Now that iOS 7 is out, what can you do that you couldn't do before? In this softModder guide, I'm going to cover all that's new and noteworthy about iOS 7. I've been playing around with it on my iPhone 5 since the first beta came out, so I'm excited to show you some of the secrets that are lurking within Apple's newest mobile operating system.

According to a new study, the majority of smartphone users check their devices 150 times a day. While that number may seem incredibly high at first glance, the influx of notifications and amount of social media apps available reduce the initial shock and make the number seem not so preposterous after all. Yeah, even on a date.
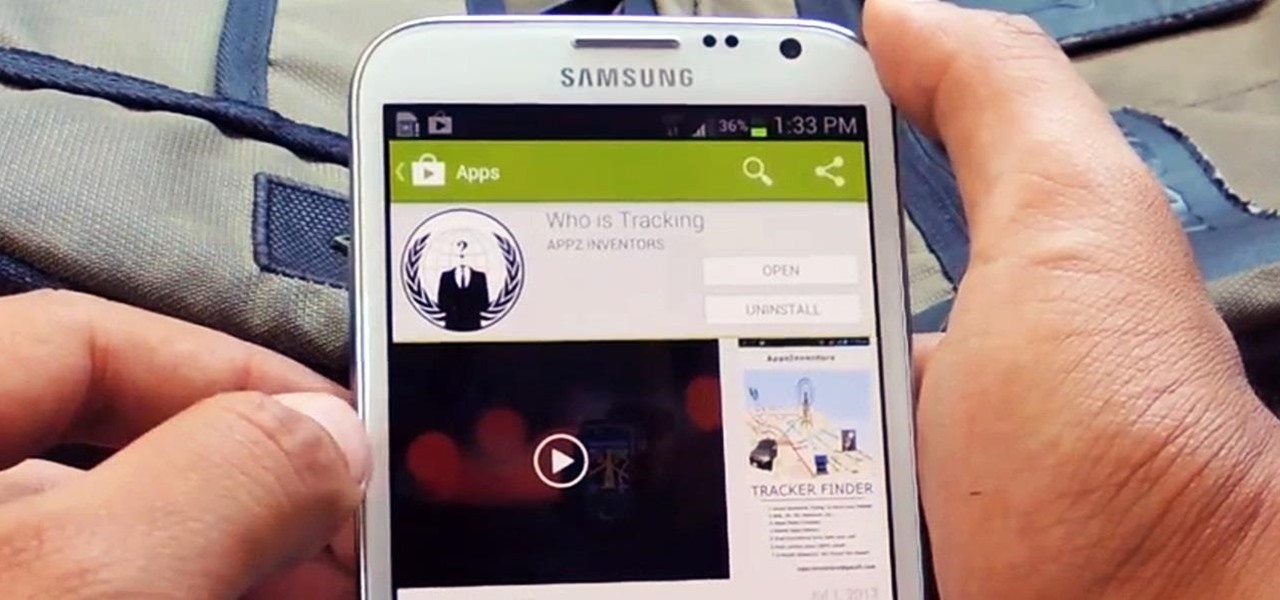
A wave of shock and anger swept across the country after Edward Snowden released private documents recounting the U.S. government's secretive mass surveillance programs. Although some of the fear was unwarranted (they don't read your emails or listen to your calls), many scrambled to find privacy of new heights for protection from the all-watchful eye. While the government may not be tracking you down, there are a myriad of other candidates that fill that Big Brother role—and I'm not talking ...

It starts innocently enough, with a nosy friend hovering over your shoulder to see what you're texting. Somehow, that doesn't satiate their inexplicable thirst for curiosity, so the first chance they get, they're rummaging through all of your super private photos—even though you told them not to.

The U.S. Postal Service has been in trouble for quite some time. With more and more people choosing to go digital to take care of bills, legal documents, and pretty much all other forms of correspondence, they haven't exactly kept up with the times. I mean, let's be honest—when was the last time you sent snail mail?

Most of us have some sort of malware scanner or antivirus program on our computers, but what about our smartphones? A lot of people don't realize that computers aren't the only devices that are susceptible to malicious software and apps—they can follow you on your smartphone or tablet, too.

There's really nothing safe about transmitting sensitive information electronically, but even if it gets there safely without being seen by prying eyes, there's no guarantee what happens to it once it reaches its destination. And let's face it, there are some things that you just don't want floating out there forever. So what can you do? Whether you want to send an email, a text, or a link, there are ways to send messages that self-destruct so that once they're read, they immediately vanish. ...

An internet connection has become a basic necessity in our modern lives. Wireless hotspots (commonly known as Wi-Fi) can be found everywhere!

Are you feeling like you've got the hang of Google+? Or do you, as I do sometimes, feel like there are just a few too many quirks to keep track of? Here, I've given you 15 quick tips you should know about Google+ so you can maximize the way you want to use it.

Want the convenience of a throwaway email address without all the hassle? How about anonymous text messaging so you can get to know someone before giving them your real information? Gliph has you covered. Gliph is a service that lets you create an identity around a set of three to five symbols called "artifacts" instead of your name, phone number, or email address. You choose how much information you reveal, and anytime you communicate with someone else who has Gliph, the data is protected us...

Every day we pass bridges, whether it's a foot bridge, a highway overpass, a span over water, or a viaduct over a valley. We pass on these structures without even thinking of the engineering genius that went into their design and construction, let alone the science behind their strength.

The video teaches the technique of crocheting with two different yarns. You start with a basic slip knot and then crochet a basic chain of ten loops. It is important to keep the loops loose and to ensure that you pull both yarns through the loop each time. Crocheting with two yarns give you a bigger fuller knot. After crocheting the chain of ten, you make a foundation row starting by crocheting two loops and then going through the second loop in the row of ten, using a single crochet stitch. ...

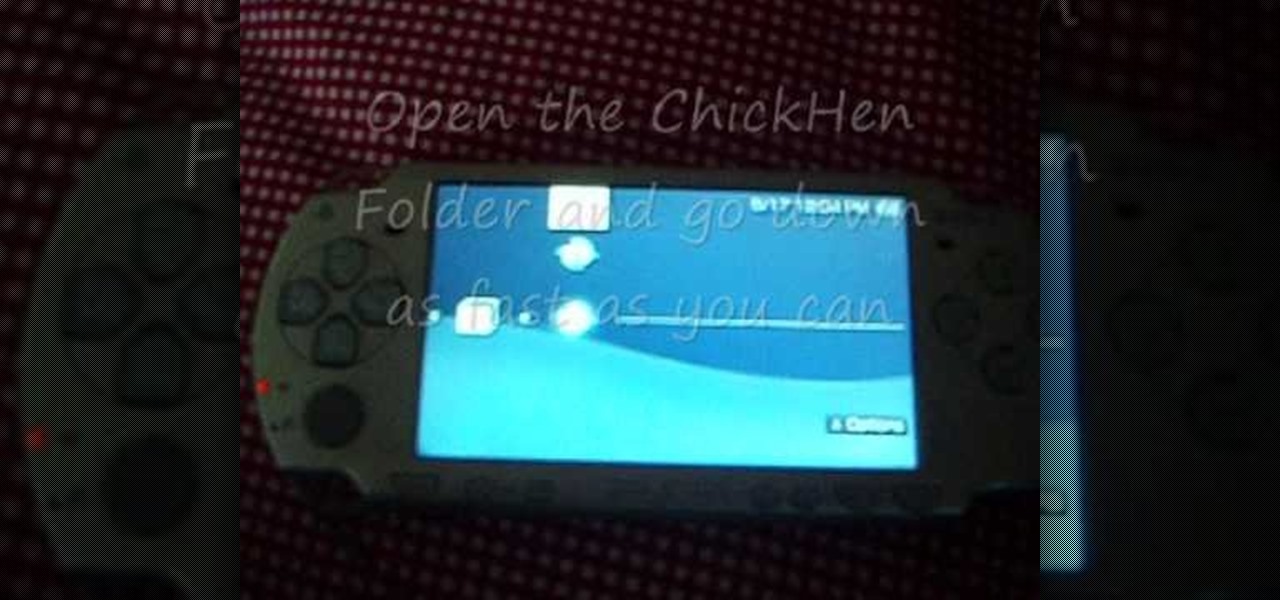
This is part 1 of 2 on how to hack a PSP without a Pandoras Battery using ChickHEN. You will need to ensure that you have firmware version 5.03 ChickHEN R2 in order for this hack to work.

If you're curious about how things work, or need to open up your Xbox 360 hard drive, be sure to check out this video. This video will also show you how to reassemble your hard drive after disassembling it. Keep in mind that opening up the Xbox 360 hard drive will break the warranty, meaning you won't be able to send it in to Microsoft for free assistance. It's recommended that you work on a desk to ensure you don't lose your screws.

Build a motor mount out of Lexan by making a template that ensures your plan will work and that you will reduce time, frustration, and re-work. Then, cut out the polycarbonate, mark the cutout on the motor, and assemble it all together on the radio control vehicle.

Dressing Timber. In this episode, we are having a look at dressing timber so that it is flat/straight and square, ready for a project. In this case, we are using some reclaimed Jarrah from an old deck, but the principle is the same if you are preparing timber that is DAR (dressed all round) from a timber yard, or hardware supply shop, or even if you have prepared your own board from raw timber.

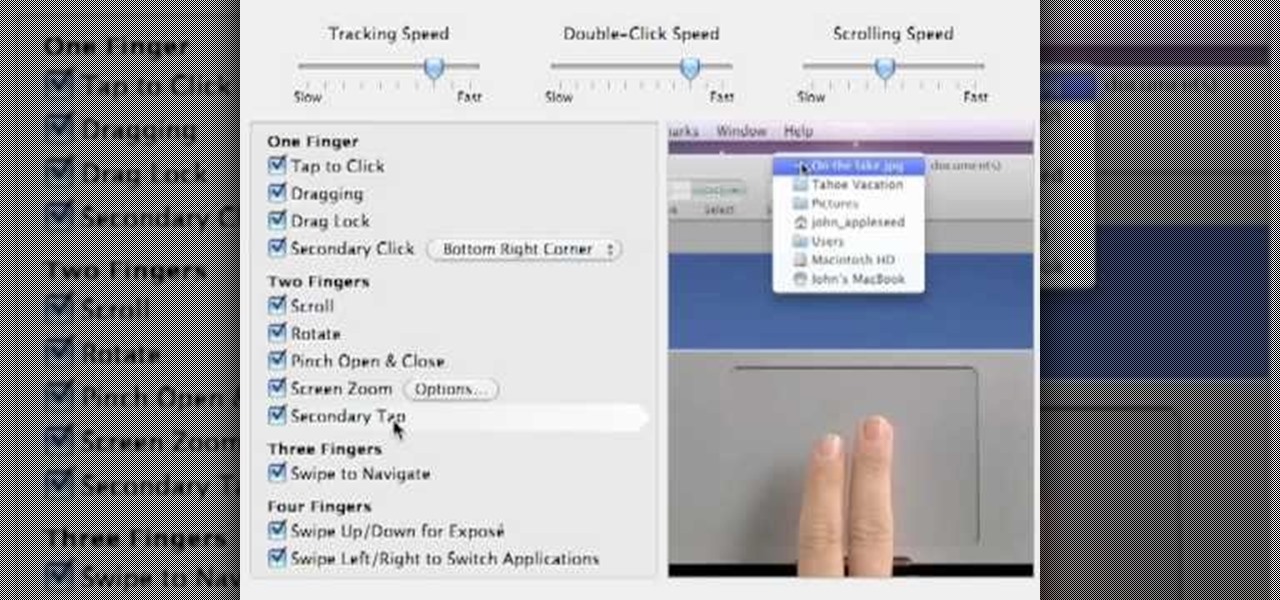
While the Macbook Pro track pad is a dream to use, it may not be immediately apparent on how to access the secondary, or "right click" menu. This video gives you a visual demonstration on how to right click using the two finger tap method. Note, it is important you check your System Preferences > Track pad preference pane to ensure secondary tap is the selected option. You can access the System Preferences by clicking on the Apple in the very top left hand corner of your screen and selecting ...

Access your computer's BIOS settings

When caring for your pet, finding and treating their insect bites which may cause allergic reaction in your pets. Bites from wasps, spider, bees, and other insects may cause an intense allergic effect. First, check if your pet is still breathing and check if there is a stinger still is in their body and scrape it out using a credit card. Using a medication that contains only chlorpheniramine if your pet is conscious, breathing, and not vomiting. Using this method, you will be able to ensure t...

Taking a screen shot of a window in Mac OS X can be a fun thing to do. Many people do not know how to complete this task. Following a couple simple steps can have you on your way in no time. The first thing that you will want to do is get your computer up and running. Once you are on the desktop, you can take a screen shot of it by pressing command-shift-4 and then holding the space bar. You should remember to hold the space bar and not just press it to ensure that the screen shot is captured...

Watch to learn how to replace an AEG fridge freezer door seal. You'll remove and replace the freezer door seal on an AEG fridge freezer. You will have a more efficient freezer and prevent energy loss if you replace a worn freezer door seal. One of many simple freezer maintenance tips that will help ensure you have the correct freezer temperature.

Your iPhone has a powerful feature that can keep your secrets hidden from other people, and you'll never have to worry about sharing or showing someone something embarrassing or incriminating ever again.

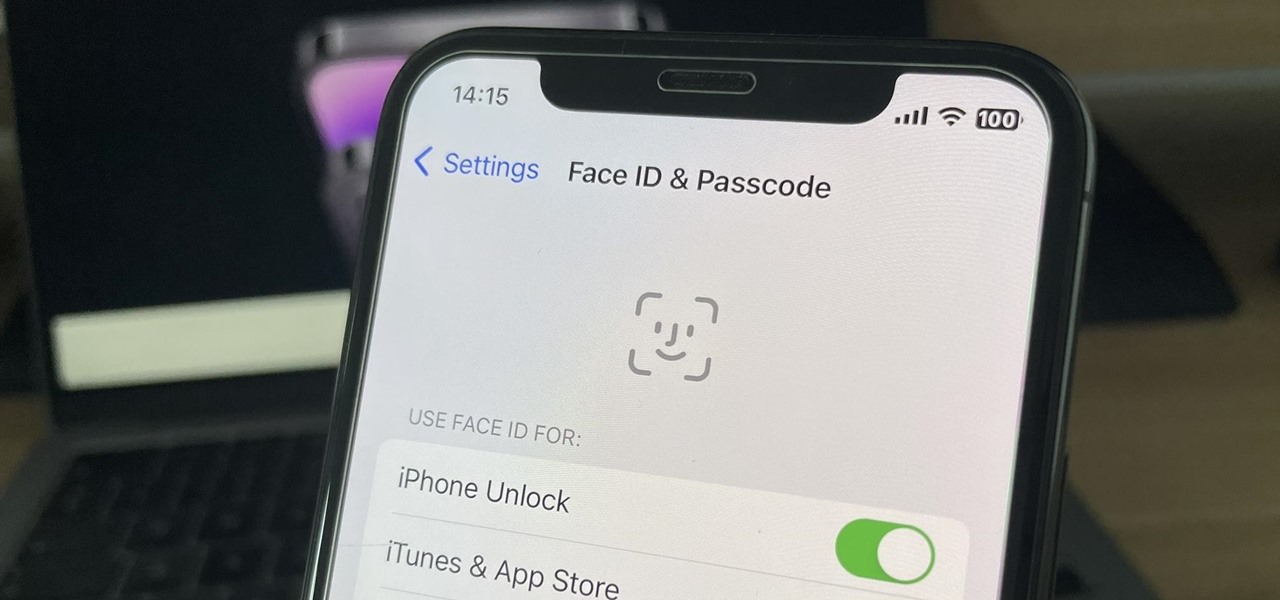
The iPhone 13 and iPhone 14 series models have a new feature on iOS 16 that lets you use Face ID when your iPhone is in landscape orientation. This is most helpful when trying to make purchases in apps and games where you use your iPhone rotated on its side. If you're having issues using Face ID in landscape mode, there may be some easy solutions to getting it working.

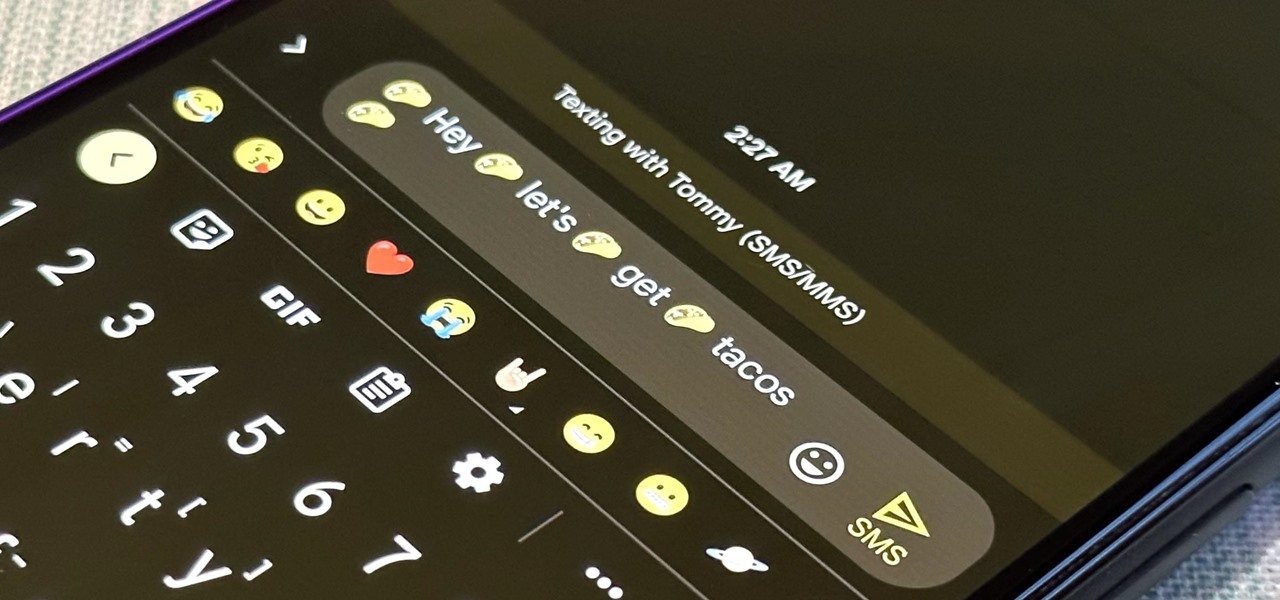
Emoji characters make messaging more fun, and Google has continuously added convenient and fun ways to insert playful symbols into your conversations using Gboard. After getting Emoji Kitchen in early 2020, we now have Emojify, a tool that automatically adds emoji to your message drafts.

Most of you have probably wondered at least once who has been checking out your social media profiles. While most platforms prohibit you from seeing who's viewed your profile, such as Facebook, Instagram, and Twitter, TikTok is one of the few places that lets you track profile visitors. And unlike with LinkedIn, you don't have to pay for the privilege.

Apparently, we learned nothing from Jurassic Park, as scientists are still working on bringing extinct species back to life. Until that day comes, you can interact with long-lost animals through augmented reality...if you have a newer model iPhone.

Apple wants to support the advertising economy, but its primary focus of late has been user privacy and security. In Safari, cross-site tracking, which lets content providers track you across websites and apps to show you more targeted ads, is disabled by default. However, content providers can get around that using less privacy-invasive ad measurements, but you can stop that too in iOS 14.5.

Apple has an excellent reputation for its privacy and security policies. That said, it isn't a perfect reputation. Take Siri, for example. The helpful iOS assistant isn't just communicating with you — Apple saves and listens to a history of your Siri interactions. If you don't want Apple storing your Siri history forever, there's something you can do about it.

It's pretty much a given at this point that Facebook has a lot of data on us. While you might be conscious of the data you share with Facebook when you post, upload photos, or chat with friends on Messenger, you might not be thinking about all the data it receives from websites and apps you use outside the social media giant. Now, you can actually do something about it.

Starting Sept. 13, you can preorder the iPhone 11, 11 Pro, or 11 Pro Max from Apple, wireless carriers, and various e-commerce websites. However, unlike with Android smartphones, there is only one set of iOS phones that come out each year, so they're pretty hot items. That means being the first to get your hands on one could be a challenge, but we're here to help you out.

It's finally out. After months of testing, iOS 13 is available to install on your iPhone, which means over 200+ new features you can use right now. The update, released on Sept. 19, can be installed over the air or from a restore image using iTunes in macOS Mojave and older or Finder in macOS Catalina. Ditto for the 13.1 update issued on Sept. 24.

We've already shown you our favorite new action games that have come out this year, but now it's time to share our all-time top ten list. These games are available for both Android and iPhone, they don't have intrusive ads or freemium schemes, and most importantly, they're all completely free to play.

A lot of people still trust their web browsers to remember every online account password for them. If you're one of those users, you need to adopt a more secure way of managing passwords, because browser-stored passwords are hacker gold mines. With a USB Rubber Ducky and physical access to your computer, they can have a screenshot of all your credentials in their inbox in less than 60 seconds.

In a previous tutorial, we were able to place the Mona Lisa on vertical surfaces such as walls, books, and monitors using ARKit 1.5. By combining the power of Scene Kit and Sprite Kit (Apple's 2D graphics engine), we can play a video on a flat surface in ARKit.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

Have you noticed the many utility ARKit apps on the App Store that allow you to measure the sizes of horizontal planes in the world? Guess what? After this tutorial, you'll be able to do this yourself!

If you're looking for your gaming fix and nothing on the App Store is piquing your interest, you should give soft-launched games a try. These are games that haven't been released in the US yet because they're getting tested in smaller markets first. Using a simple workaround, you can install them on your iPhone in any country.

PUBG is currently taking the mobile world by storm, and it's easy to see why. The game has breathed much-needed life to the multiplayer shooting genre, primarily by adding an element of sheer terror as you scavenge for weapons in a hostile environment. With new players continually joining in on the fun, many players are looking for ways to gain an edge.

Coinbase is the primary go-to for many users when it comes to investing in Bitcoin (BTC), Ethereum (ETH), Litecoin (LTC), Ripple (XRP), and more, due to its user-friendly interface. But before you join them, know that the ease of use comes with a price. Coinbase charges fees for each transaction, and your bank might even add charges on top of that. Plus, there is some fine print to be aware of.

The world is full of vulnerable computers. As you learn how to interact with them, it will be both tempting and necessary to test out these newfound skills on a real target. To help you get to that goal, we have a deliberately vulnerable Raspberry Pi image designed for practicing and taking your hacking skills to the next level.