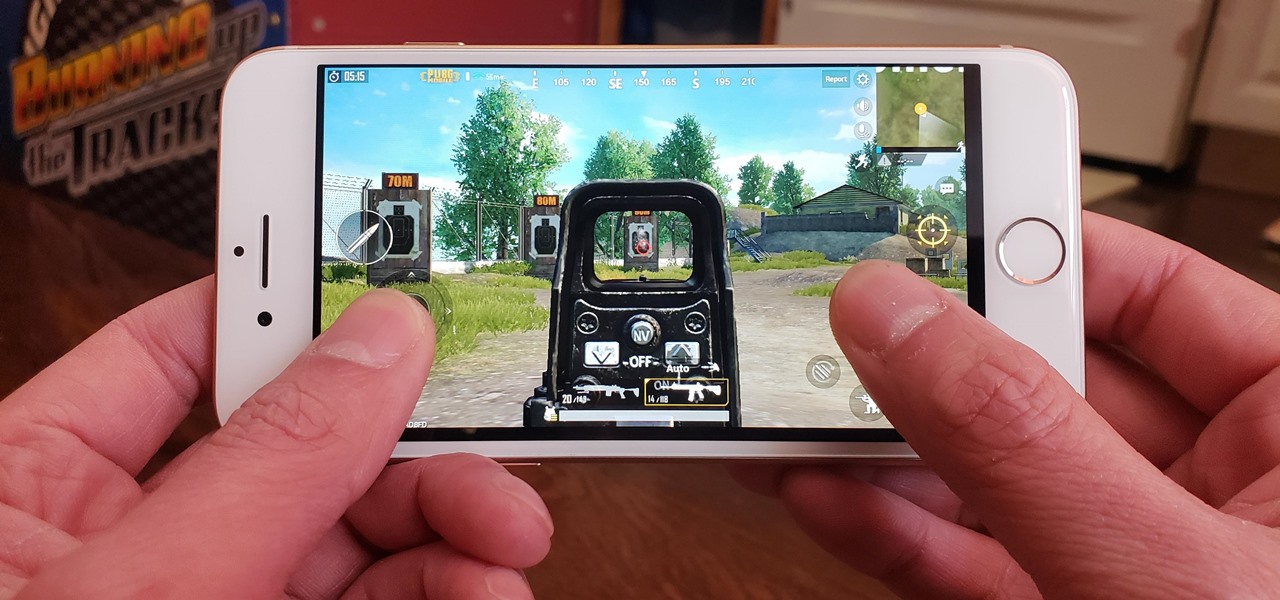
PUBG is continually getting better and more intuitive with each update, and version 0.4.0 is no exception. Besides a new training map to help you practice and a faster-paced arcade mode for on-the-go gaming, the newest version of PUBG now includes a feature that exclusively caters to iPhones from the 6S on up.

While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one. This forces the victim to connect to the fake network and supply the Wi-Fi password to regain internet access.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

There are more than 2 billion Android devices active each month, any of which can be hacked with the use of a remote administration tool, more commonly known as a RAT. AhMyth, one of these powerful tools, can help outsiders monitor a device's location, see SMS messages, take camera snapshots, and even record with the microphone without the user knowing.

In a previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when a Microsoft Word document is opened. The biggest challenge of this attack is that it requires getting the user to agree to a pop-up prompt. Fortunately, since I posted that article, many new obfuscation techniques have been discovered to make this easier. Today, we explore and combine some of them to make the ultimate hidden DDE attack.

With a new installment of the Saw horror series opening in theaters nationwide this weekend, Lionsgate is betting its ad dollars on immersive advertising to sell tickets.

If you need to scan a large number of domains for a specific web app vulnerability, Dorkbot may be the tool for you. Dorkbot uses search engines to locate dorks and then scan potentially vulnerable apps with a scanner module.

PowerShell Empire is a post-exploitation framework for computers and servers running Microsoft Windows, Windows Server operating systems, or both. In these tutorials, we will be exploring everything from how to install Powershell Empire to how to snoop around a target's computer without the antivirus software knowing about it. If we are lucky, we might even be able to obtain domain administrator credentials and own the whole network.

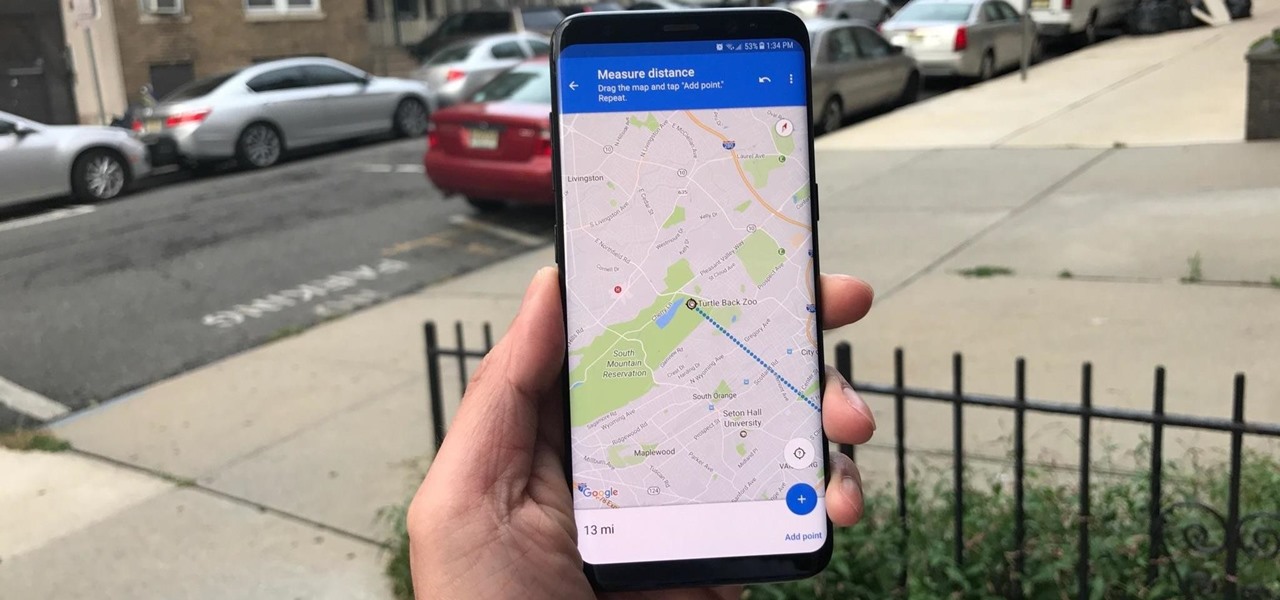
If you want to find out the linear distance between your hotel and a landmark or restaurant you want to visit, Google Maps has a great feature that lets you quickly measure the distance between two or more points. It's perfect for getting an idea of how far places are in relation to each other, which can help you plan trips more efficiently.

Natural remedies used through the ages abound, especially in Asian medicine. The willow-leaved justicia plant, found throughout Southeast Asia, has traditionally been used to treat arthritis, but scientists have just discovered it contains an anti-HIVcompound more potent than AZT. AZT was the first drug approved to treat HIV, and is still used in HIV combination therapy today.

In our first part on software-defined radio and signals intelligence, we learned how to set up a radio listening station to find and decode hidden radio signals — just like the hackers who triggered the emergency siren system in Dallas, Texas, probably did. Now that we can hear in the radio spectrum, it's time to explore the possibilities of broadcasting in a radio-connected world.

When the mosquito that carries the malaria parasite (Plasmodium falciparum) bites someone, the parasite must travel to the liver where it undergoes part of its lifecycle before infecting red blood cells and spreading to its next host. Until now, the first step of how the parasite gets to the liver hasn't been clear.

With a predicated increase in the number of Lyme disease cases in the coming spring season, new research endorses the use of bait boxes to control ticks on the rodents that serve as their hosts.

In a world increasingly regulated by computers, bugs are like real-life cheat codes. They give you the power to break the rules and do good or bad without ever leaving your seat. And government agencies around the world are discovering and stockpiling unreported bugs as cyberweapons to use against anybody they see fit.

The rate of preterm birth has been increasing in the United States for unknown reasons, causing increased health risks for infants born too soon. But researchers may have found a signal that could help doctors plan ahead for, or even prevent, early birth with a simple swab of the vagina and cervix during pregnancy.

The YouTube app for Android doesn't exactly offer the greatest user experience. For one thing, it opens to an arbitrary "Home" tab instead of your subscriptions, so you see a list of what YouTube thinks you want to watch instead of your favorite channels. In addition to that, videos are loading at a mere 144p playback resolution for many users lately, which is downright terrible quality.

As a commercial and potentially consumer product, one might assume it very unlikely to see the Microsoft HoloLens in the military marketplace. And that assumption would be completely wrong. One company from the Ukraine is currently working on using the mixed reality head-mounted computer for 360-degree vision inside armored tanks. If a tank crew could see the entire battlefield there are in, they would likely have a better chance of accomplishing their mission and avoiding damage. Tanks are l...

Since the days of flip clocks, alarms have always had one function—make a bunch of annoying racket early in the morning to ensure that you wake up in time. And this simple MO has stayed in place while technology advances at a breakneck pace, almost in spite of the fact that today's devices are capable of doing far more than beeping at 7 in the morning.

This card looks fabulous and it is so easy to put together, the longest part is cutting the paper, but if you enjoy papercutting then this is just for you, however you could adapt the design and use the full Rope design paper from Anna Griffin to create this beauty. I have used embellishments and paper cut shapes to add to the card front and create something really cool. Step 1: Now Watch the Tutorial

Over the course of the past century or so, media consumption has gone from a few readers enjoying their local print publication to billions of users viewing countless hours of video across the globe each day. This was a gradual evolution at first, but recent advancements in mobile connectivity have sent us into a climb the likes of which we have never seen before.

Here I will show you how to properly dig information on the web that has already been published, you just dont know it.

Hello again, folks! I'm back with another (final) guide on runtime crypters which is an extension on my previous runtime crypter guide. If you have not read it yet, I highly recommend that you do since the fundamental theory of the PE format. Again, this will be a Windows-specific guide, so I'll repeat this: If you're a hater and cringe at the slightest sound of Microsoft's grotesque baby, feel free to close this tab, delete your history, exit your browser, pour some oil onto your machine and...

This video was shot in de beautiful and modern city of Rotterdam, in the netherlands, starring the dutch break dancer Stefan Dirven accompained by the song "Freestyle - Crystal ball"

If your struggling to get fit your not alone. Following my struggles and victories as a become a fitter me. if you enjoy my videos please, like and subscribe!

Let me share some great information on stair climbing and how it can provide many health benefits. Burn more calories stair climbing that jogging or running. See how in the video. If you enjoy the video and would like to see more, please hit the subscribe button. I hope this helps!!

For the christmas incoming, how are you going to decorate your house or what kind of present would you like to make for your children. This video show you how to simply make a snowman from basic things: socks, rice..

This is a step by step video tutorial on how to make this beautiful hemp choker necklace with macrame knots such as alternating square knots, alternating half hitches, braids, and cowrie shells. Enjoy!!