While hackers know and love the Raspberry Pi, many don't know of its cheaper cousin, the microcontroller. Unlike a Pi, which can be used more or less like a regular computer, microcontrollers like the Wi-Fi connected ESP8266 require some necessary programming skill to master. In this guide, we'll build an Arduino program from scratch and explain the code structure in a way anyone can understand.

A lot of people still trust their web browsers to remember every online account password for them. If you're one of those users, you need to adopt a more secure way of managing passwords, because browser-stored passwords are hacker gold mines. With a USB Rubber Ducky and physical access to your computer, they can have a screenshot of all your credentials in their inbox in less than 60 seconds.

It's easier than you might think to hack into Wi-Fi routers using just one unrooted Android phone. This method doesn't require brute-forcing the password, a Windows OS for converting PowerShell scripts into EXE format, a reliable VPS for intercepting hacked Wi-Fi passwords, or Metasploit for post-exploitation tricks.

There have been concerns with how much personal information Google tracks and all the things they know about us. Of course, that's what makes Google services so useful, they can use that information to cater to each of us individually. So yes, it serves a purpose, but it's not great for personal data security.

Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal their real trackable MAC address, and it can even let an attacker take over the phone's data connection with no warning.

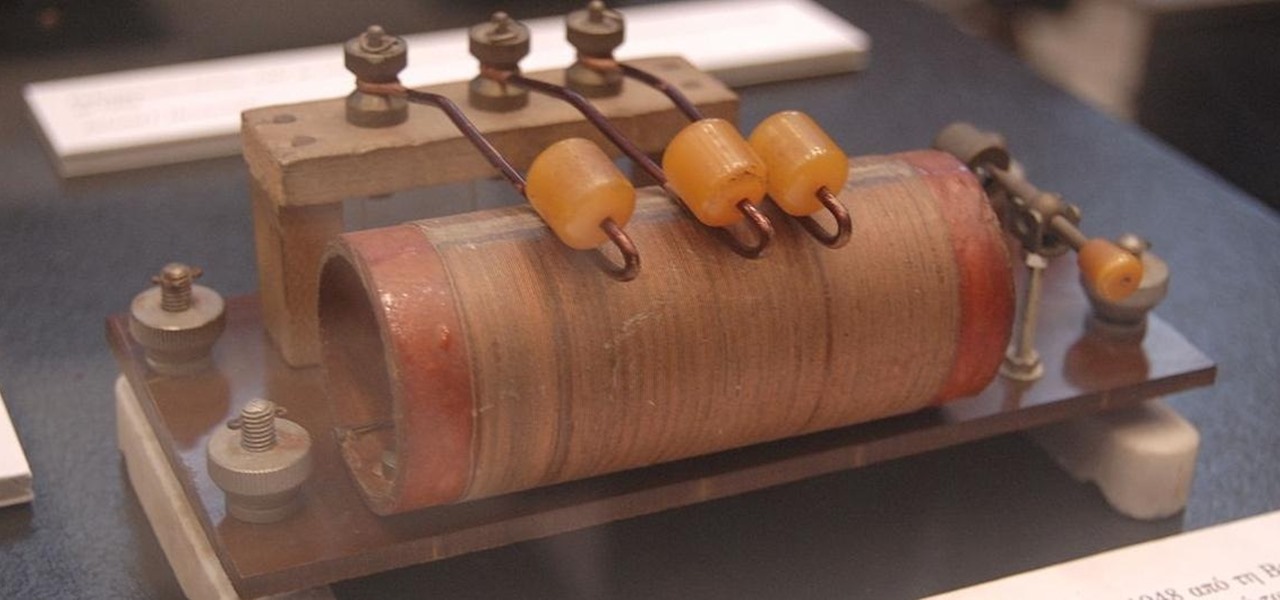
Hackers and makers are often grouped under the same label. While hackers draw on computer science skills to write programs and find bugs, makers use electrical engineering to create hardware prototypes from microprocessor boards like the Arduino. We'll exercise both sets of skills to program a $6 NodeMCU to display the status of a Wi-Fi link via an LED, allowing us to monitor for jamming attacks.

Developers creating login systems know better than to store passwords in plain text, usually storing hashes of a password to prevent storing the credentials in a way a hacker could steal. Due to the way hashes work, not all are created equal. Some are more vulnerable than others, and a little Python could be used to brute-force any weak hashes to get the passwords they were created from.

Hello, budding augmented reality developers! My name is Ambuj, and I'll be introducing all of you Next Reality readers to the world ARKit, as I'm developing an ARKit 101 series on using ARKit to create augmented reality apps for iPad and iPhone. My background is in software engineering, and I've been working on iOS apps for the past three years.

There's a lot that goes into making a nice crystal radio set, so this is going to have to be broken down into two parts. The first part is the actual making of a functional radio, and the second part is making the whole arrangement look nice. In this part, I'm actually going to tell you more than just how to make a crystal radio, but I'm also going to explain how and why they work. Crystal radios are pretty Steampunk in and of themselves, since they were first developed in the late 19th centu...

When compared to last year's model, the Pixel 4a has upgrades that go beyond the spec sheet. But since it's one generation old, 2019's Pixel 3a can be had for one hell of a discount right now, and it's still got two full years of software updates coming its way. So which one really is the better buy?

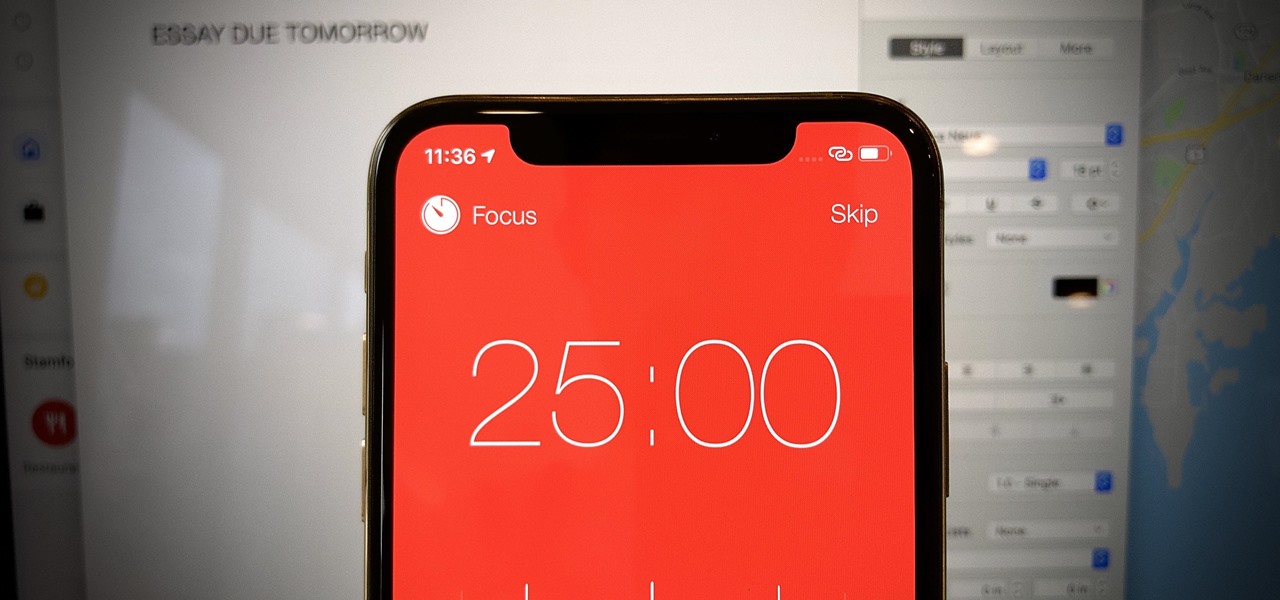
Procrastination is an ugly beast. At first, it seems so innocent to spend five minutes checking Reddit or Twitter. You'll get started on work right after. Next thing you know, it's 1 a.m. and that paper is due in seven hours. Before you start another YouTube video, know you don't have to be like Spongebob. You can be like me, taking control of your productivity with the right app.

Social media accounts are a favorite target for hackers, and the most effective tactics for attacking accounts on websites like Facebook, Instagram, and Twitter are often based on phishing. These password-stealing attacks rely on tricking users into entering their passwords into a convincing fake webpage, and they have become increasingly easy to make thanks to tools like BlackEye.

When setting up a Raspberry Pi, it's easy to overlook changing the default password. Like many IoT devices, the Raspberry Pi's default Raspbian operating system installs with a widely-known default password, leaving the device vulnerable to remote access. Using a tool called rpi-hunter, hackers can discover, access, and drop custom payloads on any weak Pi connected to the same network.

The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centered around hacker Lisbeth Salander. Of course, with the quick pace of some scenes, the hacks can be hard to follow.

Stories are everywhere in social media today, but that wasn't always the case. In 2013, Snapchat introduced the world to these temporary windows into our daily lives. Since then, stories have infiltrated other popular apps. However, to stand out, you can't solely rely on the app where the story will be posted. Instead, you need a suite of apps that can turn your story into something special.

Overall, iOS is more impressive than ever with its stability enhancements, security tools, suite of apps and services, and intuitive user interface. With each passing update, things just get better and better for iPhone users. But don't think for a second that this is all because of Apple's genius — many of these features were at least partly inspired by tweaks made by the jailbreak community.

Ports allow network and internet-connected devices to interact using specified channels. While servers with dedicated IP addresses can connect directly to the internet and make ports publicly available, a system behind a router on a local network may not be open to the rest of the web. To overcome the issue, port forwarding can be used to make these devices publicly accessible.

Individually addressable LEDs, also commonly called "NeoPixels" after the popular Adafruit product, are a bright and colorful way to get started with basic Python programming. With an inexpensive ESP8266 or ESP32 microcontroller, it's easy to get started programming your own holiday lighting animations on a string of NeoPixels with beginner-friendly MicroPython!

What appears to be an ordinary MP4 may have been designed by an attacker to compromise your Linux Mint operating system. Opening the file will indeed play the intended video, but it will also silently create a connection to the attacker's system.

If we were to assign a theme for the 2019 edition of the Next Reality 30 (NR30), it might be something along the lines of, "What have you done for me lately?"

|Choose Your View: Quick Bullet Points | Detailed Descriptions Android's newest major update is a special one — it's the tenth full version of the world's most commonly used operating system. The latest release, dubbed simply Android 10 (codename Android Q), was first showcased as a beta back in March 2019, so we've been digging around in it for several months. There's one dramatic visual change, plus there are a lot of goodies in general.

Trying to figure out which music streaming service to subscribe to can be a difficult task when the playing field is so crowded. Each has its benefits, as well as downsides, so finding the right one for your needs and wants can take a lot of overwhelming research. But we've done all the research for you to help you find the best music subscription your money can buy.

OpenBSD implements security in its development in a way that no other operating system on the planet does. Learning to use the Unix-like operating system can help a hacker understand secure development, create better servers, and improve their understanding of the BSD operating system. Using VirtualBox, the OS can be installed within a host to create a full-featured test environment.

Internet Relay Chat, or IRC, is one of the most popular chat protocols on the internet. The technology can be connected to the Tor network to create an anonymous and secure chatroom — without the use of public IP addresses.

Champagne is best enjoyed at a cool temperature and a frosted glass creates a festive mood for many drinks. In this how to video, see step by step how a create the perfect frosted glass and learn tips on how to have that perfect glass of champagne.

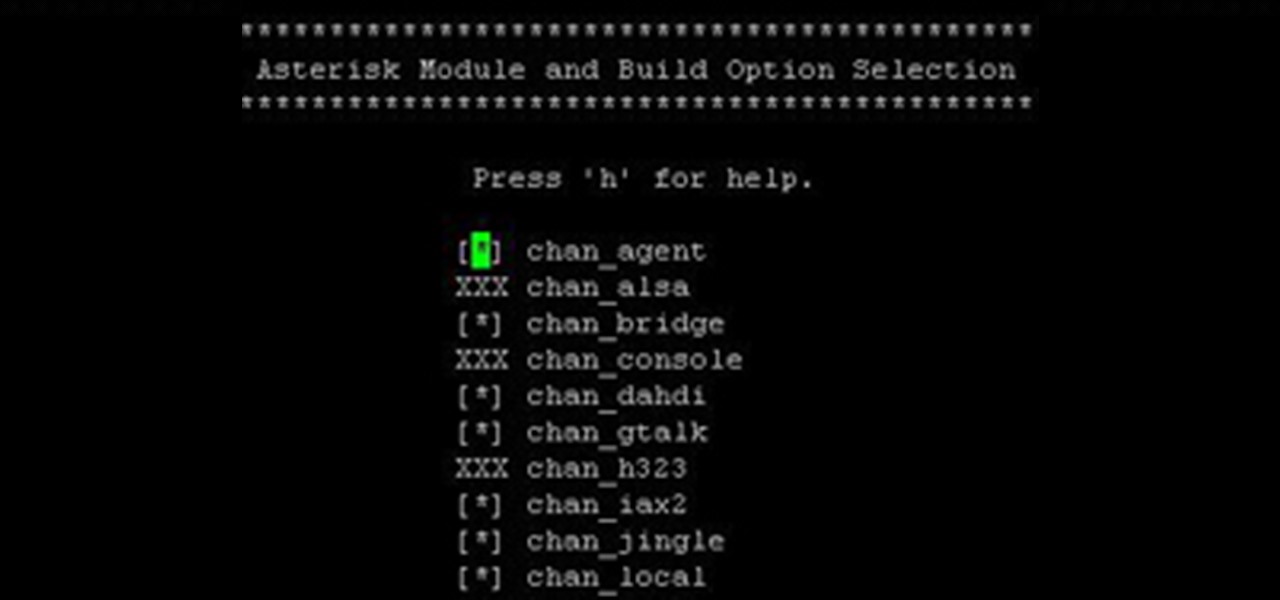
Over the years, I have enjoyed playing with Asterisk. I have found Asterisk to be extremely powerful and fun to play with. There are several books and many scattered how to articles out there, but most are outdated and the information required to build Asterisk from beginning to end can be a bit daunting. I wanted to combine all the steps into a single article and share my experience with everyone. If I have left out any steps please let me know.

This coming Friday, November 11th, 2011 is Veterans Day and everybody's celebrating! But only veterans and active military personnel can get the great deals being offered at restaurants and retail outlets across the country. If you need help locating some of those deals, below are all of the nationwide and local deals found across the Web. If you know of any more, share the spots in the comments below!

Attention all Guinness lovers… did you know that Guinness doesn't have to be enjoyed merely by itself? You can do all sorts of things with this Irish beer, like mix specialty drinks, cook, and bake…

This tutorial is for complete beginners to time-lapse photography and will show you all the settings and equipment you'll need to start taking time-lapse videos with a DSLR camera relatively cheaply. Although this tutorial focuses on the Canon 7D, the steps outlined and equipment discussed also applies to other models available on the market.

Why the Love? Every one has a reason for loving something. Mine was that it was the only thing I had. That one sure thing. I loved it because I had nothing, and it cost me nothing. At times I had no idea what was going to happen to me, or where I was going to be. The shore is always there! Rain or shine( the water is always calm beneath the surface), day or night( bring a waterproof flashlight).

Recently, buyout talks between Google and Groupon ended with Groupon turning down Google's $6 million offer. But with Amazon backing LivingSocial, should they have? Your guess is as good as mine, but one thing's for sure— Groupon has a great voice, and they're sharing it with the world via their Public Groupon Editorial Manual.

Creating a relish is easier than you think, and this bacon-corn relish is the easiest of all, not to mention deliciously sweet. You basically just throw all the ingredients together and mix. You don't need to be a master chef to make this relish.

How2heroes has a great tutorial on how to make and bake challah. This Jewish dish can be enjoyed all year long, by anyone who loves the taste of delicious bread. Suzanne Mermelstein shows us the best way to bake a delicious loaf.

Hello jackass crew! My prank is called the Slide Surprise

If you're a musician in need of some lessons, there's no better way to learn than with MusicRadar's so-called "Tuition" instructions. Although the title tuition is misleading, this video class is anything but costly, because it's free, right here. Whether you're looking for help with your voice, bass, electric guitar, drums, guitar effects, piano, Logic Pro or production techniques, Music Radar is here to show you the way.

Restoring wood furniture takes time and patience, but the results of your labor can be enjoyed for years, even generations. The restoration process usually involves stripping off old finishes, bleaching, staining and then varnishing. Two-Part Hydrogen Peroxide is a strong bleach that will lighten wood and remove previously applied finish stain, providing you with a fresh new surface to refinish.

Perfect the making of Pecan Pie with this recipe. With both pecans and pumpkins, it's two holiday favorites in one that every Thanksgiving dinner table will certainly welcome. But then again, that's not to say it can't be enjoyed any day of the year!

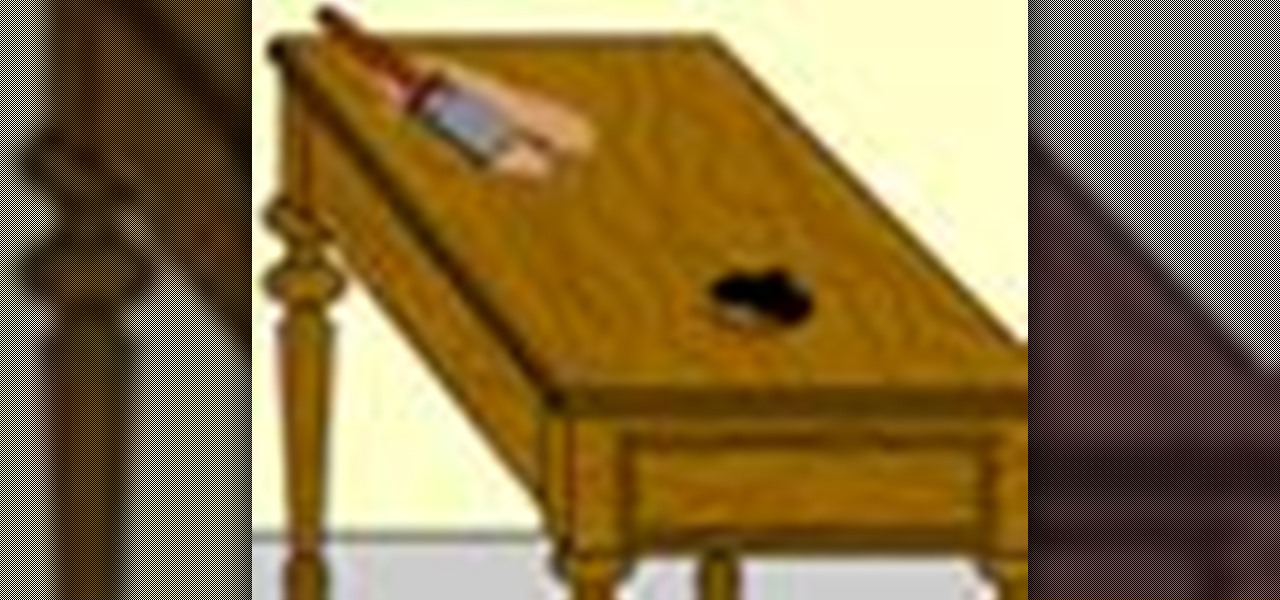
When restoring older wood furniture you will probably encounter dark rings and black spots, which are caused by water stains. Oxalic acid is a moderate bleach that will remove these stains even if they have penetrated the wood surface. Oxalic acid will also remove finish stain applied previously and lighten the wood for a fresh new look. Restoring wood furniture takes time and patience, but the results of your labor can be enjoyed for years, even generations. The restoration process usually i...

Two's company, three's a crowd... But not in this case. An elegant cocktail to be enjoyed as the sun sets on another summer's day. Make a Menage A Trois cocktail.

This delicious cod soup makes a great starter which can be enjoyed the whole year round. Preparation time is 25 minutes and cooking time is 35 minutes. Make bacalao chowder.