There's definitely a lot of new things to get used to in iOS 6, with over 200 added features, but which ones stand out about the rest? Well, it all depends on what device you're using. Some features will only work on newer models, but most of the hidden features are accessible to all.

In the first part of this series, we took a factual and technical look at the history of the Internet. I explained how all of these wires and servers got here in the first place. Obviously, a firm did not just create and build the Internet around 1995! Now that we know how the Internet came to be, we can get into the really fun stuff—what the Internet looks like now! Well, that's not quite the network design I was talking about, but it does show what the Internet looked like back in 2007 befo...
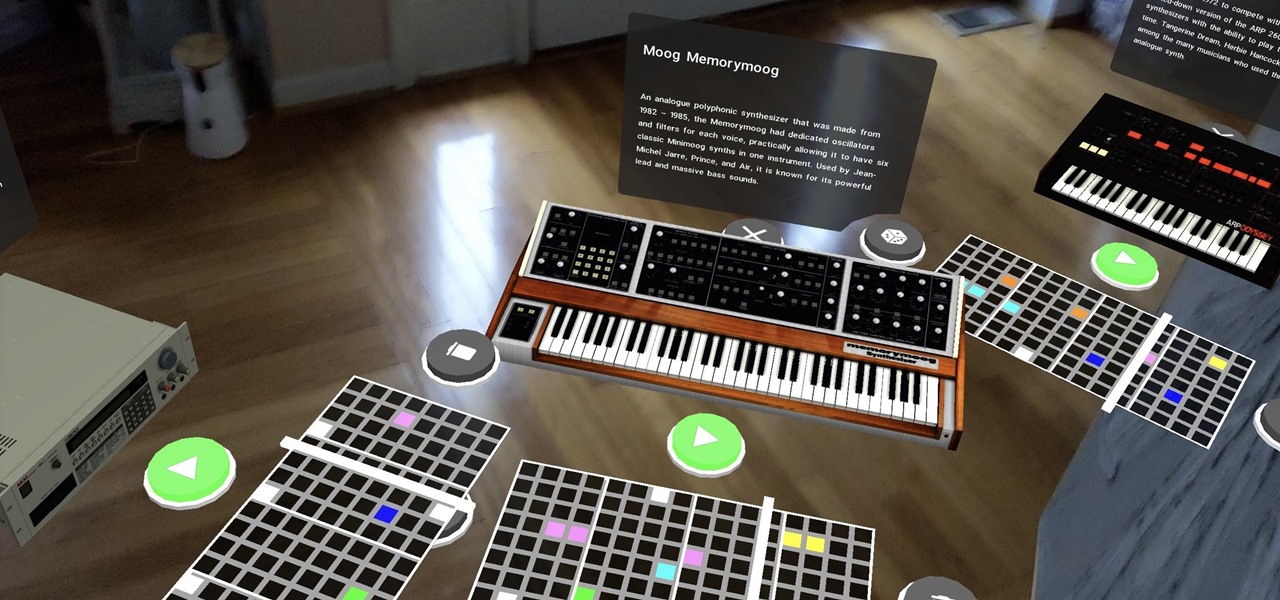
Museum curators typically frown upon visitors touching paintings, sculptures, and artifacts, but not when those exhibits are displayed in augmented reality.
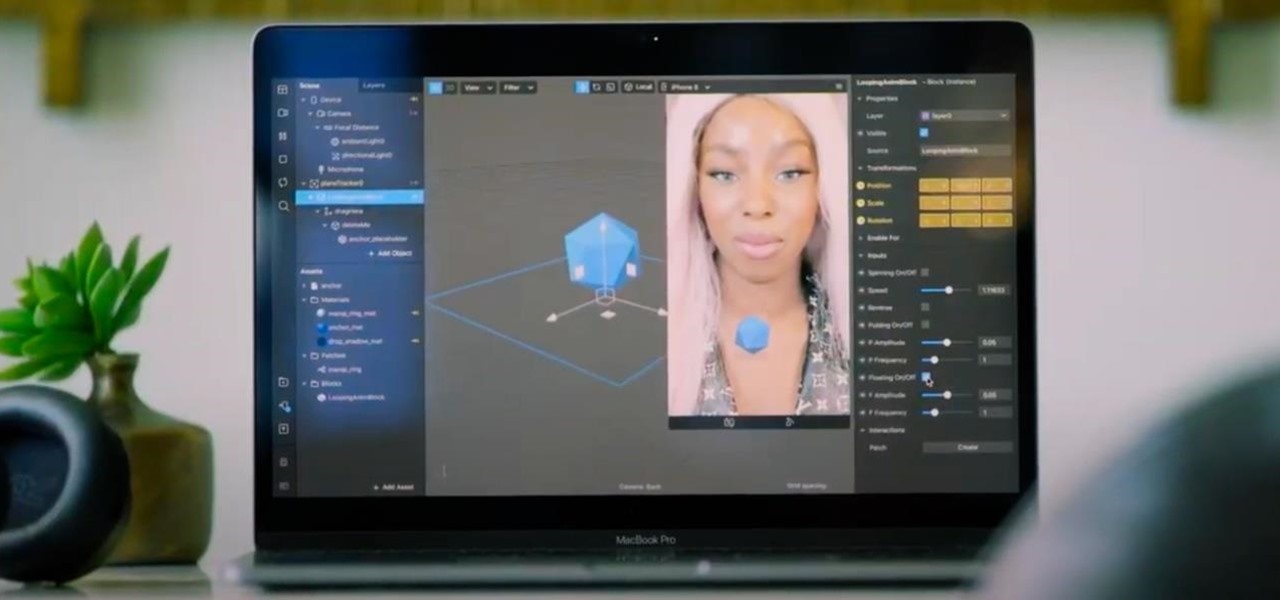
As Apple, Google, Snap, and Facebook wrestle for positioning to lure developers and creators to build augmented reality experiences for their respective tools, Facebook is looking at a learning approach for its Spark AR platform.

Whenever the name Magic Leap comes up, the talk inevitably seems to turn to the company's big-name backers and "unicorn-level" amounts of cash poured into the venture. And if it's not that, observers tend to focus on the company's market strategy and overall prospects.

Give an 18-month-old a shoe, check back 10 minutes later, and it's a very big maybe he will have it on his foot. But give him your smartphone, and in a mere five minutes, he can take 100 pictures of the carpet, send weird messages, and delete essential apps. Imagine what your child could do if they were able to harness this technical aptitude and put it to good use — and they can, with learning apps.

Whether you're in high school or college, you no doubt will have your iPhone in your pocket all day long. To make your iPhone last the whole time and even help you out with your studies, these are the accessories you'll want to get your hands on.

We've shown you the best augmented reality headsets, and now it's time to show you the rest. These are the AR headsets you've probably never heard of or even seen. The AR headsets that, in some cases, have a shot at the big time, and may one day reach widespread adoption, and, in other cases, are unwieldily contraptions that look like something out of a weird science fiction movie.

Contrary to popular belief, augmented reality apps have been available for a while now. I remember using the Layar app (still available for iOS and Android) to explore nearby businesses and landmarks with varying success via an early-generation Android handset.

Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life.

Black Friday is fast approaching, and just like every other day-after-Thanksgiving, there will be too many tech deals you won't want to pass up. If you've been saving up all year just for this sometimes-chaotic shopping holiday, we'll help you figure out the best tech sales to take advantage of and when, whether it's Black Thursday, Black Friday, or Black Friday weekend.

Greetings my fellow hackers, In the previous article, I discussed briefly about ransomwares and their devastating capabilities. Devastating in a way that ransomwares are not only known to encrypt files but to also lockout some specific functions of the system and hold it up for a ransom.

YouTube's massive user base comprises almost one third of all people on the internet, and collectively, users spend well over 100 million hours on the site watching billions of videos each day. Add it all up, and this means that YouTube is viewed by more people than any U.S. cable network—making it by far the favorite "TV station" of the internet generation.

Today's smartphones and tablets offer a great way for children to learn through interactive sight, sound, and touch, but they can also provide hours of genuine fun. If you have a spare tablet laying around—or at least a nice, durable case—the only thing you need to get your child started in this world of fun and learning is a handful of good apps.

It's been a while when the major web browsers first introduced HTTP Strict Transport Security, which made it more difficult to carry Man In The Middle (MITM) attacks (except IE, as always, which will support HSTS since Windows 10, surprised?).

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Hello readers, and welcome to Null Byte. Before we start, for those of you who may not know me, my name is ghost_; I'm a relatively active member of our community and have been around for a while.

I am an English major physically allergic to all algebraic formulas, so you're unlikely to get any help from me when it comes to solving any expressions. But in the glorious technological age we live in, there are plenty of apps that actually make math and problem solving fun, even a little bit addictive.

Do you have an Alfa AWUS036NH Wi-Fi adapter that claims it can go to 2000 mWs, or some card that can supposedly transmit power over 1000 mW? If so, you may have run into problems setting your card's TXPOWER higher than 30 dBm, which is about 1000 mW. Well, I will show you how to break that barrier and go as high as you want!

Imagine being able to play a video instantly on hundreds of thousands of devices across the globe. It's totally possible, as long as all of those devices have a Chromecast plugged in. When Chromecasts are left exposed to the internet, hackers can use add them to a botnet that can play YouTube videos at will. The "attack" is made even easier thanks to a simple Python program called CrashCast.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website was viewed. There's no doubt Coinhive, an innovative mining method, is being abused and exploited by hackers in the wild.
Have you ever used an open wifi, which after you connect displays a website to enter your credentials to get internet? That website is called captive portal and widely used in airports, hotels, universities etc. Have you ever wondered what would happen if someone would set up an open wifi with the same name displaying a very similar web page asking for credentials? Usually if there are multiple wifi networks with the same name and encryption, devices only display the one with the highest sign...

First off, don't be frustrated. YOU CAN DO IT! Contrary to the message in the image above, it's NOT over. It's just beginning. And when it comes to solving the New York Times crossword puzzle, the old cliche does apply: practice makes perfect.

While the airline, casino, cruise, and hotel industries are asking for government bailouts during the COVID-19 pandemic, companies around the US are giving away its apps and services for a limited time. So while you're stuck at home, keep your mind off of coronavirus with free movies, TV, music apps, concerts, internet, fitness sessions, classes, and more.

If we were to assign a theme for the 2019 edition of the Next Reality 30 (NR30), it might be something along the lines of, "What have you done for me lately?"

Welcome to the first annual Next Reality 30, our list of people who've made the biggest impact on the augmented reality space in the last 12 months — and what a 12-month roller-coaster ride it's been. Apple introduced ARKit-powered apps last fall, Google launched ARCore for Android soon after, Snapchat began monetizing AR, and the Magic Leap One headset finally came out. These are historic times.

While our time with the Protostar VM from Exploit Exercises was lovely, we must move on to bigger things and harder challenges. Exploit Exercises' Fusion VM offers some more challenging binary exploitation levels for us to tackle. The biggest change is that these levels are all network services, which means we'll write our first remote exploits.

A PirateBox creates a network that allows users to communicate wirelessly, connecting smartphones and laptops even when surrounding infrastructure has been disabled on purpose or destroyed in a disaster. Using a Raspberry Pi, we will make a wireless offline server that hosts files and a chat room as an educational database, a discreet local chat room, or a dead-drop file server.

You may think your iPhone has all the features you could ever need or want, but that may change once you discover the features and services you're missing out on by residing in the United States.

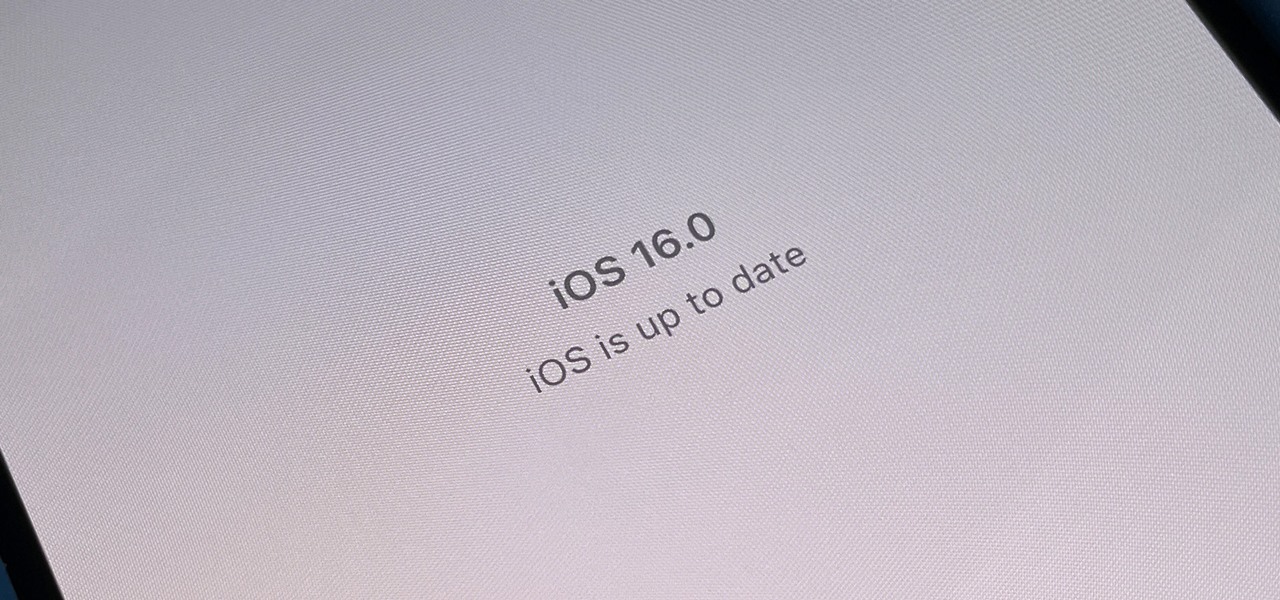
Apple's new iOS 16 software update is finally here, and there are over 350 new features and changes for you to enjoy on your iPhone. There are major lock screen and home screen improvements, a pleasant surprise for the Contacts app, and tons of new upgrades to Safari, Mail, Messages, and more.

Out of the more than 200 new features Apple included with iOS 13, perhaps none is more anticipated than system-wide dark mode. Finally, we no longer need to blind ourselves when responding to an iMessage late at night or checking Reminders to see the following day's tasks. But this benefit also applies to third-party apps, so long as they are updated accordingly.

Chef David Blom demonstrates how to make babas and savarin - A yeast dough, enriched with butter and eggs, baked in two different shapes. It's a very spongy dough. Chef Blom demonstrates how to prepare the molds with melted butter and then adds the dough to the molds. Make babas and savarin.
Iran has stepped up efforts to produce enriched uranium in violation of international resolutions to stop, the International Atomic Energy Agency said Friday in a report posted online by a nonproliferation group.

“Western Imports”, by artist Cayetano Ferrer, uses inkjet prints to create site-specific optical illusions in public spaces.

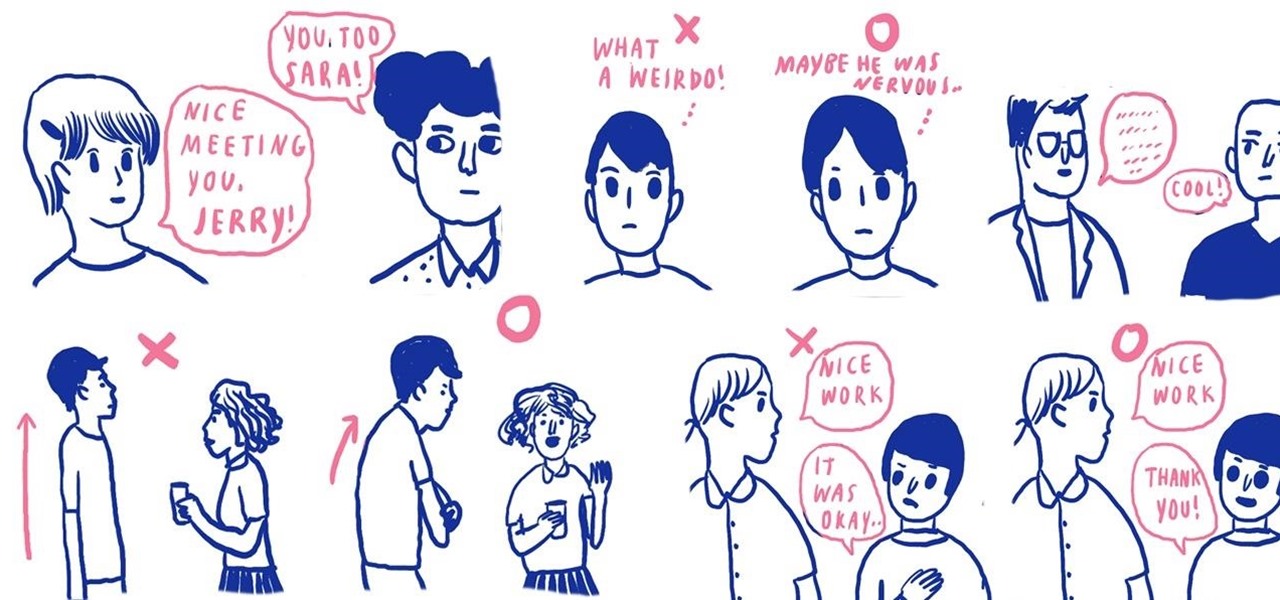
If you're in a social situation where you're meeting a lot of new people and you want to make the other person feel at ease, subtly mirror the other person's body language and make a point to say the other person's name.

When you sauté kale, it tends to retain all of its nutritional value, whereas boiling and steaming kale will kill the vitamin-enriched goodness. So, this simple kale side dish should be in every cook's recipe box. Kale by itself has a rather bitter flavor, but when cooked in soup or even just briefly with garlic and oil, it's delicious. Harvard University's Martin Breslin shares a quick side dish that's good for you, goes with fish or meats, uses only one pan, and clean-up is a breeze. Best o...

An easy tutorial on how to get unlimited respect points for the iPod Touch/iPhone game Drag Racing. Only for EDUCATIONAL PURPOSES!