Even if you live in a big city, chances are you have some wild raccoons or foxes that cannot abide a vertical trash barrel. While apparently omnipresent, these phantasmic critters usually vanish in the night leaving only a shameless trail of refuse you never wanted to see ever again. While I haven't found a way to stop them, I can help you snap some photos of the dastardly creatures.

Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!

With the mass arrests of 25 anons in Europe and South America, and the rumors of an FBI sweep on the east coast of America floating around, times look dicey for hackers. Over the past few days, a lot of questions have been posed to me about removing sensitive data from hard drives. Ideas seem to range from magnets to microwaves and a lot of things in-between. So, I'd like to explain a little bit about data forensics, how it works, and the steps you can take to be safe.

There is nothing more annoying than a greedy roommate. It's absolutely infuriating to wake up and find the cookies your mother just made for you gone without a trace. Your favorite drink is empty and the homemade meal you worked so hard on the night before is nowhere to be found. This irked me so much that I made this shocking cookie jar. When a cookie burglar touches the side and the lid of the jar simultaneously, a small electric shock stops them in their tracks.

Download the Software Go to the Antiprism downloads page. Download and install Antiprism 0.20.

Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!

There are so many hackers around these days, and they are becoming very smart. So smart that they have successfully taken down many government websites. The most recent attack was on the Department of Justice (DOJ). To read about the history of these hackers, check out Wikipedia.
If you are looking for ways/opportunities for you to be politically involved you have come to the right place. Here is a series of links that will take you to a webpage of a location where you can volunteer in and make a difference. In each section you will find:

Hello and welcome to another InfoSecurity World tutorial. The intent of this article is to teach one how to encrypt sensitive files. When set up correctly with a strong password, it would be almost impossible to hack. Even the FBI have had issues decrypting this software. I'm here to teach you how to create a general encrypted container—not the complex hidden TrueCrypt volume.

I want to write this article because in my childhood, I had experienced internet stalking which ultimately ended in physical stalking which then lead to several attempted abductions. I have now learned how to use the internet safely, who to communicate with and I've learned how stalkers work.

If you've read Alex Long's last two articles in this series (Part 1 and Part 2), you know by now that making money rarely is risk free, and generally plays out to be a high risk-high gain/loss scenario. The best way to make money is to have money, so for this article, lets assume a financial backing of about $10,000 dollars. For the sake of simplicity, I'm going to be working with online trading systems in this article. Some stocks are traded on exchanges, where buyers meet sellers and decide...

This is Part II in the Lockdown: The InfoSecurity Guide To Securing Your Computer series. Before beginning, check out Part I. This article will cover using alternate software to increase your security and will provide you with some information about websites and programs that test a computer's security. It will also guide you to software you can install or follow so you know what programs need to be updated on the computer. Lastly, I will talk about some features that should be disabled when ...

A few days ago, CloudOn released their free mobile app that brought Microsoft Office directly to your Apple iPad. The cloud-based service effectively runs Office on their end, allowing you to use apps like Word and PowerPoint to edit your documents, which you would house in Dropbox. But after overwhelming demand, they removed the free app yesterday from the iTunes App Store.

Overclocking is quite an awesome thing. When computer components are designed, they are made to run at a certain speed, otherwise known as their clock and bus speeds. These limits are not actually limits. You can overclock components, which essentially makes them go faster than their set limitations. This can save you a lot of cash when newer components come out and you don't have enough money to upgrade. However, when you overclock components, you must be careful and make sure that the machi...

This is my attempt to show people some cool things we can do with programming, and to give a small incentive for people to join the weekly Community Bytes. I wanted to make a tutorial on how to use Twitter from the command line with Python. This would have been an easy project to do not too far back, and a good bit of practice for a beginner to programming. It teaches that you can do useful stuff with programming. However, a while ago Twitter started using something called OAuth to access the...

A degree in nursing from Kaplan University addresses the challenges and scenarios real nurses work through on a daily basis. Kaplan University’s Master of Science in Nursing (MSN program) is based on relevant material to help ensure our students are prepared for their careers. Our online nursing degrees are based on flexible coursework; students enrolled in the Kaplan University School of Nursing program are already nurses and there is no easier way to cater to the ever-changing schedule of a...

Kaplan University presents Visionary Voices, a series of interviews that chronicle our goals in regards to adult education and continuing education throughout your life. Kaplan University offers online degree programs designed to expand the way you think and help you develop both personally and professionally. Students turn to us to develop their critical thinking skills, to challenge and prepare them for successful careers.*

Microsoft has had a pretty bad wrap with their Xbox 360 gaming console. Right from the start, the console has suffered a multitude of different hardware failures and design flaws. These problems cause the parts to get too hot and become faulty. I'm sure everyone who's had an Xbox 360 has gotten at least one Red Ring of Death or E74 error.

This Null Byte is the first part in a mini-series on the art of Social Engineering. I will be teaching you how to effectively defend yourself against it.

The dreaded moment you hope never happens—someone has stolen your laptop. You could have private information, pictures, or even private information belonging to the company you work for, all lost forever. It can cause you pain, money, or even a job.

Much of the press around the launch of Google+ has pitted it squarely against Facebook. This was highlighted painfully for Facebook with their (misguidedly dubbed) "awesome" announcements yesterday. Their launch of a new design, video calling, and group chat might have been exciting, had not Google announced its Hangout feature for Google+ a week earlier (and by the way, introduced their own 1-on-1 video calling inside of Gmail way back in 2008). Hangouts took video calling a step further and...

Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.

It's really a shame that it is so hard for people to make money on the internet these days. The dot com bubble has receded and scams are plentiful on the web. There are, however, a couple of legitimate ways to make a few extra bucks online, Amazon Mechanical Turk, or MTurk for short, is one of them. The idea of MTurk is to hook up programmers with people that do tasks that computers can not, these tasks are called HITs (Human Intelligence Task). These tasks include article creation, creative ...

Alas, today we continue on the journey to a more environmentally conscious way of being with part 2 of How to make your beauty routine more eco-friendly. Check out part 1 here.

GreenYou can tell a lot about a person's thought process by MTG color they favor: Red: aggressive, unsubtle, will surpass an obstacle by blowing it to bits with the largest explosives available (or Fireballs, as the case may be

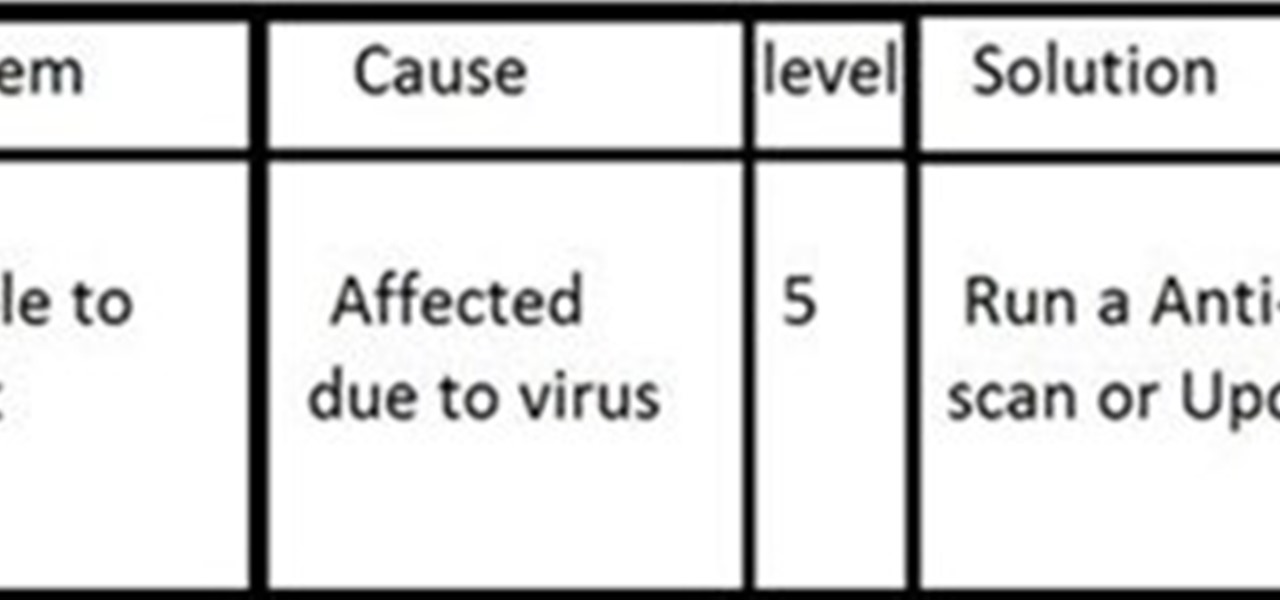
INTRODUCTION The everyday PC user doesn't think much about its PC and problems that can cause critical damage to their data or other stuffs stored on Hard drive and other electronic parts until the problem actually occurs. Once a failure happens, the repairs can be costly and very time-consuming and one also have to sacrifice their data stored on hard drives if the damage is more severe!

So what's all the fuss about World of Warcraft? I guess the first question would be 'is there a fuss?' and the simple answer is Yes there is, very much so.

Wondering how to set up Mozilla Thunderbird? Follow these simple steps: 1. When you first launch Thunderbird you are asked to create a new account. First click Email account and click Next.

STANDP'S WINDOWS 7 "ASTON-2" CUSTOMIZED DESKTOP IT ROCKS COMPLETELY!. DEC

So you've found yourself opting to be a vegetarian. The transition into a new way of eating and living is not always easy and as a result people often ditch their vegetarian goals and revert back to their previous eating habits. Here are some steps to ensure a successful transition to vegetarianism:

Graffiti is a great way of getting your message out to the masses. The earliest known graffiti dates back to 30,000 years ago and used the traditional apply-paint-to-wall technique. Though our paint now comes in cans and not from scavenged berries, the actual graffiti process hasn't really evolved from those first cave paintings.

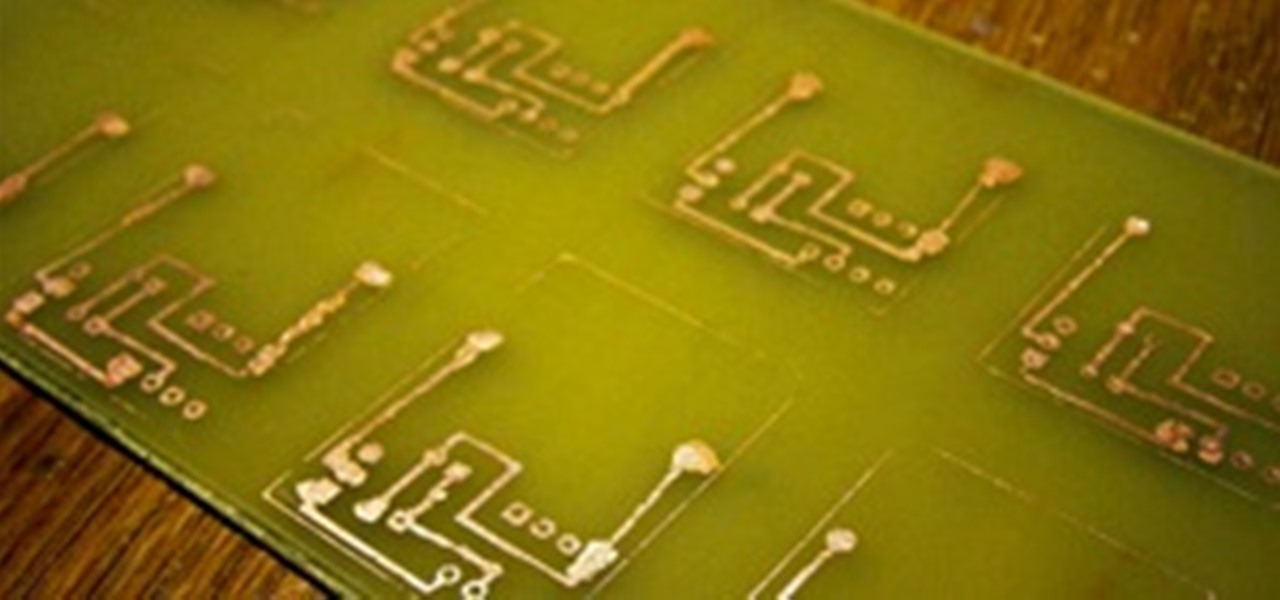
Homemade circuits are amazing. You can build any kind of circuit on a simple perfboard, as we have seen in previous projects. However, some projects require very tiny circuit boards. We could special order some boards from a printed circuit board (PCB) factory, but that will most likely involve a high price per board and a few thousand miles of delivery service to pay for.

Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!

If you follow the Anonymous, Occupy, and IT security scenes, you have no doubt heard about a dox release. What is it? How can it hurt you? And most importantly, how can you protect yourself from it? Some of these steps might seem common sense, while others will be an ah-ha! moment. Your private info is both your biggest weakness and your biggest weapon in your battle to remain anonymous. You must learn how to use it as both.

Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

Today's article serves as a general guide to keeping Windows 7 and Vista clean. The goal is to clean up your messy computer and have it running at maximum performance in no time. The question at hand is—what is your computer's performance like?

This is a two-part series to locking down the computer to provide maximum protection. Even though this guide will sound intrusive, we are talking about reality here. Extreme measures must be taken to protect our computers, especially when we have confidential documentation or do internet banking, which many people do. We all have to use electronic devices at some stage, whether it be for business or personal use.

Welcome to Minecraft World! Check out our advanced tutorials and come play with us on our free server.