Do you ever thought that you can't control an Internet disconnected system? I saw a funny video in Chema Alonso's youtube channel (A well-known hacker of my country and creator of Fingerprinting Organizations with Collected Archives among other security tools), and decided to post something similar.

A lot of people think that TOR services are unhackable because they are on a "secure environment", but the truth is that those services are exactly the same that run on any normal server, and can be hacked with the same tools (metasploit,hydra,sqlmap...), the only thing you have to do is launch a transparent proxy that pass all your packets through the TOR network to the hidden service.

Hello null_byters, after some time out here we are again with another tutorial, continuing our beautiful series, today we will write our first real world bash script.

As an American to who is married to a Korean and living in Korea, I have gotten chances to experience Korean Thanksgiving called Chuseok (??).

Hello~ Here is a simple recipe that Koreans love and have grown-up eating. It is a great recipe for a quick meal and if you make a large amount it is great for leftovers!

Hello~ Here is a short video on how to do a simple hairstyle for when you are wearing a Korean Hanbok.

Black Friday and Cyber Monday are becoming almost synonymous these days, but there are still plenty of awesome deals that you can only get starting on the Monday after Thanksgiving. Amazon, for instance, will be hosting a week-long Cyber Monday sale, and of course, most big-box retailers will follow suit with their online stores.

The first video is a demonstration or throwing punches i bunches while staying on balance! The second video is a example of how a coach or trainer should spar with his/students.

Halloween is coming up and skulls never go out of trend! I created this cool sexy blonde-looking skull to spice the whole skull Halloween look up! Hope you enjoy. All of the products are in the description box of the video on YouTube.

The following are simple Halloween pranks you can set up on friends and family members for the scariest night of the year. They all require common props you can get at your local dollar store, especially during the halloween season! have fun and enjoy!!

I hope you will enjoy it and learn how to make the aircraft.

Hi! I'm Kasia from CreativePetKeeping and this is my guide to owning gerbils. Hope you enjoy!

Hi, my name is Alan, and I am not a script kiddy brat from Xbox Live asking you how to boot someone offline for being mean to me. I am an amateur white hat hacker hoping to learn and teach and this is my first tutorial.

I saw a video that Kurz Gesagt made about the Fermi Paradox, and I liked how the video was made, so I looked up what else they had, and came across this:

This video is a Ahi poke dish, you don't have to go all the way to Hawaii to enjoy this awesome dish. Its a great summer and party dish and easy to make.

This ship is over 4 ft. long with many moving parts all run from a live steam engine. There are two videos, one more detailed about the story and one blog showing how it was built. Hope you enjoy.

The basics of how to pack personal gear for a canoe trip. This video doesn't cover food or larger gear like tents and canoes, but the rest is covered. Enjoy!

Hi again! Here's another dessert recipe—today it's a custard cream recipe, or what is also called creme patissiere.

Welcome back, my budding hackers! With this article, I am initiating a new series that so many of you have been asking for: Hacking Web Applications.

Hi again! :) Many people have been asking me to do a lesson about what to say when you visit the doctor in Lebanon, so here's that lesson. So if you're sick, I hope you get well, and I hope you enjoy this lesson and find it useful.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Inspiration for tutorial: Foxtrot's "How to Trap a Tracker"

Hi again, everyone! I hope your enjoying this winter. Here are some sentences you might use if you are spending your winter in Lebanon.

This is a simple drawing tutorial, in which I show you a super easy way to draw a cute cartoon owl! It's a basic line drawing, so it's perfect for beginner artists - enjoy! :-)

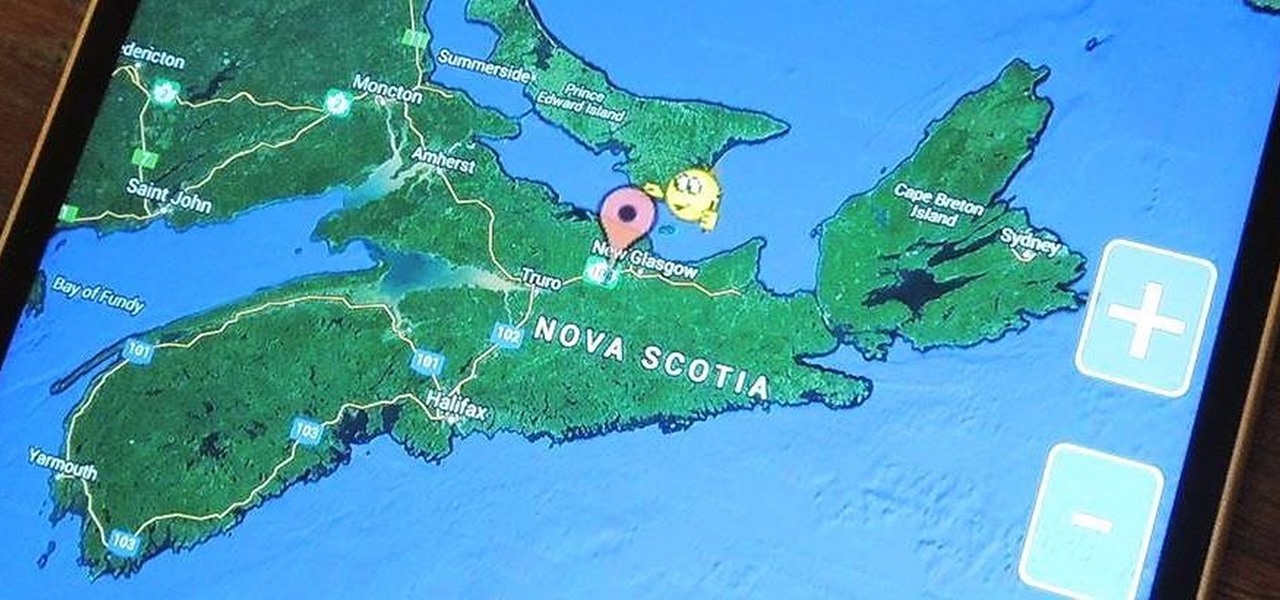
You wouldn't send your GPS coordinates to a completely random stranger just because he or she asked you for it, right? So why are you constantly sharing your location (and other data) to apps on a daily basis?

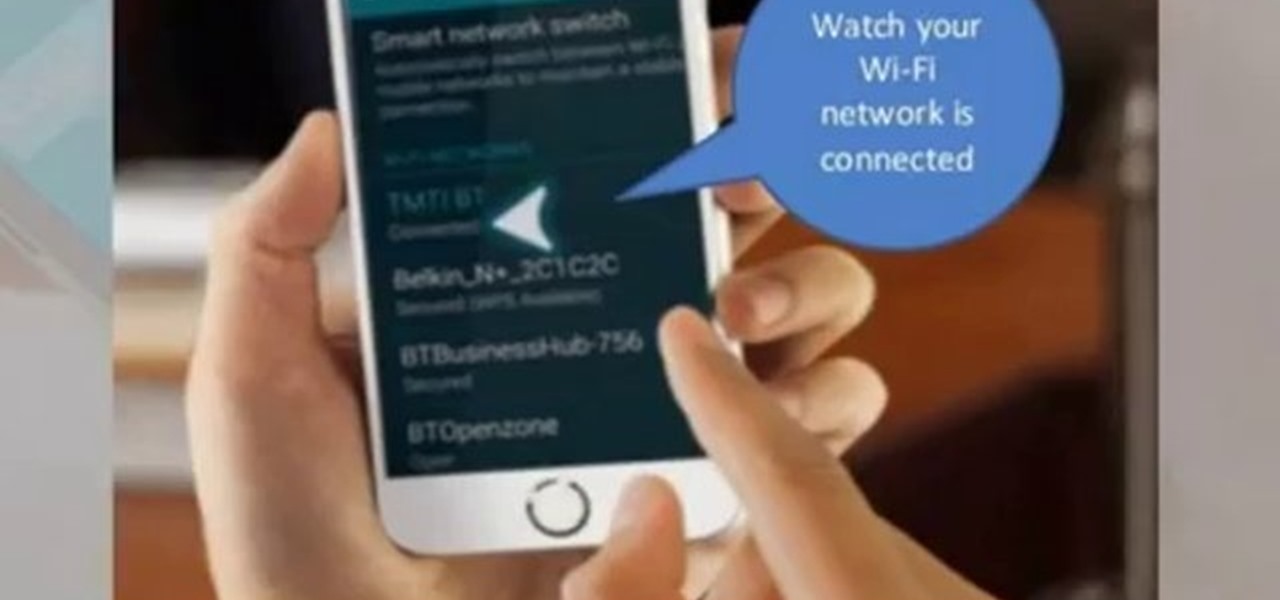
This tutorial video will show you how to connect a wifi network in your Samsung Galaxy S5. This is very easy to employ. So please watch the video. Follow all the steps to do it yourself in your Samsung Galaxy S5 phone and enjoy a wifi environment.

This video will show you how to set up a connection with wifi network in your Samsung Galaxy S5. So please watch the video and follow all the steps carefully. Employ the technique in your Samsung Galaxy S5 phone and enjoy a wifi environment.

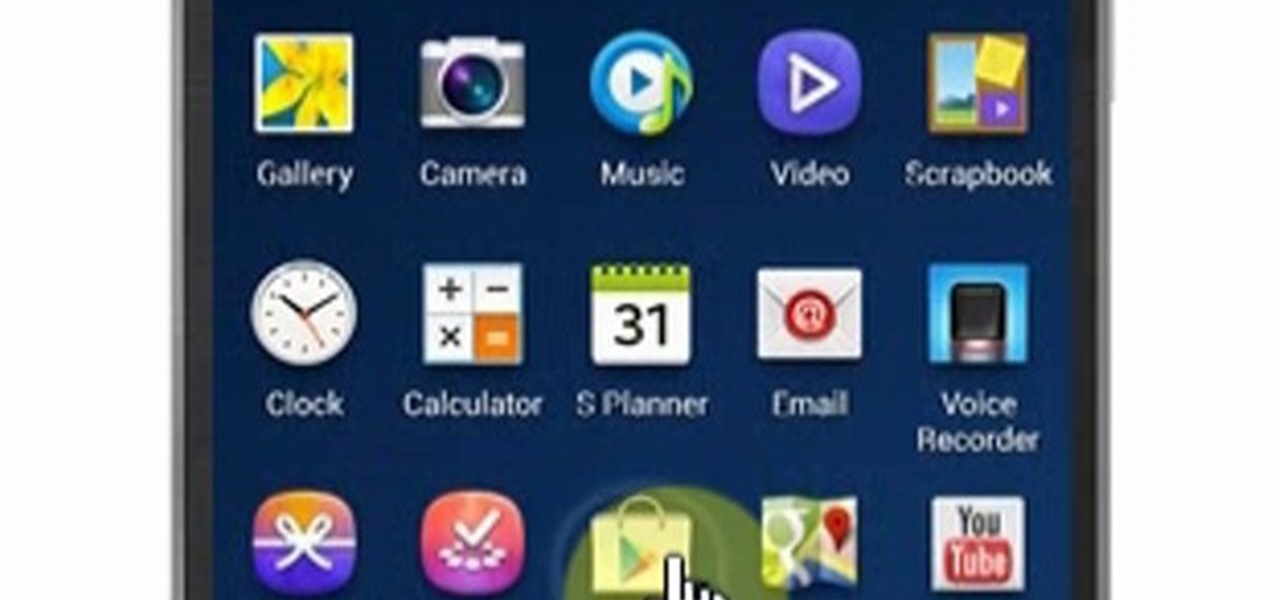
This video will show you how to download apps and games in Samsung Galaxy Note 3. Enjoy new apps and games in Samsung Galaxy Note 3. So please watch the presentation and follow all the steps carefully. Employ the technique to download new app and games on your device.

Want to get even this Halloween? Want to scare somebody with nothing but a few lines of code? Here's how it can be done...

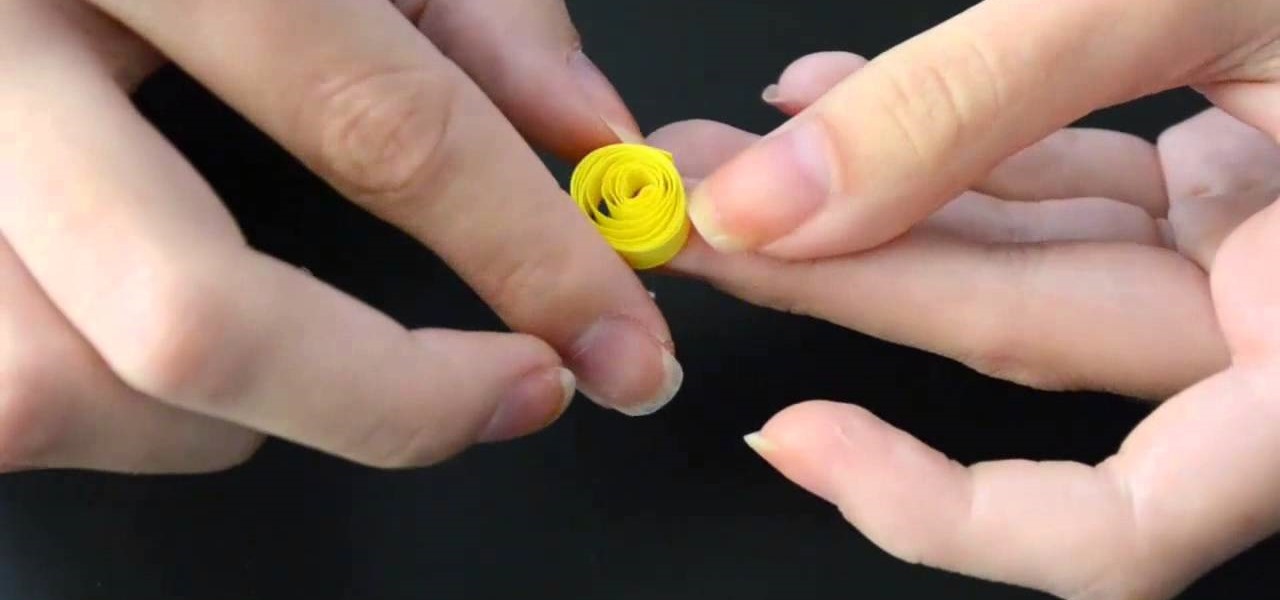
Video: . DIY How to make Quilling Candle Holder

Video: . In this tutorial, I will show you how to make a necklace - Quilling necklace !

In this tutorial, I will show you how to make an Origami flower ball. Welcome to our Origami and Quilling for beginners series :) In this videos we use Paper Art to do some cool things that you can sell them, give them like a gift and more :)Enjoy!

Video: . Welcome to our Origami and Quilling for beginners series where we show you how to use Paper Art to do some cool things that you can sell them, give them like a gift and more.Enjoy:)

Hi again everyone, In this lesson I will be talking about jobs and their meanings in Lebanese Arabic. Enjoy and feel free to ask about other jobs not mentioned here.

Whaaaatsup guys, Uber here and today I bring you the second video in the BronzeSMP series! I hope you enjoy!

Hello! This video is for kids and teens who are bored and/or home alone, I hope you enjoy the video and I hope it helps you find something fun to do!

How to make Eternal Waves - Twisted Waves or Double Wave Bracelet. This Bracelet featuring oval shaped designs and wavy bars that crisscross. The bead clasp can be changed if you prefer to use a Sliding Clasp instead, or Clasp with Button. Hope you enjoyed the tutorial.

Hello guys, this lesson is for students and about everything related to studying . I hope you enjoy it.

Hello guys! This lesson is for all of you Football fans out there. I will be talking with my friend Chantal about the World Cup and teaching Lebanese sentences that revolve around it.

In Honor for the FIFA World Cup 2014, we made this Brazilian Bracelet, with a Soccer Ball button on it, enjoy! How to make a Macrame Football Bracelet - Tutorial.