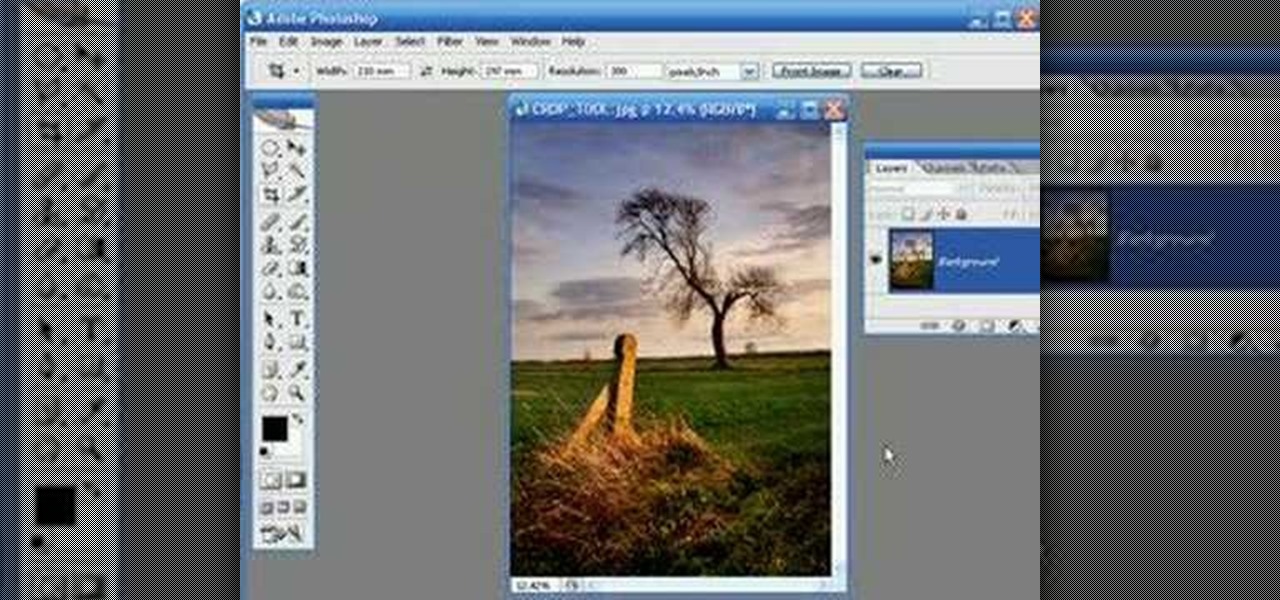
Kingsley Singleton teaches us about cropping images in Adobe Photoshop. He discusses the importance of properly cropping pictures, and the basic ways to do so. He first shows us how to properly crop images to ensure that printed pictures are the proper size for the paper. Clicking on the image and then dragging the marquis over the picture will select the area of the picture that you would like to use. Moving the corner arrows will adjust the size of the area selected. Then, to properly size ...

Nuts and Bolts present how to lay a west Australian natural stone. When beginning the laying of any tile or stone, it is very important to make sure the first stone is perfectly straight. So, the first step is to measure from two walls and get the dead center of the room. They use a straight edge to make sure the tile is laid straight. Then, they cover the floor with a light adhesive to ensure the placement of the tile. He uses a saw with a guide to make sure all his cuts are straight. He lay...

Learn how to follow proper netiquette rules. You may be a model of decorum in person, but a bonehead online. Check out how much you know about Internet manners.

A virtual private network is a necessary part of your arsenal if you're insistent on surfing the web privately and securely on your iPhone. The App Store is littered with hundreds of different VPN services that encrypt traffic and mask your IP address, but what they all have in common are connectivity issues.

By far the most significant development for AR in the coming months and years — the development that will drive AR adoption — will be our reliance upon the AR cloud.

Whether we like it or not, our personal information and smartphones are tied together at the hip. The former needs the latter to deliver a personalized experience that matches our individual needs. This personal data, however, makes your phone a prime target for thieves of all sorts to turn your privacy into illicit profit.

On Monday, Apple unveiled its Apple Card, the company's boldest move yet toward becoming a truly mainstream mobile payments company. And the product has vast implications for our augmented reality future, some of which may not be immediately obvious to many.

Stumbling upon a specifically tailored advertisement on your iPhone can be a bit disconcerting. But that's what happens when you let advertisers track your data. Some of you may appreciate more relevant ads in apps, but the rest of you might consider it a straight-up privacy invasion.

Every photo you take is brimming with metadata such as iPhone model, date and time, shooting modes, focal length, shutter speed, flash use, and geolocation information. Share these pictures with friends, family, or acquaintances via texts, emails, or another direct share method, and you unwittingly share your location data. Even sharing via apps and social media sites can compromise your privacy.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

Unlike many browsers, Firefox gives a lot of control to the user. By default, Firefox does a great job of balancing security and performance. However, within the app's settings, you can modify options to shift this balance in one direction or another. For those looking to shift it toward security, here are few suggestions.

Learn to make your own privacy fence in this instructional video with expert builder Mark Sullivan. Mark will teach you all about fences and help you decided if a privacy fence is right for your yard or lawn.

First you must take inventory of all items in order to be able to create your bag. Make sure all labels are in the correct order. Lining should be ready before attempting to begin construction. The stay should be 10in long and 4in wide. Pocket the stays and glue the stays to the outside fabric. Use the notches to line everything up. Take the magnetic snap and attach it to the front and back. Take a knife and cut holes for the magnetic snap. The magnetic snap comes with a washer. Use cardboard...

Jennifer is showing us how to paint rims. You can use Dupicolor paint bought from Auto Zone and costs five dollars. First, you must sand and wipe your rims to ensure a smooth clean coat. Other items you will need are duct tape, newspaper, and a jack. The first step is to place the hand brake on, loosen up the first tire you want to work on, and then jack up the car to easily remove the wheel. Next, clean the tire and rim really well and use a paper towel to dry the rim. Tape newspaper around ...

With the growing popularity of digital downloads, it's important for aspiring musicians to have some sort of download available of their music. If you're an unsigned musician, selling your music on iTunes might seem daunting, but it's actually very easy! Learn how to do it in this video.

Having a boring Facebook profile is lame! Impress your friends and flaunt your social networking skills by sprucing up your Facebook profile.

The video tutorial describes how to tie your belt (obi or sash) around your gi suit for aikido. This method is particularly good for aikido as the finished knot is fairly flat and the layers of the belt do not cross at the back.

Coming soon to an Android device near you: Diminished Reality! What's Diminished Reality? A lot like Augmented Reality, really, but with one big difference: Where AR giveth, insinuating virtual elements into a live representation of the real world, Diminished Reality taketh away, hiding actually-existing objects within a live feed.

Remember summer camp? Remember the smell of the log cabins? The feel of the treated wood? Well, you can create something for your home that's perfect for a nostalgic summer camp aesthetic. Meg Allen Cole (recently of Threadbanger) was inspired to make this mid-century modern wall hanging piece made from a small wooden log (or branch) when she was at a relaxing, wooded vacation spot in Maine. And she shows you how to make one, too!

In this video tutorial, viewers learn how to clear their cookies in Mozilla Firefox. Begin by opening the web browser. Then click on Tools from the top menu and select Options. In the Options window, click on the Content tab and deselect "Block pop-up windows". Click OK. Now click on Tools and go to Options once again. Click on the Privacy tab and click on Clear Now under Private Data. Make sure that Cookies and Cache are checked and click OK when finished. This video will benefit those viewe...

Deleting cookies in Firefox is pretty easy. Start by opening your Firefox browser. You will click a series of tabs to delete all or part of the cookies on your computer. Click the ‘Tools’ tab and go to ‘Options’. In the ‘Options’ box choose ‘Privacy’. Look for the ‘Cookies’ section of the box and choose ‘Show Cookies’. That will bring up a list of all the cookies on your computer. Choose ‘Remove Cookies’ or ‘Remove All Cookies’. Then close everything and restart Firefox and you are all finished.

Starting with Android 9 and 10, Google made privacy and security the main priorities for Android updates. Both versions brought numerous changes to help erase the notion that Android isn't safe, but Android 11 might even have them beat.

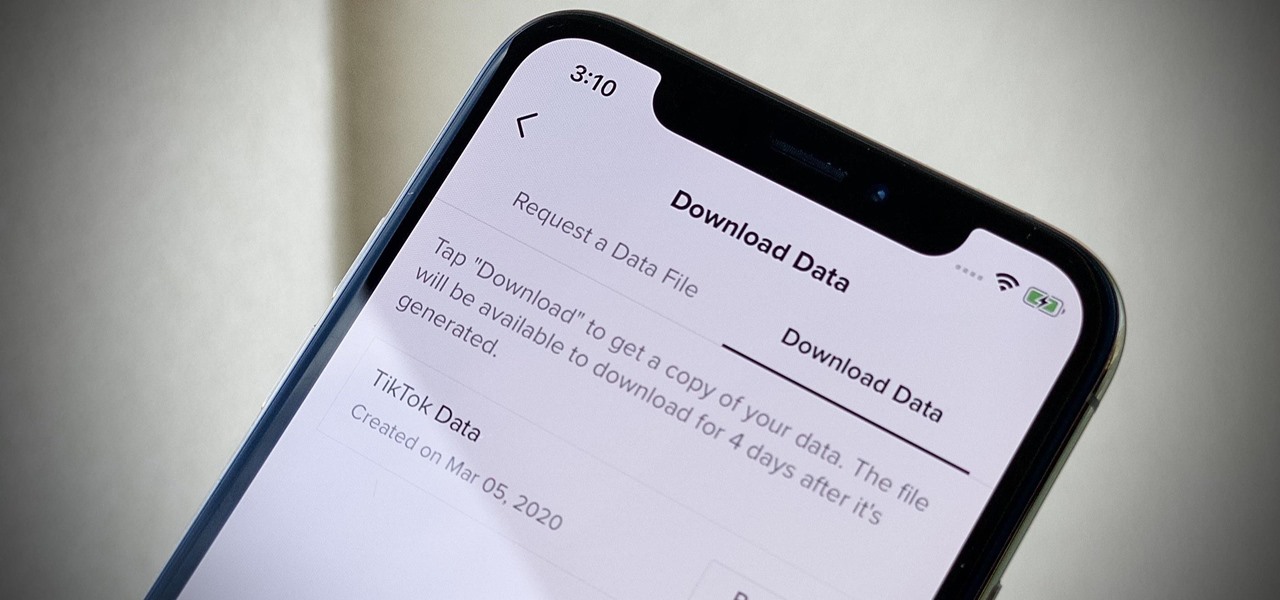
If you're concerned about your privacy, TikTok might not be the app for you. Its shady practices with user data have been the subject of concern, criticism, and even legal action by the US government. Then again, it's just so addicting. If, like me, you're not going to stop using TikTok anytime soon, you should at least know how to view the personal data it has collected on you.

The recent Oculus conference in California revealed just a bit more about Facebook's secretive plans to compete in the augmented reality space with its own wearable devices.

WhatsApp, the popular messaging app owned by Facebook, has several important privacy and security-related features, including end-to-end encryption, screen lock, read receipts, and two-step verification. If you're an avid WhatsApp user, you'll be happy to know there are more privacy features you might not know, such as hiding your profile photo from other users.

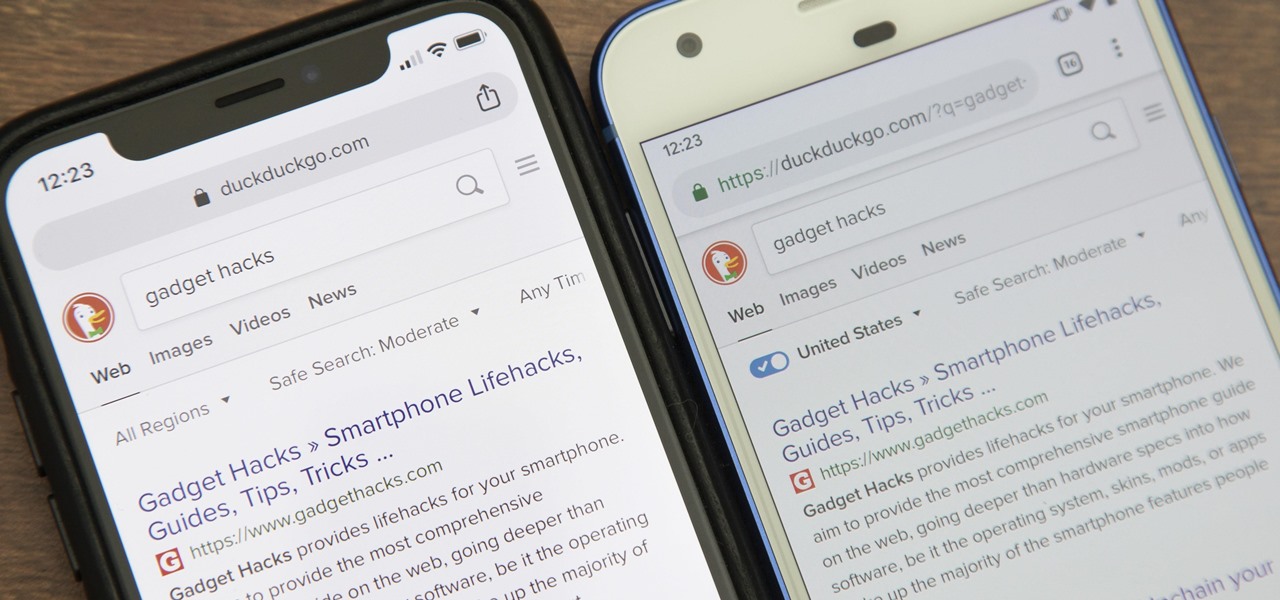
While Google would rather you use Google as the default search engine in Chrome, there's a way to switch to the more privacy-geared DuckDuckGo search engine for all your web browsing needs. With DuckDuckGo, the company does not track anything you search or allow anyone else to track it, so you can effectively search from your iPhone or Android phone anonymously.

When you don't want certain friends viewing your account or just need to take a break from social media, Instagram lets you do so. While you can completely delete your Instagram account, then start over when you're ready again, it makes much more sense to just disable your account temporarily. Doing so will hide your profile, photos, comments, and likes from everyone, including your friends.

Unless you're completely new to Instagram, it's likely that you've linked your account with a third-party service at some point and forgotten about it. Those services still have access to data such as your media and profile information, so it's important that you not only know how to find these "authorized" apps, but that you know how to revoke their permissions.

Thanks to recent reports, we now know third-party apps have a lot more access to our Gmail than we may have initially thought. In fact, these third-party apps have the ability to read our emails, not because these companies are necessarily shady, but because we agreed to it. Luckily, there's a way to view which apps have this access, as well as a way to boot those apps from your Gmail entirely.

Augmented reality is expected to eventually change everything, and the prevailing view is that those changes will be for the better. The converse view, however, is that the technology will further erode privacy.

When you leave your iPhone on a table or anywhere within somebody else's eyeshot, a private message may pop up on your lock screen that could be read by anyone who sees it. But there's a way to keep others from reading your possibly sensitive text messages and emails without giving up the convenience of lock screen notifications entirely.

Since starting as a simple messenger with self-destructing pictures, Snapchat has grown into a full-fledged social media platform. As features were added, new permissions were requested, and we're all probably guilty of just tapping "OK" to try out the latest and greatest. But at some point, it's a good idea to review your settings to see what personal data you're putting out there for all to see.

BlackBerry's focus on secure software and their new partnership with manufacturer TCL are two of the biggest factors in their recent resurgence. Last year, the company announced two new devices — the KEYone and the BlackBerry Motion. The KEYone has been available for a while, but after months of waiting, BlackBerry announced the Motion will hit US shores in a few days.

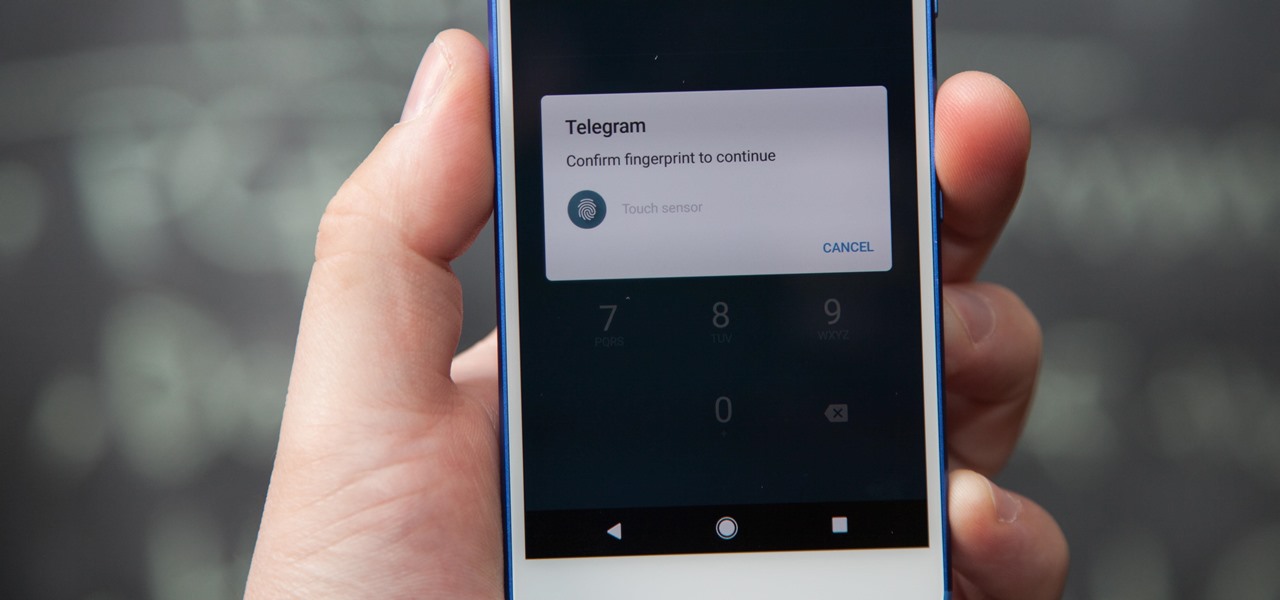
If you're using Telegram for its "Secret Chats" feature, which provides end-to-end encryption for your messages, then I'd highly recommend locking down the app itself with a passcode, PIN, or password. While your phone itself may have a secure lock screen already, if that gets compromised, you'll at least have an extra layer of security on your important conversations.

Google seems to be growing tired of the way links appear in its Search results page, because they're currently experimenting with a color change (that's already causing lots of controversy).

For most Android phones, the system clock is set using a protocol called NITZ, which relies on a connection with your carrier to ensure that the time stays in sync. The trouble here is that this feature won't work when you're outside of cellular range, and a lot of times, the carriers themselves have technical difficulties that can result in your phone's clock being minutes or even hours out of sync.

Even the best-maintained kitchens occasionally get a fruit fly infestation. These critters descend, lay eggs (up to 500 at a time!), and then disappear usually only after extreme cleaning efforts (i.e., finally attacking that weird puddle of goo behind your refrigerator).

When you post something online, it pretty much stays there. So it's no surprise that Snapchat, the self-destructive photo-sharing app, became such a huge hit, boasting an estimated 50 million users. Its ephemeral nature has proven popular, especially with teenagers—who are now well aware of the burden that permanence on the internet has.

If you've been using Google's hidden App Ops to lock down and prevent some of your Android applications from exposing your privacy, then think twice before updating to the new Android 4.4.2 software.

Former Vice President Dick Cheney was so fearful of attacks, he had his heart defibrillator re-calibrated to block incoming wireless signals so that highly skilled hackers couldn't send him into cardiac arrest.